当前位置:网站首页>Explanation on the use of password profiteering cracking tool Hydra
Explanation on the use of password profiteering cracking tool Hydra
2022-06-30 08:57:00 【huwei0814】
Contents of this article
Hydra summary

Hydra Is a famous hacker organization THC Developed Open source Brute force tools , Support online password cracking for most protocols , It's network security · Penetration test A necessary tool .
Installation method :Kali Bring it with you hydra, Search keywords directly .
Parameters,
stay Kali From the command line of hydra -h You can view it hydra All parameters of 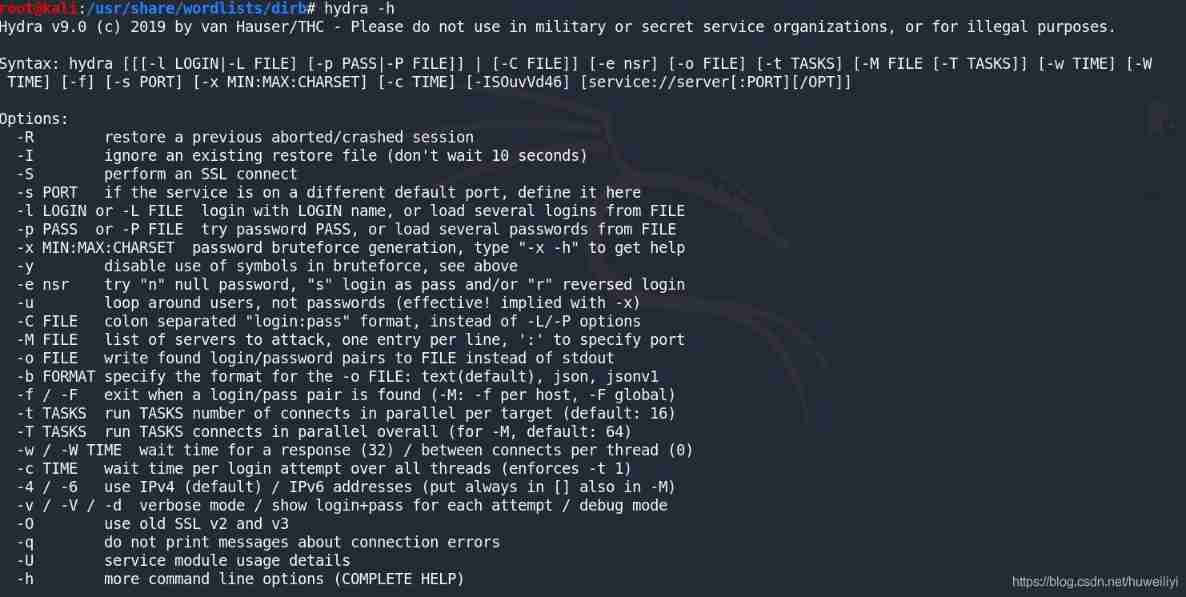

See the following table for the specific parameter meanings :
| Parameter name | Parameter meaning |
|---|---|
| -l : | Specify users to crack , Crack for specific users |
| -L | Specify the user name dictionary |
| -p | A lowercase letter , Specify password cracking , To use less , It's usually a password dictionary |
| -P | Capitalization , Specify a password dictionary |
| -R | Continue to crack from the last progress |
| -S | Capitalization , use SSL link |
| -s | A lowercase letter , You can use this parameter to specify a non default port |
| -e | Optional options ,n: Empty password test ,s: Use designated users and password Heuristics |
| -t | Number of threads running at the same time , The default is 16 |
| -C | Use colon split format , for example “ Login name : password ” Instead of -L/-P Parameters |
| -M | Specify the target list file line by line |
| -o | Specify the result output file |
| -f | In the use of -M After the parameters , Stop cracking when finding the first pair of login names or passwords |
| -w | Set the maximum timeout time , Unit second , The default is 30s |
| -v / -V | Show detailed process |
| server | The goal is ip |
| service | Specify the service name , Supported services and protocols |
Usage method
stay hydra In the help command of, we provide some examples as follows
hydra -l user -P passlist.txt ftp://192.168.0.1
hydra -L userlist.txt -p defaultpw imap://192.168.0.1/PLAIN
hydra -C defaults.txt -6 pop3s://[2001:db8::1]:143/TLS:DIGEST-MD5
hydra -l admin -p password ftp://[192.168.0.0/24]/
hydra -L logins.txt -P pws.txt -M targets.txt ssh
The basic usage of these commands is very similar , Let's take the first command as an example , In general, it can be divided into three parts , namely user name , password , and agreement 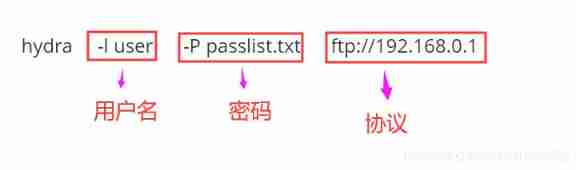
We use a OWASP The machine is used as the attacked machine to demonstrate several common protocol cracking methods
OWASP Environment building portal : OWASP Broken Web Apps Penetration testing environment setup and installation tutorial
Crack SSH
We use the following command
hydra -L user.txt -P passwd.txt -o ssh.txt -vV -t ip ssh -s 22
-L Specify the user dictionary file
-P Specifies the password dictionary file
-o Output success to ssh.txt file
-vV Show details
-s Specify another port If you want to modify the default 22 port , have access to -s Parameters
First, in the /test Create a new folder named userlist.txt The file of , And input some test data into it 
stay /test Create a new folder named passwdlist.txt The file of , And input some test data into it 
Enter the following command to start cracking
hydra -L /test/userlist.txt -P passwdlist.text -vV -o ssh.txt -t 5
192.168.0.129 ssh
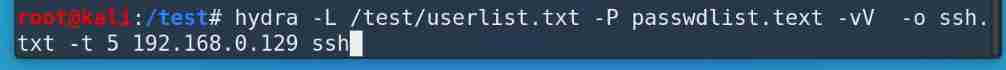

