当前位置:网站首页>Commonly used security penetration testing tools (penetration testing tools)
Commonly used security penetration testing tools (penetration testing tools)
2022-07-31 20:10:00 【Full stack programmer webmaster】
Hello everyone, meet again, I'm your friend Quanstack Jun.
Application security is not new, but it is rapidly growing in demand, complexity and depth.With cybercrime increasing by nearly 600% since the outbreak, more and more SaaS businesses are scrambling to protect their applications.Even those systems running the latest endpoint protection face significant vulnerabilities.
However, the next question is: Even with these security precautions, can you protect yourself from cyberattacks?
The answer lies in application securitytesting solution that proactively tests your code for bugs, critical vulnerabilities, and areas that need overall improvement.The following are some common tests.
- Penetration Testing
- Deployment Automationtools such as SAST, DAST, RAST and IAST
When comparing test tools, keep the following in mind:
Depth and breadth of testing Frequency of deployment Degree of manual effort involved Cost Ease of implementation Ease of maintenance Applicable to your business logic
Introduction to Penetration Testing
Penetration testing, also known as "penetration testing" or "ethical hacking," is an authorized test used to test the security resiliency of software or network systems.As one of the commonly used testing options, penetration testing usually involves experienced security penetration testers who perform tests manually according to a set of predefined security testing plans.
The biggest difference between penetration testing and hacking is that penetration testing is authorized by customers, using controllable, non-destructive methods and means to find weaknesses in targets and network equipment, helping managers to know the problems faced by their own networks, and at the same timeProvide security hardening suggestions to help customers improve system security.
Over the past decade, penetration testing has been widely used as a prerequisite for numerous compliance standards and regulations such as SOCII, OWASP Top 10, and PCI-DSS.
Using automated security testing tools
Currently, most companies opt to use a security inspection tool, sometimes considered more scalable and cheaper, and sometimes considered the easiest way to "check" the security box.
Dynamic Analytical Security Testing (DAST), Interactive Analytical Security Testing (IAST), and Runtime Application Security Protection (RASP) are all different security testing tools.The use of these tools is an important part of a complete application security program, while also complementing manual testing such as penetration testing.
These security testing tools help developers improve development efficiency, while also providing security testing at a certain scale.For example, if you have hundreds of applications, these tools can provide advanced test coverage for all of your applications faster than manual testing.Another example of using these tools is if you need to do basic security checks on every PullRequest push.
In addition, these security testing tools are mostly used in the software development life cycle, which also means that security risks can be discovered in time during the development process, and vulnerabilities can be fixed in the first time.Compared with the completion of the later security testing of the software, it can be said to be prepared for a rainy day.
Conclusion
Security and compliance continue to be key requirements for vendor-delivered software. To meet the growing need for application security proofs, it is recommended that enterprises combine their business goals, budget, scale, and number of applications with aChoose to use the above-mentioned test methods and security detection tools.
Publisher: Full-stack programmer, please indicate the source: https://javaforall.cn/127867.htmlOriginal link: https://javaforall.cn
边栏推荐
- Mobile web development 02
- "The core concept of" image classification and target detection in the positive and negative samples and understanding architecture
- 【Yugong Series】July 2022 Go Teaching Course 023-List of Go Containers
- OSPFv3的基本配置
- leetcode: 6135. The longest ring in the graph [inward base ring tree + longest ring board + timestamp]
- 性能优化:记一次树的搜索接口优化思路
- Count characters in UTF-8 string function
- leetcode 665. Non-decreasing Array 非递减数列(中等)
- 【Yugong Series】July 2022 Go Teaching Course 025-Recursive Function
- [Open class preview]: Research and application of super-resolution technology in the field of video image quality enhancement
猜你喜欢

