当前位置:网站首页>Redis problem (I) -- cache penetration, breakdown, avalanche
Redis problem (I) -- cache penetration, breakdown, avalanche
2022-06-12 06:19:00 【leo_ messi94】
Cache penetration
key The corresponding data does not exist in the data source , Each time for times key The request for could not be fetched from the cache , Requests are pushed to the data source , That could crush the data source .

For example, use a non-existent user id To get user information , There is no such data in the cache or database , Hackers may use this vulnerability to attack and overwhelm the database
The goal is to crash the server
What happened
- The pressure on the application server has increased
- redis Hit rate reduced
- Keep querying the database
The reason for this
- redis No data in , There's nothing in the database
- There are a lot of anomalies url visit
Solution
There must be no data that cannot be cached or queried , Because the cache is written passively on Miss , And for the sake of fault tolerance , If the data cannot be queried from the storage tier, the cache will not be written , This will cause the non-existent data to be queried by the storage layer every time it is requested , It loses the meaning of caching .
- Cache null values : If the data returned by a query is empty ( Whether or not the data does not exist ), We still cache this empty result , Setting the expiration time for empty results can be very short , Not more than 5 minute
- Set up an accessible list ( White list ): Use bitmaps Type defines a list of accessible , list id As bitmaps The offset , Every visit and bitmap Medium id Compare , If you visit id be not in bitmaps in , To intercept , Access not allowed .
- Use of Blum filter : The bloom filter is actually a very long binary vector ( Bitmap ) And a series of random mapping functions (hash function ). The bloom filter can retrieve whether an element is in a collection . Its advantage is that the space efficiency and query time are far more than the general algorithm , The disadvantage is that it has certain error recognition rate and deletion difficulty
- Real-time monitoring : If I found redis It's starting to drop , Need to check access objects and data , Cooperate with operation and maintenance personnel , You can set up a blacklist to restrict services
Cache breakdown
key The corresponding data exists , But in redis Medium overdue , At this time, if a large number of concurrent requests come , These requests are read from the database and set back to the cache , At this time, a large amount of concurrency may overwhelm the database .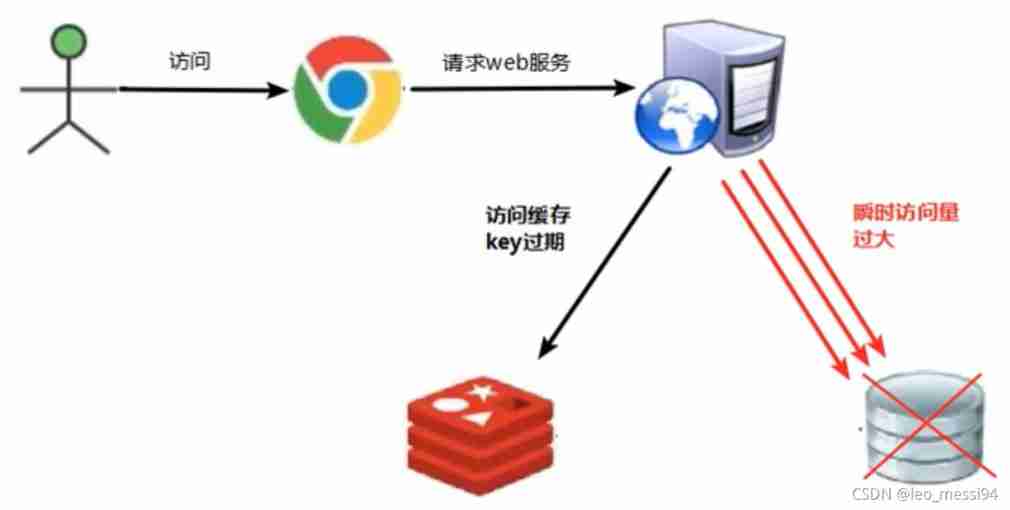
What happened
- Database access pressure increases instantaneously
- redis Not in a large number key Be overdue
- redis The normal operation
The reason for this
- redis One of them key Out of date , At the same time the key Be visited a lot
Solution
key It may be accessed at some point in time with super high concurrency , Is a very popular data . At this time, we need to consider a problem : The problem of cache breakdown .
- Preset hot data : stay redis Before the peak visit , Put some hot data into redis in , Increase these hot key Duration
- Timely adjustment : On site monitoring of those data is popular , Adjust expiration time in real time
- Using locks :
- When the cache fails ( The value is empty ), Not immediately load db
- First, use the caching tool to perform some operations with the return value of successful operations ( such as setnx)
Cache avalanche
key The corresponding data exists , But in redis Medium overdue , At this time, if a large number of concurrent requests come , These requests are read from the database and set back to the cache , At this time, a large amount of concurrency may overwhelm the database .
The difference between cache avalanche and cache breakdown is cache avalanche For many key cache .

What happened
The pressure on the database increases and the server crashes
The reason for this
In a very small period of time , A lot of key The centralized expiration of
terms of settlement
- Building a multi-level cache architecture :nginx cache +redis cache + Other caches
- Use locks or queues : Lock or queue is used to ensure that there will not be a large number of threads reading and writing to the database at one time , So as to avoid a large number of concurrent requests falling on the underlying storage system in case of failure . Not for high concurrency
边栏推荐
- JS预解析
- QT--实现TCP通信
- RNN implementation regression model
- 为什么数据库不使用二叉树、红黑树、B树、Hash表? 而是使用了B+树
- Leetcode-1706. Where does the club fall
- BRDF of directx11 advanced tutorial PBR (2)
- IBL of directx11 advanced tutorial PBR (3)
- Touch screen setting for win7 system dual screen extended display
- Directx11 advanced tutorial tiled based deffered shading
- Leetcode-1705. Maximum number of apples to eat
猜你喜欢

Directx11 advanced tutorial tiled based deffered shading

MNIST handwritten data recognition by CNN
Bert use

Jetson TX2 machine brushing jetpack4.2 (self test successful version)
Word2Vec
. Net core - pass Net core will Net to cross platform

EBook upload

勤于奋寻找联盟程序方法介绍

Cv2.fillpoly coco annotator segment coordinate conversion to mask image

Why doesn't the database use binary tree, red black tree, B tree and hash table? Instead, a b+ tree is used
随机推荐
CONDA create use virtual environment
夜神模拟器adb查看log
Explanation of sensor flicker/banding phenomenon
EBook list page
RNN implementation regression model
Leetcode 第 80 场双周赛题解
Pytorch implementation of regression model
Mastering UI development with unity
Nodemon cannot load the file c:\users\administrator\appdata\roaming\npm\nodemon PS1, because script execution is prohibited in this system
OverFeat: Integrated Recognition, Localization and Detection using Convolutional Networks
为什么联合索引是最左匹配原则?
The first principle of thinking method
Directx11 advanced tutorial cluster based deffered shading
Information content security experiment of Harbin Institute of Technology
(UE4 4.27) customize globalshader
Project technical structure
Video based fire smoke detection using robust AdaBoost
E-book analysis
Idea common configuration
Project progress on February 28, 2022