当前位置:网站首页>Section VII starting principle and configuration of zynq
Section VII starting principle and configuration of zynq
2022-06-28 07:36:00 【youbin2013】
ZYNQ Starting principle and configuration of
1 The boot process
The device configuration contains for initialization and configuration ps and pl All methods and processes . Under the control of software ,ps Internal DevC Provides for initialization and configuration ps and pl Means and methods , stay zynq Two modules are provided in to control the configuration process :
- BootROM, A static memory blocker block , After power on reset and warm reset , Yes Cortex-A9 Of CPU Execute this built-in program ;
- Device configuration unit : Used to control the JTAG Debug access and provide connections to AES、HMAC and PCAP Module interface , It is used to realize the pl Configuration and data decryption .
stay ps Under the control of , It can realize safe or non safe configuration ps and pl. adopt zynq Provided JTAG Interface , The user can control the... Under the control of an external host zynq To configure ,zynq Configuration from the beginning is not supported pl The process of . Yes zynq The configuration process for includes at least two stages , But it usually requires 3 Stages .
- Stage 0: This stage is also called BootROM, This stage controls the start-up of the initial equipment .BootROM After power on reset or warm reset , The code executed by the processor that cannot be modified by the user , The code has been solidified to zynq Of BootROM in ;
- Stage 1: In this phase , Usually the first level boot program is executed . however , It can also be any user controlled code ;
- In this phase , Usually, the software program written by the user is executed , however , It can also be the second level boot program , This phase is completely under the control of the user .
2 zynq Of BootROM
BootROM characteristic :
- Provide 3 In a different way , Used for configuration PS: Two master modes and one slave mode , That's safety 、 Encrypted image 、 Main mode ; Non secure main mode ; adopt JTAG Non secure slave mode ;
- Support 4 Different external startup sources :Quad-SPI Flash、NAND Flash、NOR Flash、SD;
- Support use AES-256 and HMAC(SHA-256) Of PS Security configuration ;
- Support Soc Debug security ;
- from NOR and QSPI The configuration process is performed in the chip .
After power on and reset , start-up PS The configuration process , When forbidden JTAG Mode time ,zynq Internal Cortex-A9 Processor from on-chip BootROM Start executing code ,BootROM Contains for driving NADN、NOR、Quad-SPI、SD and PCAP Basic program code .
stay BootROM Initialization of peripherals is not performed in , In phase 1 Or after this stage zynq To initialize other peripherals , Considering the safety factor , When out of the reset state ,Cortex-A9 The processor always PS The first device in all other master device modules in the , When executing BootROM when , Prohibition of execution JTAG, To ensure safe operation .
BootROM The code is also responsible for loading the first boot image file ,zynq The hardware in supports loading multi-level user boot images , After the first stage is started , The user is responsible for further loading the user initiated image , When BootROM Hand over control fsbl after , The user is responsible for further loading the user initiated image , When the reset operation , Will be re executed BootROM Code in .
BootROM Supports encrypted and unencrypted images , Besides , When using on-chip execution features , When from linear flash、NOR or QSP Copy the image directly or after execution ,BootROM Support from the OCM Start the execution phase 1 Mirror image .
At safe start CPU when , From safety BootROM Run code , also , For incoming users PS Image decoding and authentication , Save it to OCM RAM in , then , Branch into it , In case of unsafe startup CPU when , from BootROM Run code , If used XIP features , Jump to at branch OCM ROM or Flash When mirroring a user in , Disable all safe boot features , Unless you use something with XIP Start of , Generally will PS The boot image is limited to 192KB Within the scope of .
Then used for PS/PL The process of the start-up phase , It is the responsibility of the user , And under the control of the user . stay zynq in , Users are not allowed to access BootROM The code in , In the completion phase 1 After the process of safe start , The user can continue to perform subsequent security / Non safe start-up phase , If the first stage of non security is implemented at the beginning , Only the non safe phase can then be started .
adopt PL Hardwired inside AES-256 and SHA-256 modular ,PS Realize decryption and authentication , For this reason , At any stage of safe start-up , Even if only for PS To configure , Must also give PL Access to electricity , such , Users can use the on-chip eFUSE On a unit or chip BRAM, Select the key of the device .
stay zynq Internal support 5 Available starting devices , Include NAND、NOR、SD、Quad-SPI and JTAG, The top 4 Three startup sources are used for main mode startup .
- During main mode startup ,Cortex-A9 The processor is responsible for loading the image file from the external nonvolatile memory to the on-chip PS in .
- JTAG Can only be used to start the process from mode ,JTAG Only non safe startup is supported , An external computer acts as a master device , adopt JTAG Connect , Load the boot image into OCM, When the boot image is loaded ,PS CPU Keep idle mode .
BootROM The high-level configuration flow of is shown in the figure 2.1 Shown .

