当前位置:网站首页>DNS hijacking
DNS hijacking
2022-07-04 10:36:00 【I·CE】
Are simulated locally , Please do not use it in illegal ways
Xiaobai studies , If there are any errors or suggestions, please put forward
So let's see dns agreement , Of course dns It can also be used as a hidden tunnel ,,, Write it later
DNS The protocol is used to convert domain names to IP Address ( Can also be IP Convert the address to the corresponding domain name address )
dns hijacked :
Experimental environment :
Windows10( Drone aircraft ) 192.168.64.139,kali Linux( attack ) 192.168.64.133
Are all NAT Pattern , Ensure that they are in the same gateway , Be able to communicate , It can be used ping test (windows Default ping The four time ,Linux Default always ping, You can add a parameter -c To specify the ping The number of times )
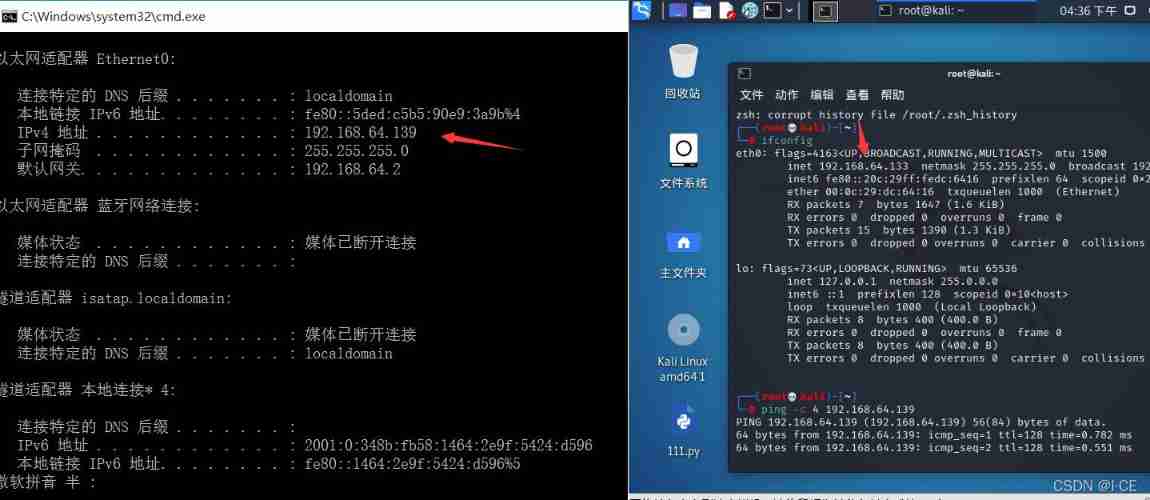
Get ready :
The tools used are kali Under the ettercap, Need to be in ettercap.dns Add the following data to the file ( stay /etc/ettercap/ettercap.dns in ):
###################################################
#microsoft sucks
#redirect it to www.linux.org
microsoft.com A 107.170.40.56
*.microsoft.com A 107.170.40.56
www.microsoft.com PTR 107.170.40.56 # wildcards in PTR are not allowed
*A 192.168.64.133
*PTR 192.168.64.133
##################################################
ps: Below * Represents all parsed to the target IP
Start
open ettercap, Choose the network card eth0
hosts Choose from scan for hosts Scan host , then hosts list List the surviving hosts
Take the attack IP Add to target1, Join the gateway target2
choice ARP poisoning… that , Default ,ok, Where to find out for yourself , Different versions and positions
stay plugins choice manage plugins, choice dns_spoof
Then it began to attack
then ping Baidu will find that the analysis is kali Of ip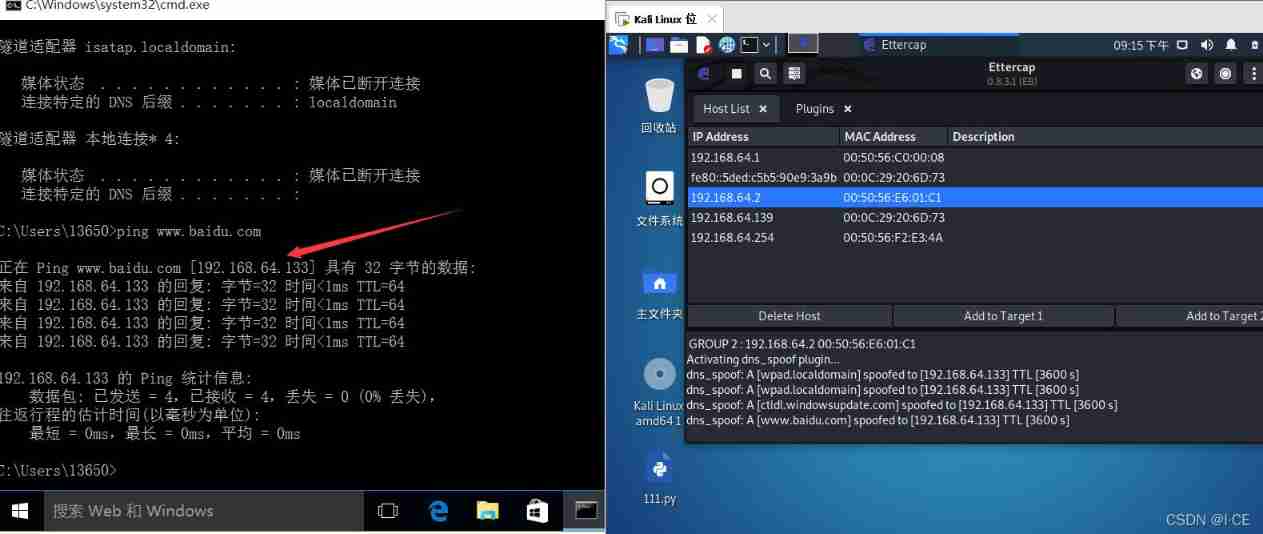
Little knowledge : If a website suddenly cannot be accessed, it may be that the operator hijacked your dns, Try modifying it locally hosts file
Usage expansion , Inside net fishing :
msf Create a Trojan , Let the target resolve to the server you set up , Build a website on the server , Prompt to download and upgrade the browser plug-in , Induced download generated Trojan
service apache2 start // start-up apache The server , Remember to drive 80 port
cp test.exe /var/www/html // Put the Trojan under the page
Limited ability , The page of inducing downloading and upgrading browser plug-ins cannot be written ,,, No code found , Subsequent patch ,,,
边栏推荐
- Rhcsa day 9
- DCL statement of MySQL Foundation
- 【Day1】 deep-learning-basics
