当前位置:网站首页>Rainbow share | how to use moving targets defense technology to guard against the unknown
Rainbow share | how to use moving targets defense technology to guard against the unknown
2022-08-01 00:03:00 【Rainbow that network visualization and security】
Moving target defense technology protects your network endpoints
In recent years, various organizations have been engaged in cybersecurity struggles all the time, but not all of them can achieve perfect cybersecurity protection.Cybercriminals use polymorphism, obfuscation, encryption, and self-modification to arm their malware to evade detection, and are constantly changing attack patterns and techniques to remain unpredictable.However, security proxies have common technical precursors known to attackers, creating a predictable and vulnerable global attack surface.
Moving Target Defense (MTD) replaces this asymmetric advantage.MTD dynamically changes the attack surface, making it more uncertain and complex, making enemy attacks more challenging.Protect your business from zero-day and evasive advanced threats with Mobile Target Defense, while Morphisec protects your applications and web browsers from any access attempts.The terminal is robustly protected, yet very simple to operate.

Function of moving target defense technology
01 Closing security holes
Many malicious actors publish millions of threats each year.Adversaries use their deep knowledge of the target environment to develop stealthy, highly targeted attacks that employ polymorphism, obfuscation, encryption, and other advanced techniques to evade security mechanisms, but Moving Target Defense (MTD)Technology is always one step ahead.
02 Reducing security risks and costs
MTD technology enables a prevention-first approach.
Other solutions identify the attack before blocking it.This exposes businesses to unknown attacks or those that leave no sign.
MTD technology blocks first and then identifies attacks.No guesswork, no hunting for missed attacks, no need to remediate losses.Independent of IOCs, MTD technology deterministically blocks the execution of exploits, evasive malware, and exploitless attacks before any damage occurs.It is easy to deploy into existing security infrastructure without false positives and without compromising system or network performance.
03 was born to defeat fileless attacks
Fileless, in-memory attacks are more than 10 times more likely to evade detection by taking legitimate system resources.
Advantages of Moving Target Defense Technology
01 Proactive Threat Prevention at its earliest stages
Based on a platform for moving target defense, MTD technology protects against known and unknown threats at the earliest stages of the attack lifecycle.
①Instant and complete protection against advanced threats and zero-day attacks. No need to detect, guess or search for missed attacks.
②Non-invasive proxy, zero performance degradation, no need to update.
③Reduce false positive reactions.No alarm fatigue or wasting resources on attacks that never happen.
④Replace traditional antivirus software with safer antivirus software. Replace traditional antivirus software with a more secure alternative at no additional cost with the integration of Morphisec's Defender AV.
02 Safer security for the IT community
Reduce security risks without reducing business operations or productivity.Morphisec was built from the ground up to align business and security needs.
①Prevent threats without continuous monitoring or generating large amounts of data
②Reduce IT complexity and protect business continuity.
③ Protection between patch cycles; as a compensating control for Windows 7.
④ Gain visibility into all endpoint attacks, including Microsoft Defender AV incidents.
⑤View the complete attack timeline and correlate events to make smarter and faster decisions.
⑥Easily deploy across virtual, physical or hybrid IT environments.
How does moving target defense technology work?

01 Morphing and Stealth: Turns the terminal into an unpredictable target.
When an application loads into memory space, Morphisec willChange the process structure, relocate and transform libraries, functions, variables and other data segments in a controlled manner.Each run is unique, and so is each process instance, which makes memory constantly unpredictable to an attacker.
02 Protection and Deception:Controlled Access to Transformed Structures
Legal application code memory is dynamically updated to use morphed resources.The application continues to load and run as usual, leaving the lightweight skeleton of the original structure as a trap.
03 Prevention and Exposure:Defuse and Expose Attacks
The attack targeted the original structure, but failed, unable to access the resources they expected and needed in order to execute.The attack was immediately stopped, contained, and recorded with full forensic details.
边栏推荐
- cobaltstrike
- NIO编程
- 类和对象:上
- The difference between adding or not adding the ref keyword when a variable of reference type is used as a parameter in a method call in C#
- Input and output optimization
- Matlab / Arcgis处理nc数据
- [Cloud Residency Co-Creation] [HCSD Big Celebrity Live Broadcast] Personally teach the secrets of interviews in big factories
- 一行代码解决CoreData托管对象属性变更在SwiftUI中无动画效果的问题
- Matlab / ArcGIS 处理GPM全球月均降水数据
- WindowInsetsControllerCompat is simple to use
猜你喜欢

MLP神经网络,GRNN神经网络,SVM神经网络以及深度学习神经网络对比识别人体健康非健康数据
In 2022, the latest eight Chongqing construction members (electrical construction workers) simulation question bank and answers

一行代码解决CoreData托管对象属性变更在SwiftUI中无动画效果的问题
cobaltstrike

NIO编程
![[微服务]分布式事务解决方案-Seata](/img/a8/fc6c24e4d42dfb635bad786cc02164.png)
[微服务]分布式事务解决方案-Seata
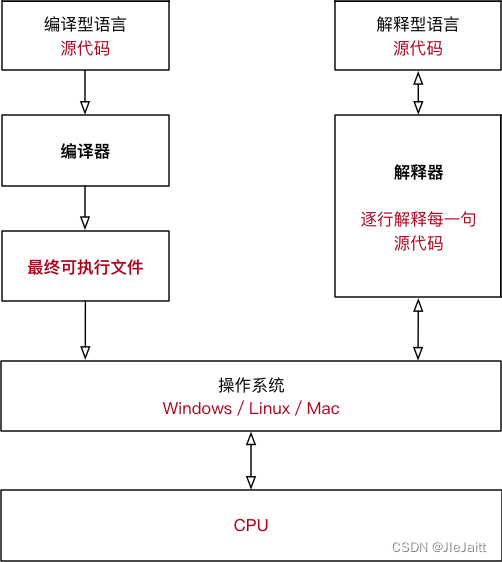
编译型语言和解释型语言的区别

SVN server construction + SVN client + TeamCity integrated environment construction + VS2019 development
![[MATLAB project combat] LDPC-BP channel coding](/img/37/4777e4d05cb2dbb1865f1d05ae9878.png)
[MATLAB project combat] LDPC-BP channel coding

高等代数_证明_任何矩阵都相似于一个上三角矩阵
随机推荐
The difference between /usr/local/bin and /usr/bin
pycaret源码分析:下载数据集\Lib\site-packages\pycaret\datasets.py
SQL injection Less38 (stack injection)
22年8月推广大使额外奖励规则
WindowInsetsControllerCompat is simple to use
2022年CSP-J1 CSP-S1 第1轮初赛 报名指南
助力数字政府建设,中科三方构建域名安全保障体系
lua入门案例实战123DIY
The difference between adding or not adding the ref keyword when a variable of reference type is used as a parameter in a method call in C#
Kyoto University:Masaki Waga | 黑箱环境中强化学习的动态屏蔽
虹科分享|如何用移动目标防御技术防范未知因素
NgRx 里 first 和 take(1) 操作符的区别
编译型语言和解释型语言的区别
cobaltstrike
基于simulink的Passive anti-islanding-UVP/OVP and UFP/OFP被动反孤岛模型仿真
Shell common scripts: Nexus batch upload local warehouse enhanced version script (strongly recommended)
SQL注入 Less47(报错注入) 和Less49(时间盲注)
Kyoto University: Masaki Waga | Dynamic Masking for Reinforcement Learning in Black Box Environments
WindowInsetsControllerCompat简单使用
Daily--Kali opens SSH (detailed tutorial)