当前位置:网站首页>Handling write conflicts under multi-master replication (4) - multi-master replication topology
Handling write conflicts under multi-master replication (4) - multi-master replication topology
2022-07-31 15:32:00 【Huawei cloud】
The topology of replication describes the communication path through which write requests are propagated from one node to another.With two masters, as in Figure-7, there is only one reasonable topology: M1 must synchronize all his writes to M2, and vice versa.When there are more than two M, a variety of different topologies are possible.Figure-8 illustrates some examples.
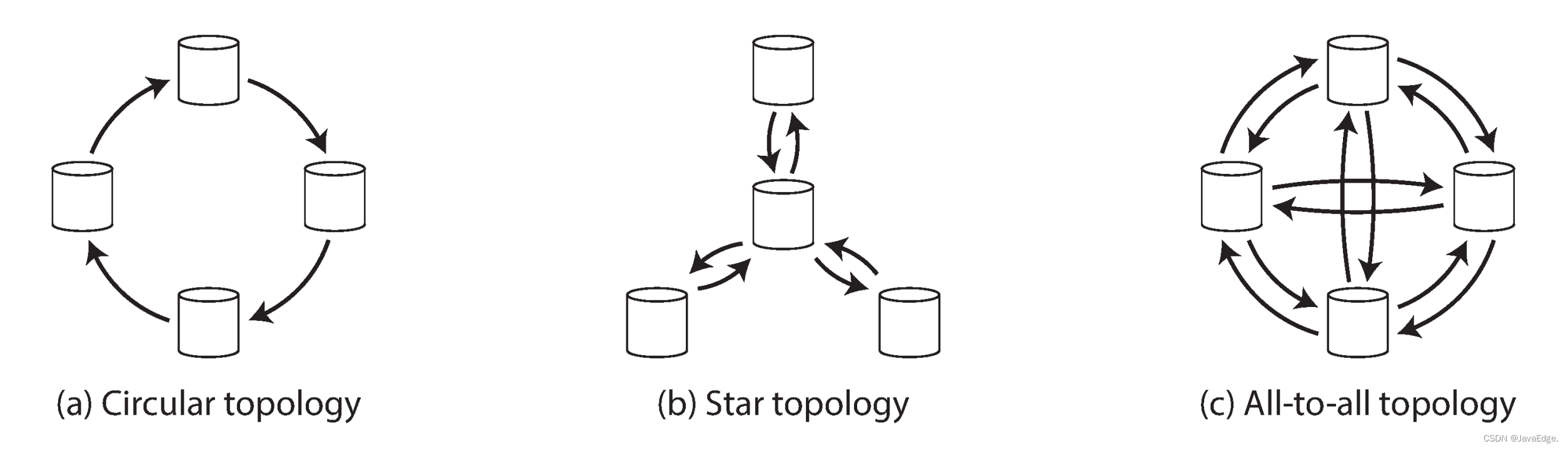
The most common topology is all-to-all, i.e. Figure-8, where each M synchronizes its writes to all other Ms.
But more restricted topologies are also used: for example, MySQL only supports circular topologies, where each node receives writes from the previous node and writes those writes (plus its own writes)In) forwarded to the subsequent node.
Another popular structure is the star shape ^v.A designated root node forwards writes to all other nodes.The star topology can be generalized to trees.
Ring, star topology
Write requests need to go through multiple nodes to reach all replicas, i.e. intermediate nodes need to forward data changes received from other nodes.To avoid infinite loops, each node needs to be assigned a unique identifier, and each write request in the replication log is marked with the identifiers of all nodes that have passed.When a node receives a data change marked with its own identifier, the data change will be ignored, avoiding repeated forwarding.
Questions
If a node fails, it may disrupt the flow of replicated messages between other nodes, rendering them unable to communicate until the node is repaired.Topologies can be reconfigured to work on failed nodes, but in most deployments this reconfiguration must be done manually.A more densely connected topology (such as all-to-all) is more fault-tolerant because it allows messages to travel along different paths, avoiding a single point of failure.
All-to-all topologies can also be problematic.Especially when some network links may be faster than others (network congestion), as a result some replicated messages may "overtake" others, as shown in Figure-9.
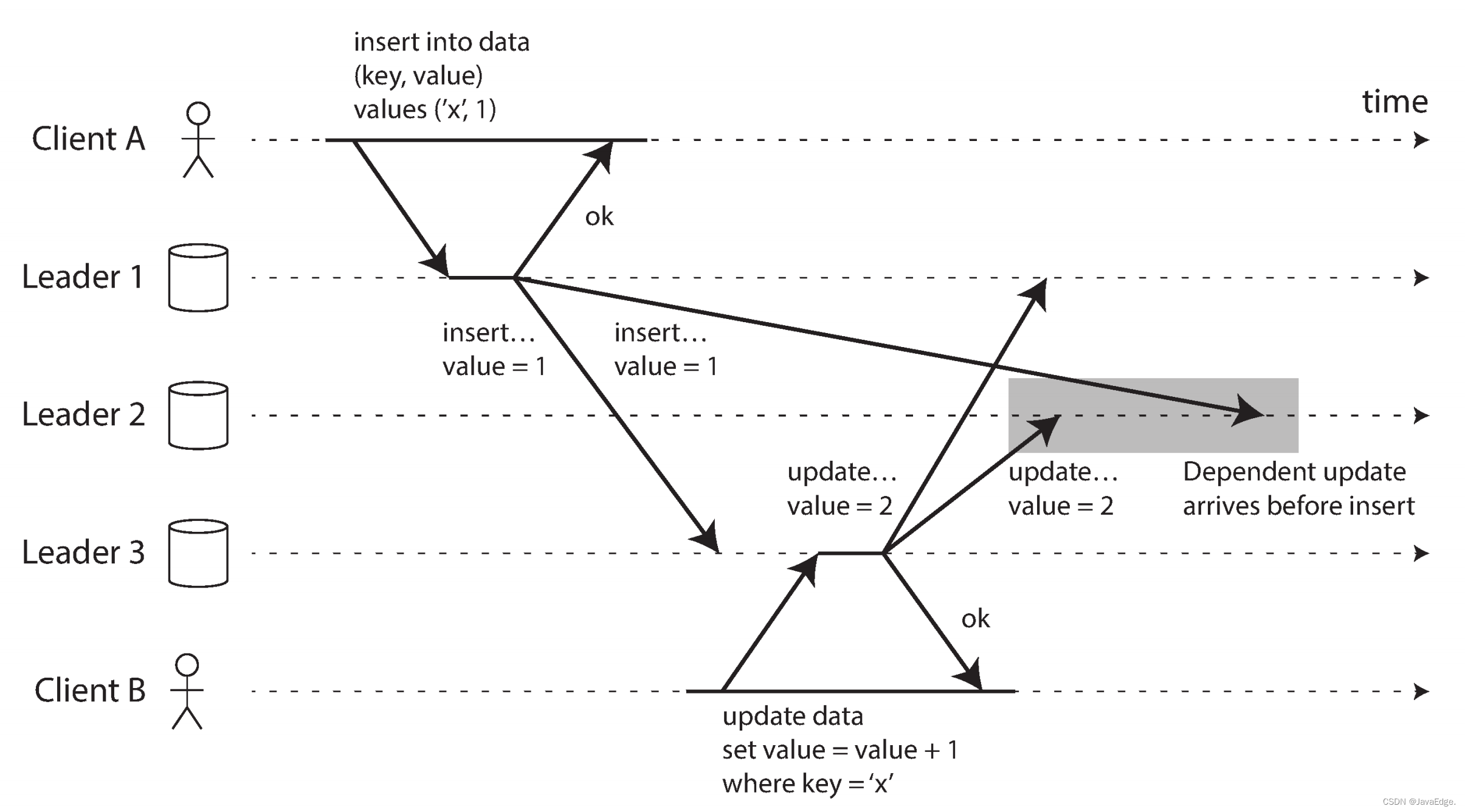 Client A sends L1A row is inserted into the table, and B updates the row in L3.However, L2 can receive writes in a different order: updates (from its perspective, updates to rows that don't exist in the database) can be received first, and then L1's insert log (which should arrive before the update log).
