当前位置:网站首页>ARTS_ twenty million two hundred and twenty thousand six hundred and twenty-eight
ARTS_ twenty million two hundred and twenty thousand six hundred and twenty-eight
2022-07-04 17:50:00 【cswh】
ARTS The first 1 Zhou
One per week ARTS: Algorithm: Do one every week leetcode The algorithm of Review: Read and comment on writing an English technical article Tip: Learn at least one technical skill Share: Share a technical article with ideas and thoughts .
Table of Contents
- Algorithm Two points search
- Review JVM Reading guide ——— explain Java Virtual machine architecture
- Tip Regular expressions , Replace spaces and comments
- Share Computer science course recommendation
Algorithm
704. Two points search
Title Description : Given a n The elements are ordered ( Ascending ) integer array nums And a target value target , Write a function search nums Medium target, If the target value has a return subscript , Otherwise return to -1.
public class Two points search _704 {
public static void main(String[] args) {
int[] nums = new int[]{-1,0,3,5,9,12};
int target = 9;
System.out.println(search(nums, target));
nums = new int[]{-1,0,3,5,9,12};
target = 2;
System.out.println(search(nums, target));
}
public static int search(int[] nums, int target) {
int left = 0, right = nums.length - 1;
while (left <= right) {
int mid = (right - left) / 2 + left;
int num = nums[mid];
if (num == target) {
return mid;
} else if (num > target) {
right = mid - 1;
} else {
left = mid + 1;
}
}
return -1;
}
} Time complexity :O(logn), among n Is the length of the array .
Spatial complexity :O(1)O(1).Review
JVM Tutorial - Java Virtual Machine Architecture Explained for Beginners
JVM Reading guide —— Explain for beginners Java Virtual machine architecture ,JVM(Java virtual machine ) yes Java The core of the ecosystem , Make the software program able to “ Write once , Run anywhere ”,JVM Originally designed to support JAVA, Later, as time goes by , Also supports the Scala、Kotlin and Groovey. In this article , The author introduces JVM Its working principle and its various components .What is a virtual machine ?
A virtual machine is a virtual representation of a physical computer , A physical machine can run multiple virtual machines , Each virtual machine has its own operating system and Application , These virtual machines are isolated from each other .evernotecid://3E6433C6-011C-425E-8C4F-812D1500C164/appyinxiangcom/25583646/ENResource/p4599
What is? Java virtual machine ?
stay C and C++ In programming languages , The code is first compiled into platform specific machine code . These languages are called compilation languages (compiled languages). On the other hand , stay JavaScript and Python Such as language , The computer executes instructions directly without compiling them . These languages are called interpretive languages (interpreted languages).Java Combine these two technologies . Java The code is first compiled into bytecode to generate a class .class file . Then this class file is composed of Java Virtual machine explains . The same class file can run on any version of any platform and operating system JVM On the implementation . Similar to virtual machines ,JVM Create an isolated space on the host . This space can be used to perform Java Program , It has nothing to do with the platform or operating system of the machine Java Virtual machine architecture
JVMb Include 3 Two different components :
- Class Loader ( Class loader )
- Runtime Memory/Data Area ( Run time memory / Data area )
- Execution Engine ( Execution engine ) evernotecid://3E6433C6-011C-425E-8C4F-812D1500C164/appyinxiangcom/25583646/ENResource/p4600
image.png
Class loader Class Loader
The class loading process is divided into three stages : load (loading)、 link (linking) And initialize (initialization).
evernotecid://3E6433C6-011C-425E-8C4F-812D1500C164/appyinxiangcom/25583646/ENResource/p4601
Run time memory / Data area Runtime Memory/Data Area
There are five components in the runtime data area , Here's the picture
evernotecid://3E6433C6-011C-425E-8C4F-812D1500C164/appyinxiangcom/25583646/ENResource/p4602
Execution engine Execution Engine
Once bytecode is loaded into main memory , And the details in the runtime data area are available , The next step is to run the program . The execution engine handles this problem by executing the code that exists in each class .
however , Before executing the program , Need to convert bytecode into machine language instructions . JVM You can use an interpreter for the execution engine (Interpreter) or JIT compiler .
evernotecid://3E6433C6-011C-425E-8C4F-812D1500C164/appyinxiangcom/25583646/ENResource/p4603
Java Native Interface (JNI)
Java Supported by Java Native interface (JNI) Execute native code .
Native method library (Native Method Libraries) Using other programming languages ( for example C、C++ And assembly language ) Authored Library . These libraries are usually in the form of .dll or .so The form of the document exists . These local libraries can be accessed through JNI load .
summary :
The author discusses Java The architecture of virtual machine and its various components . Usually we don't delve into JVM Internal mechanism , It doesn't care how the code works when it runs . Only when there is a problem and we need to adjust JVM Or repair memory leaks , We will try to understand its internal mechanism .
This is also a very popular interview question , Whether it's a junior or senior back-end position . Deepen understanding JVM It can help you write better code and avoid the pitfalls associated with stack and memory errors .
Tip
Use VS code perhaps IDEA when , If you need to delete comments or spaces in the code , You can use the following regular expression
// Format notes , Regular expressions
(/\*([^*]|[\r\n]|(\*+([^*/]|[\r\n])))*\*+/|[ \t]*//.*)
Blank line , The rules are as follows
^\s*(?=\r?$)\nShare
Share a computer science course , Ten minute course series : Computer science
边栏推荐
- What if Kaili can't input Chinese???
- 估值900亿,超级芯片IPO来了
- NFT流动性市场安全问题频发—NFT交易平台Quixotic被黑事件分析
- 《吐血整理》保姆级系列教程-玩转Fiddler抓包教程(2)-初识Fiddler让你理性认识一下
- I2C子系统之适配器的设备接口分析(i2c-dev.c文件分析)
- Two methods of MD5 encryption
- 解决el-input输入框.number数字输入问题,去掉type=“number“后面箭头问题也可以用这种方法代替
- 设置窗体透明 隐藏任务栏 与全屏显示
- Superscalar processor design yaoyongbin Chapter 7 register rename excerpt
- 公司要上监控,Zabbix 和 Prometheus 怎么选?这么选准没错!
猜你喜欢

