当前位置:网站首页>Host based intrusion system IDS
Host based intrusion system IDS
2022-07-03 17:03:00 【Brother Xing plays with the clouds】
experiment Linux platform CentOS System
Application background : As system administrator , They need a security mechanism , For example, the mechanism of detecting file tampering
What exactly does it detect ? The contents of the document 、 File properties
AIDE: The abbreviation of advanced intrusion detection system
How can it be achieved :AIDE By scanning the surface, one is tampered linux The server File system to build file attribute database
take The server File attributes and database conversion , Warn the index of the modified file !
You can see from above :ADIE The initial installation of must keep the data ‘ clean ’
After the system is installed , And no services are exposed on the Internet or even on the LAN
step : After installing the system ----- Broken net ------ Install at the terminal AIDE service ------ To configure
install The server End software aide
# yum install aide
Default profile /etc/aide.conf
The main protection rules in the configuration file are :FIPSR NORMAL DIR DATAONLY
FIPSR = p+i+n+u+g+s+m+c+acl+selinux+xattrs+sha256
jurisdiction :p The index node :i Link number :l user :u
Group :g size :s Modification time :m Creation time :c
ACL:acl SELINUX:selinux xattrs:xattr
SHA256/SHA512 Monitoring and (sh256 and sh 512)
Exclamation point before entry ! tell ADIE Ignore subdirectories or directory files
First run AIDE
Initialize first ADIE database
aide --init
according to /etc/side.conf Generated by configuration file /var/lib/aide/aidedb.new.gz The file needs to be renamed /var/lib/aide/aidedb.gz
First proofreading
# aide Run this command directly , If there are no parameters, it defaults to check Options
to update AIDE database
# aide --update
thank you ~~~~~
边栏推荐
- 简单配置PostFix服务器
- LeetCode 1657. Determine whether the two strings are close
- Mysql database DDL and DML
- Preventing/catching “IllegalArgumentException: parameter must be a descendant of this view” error
- 新库上线 | CnOpenData中国保险机构网点全集数据
- RF analyze demo build step by step
- 跨境电商:外贸企业做海外社媒营销的优势
- What kind of material is 14Cr1MoR? Analysis of chemical composition and mechanical properties of 14Cr1MoR
- Define a structure fraction to represent a fraction, which is used to represent fractions such as 2/3 and 5/6
- One brush 146 force buckle hot question-3 longest substring without repeated characters (m)
猜你喜欢

Pools de Threads: les composants les plus courants et les plus sujets aux erreurs du Code d'affaires

New features of C 10
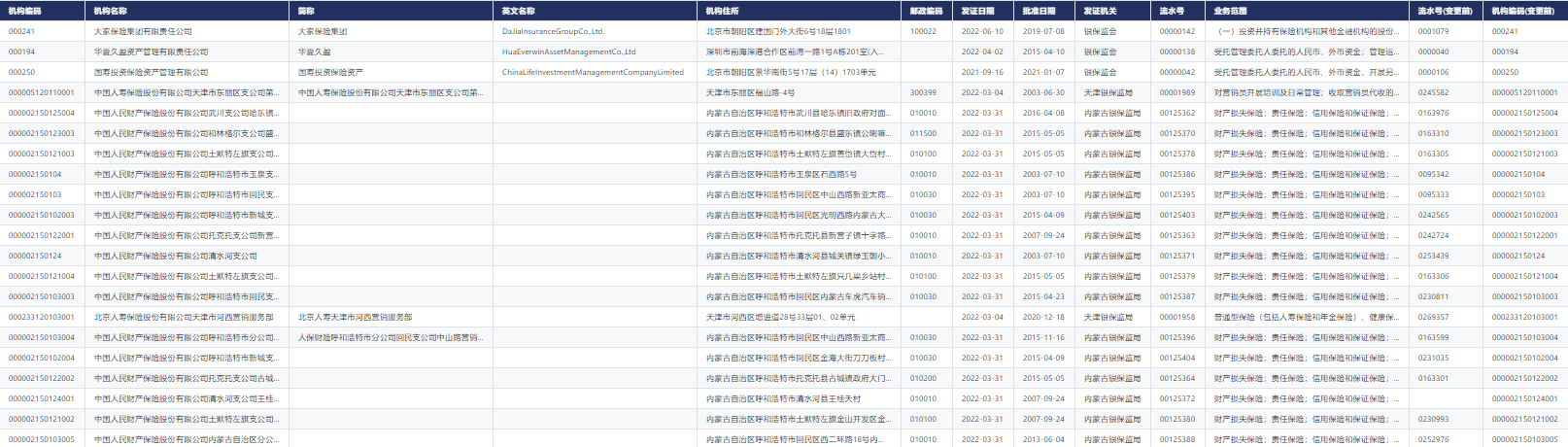
New library online | cnopendata complete data of Chinese insurance institution outlets

