当前位置:网站首页>Apache middleware vulnerability recurrence
Apache middleware vulnerability recurrence
2022-07-06 07:27:00 【mingyeqf】
kali Reappear apache Unknown extension resolution vulnerability
- Reappear
I uploaded a name called shell.php.aaa The file of , When this feature exists , Take a look .aaa incognizance ,
Continue to parse ,.php I know , It can be interpreted as php The file . The same goes for visits , For example, visit phpinfo.php.qqq Can be displayed successfully phpinfo
So which suffixes Apache incognizance ?
be not in mime.types None of them know (Multipurpose Internet Mail Extensions)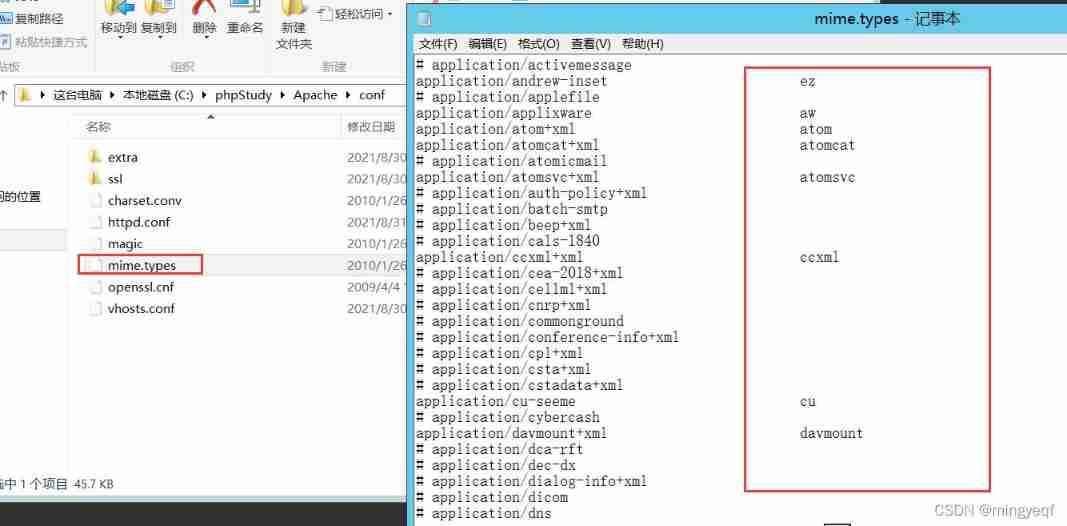
sudo service apache2
restart cd /etc/apache2/mods-enabled sudo
vim php7.4.conf
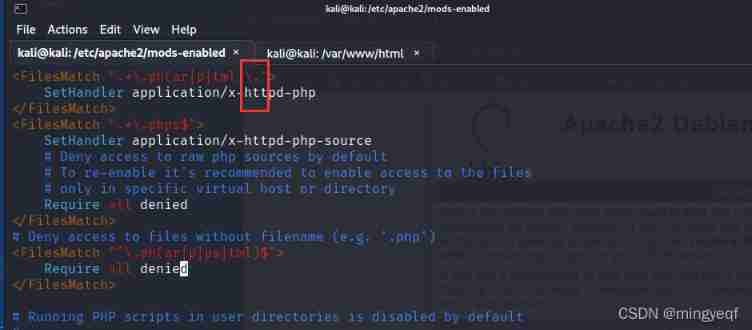
hold $ Switch to . And then restart apache It can be parsed into php
sudo service apache2 restart
stay /var/www/html establish shell.php.aaa And write <?php phpinfo();?>
Access local files 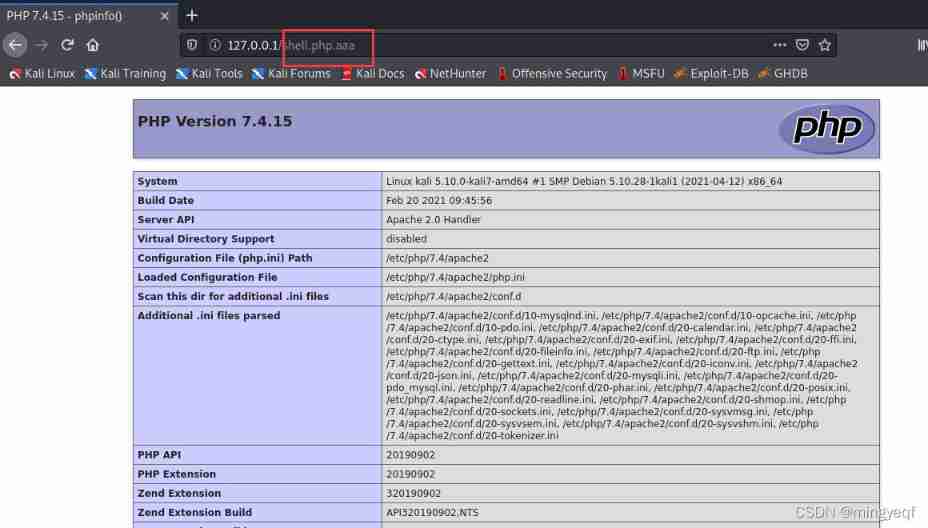
4. Repair suggestions
Solution 1
stay httpd.conf or httpd-vhosts.conf Add the following statement , This prevents the file name format from being .php. Access rights of :
<FilesMatch ".(php.|php3.|php4.|php5.)">
Order Deny,Allow
Deny from all
</FilesMatch>
Solution 2
If you need to keep the file name , You can modify the program source code , Replace... In the upload file name “.” by “_”:
