当前位置:网站首页>The realization of online Fox game server room configuration battle engagement customization function
The realization of online Fox game server room configuration battle engagement customization function
2022-06-11 06:39:00 【RemoteDev】
Final effect :
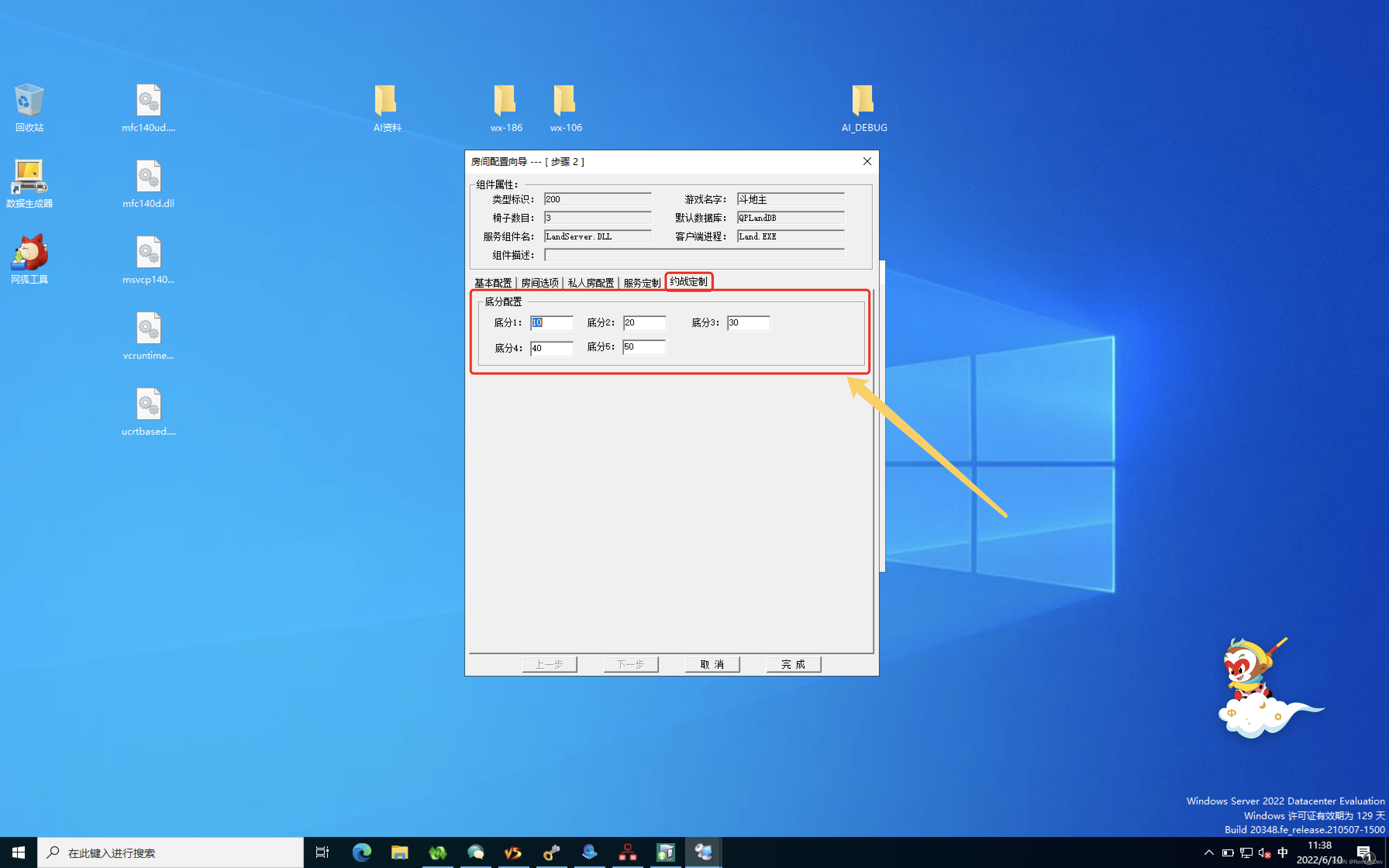
1. Create dialog resources and modify ID by IDD_PERSONAL_RULE, Then design the effect as shown in the figure below
 2. Add dialog resource processing class DlgPersonalRule
2. Add dialog resource processing class DlgPersonalRule

3. Declare structure variable and control data interaction function and rule structure operation function
// Configuration structure
struct tagPersonalRule
{
byte cbSpecialRule; // Are there any special rules
tagPersonalGeneralRule personalRule[PERSONAL_OPTION_COUNT]; // Configuration parameters
int nCellScore[CELLSCORE_COUNT]; // Initial integral
tagPersonalRule()
{
memset(nCellScore, 0, sizeof(nCellScore));
}
};
4. Initialization class
边栏推荐
- fatal: refusing to merge unrelated histories
- On cursor in MySQL
- JS implementation of graphic merging and sorting process [source code attached]
- [TP5 online export picture generation excel detailed explanation example]
- arguments......
- CCS安装编译器的方法
- Differences between FindIndex and indexof
- Convert text label of dataset to digital label
- A multi classification model suitable for discrete value classification -- softmax regression
- Convert multiple pictures into one NPY file storage
猜你喜欢

Teach everyone how to implement an electronic signature

Jenkins user rights management

617. merge binary tree

Eureka cluster setup
![[]==![]](/img/65/ab724c74b080da319ed5c01c93fdb7.png)
[]==![]

235-二叉搜索树的最近公共祖先
NPM upgrade: unable to load file c:\users\administrator\appdata\roaming\npm\npm-upgrade ps1

解决ffmpeg獲取AAC音頻文件duration不准

Verilog realizes binocular camera image data acquisition and Modelsim simulation, and finally matlab performs image display
![Illustration of JS implementation from insertion sort to binary insertion sort [with source code]](/img/e5/1956af15712ac3e89302d7dd73f403.jpg)
Illustration of JS implementation from insertion sort to binary insertion sort [with source code]
随机推荐
The difference between call and apply and bind
go的fmt包使用和字符串的格式化
Jenkins voucher management
347. top k high frequency elements
Résoudre le problème de la durée inexacte du fichier audio AAC obtenu par ffmpeg
不引入第三个变量,交换两个值
How exactly does instanceof judge the reference data type!
A piece of code has been refactored six times by the boss, and my mind is broken
JS implementation of Hill sort of graphic insertion sort [with source code]
Shuffleerror:error in shuffle in fetcher solution
解决ffmpeg獲取AAC音頻文件duration不准
563. slope of binary tree
arguments......
617. 合并二叉树
The classification effect of converting video classification data set to picture classification data set on vgg16
Text overflow failure
必读1:格局越大的人,越懂得说话
FPGA interview topic notes (I) - FPGA development process, metastable state and competitive risk, build and hold time, asynchronous FIFO depth, etc
Wechat applet (authorized login) (not recommended, click the home page to view the updated authorized login)
Who is stronger, zip or 7-Zip, and how to choose?