CC2530 common registers for crystal oscillator settings

13mnnimo5-4 German standard steel plate 13MnNiMo54 boiler steel 13MnNiMo54 chemical properties

线程池:业务代码最常用也最容易犯错的组件

大消费企业怎样做数字化转型?

Bcvp developer community 2022 exclusive peripheral first bullet
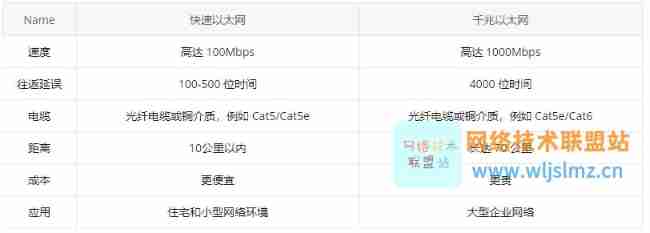
Fast Ethernet and Gigabit Ethernet: what's the difference?
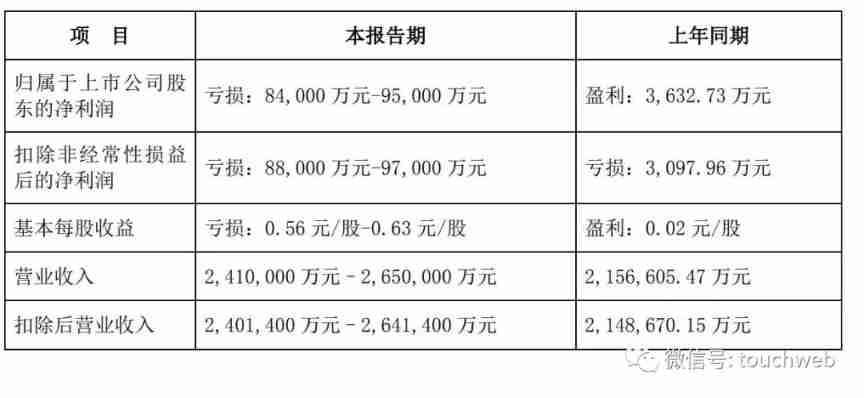
Shentong express expects an annual loss of nearly 1billion
随机推荐
New library online | cnopendata complete data of Chinese insurance institution outlets
2022.02.14_ Daily question leetcode five hundred and forty
IL Runtime
深入理解 SQL 中的 Grouping Sets 语句
Web crawler knowledge day03
Apache服务挂起Asynchronous AcceptEx failed.
The largest matrix (H) in a brush 143 monotone stack 84 histogram
[mathematical logic] equivalent calculus and reasoning calculus of propositional logic (propositional logic | equivalent calculus | principal conjunctive (disjunctive) paradigm | reasoning calculus)**
人生还在迷茫?也许这些订阅号里有你需要的答案!
The word backspace key cannot delete the selected text, so you can only press Delete
CC2530 common registers for watchdog
RedHat 6.2 配置 Zabbix
Atom QT 16_ audiorecorder
Take you to API development by hand
[combinatorics] recursive equation (characteristic equation and characteristic root | example of characteristic equation | root formula of monadic quadratic equation)
Idea configuration plug-in
Recommendation of good books on learning QT programming
13mnnimo5-4 German standard steel plate 13MnNiMo54 boiler steel 13MnNiMo54 chemical properties
PHP online confusion encryption tutorial sharing + basically no solution
[2. Basics of Delphi grammar] 1 Identifiers and reserved words