From the output, we can see that there are 1 Group value successfully cracked 
From the previous print, you can also see that the group value is rootowaspbwa
You can also find the cracked user name by viewing the saved directory file 
Dictionary recommendation
Kali Bring your own password dictionary
The most important condition for the success of brute force cracking is to have a strong password dictionary !Kali Some dictionaries are included by default , stay /usr/share/wordlists Under the table of contents
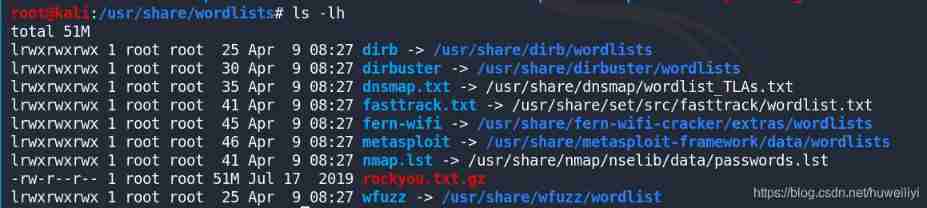
dirb Folder

The meaning of the dictionary file in this directory is as follows
- big.txt # A big dictionary
- small.txt # A little dictionary
- catala.txt # Project configuration Dictionary
- common.txt # Public Dictionary
- euskera.txt # Data catalog Dictionary
- extensions_common.txt # Common file extension Dictionary
- indexes.txt # Home page dictionary
- mutations_common.txt # Backup extension
- spanish.txt # Method name or Library Directory
- others # Extended Directory , Default user name, etc
- stress # Pressure test
- vulns # Vulnerability testing
28G Big dictionary
Whether the password can be cracked depends on whether the password dictionary is strong enough , Recommend a 28G Big dictionary , Compress 27M Less than , You know 
Portal :28G Super large password dictionary
边栏推荐
- Pytorch BERT
- Evaluation standard for audio signal quality of intelligent speakers
- Opencv learning notes -day1 (image reading display imread, imshow, namedwindow)
- Mmdet line by line deltaxywhbboxcoder
- [untitled]
- Use Huawei performance management service to configure the sampling rate on demand
- Flink 数据偶尔数据积压导致checkpoint失败
- Summary of common pytoch APIs
- Interpretation of orientedrcnn papers
- 云服务器上部署仿牛客网项目
猜你喜欢

Opencv learning notes -day4 image pixel reading and writing operations (array traversal and pointer traversal implementation, uchar vec3b data type and mat class functions mat:: at(), mat:: ptr())

codeforces每日5题(均1700)-第三天

Redis design and Implementation (IV) | master-slave replication

Gilbert Strang's course notes on linear algebra - Lesson 4

Redis design and Implementation (III) | interaction between server and client (event IO model)

Mmcv expanding CUDA operator beginner level chapter

Redis design and Implementation (VI) | cluster (sharding)

Mmdet line by line deltaxywhbboxcoder
![[untitled]](/img/45/368c41a74bf0738369c58c5963fca0.jpg)
[untitled]

Summary of common pytoch APIs
随机推荐
Flink SQL custom connector
Treatment process record of Union Medical College Hospital (Dongdan hospital area)
Redis design and Implementation (VI) | cluster (sharding)
Is it safe to open an account? How can anyone say that it is not reliable.
Opencv learning notes -day13 pixel value statistics calculation of maximum and minimum values, average values and standard deviations (use of minmaxloc() and meanstddev() functions)
Occasionally, Flink data is overstocked, resulting in checkpoint failure
Maxiouassigner of mmdet line by line interpretation
Flink 数据偶尔数据积压导致checkpoint失败
[kotlin collaboration process] complete the advanced kotlin collaboration process
Is the reverse repurchase of treasury bonds absolutely safe? How to open an account online
维基媒体基金会公布新商业产品“维基媒体企业”首批客户
el-input 限制只能输数字
Opencv learning notes -day 11 (split() channel separation function and merge() channel merge function)
Circuit analysis of current probe
[untitled]
Esp32 things (V): analysis of common API of esp32 of Swiss Army knife
[untitled]
C#访问SQL Server数据库两种方式的比较(SqlDataReader vs SqlDataAdapter)
Esp32 (6): Bluetooth and WiFi functions for function development
A troubleshooting of CPU bottom falling