智捷云——元宇宙综合解决方案服务商

上网成瘾改变大脑结构:语言功能受影响,让人话都说不利索
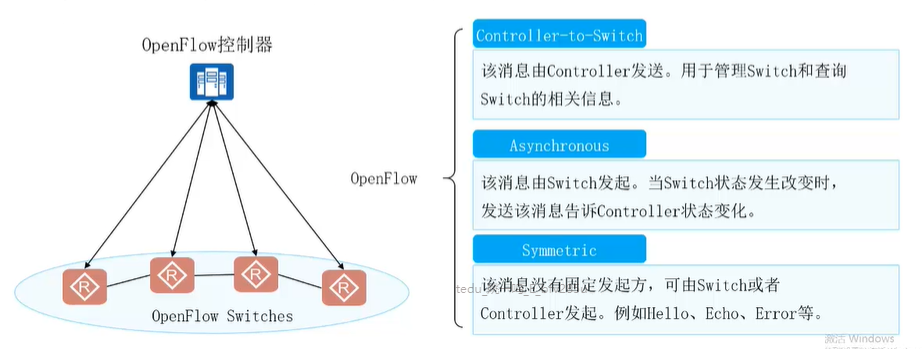
【华为HCIA持续更新】SDN与FVC

Zhijieyun - meta universe comprehensive solution service provider
Offline and open source version of notation -- comprehensive evaluation of note taking software anytype

KS007基于JSP实现人个人博客系统

Internet addiction changes brain structure: language function is affected, making people unable to speak neatly
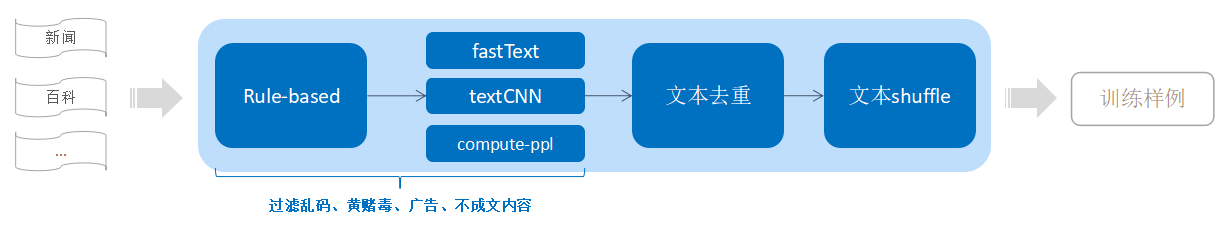
Oppo Xiaobu launched Obert, a large pre training model, and promoted to the top of kgclue
La 18e Conférence internationale de l'IET sur le transport d'électricité en courant alternatif et en courant continu (acdc2022) s'est tenue avec succès en ligne.
PingCode 性能测试之负载测试实践
随机推荐
数学分析_笔记_第7章:多元函数的微分学
利用win10计划任务程序定时自动运行jar包
【HCIA持续更新】广域网技术
【华为HCIA持续更新】SDN与FVC
S5PV210芯片I2C适配器驱动分析(i2c-s3c2410.c)
[HCIA continuous update] overview of WLAN workflow
ble HCI 流控机制
Is it safe for CITIC Securities to open an account online? Is the account opening fee charged
New technology releases a small program UNIPRO to meet customers' mobile office scenarios
kaili不能输入中文怎么办???
PingCode 性能测试之负载测试实践
Zebras are recognized as dogs, and the reason for AI's mistakes is found by Stanford
长城证券安全不 证券开户
CANN算子:利用迭代器高效实现Tensor数据切割分块处理
Master the use of auto analyze in data warehouse
VB cannot access database stocks
【每日一题】556. 下一个更大元素 III
【Proteus仿真】基于VSM 串口printf调试输出示例
tx.origin安全问题总结
Display opencv drawn pictures on MFC picture control control