Short-circuit characteristics and protection of SiC MOSFETs

Socket回顾与I/0模型
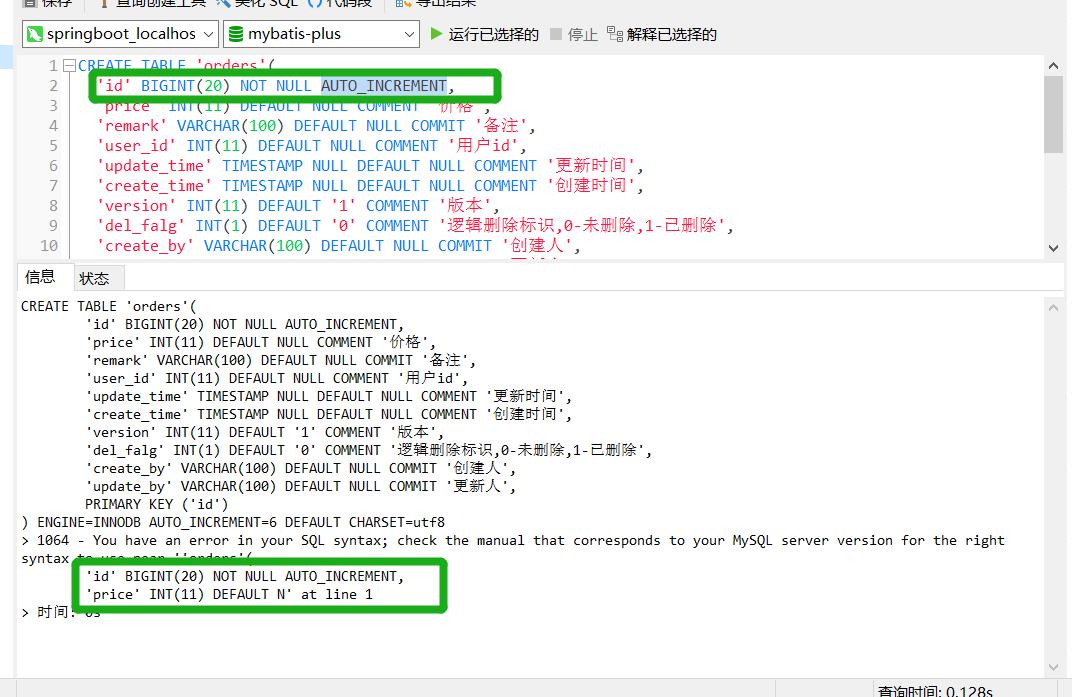
What's wrong with the sql syntax in my sql

请问我的这段sql中sql语法哪里出了错

Redis Overview: Talk to the interviewer all night long about Redis caching, persistence, elimination mechanism, sentinel, and the underlying principles of clusters!...
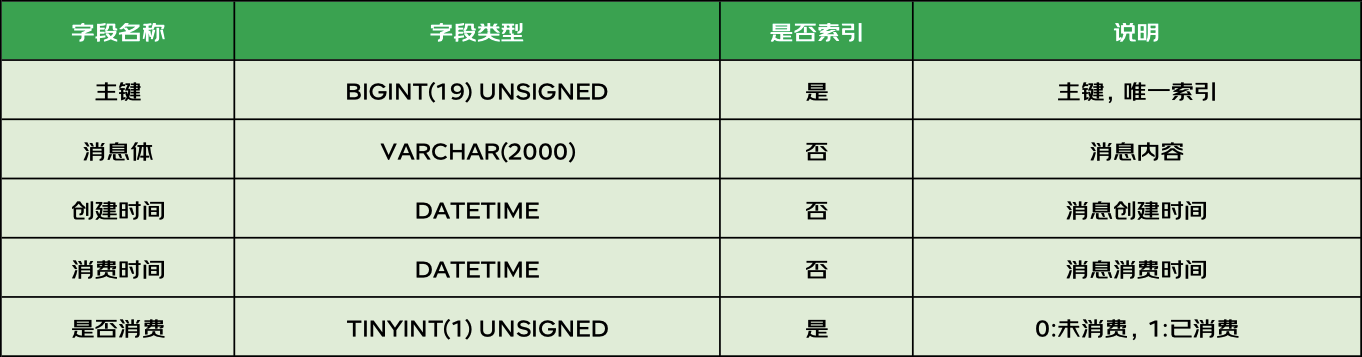
架构实战营模块 8 作业

Shell 脚本 快速入门到实战 -02
Implementing a Simple Framework for Managing Object Information Using Reflection

Count characters in UTF-8 string function

MySQL---子查询
随机推荐
ResNet的基础:残差块的原理
中文编码的设置与action方法的返回值
高通cDSP简单编程例子(实现查询高通cDSP使用率、签名),RK3588 npu使用率查询
MySQL - single function
leetcode: 6135. The longest ring in the graph [inward base ring tree + longest ring board + timestamp]
Book of the Month (202207): The Definitive Guide to Swift Programming
MySQL---多表查询
1161. Maximum Sum of Elements in Layer: Hierarchical Traversal Application Problems
Made with Flutter and Firebase!counter application
基于WPF重复造轮子,写一款数据库文档管理工具(一)
leetcode:6135. 图中的最长环【内向基环树 + 最长环板子 + 时间戳】
【Yugong Series】July 2022 Go Teaching Course 023-List of Go Containers
有一说一,外包公司到底值不值得去?
Routing interception of WeChat applet
全网一触即发,自媒体人的内容分发全能助手——融媒宝
嵌入式开发没有激情了,正常吗?
Basics of ResNet: Principles of Residual Blocks
全平台GPU通用AI视频补帧超分教程
请问我的这段sql中sql语法哪里出了错
Apache EventMesh 分布式事件驱动多运行时