当前位置:网站首页>[figure attack and Defense] backdoor attacks to graph neural networks (sacmat '21)
[figure attack and Defense] backdoor attacks to graph neural networks (sacmat '21)
2022-07-25 13:08:00 【chad_ lee】
Backdoor Attacks to Graph Neural Networks (SACMAT’21)
Neil Zhenqiang Gong Team work .
This paper mainly attacks GNN Model , The task scenario is transaction fraud 、 Social networks detect fake users 、 Malware detection, etc , These tasks are to classify a graph . In this paper, the backdoor attack Is to inject a sub graph structure into the graph as trigger, Then, if the same subgraph structure appears in the test set , Will predict the goal label. The method of injecting subgraphs is also relatively simple , Is the random method . Then the article puts forward defense methods , utilize Randomized Subsampling Achieve verifiable defense .
The target of the attacker is backdoored GNN The model should be in clean testing graph The accuracy is as high as possible , But in the injection trigger Of testing graph On ASR It should be as high as possible .
Generate trigger Method
First add trigger Only modify the diagram structure , Such as choice 4 Nodes as trigger Subgraphs , No matter what the structure of these four nodes is , Now change to this structure . control trigger Four parameters of subgraph
Trigger size:trigger The number of nodes of the subgraph t t t.
Trigger density:trigger The density of the graph ρ \rho ρ. ρ = 1 \rho=1 ρ=1 That is, each node and all other nodes have an edge connected .
Trigger synthesis method M M M: Generate trigger Method of subgraph , use ER Random graph generation . Basically random generation .
The density of poisoning γ \gamma γ : Yes trigger Percentage of the graph in the training set .
Attack process
Set it up Trigger size t t t and Trigger density ρ \rho ρ, And then use ER Random graph generates a trigger Subgraph template ( Only once ); Then randomly select several graphs in the training set as the data to be poisoned ; Then select randomly on each map to be poisoned t t t Nodes as , Let them become trigger. There are two points to explain :
1、 Training and testing trigger The subgraph structure is exactly the same . The author tries to use the same parameters fix trigger Or generate more random trigger, It is found that the index has little impact , Little reduction , The author explains GNN You can put similar structures trigger and label Connect .
2、 Choose which nodes form trigger Is random . The author tries to choose randomly t t t individual 、 choice degree Maximum / The smallest t t t、 Choose the one with the highest density of interconnection t t t Nodes , It is found that random is the most stable on different data sets , Other strategies have bad data sets .
Certified Defense
The author then proposes to use SOTA The verifiability of defense methods to defend him backdoor attack.
Verifiable defense is the use of Randomized smoothing Come on smooth Model , This paper makes use of Randomized Subsampling Come on smooth GNN. The specific method is to randomly sample each image in the training set , Training with randomly generated subgraphs , Then, when predicting, the prediction label is decided by voting .
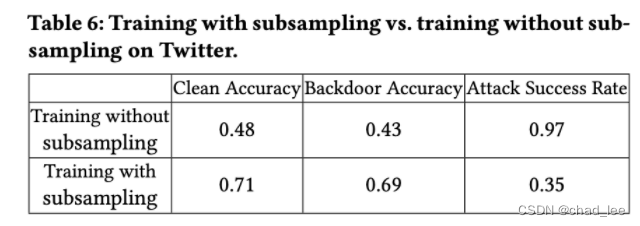
such Randomized Subsampling The defense method of can reduce the attack effect to a certain extent , But with datasets 、trigger size It matters a lot , When trigger size Above a certain threshold ,Certified Defense It's completely ineffective , This is it. GNN in Certified Defense Safe radius .

Verifiable defense and comparative learning
It can be seen that there are actually some comparative learning in the figure Randomized smoothing It means , By amplifying different subgraphs , Keep the same feature Output , Come on Randomized smoothing GNN encoder.
边栏推荐
- Make a general cascade dictionary selection control based on jeecg -dictcascadeuniversal
- Docekr学习 - MySQL8主从复制搭建部署
- 需求规格说明书模板
- Business visualization - make your flowchart'run'(3. Branch selection & cross language distributed operation node)
- Cyberspace Security penetration attack and defense 9 (PKI)
- R语言GLM广义线性模型:逻辑回归、泊松回归拟合小鼠临床试验数据(剂量和反应)示例和自测题
- 零基础学习CANoe Panel(16)—— Clock Control/Panel Control/Start Stop Control/Tab Control
- 【问题解决】org.apache.ibatis.exceptions.PersistenceException: Error building SqlSession.1 字节的 UTF-8 序列的字
- Shell common script: check whether a domain name and IP address are connected
- JS convert pseudo array to array
猜你喜欢

massCode 一款优秀的开源代码片段管理器

Mid 2022 review | latest progress of large model technology Lanzhou Technology

B tree and b+ tree
零基础学习CANoe Panel(12)—— 进度条(Progress Bar)
【问题解决】ibatis.binding.BindingException: Type interface xxDao is not known to the MapperRegistry.

ECCV2022 | TransGrasp类级别抓取姿态迁移

深度学习的训练、预测过程详解【以LeNet模型和CIFAR10数据集为例】
机器学习强基计划0-4:通俗理解奥卡姆剃刀与没有免费午餐定理

EMQX Cloud 更新:日志分析增加更多参数,监控运维更省心
Business visualization - make your flowchart'run'(3. Branch selection & cross language distributed operation node)
随机推荐
【重温SSM框架系列】15 - SSM系列博文总结【SSM杀青篇】
【AI4Code】《CoSQA: 20,000+ Web Queries for Code Search and Question Answering》 ACL 2021
Moving Chinese figure liushenglan
Shell common script: check whether a domain name and IP address are connected
Introduction to web security UDP testing and defense
Shell常用脚本:检测某域名、IP地址是否通
[problem solving] ibatis.binding BindingException: Type interface xxDao is not known to the MapperRegistry.
Docekr学习 - MySQL8主从复制搭建部署
【OpenCV 例程 300篇】239. Harris 角点检测之精确定位(cornerSubPix)
AtCoder Beginner Contest 261 F // 树状数组
部署Apache网站服务以及访问控制的实现
Deployment of Apache website services and implementation of access control
EMQX Cloud 更新:日志分析增加更多参数,监控运维更省心
ORAN专题系列-21:主要的玩家(设备商)以及他们各自的态度、擅长领域
如何理解Keras中的指标Metrics
cv2.resize函数报错:error: (-215:Assertion failed) func != 0 in function ‘cv::hal::resize‘
卷积神经网络模型之——VGG-16网络结构与代码实现
The larger the convolution kernel, the stronger the performance? An interpretation of replknet model
G027-OP-INS-RHEL-04 RedHat OpenStack 创建自定义的QCOW2格式镜像
Machine learning strong foundation program 0-4: popular understanding of Occam razor and no free lunch theorem