当前位置:网站首页>320. Energy Necklace (ring, interval DP)
320. Energy Necklace (ring, interval DP)
2022-07-03 22:08:00 【seez】

320. Energy necklace - AcWing Question bank
analysis : It can be regarded as a circular interval dp problem
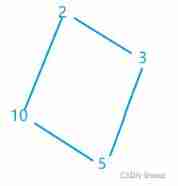 Altogether 4 A bead , There are four marks as shown in the figure , It can be merged to the end, leaving only 2 A sign , That is to say 1 A bead .
Altogether 4 A bead , There are four marks as shown in the figure , It can be merged to the end, leaving only 2 A sign , That is to say 1 A bead .
Then at least it needs 3 Tags can continue to merge , If it is less than three tags, there is no need to merge .

State means : All consolidation i~j A collection of tags
State calculation / Basis of division : according to i~j The marks in the middle can be divided into those that are neither heavy nor missing j-i-1 A collection of , because i,j It means the mark , Therefore, you cannot participate in the merger (dp[i][i] Not a bead , Do not participate in the operation , therefore dp[i][j],j>=i+1)
The recurrence formula is dp[i][k]+dp[k][j], Because the set before the breakpoint k As a tail mark , The latter set k As a header mark
- i+1 As a breakpoint , Merge dp[i][i+1],dp[i+1][j],dp[i][j]=dp[i][i+1]+dp[i+1][j]+w[i]*w[i+1]*w[j]
- ...
- j-1 As a breakpoint , Merge dp[i][j-1],dp[j-1][j],dp[i][j]=dp[i][j-1]+dp[j-1][j]+w[i]*w[j-1]*w[j]
Initialization and boundary are 0
Recursive method :
for(int len=1;len<=n+1;len++)// Because the right endpoint may be the starting point , therefore <=n+1
// Because the tail mark of the last bead is the first mark
for(int i=1;i+len-1<=2*n;i++)
{
...
}ac Code
#include <iostream>
#include <algorithm>
using namespace std;
const int N=205;
const int INF=0x3f3f3f3f;
int a[N];
int s[N];
int dp[N][N];
int main()
{
int n;
cin>>n;
for(int i=1;i<=n;i++)
cin>>a[i],a[n+i]=a[i];
for(int len=1;len<=n+1;len++)
for(int i=1;i+len-1<=2*n;i++)
{
int j=i+len-1;
for(int k=i+1;k<j;k++)
dp[i][j]=max(dp[i][j],dp[i][k]+dp[k][j]+a[i]*a[k]*a[j]);
}
int res=0;
for(int i=1;i<=n;i++)
res=max(res,dp[i][i+n]);
cout<<res;
}边栏推荐
- Covariance
- The latest analysis of crane driver (limited to bridge crane) in 2022 and the test questions and analysis of crane driver (limited to bridge crane)
- The 14th five year plan for the construction of Chinese Enterprise Universities and the feasibility study report on investment Ⓓ 2022 ~ 2028
- js demo 計算本年度還剩下多少天
- (5) User login - services and processes - History Du touch date stat CP
- Solve the problem that openocd fails to burn STM32 and cannot connect through SWD
- [secretly kill little partner pytorch20 days] - [day3] - [example of text data modeling process]
- Preliminary understanding of C program design
- Code in keil5 -- use the code formatting tool astyle (plug-in)
- Conditional statements of shell programming
猜你喜欢
Control loop of program (while loop)
How PHP adds two numbers

gslb(global server load balance)技術的一點理解

This time, thoroughly understand bidirectional data binding 01

On my first day at work, this API timeout optimization put me down!

Blue Bridge Cup Guoxin Changtian single chip microcomputer -- led lamp module (V)
2022 free examination questions for safety management personnel of hazardous chemical business units and reexamination examination for safety management personnel of hazardous chemical business units

Yiwen teaches you how to choose your own NFT trading market

Farmersworld farmers world, no faith, how to talk about success?
Team collaborative combat penetration tool CS artifact cobalt strike
随机推荐
The latest analysis of R1 quick opening pressure vessel operation in 2022 and the examination question bank of R1 quick opening pressure vessel operation
Global and Chinese market of wall mounted kiosks 2022-2028: Research Report on technology, participants, trends, market size and share
Code in keil5 -- use the code formatting tool astyle (plug-in)
China's TPMS industry demand forecast and future development trend analysis report Ⓐ 2022 ~ 2028
常用sql集合
Control loop of program (while loop)
Dynamic research and future planning analysis report of China's urban water supply industry Ⓝ 2022 ~ 2028
[SRS] build a specified version of SRS
使用dnSpy對無源碼EXE或DLL進行反編譯並且修改
[dynamic planning] counting garlic customers: the log of garlic King (the longest increasing public subsequence)
抓包整理外篇——————autoResponder、composer 、statistics [ 三]
内存分析器 (MAT)
Great gods, I want to send two broadcast streams: 1. Load basic data from MySQL and 2. Load changes in basic data from Kafka
Report on the development status and investment planning trends of China's data center industry Ⓡ 2022 ~ 2028
Farmersworld farmers world, no faith, how to talk about success?
Luogu deep foundation part 1 Introduction to language Chapter 6 string and file operation
gslb(global server load balance)技术的一点理解
Electronic tube: Literature Research on basic characteristics of 6j1
China HDI market production and marketing demand and investment forecast analysis report Ⓢ 2022 ~ 2028
treevalue——Master Nested Data Like Tensor