当前位置:网站首页>Principle of TCP reset attack
Principle of TCP reset attack
2022-06-26 15:00:00 【Hua Weiyun】
TCP Reset attack principle
TCP
TCP Connection oriented transport layer protocol , The application is using TCP Before the agreement , You have to set up TCP Connect . After the transmission of data , The established... Must be released TCP Connect .TCP It's point-to-point communication , Provide reliable delivery , adopt TCP Connect the transmitted data , No mistakes , No loss , No repetition , And arrive in order .TCP Provide full duplex communication ,TCP Both ends of the connection are provided with send cache and receive cache , Used to temporarily store data for two-way communication , such TCP Send data when appropriate , The application process reads the data in the cache when appropriate .TCP Is oriented to a byte stream ,TCP Treat the data given by the application as a series of unstructured byte streams , however TCP The data unit transmitted is the message segment .
TCP message
One TCP The message segment is divided into two parts: the first part and the data part , There is a reset in the head RST(ReSet) Field , It is the reset bit , When RST=1 Time indicates TCP There was a serious error in the connection , Connection must be released , Then reestablish the transport connection .RST Set to 1 Used to reject an illegal segment or to refuse to open a connection .
Reset attack
RST An attack is a server A and B Established TCP Connect ,C Forged a TCP Send the bag to B, send B Abnormal disconnection and A Between TCP Connect .
When the server C Disguised as a A My bag , send out RST package ,B Will discard and A Data in the buffer , Force the connection off .
When the server C Disguised as a A My bag , send out SYN package , The server B Create a new connection when the connection is normal ,B Active direction A send out RST package , And forcibly close the connection on the server .
This is the specific implementation method of reset attack .
summary
To successfully implement the attack , You need to set the source and destination correctly IP Address 、 Port number and serial number , Putting the attacker and the victim in the same network can reduce the difficulty of guessing the serial number .
️ Thank you for your
If you think this is helpful for you :
- Welcome to follow me ️, give the thumbs-up , Comment on , forward
- Focus on
Panpan small class, Push good articles for you regularly , There are also group chat and irregular lottery activities , You can say what you want , Communicate with the great gods , Learning together .
边栏推荐
- 获取两个dataframe的交并差集
- 一个快速切换一个底层实现的思路分享
- IP certificate application process of sectigo
- [async/await] - the final solution of asynchronous programming
- 备战数学建模31-数据插值与曲线拟合3
- TS common data types summary
- Informatics Olympiad 1405: sum and product of prime numbers (thinking problem)
- R language GLM function logistic regression model, using epidisplay package logistic The display function obtains the summary statistical information of the model (initial and adjusted odds ratio and
- Redis集群消息
- The annual salary of 500000 is one line, and the annual salary of 1million is another line
猜你喜欢
【soloπ】adb连接单个多个手机

Program analysis and Optimization - 8 register allocation

【使用yarn运行报错】The engine “node“ is incompatible with this module.

关于 selenium.common.exceptions.WebDriverException: Message: An unknown server-side error 解决方案(已解决)

Bank of Beijing x Huawei: network intelligent operation and maintenance tamps the base of digital transformation service
![[solo π] ADB connects multiple mobile phones](/img/44/4bd88725434fb67c9237645f024071.png)
[solo π] ADB connects multiple mobile phones