$filename = str_replace('.', '_', $filename);
2.2 AddHandler Parsing vulnerability caused by
1. Loophole :
(1)apache There is a principle when parsing files : When encountering an unknown extension , It will be parsed from back to front , Until we meet the expansion of knowledge
Until the exhibition name
(2) If you don't know it, the source code will be exposed .
stay apache Improper configuration will cause apache Parsing vulnerabilities .
2. Reappear :
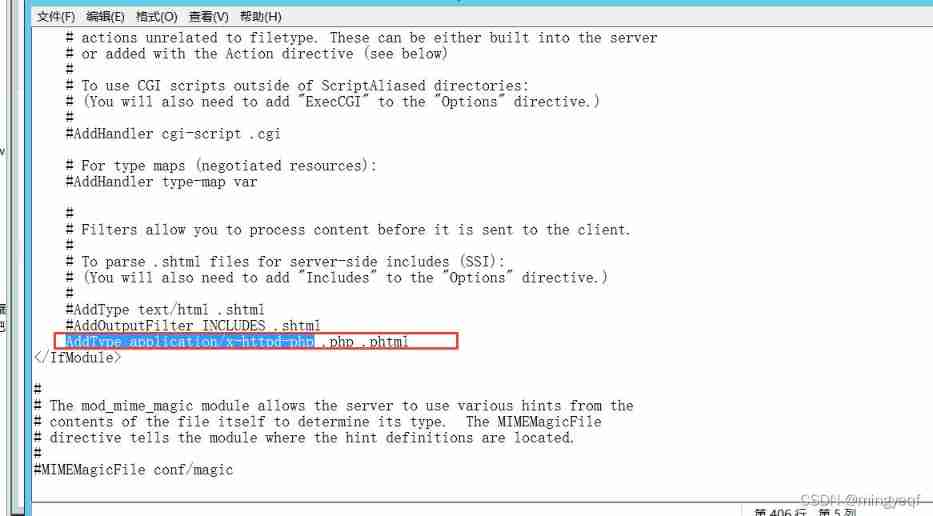
1、 stay httpd.conf Take out the notes , Suffixes exist .php .phtml Will be resolved into php file
AddType application/x-httpd-php .php .phtml

3. Repair suggestions
1. stay httpd.conf or httpd-vhosts.conf Add the following statement , This prevents the file name format from being .php. Access rights of :
<FilesMatch ".(php.|php3.|php4.|php5.)">
Order Deny,Allow Deny from all
</FilesMatch>
2. Modify the improperly configured file
2.3 Directory traversal vulnerability
1. principle
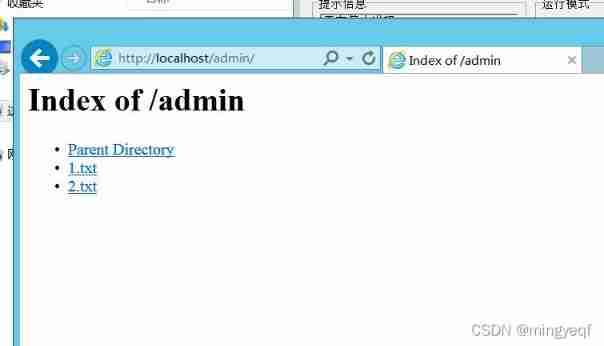
principle : When a client accesses a directory ,Apache The server will look for one by default index list Documents in , Ruvin Pieces do not exist
stay , All files in the current directory will be listed or returned 403 Status code , The behavior of listing all files in the directory is called directory traversal .
