当前位置:网站首页>Mysql 45 study notes (twenty-four) MYSQL master-slave consistency
Mysql 45 study notes (twenty-four) MYSQL master-slave consistency
2022-07-31 03:18:00 【Kong Tom】
One. The basic principle of MySQL master and backup
Active-standby switching process:
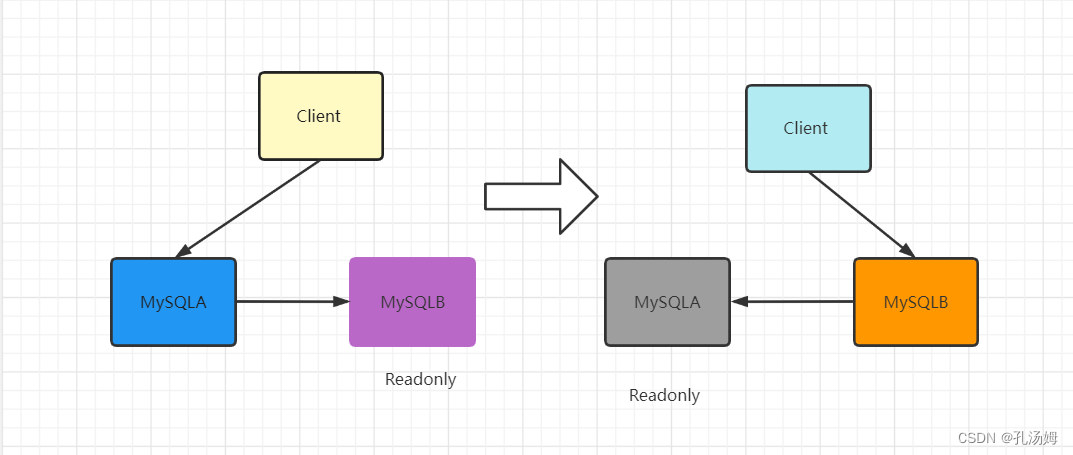
- The client's read and write directly access node A, and node B is the standby database of A. It just synchronizes the updates of A and executes it locally, so that the data of nodes B and A are kept the same
- Switch to state 2, the client read and write access to node B, and node A is the standby database of B
Set Node B (standby database) to readonly mode
- Some operational query statements will be placed in the backup database to check,Set read-only to prevent misuse;
- Prevent switching logic from bugs.Double writing occurs during the switching process, resulting in inconsistency between active and standby;
- readonly state, to determine the role of the node
Set standby to read-only, and follow The main library is kept up to date:
Because the readonly setting is invalid for super users, it is used for A thread that synchronizes updates has super permission.
Second, the UPDATE statement executes the steps of synchronizing to node B on node A:
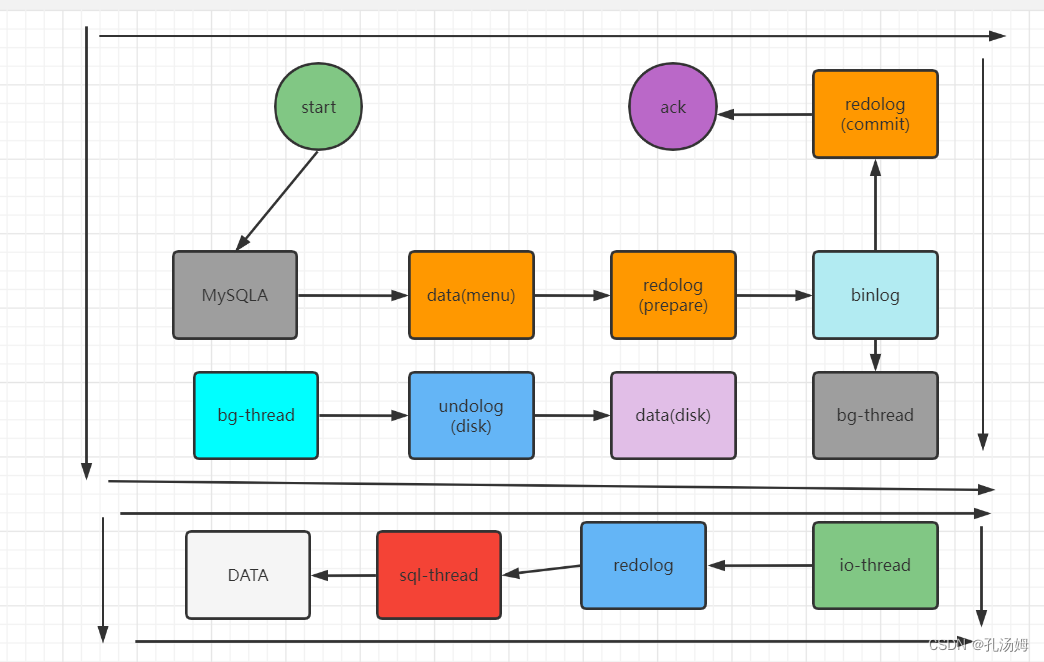
- After the main library receives the follow-up request from the client, it executes the update logic of the internal transaction and writes the binlog at the same time
- A long connection is maintained between the standby database B and the primary database A.There is a special thread inside the main database A to serve the long connection of the standby database B
Three. The complete process of transaction log synchronization:
- Use the change master command on the standby database B to set the IP of the primary database A.Port, username, password and where to start requesting binlog, this location contains filename and log offset
- Execute the start slave command on the standby database B. At this time, the standby database will start two threads, namely io_thread and sql_thread in the figure.Among them, io_thread is responsible for establishing a connection with the main library
- After verifying the user name and password, the main database A starts to read the binlog from the local according to the location passed by the standby database B, and sends it to B
- After the standby database B gets the binlog, it writes it to the local file, which is called the relay log
- sql_thread reads the secondary school log, parses the commands in the log, and executes them.
边栏推荐
猜你喜欢
随机推荐
Day32 LeetCode
JetPack component Databinding
els block to the left to move the conditional judgment
【编译原理】词法分析程序设计原理与实现
一份高质量的测试用例如何养成?
10. Redis implements likes (Set) and obtains the total number of likes
With 7 years of experience, how can functional test engineers improve their abilities step by step?
WebSocket Session is null
SIP协议标准和实现机制
5. SAP ABAP OData 服务如何支持 $filter (过滤)操作
浅识Flutter 基本组件之showDatePicker方法
The els block moves the boundary to the right, and accelerates downward.
Atomic operation CAS
Database implements distributed locks
Golang中的addressable
【C语言】求两个整数m和n的最大公因数和最小公倍数之和一般方法,经典解法
LeetCode每日一练 —— 138. 复制带随机指针的链表
TCP详解(一)
【AUTOSAR-RTE】-5-Explicit(显式)和Implicit(隐式) Sender-Receiver communication
品牌广告投放平台的中台化应用与实践