使用 Abp.Zero 搭建第三方登录模块(二):服务端开发

Common operation and Principle Exploration of stream
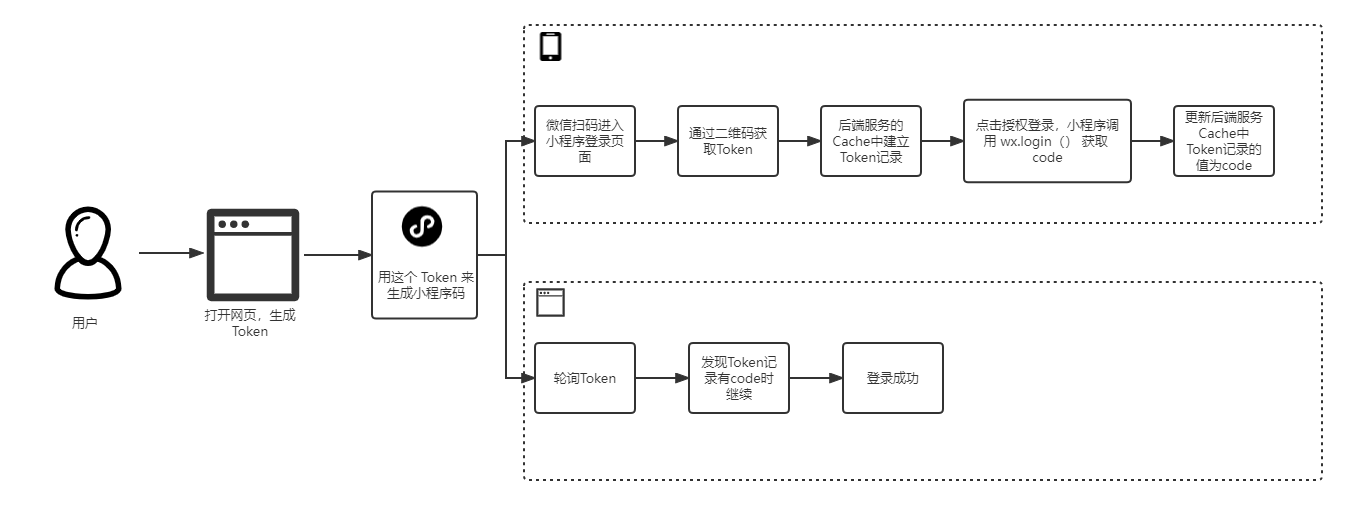
使用 Abp.Zero 搭建第三方登录模块(一):原理篇
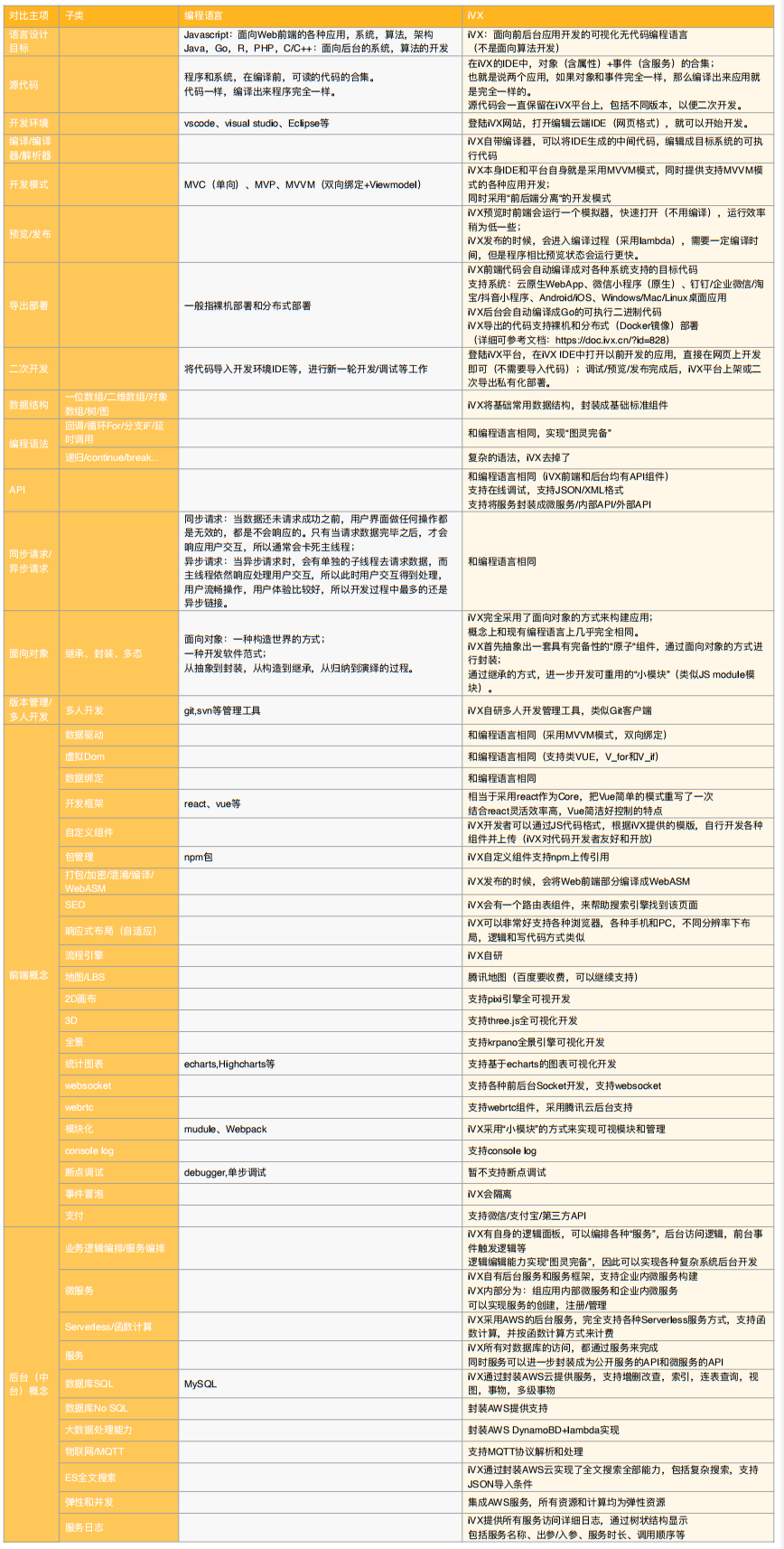
【雲原生】 ”人人皆可“ 編程的無代碼 iVX 編輯器
随机推荐
Combat readiness mathematical modeling 32 correlation analysis 2
Excel-vba quick start (II. Condition judgment and circulation)
Pytorch深度学习代码技巧
Is it safe to open an online stock account? Somebody give me an answer
[cloud native] codeless IVX editor programmable by "everyone"
同花顺注册开户安全吗,有没有什么风险?
R language dplyr package bind_ The rows function merges the rows of the two dataframes vertically. The final number of rows is the sum of the rows of the original two dataframes (combine data frames)
Transformers datacollatorwithpadding class
Equation derivation: second order active bandpass filter design! (download: Tutorial + schematic + Video + code)
R语言epiDisplay包的dotplot函数通过点图的形式可视化不同区间数据点的频率、使用by参数指定分组参数可视化不同分组的点图分布、使用cex.X.axis参数指定X轴轴刻度数值标签字体的大小
Solution to the upper limit of TeamViewer display devices
券商经理给的开户二维码安全吗?找谁可以开户啊?
Is it safe for flush to register and open an account? Is there any risk?
Kubernetes的pod
关于 selenium.common.exceptions.WebDriverException: Message: An unknown server-side error 解决方案(已解决)
印尼投资部长:鸿海考虑在其新首都建立电动公交系统、城市物联网
Sharing ideas for a quick switch to an underlying implementation
One copy ten, CVPR oral was accused of plagiarizing a lot, and it was exposed on the last day of the conference!
集群中命令的执行过程
Use abp Zero builds a third-party login module (II): server development