2. Reappear
httpd.conf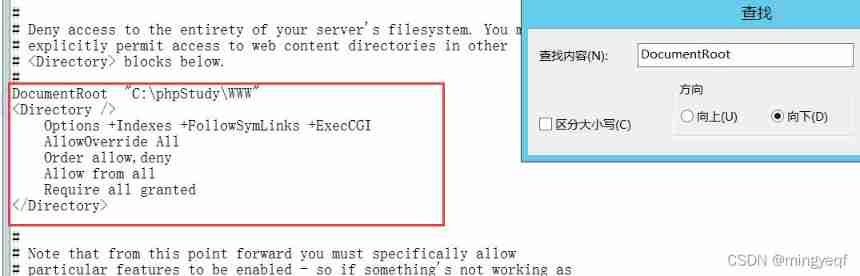
3. defense
stay httpd.conf Found in file Options + Indexes + FollowSymLinks + ExecCGI And modified to Options - Indexes +FollowSymLinks + ExecCGI And save ( Well + It is amended as follows -)
+ Indexes Allow directory browsing — Indexes Disable directory browsing
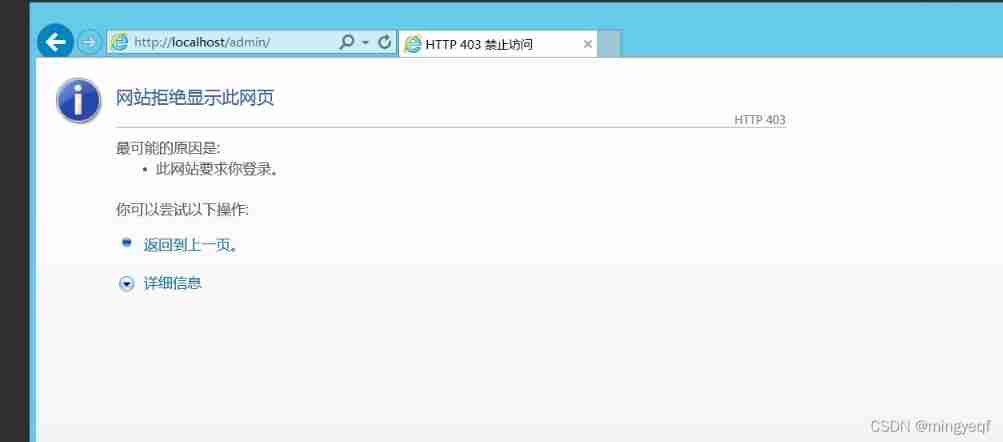
2.4 Apache HTTPD Newline parsing vulnerability (CVE-2017-15715)
1. Vulnerability description
Apache HTTPD Is a HTTP The server , It can go through mod_php To run the PHP Webpage . Its 2.4.0~2.4.29 There is
A parsing vulnerability , In parsing PHP when ,1.php\x0a Will be in accordance with PHP The suffix is parsed , This leads to bypassing the security policies of some servers
A little .
As you can see, you need to get the file name separately post One name Of , Because if you pass $_FILES[‘file’][‘name’] a
Take the file name , Will be able to \x0a Automatically remove , therefore $_FILES[‘file’][‘name’] Getting the file name in this way will not cause
This loophole
2. scope
apache :2.4.0~2.4.29 edition
3. Loophole recurrence
Apache HTTPD Newline parsing vulnerability (CVE-2017-15715)
Reference resources :https://blog.cfyqy.com/article/b0e821f4.html
Apache HTTPD Is a HTTP The server , It can go through mod_php To run the PHP Webpage . Its 2.4.0~2.4.29 There is a parsing vulnerability in the version , In parsing PHP when ,1.php\x0A Will be in accordance with PHP The suffix is parsed , This leads to bypassing some of the server's security policies .
