边栏推荐
- Unity addressable batch management
- Unity Addressable批量管理
- 故障:Outlook 收发邮件时的 0x800CCC1A 错误
- 420 sequence traversal of binary tree 2 (429. sequence traversal of n-ary tree, 515. find the maximum value in each tree row, 116. fill in the next right node pointer of each node, 104. maximum depth
- Find the nearest common ancestor (Sword finger offer) of two nodes in the binary tree (search tree)
- How to calculate the D value and W value of statistics in normality test?
- NIPS 2014 | Two-Stream Convolutional Networks for Action Recognition in Videos 阅读笔记
- 4 raisons inconnues d'utiliser le "déplacement sûr à gauche"
- The era of enterprise full cloud -- the future of cloud database
- Use pytorch to build mobilenetv2 and learn and train based on migration
猜你喜欢
Index analysis of DEMATEL model

What are the indicators of DEA?

How to analyze the grey prediction model?

Stack awareness - stack overflow instance (ret2libc)

Daily question brushing record (III)
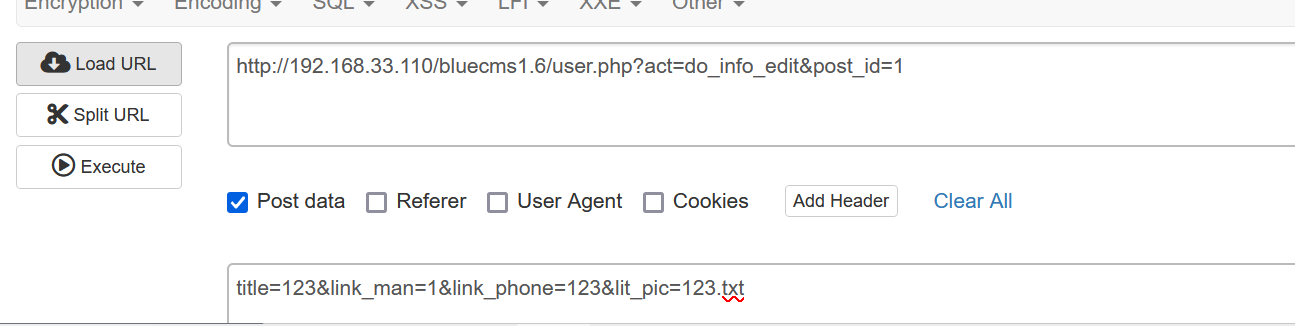
Bluecmsv1.6- code audit

First experience Amazon Neptune, a fully managed map database

Scanpy (VII) spatial data analysis based on scanorama integrated scrna seq

Wechat applet opening customer service message function development

DNS protocol and its complete DNS query process
随机推荐
Getting to know the generation confrontation network (11) -- using pytoch to build wgan to generate handwritten digits
First experience Amazon Neptune, a fully managed map database
Unity Addressable批量管理
Stm32cubemx learning (5) input capture experiment
Network model -- OSI model and tcp/ip model
Static web server
4 raisons inconnues d'utiliser le "déplacement sûr à gauche"
堆栈认知——栈溢出实例(ret2libc)
Sword finger offer (simple level)
Is it safe to open an account online? Xiaobai asks for guidance
Scanpy (VII) spatial data analysis based on scanorama integrated scrna seq
4個不可不知的采用“安全左移”的理由
软件测试月薪10K如何涨到30K,只有自动化测试能做到
June training (day 25) - tree array
Nips 2014 | two stream revolutionary networks for action recognition in videos reading notes
Go language learning tutorial (13)
What are the indicators of VIKOR compromise?
Quickly build a real-time face mask detection system in five minutes (opencv+paddlehub with source code)
Hyper-v:Hyper-v 第 1 代或第 2 代虚拟机
Bluecmsv1.6-代码审计