chart 2.1 BootROM High level configuration process
3 zynq Device configuration interface
Equipment configuration interface structure DevC Module by 3 A main module with independent operation :
- Used to connect to PL Configure logical AXI-PACP Interface ;
- Device security management unit ;
- One XDAC Interface ;
The device configuration interface contains a APB Interface , Host use APB Interface configuration 3 A module , And access the entire state as well as the implementation and PL XADC signal communication .
AXI-PCAP Bridge :
AXI-PCAP Bridge will 32 position AXI Format data into 32 Bit PCAP agreement , vice versa , This bridge supports configuration data , Download and upload in concurrent and non concurrent ways , Pictured 3.1 Shown .

chart 3.1 AXI-PCAP Bridge
stay AXI and PCAP There is a send and receive between interfaces FIFO buffer , In the picture DMA The engine is used in FIFO And memory devices (OCM、DDR Memory , Or a peripheral memory ) Move data between .
When passed PCAP When the interface moves data , Must give zynq Of PL Power supply at one end , adopt DevC Controller register PCAP MODE and PCAP PR bits , Can make PCAP Interface , If you send encrypted data , You should also set QUARTER PCAP RATE EN bits .
adopt DevC Built in module DMA engine , stay PCAP Data transmission between interfaces . To start a data transfer process , It must be written in the following order 4 individual DMA register :DMA Source address register ;DMA Destination address register ;DMA Source length register ;DMA Destination length register .
To pass through PCAP Transfer data to PL, The destination address should be set to 0xffffffff. Allied , adopt PCAP Interface from PL Reading data , The source address should be set to 0xffffffff, Must pass PCAP Interface to send encrypted PS Mirror image , This is because AES and HMAC The engines reside in PL one end . In this case ,DMA The source address should be set to an external memory interface , The destination address should be set to OCM.
DevC Of DMA The engine can be used to load unsafe PS Mirror image , Before loading , Set... In miscellaneous control register PCAP LPBK bits , This bit enables the internal loop , Bypass PCAP Interface , In the use of PCAP front , This bit needs to be disabled again ,DMA The source address should be set to an external memory , The destination address should be set to a OCM Or a valid external memory interface , Such as DDR.
PCAP Interface is also used to read back PL To configure . To perform a read back operation ,PS Software code must be run , Enable to produce the correct PL Read back instructions , Use two DMA Access cycle , Read back a PL To configure .
Equipment safety management :
DevC It contains a security policy module , The following functions are provided :
- Monitoring system security , When a conflicting state is detected , Can confirm a safe reset , This state can indicate inconsistent system configuration or tampering ;
- adopt APB Interface control and monitoring PL Configuration logic ;
- control ARM CoreSight Debugger access port for DAP And commissioning level ;
- Provide on-chip ROM control .
XADC Interface :
- Read and write XADC register ;
- 15 A deep write command FIFO and 15 A deep reading FIFO(32 Bit width );
- programmable FIFO Level interrupt ;
- Alarm interrupt ;
- Overtemperature interruption ;
3.1 PS The main equipment is not started safely
In this startup mode ,PS As the main equipment .BootROM Load a plain text from the selected external memory PS Mirror image , Pictured 3.2 Shown , under these circumstances , There is no demand for PL Access to electricity , have access to PS The image is loaded immediately or later PL Bit stream .
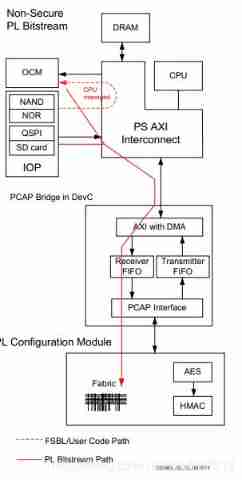
chart 3.2 PS Main non safety startup process
The main steps of the configuration process are as follows :
- Power on and reset the equipment ;
- BootROM perform :1, Read bootstrap program , To determine the external memory interface type ;2, Read start header information , To determine the state of encryption and the target of mirroring ;
- BootROM Use DevC Of DMA, take FSBL Load into OCM Or other valid destination address ;
- close BootROM, Release CPU Used to control the FSBL;
- adopt PCAP,FSBL load PL Bit stream .
3.2 PS The main equipment starts safely
In this startup mode ,PS As the main equipment ,BootROM Load an encrypted... From the selected external storage PS Mirror image , Pictured 3.3 Shown , because AES and HMAC The engine resides in PL in , So it requires PL Power up to initialize the startup sequence , Trying to decrypt FSBL front ,BootROM verification PL It's powered on , When to start PS after , You can use an encrypted bitstream configuration , Or configure after power failure PL.