Loophole recurrence
Upload a file named index.php The file of , Be intercepted , stay index.php Insert a \x0A( Be careful , It can't be \x0D\x0A, It can only be one \x0A), No longer intercept 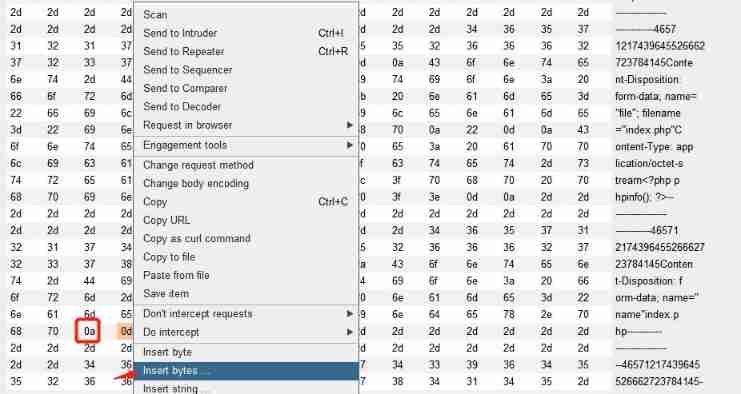
Visit the just uploaded /index.php%0a, It is found that... Can be successfully parsed , But this file is not php suffix , This indicates that the target has a parsing vulnerability :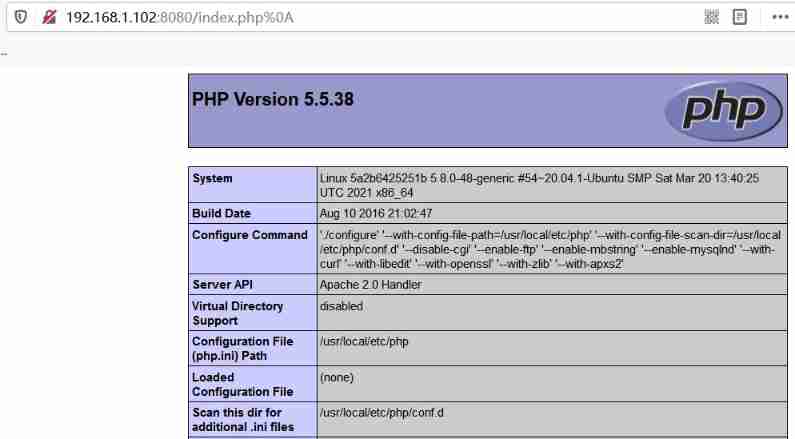
Repair suggestions
1. Upgrade to the latest version
2. Or rename the uploaded file to timestamp + random number +.jpg And disable the upload file directory execution
边栏推荐
- How Navicat imports MySQL scripts
- Brief explanation of instagram operation tips in 2022
- js对象获取属性的方法(.和[]方式)
- Typescript function definition
- JDBC学习笔记
- OpenJudge NOI 2.1 1749:数字方格
- Scala语言学习-08-抽象类
- Week6 weekly report
- Oracle database 11gr2 uses TDE transparent data encryption to report an error ora28353. If you run to close the wallet, you will report an error ora28365. If you run to open the wallet, you will repor
- Jerry's general penetration test - do data transmission with app Communication [article]
猜你喜欢
Related operations of Excel
Force buckle day31

Excel的相关操作

软件测试界的三无简历,企业拿什么来招聘你,石沉大海的简历

The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
![[online problem processing] how to kill the corresponding process when the MySQL table deadlock is caused by the code](/img/93/ec9de907cae4714038bb5f95aba52b.png)
[online problem processing] how to kill the corresponding process when the MySQL table deadlock is caused by the code
变量的命名规则十二条
![If Jerry's Bluetooth device wants to send data to the mobile phone, the mobile phone needs to open the notify channel first [article]](/img/d6/92ad1c6f84415de6ab0dfd16cd6073.png)
If Jerry's Bluetooth device wants to send data to the mobile phone, the mobile phone needs to open the notify channel first [article]

Multi attribute object detection on rare aircraft data sets: experimental process using yolov5
![Ble of Jerry [chapter]](/img/d8/d080ccaa4ee530ed21d62755808724.png)
Ble of Jerry [chapter]
随机推荐
jmeter性能测试步骤实战教程
Memory error during variable parameter overload
[MySQL learning notes 30] lock (non tutorial)
可变参数重载时的内存错误
软件测试界的三无简历,企业拿什么来招聘你,石沉大海的简历
Leecode-c language implementation -15 Sum of three ----- ideas to be improved
js对象获取属性的方法(.和[]方式)
Multi attribute object detection on rare aircraft data sets: experimental process using yolov5
OpenJudge NOI 2.1 1661:Bomb Game
Relevant introduction of clip image
Mise en œuvre du langage leecode - C - 15. Somme des trois chiffres - - - - - idées à améliorer
Simulation of Teman green interferometer based on MATLAB
Bloom taxonomy
Three treasures of leeks and Chinese men's football team
位运算异或
leecode-C語言實現-15. 三數之和------思路待改進版
Résumé de la structure du modèle synthétisable
Select all the lines with a symbol in word and change them to titles
GET/POST/PUT/PATCH/DELETE含义
Word setting directory