Client A sends L1A row is inserted into the table, and B updates the row in L3.However, L2 can receive writes in a different order: updates (from its perspective, updates to rows that don't exist in the database) can be received first, and then L1's insert log (which should arrive before the update log).
This is a causality problem, similar to "consistent prefix reads": updates depend on previously completed inserts, so make sure all nodes receive inserts before processing updates.Adding a timestamp to each log write is not enough, mainly because there is no way to ensure that the clocks are fully synchronized and thus the received logs cannot be ordered correctly on L2.
To properly order log messages, a version vector can be used.Conflict detection technology is not fully implemented in many primary replication systems.As PostgreSQL BDR does not provide causal ordering of writes, Tungsten Replicator for MySQL does not even attempt to detect conflicts.
边栏推荐
- .NET 20周年专访 - 张善友:.NET 技术是如何赋能并改变世界的
- JVM参数解析 Xmx、Xms、Xmn、NewRatio、SurvivorRatio、PermSize、PrintGC「建议收藏」
- 【MySQL】Mysql范式及外键作用
- Why is the field of hacking almost filled with boys?
- WPF project - basic usage of controls entry, you must know XAML
- RecyclerView高效使用第二节
- Kubernetes原理剖析与实战应用手册,太全了
- Doing things software development - the importance of law and understanding of reasonable conclusions
- Kubernetes principle analysis and practical application manual, too complete
- TRACE32——C源码关联
猜你喜欢

WeChat chat record search in a red envelope
TRACE32——基于SNOOPer的变量记录

RecyclerView的高效使用第一节

AVH Deployment Practice (1) | Deploying the Flying Paddle Model on Arm Virtual Hardware
Kubernetes common commands

How useful is four-quadrant time management?

工程流体力学复习

button控件的使用
Female service community product design

Why don't you make a confession during the graduation season?
随机推荐
type of timer
Browser's built-in color picker
Delete table data or clear table
QGIS 加载WMS数据,重新投影
"Autumn Recruitment Series" MySQL Interview Core 25 Questions (with answers)
Why don't you make a confession during the graduation season?
Snake Project (Simple)
【MySQL】Mysql范式及外键作用
C语言”三子棋“升级版(模式选择+AI下棋)
删除表格数据或清空表格
双边滤波加速「建议收藏」
01 Encounter typescript, build environment
多主复制下处理写冲突(4)-多主复制拓扑
Deployment应用生命周期与Pod健康检查
Codeforces Round #796 (Div. 2) (A-D)
对话庄表伟:开源第一课
力扣:738.单调递增的数字
TRACE32 - C source code association
what exactly is json (c# json)
Kubernetes常用命令