chart 3.3 PS Main safety start diagram
The detailed steps of the configuration process are given below :
- Power on and reset the equipment ;
- BootROM perform :1, Read bootstrap program , To determine the external memory interface ;2, Read start header , To determine the state of encryption ( Security );3, confirm PL Access to electricity , Start decrypting FSBL;
- BootROM Use DevC DMA engine , adopt PCAP, Will be encrypted FSBL Sent PL Internal AES and HMAC;
- PL Use PCAP To be decrypted FSBL Back to PS, then , Load it into the chip here OCM;
- close BootROM, Release CPU Used to control the FSBL;
- FSBL Configure with an encrypted stream PL.
边栏推荐
- In idea, the get and set methods may be popular because the Lombok plug-in is not installed
- LLVM 与 Clang
- Design and implementation of spark offline development framework
- Unity-UI-shadow组件
- R 语言绘制 动画气泡图
- Face to face experience --- test engineer web side automation --- interview questions for large factories
- 7-1 懂的都懂
- 看似简单的光耦电路,实际使用中应该注意些什么?
- Huawei cloud computing physical node cna installation tutorial
- NDK cross compilation
猜你喜欢

HTTP Caching Protocol practice

Safety training is the greatest benefit for employees! 2022 induction safety training for new employees

Kubernetes deploys a secret pit where thanos ruler sends repeated alarms

8 张图 | 剖析 Eureka 的首次同步注册表
Jinshan cloud team shared | 5000 words to understand how Presto matches with alluxio
BACnet/IP網關如何采集樓宇集中控制系統數據

阿里云服务器创建快照、回滚磁盘

Devtools implementation principle and performance analysis practice

2021 programming language ranking summary
PLC -- 笔记
随机推荐
What should I do if the version is incompatible with the jar package conflict?
linux下修改mysql用户名root
剑指Offer||:链表(简单)
7-1 understand everything
Drawing animated bubble chart with R language
R language drawing ggplot2 seasonal graph
Sword finger offer|: linked list (simple)
linux下修改mysql端口号
Practice of traffic recording and playback in vivo
Practice and exploration of vivo live broadcast application technology
MySQL master-slave replication, detailed configuration, create unable to connect processing prompt
Modifying MySQL port number under Linux
[ thanos源码分析系列 ]thanos query组件源码简析
HTTP Caching Protocol practice
股票炒股注册开户靠谱吗?安全吗?
mysql57 zip文件安装
kubelet驱逐机制的源码分析
安全培训是员工最大的福利!2022新员工入职安全培训全员篇
R 语言 ggmap
What is a consistent hash? What scenarios can it be applied to?