- What is an excellent architect in my heart?
- Service developers publish services based on EDAs
- Batch distribution of SSH keys and batch execution of ansible
- /*The rewriter outputs the contents of the IA array. It is required that the type defined by typedef cannot be used in the outer loop*/
- Legion is a network penetration tool
- What is devsecops? Definitions, processes, frameworks and best practices for 2022
- Work order management system OTRs
猜你喜欢
![[FAQ] summary of common causes and solutions of Huawei account service error 907135701](/img/73/c4ee842475f05e2e67297fcac68779.png)
[FAQ] summary of common causes and solutions of Huawei account service error 907135701
![[Galaxy Kirin V10] [server] NUMA Technology](/img/9b/65466c6fc6336e27e842f50c26b9c3.jpg)
[Galaxy Kirin V10] [server] NUMA Technology
Sword finger offer 05 (implemented in C language)
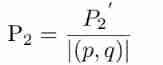
Latex error: missing delimiter (. Inserted) {\xi \left( {p,{p_q}} \right)} \right|}}
Idea SSH channel configuration
VLAN part of switching technology
Network connection (III) functions and similarities and differences of hubs, switches and routers, routing tables and tables in switches, why do you need address translation and packet filtering?
Software sharing: the best PDF document conversion tool and PDF Suite Enterprise version sharing | with sharing

Remove linked list elements
leetcode842. Split the array into Fibonacci sequences
随机推荐
leetcode1229. Schedule the meeting
【FAQ】华为帐号服务报错 907135701的常见原因总结和解决方法
Linked list operation can never change without its roots
Evolution from monomer architecture to microservice architecture
How do microservices aggregate API documents? This wave of show~
Static comprehensive experiment ---hcip1
system design
What is devsecops? Definitions, processes, frameworks and best practices for 2022
leetcode1-3
[Galaxy Kirin V10] [desktop] login system flash back
Legion is a network penetration tool
Write a program to judge whether the elements contained in a vector < int> container are 9.20: exactly the same as those in a list < int> container.
Rhcsa - day 13
Container cloud notes
Sword finger offer 05 (implemented in C language)
DDL language of MySQL database: create, modify alter, delete drop of databases and tables
Basic data types of MySQL
Network connection (III) functions and similarities and differences of hubs, switches and routers, routing tables and tables in switches, why do you need address translation and packet filtering?
RHCE - day one
Reprint: summation formula of proportional series and its derivation process