当前位置:网站首页>[redis notes] compressed list (ziplist)
[redis notes] compressed list (ziplist)
2022-07-02 23:11:00 【Twilight_ years】
Definition of compressed list :
Compressed lists are developed to save memory , It is a sequential data structure composed of a series of special coded continuous memory blocks .
Structure of compressed list :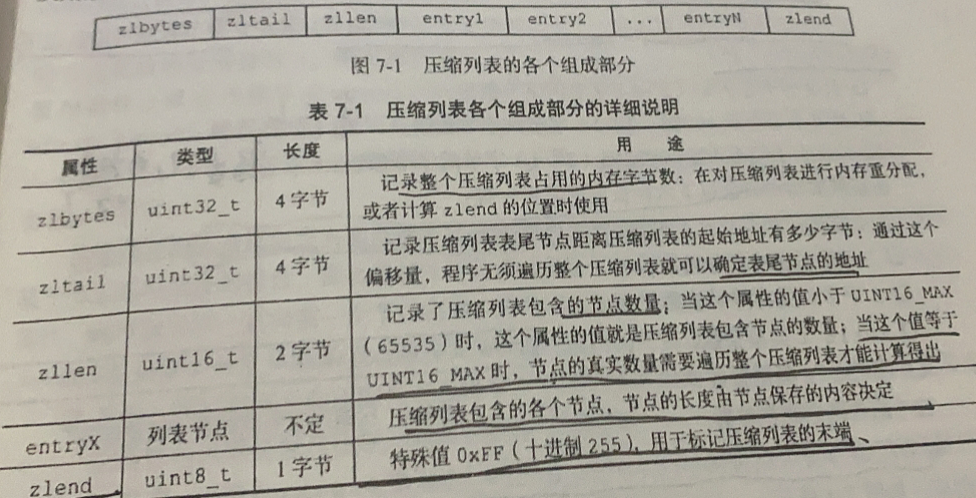
Structure of compressed list nodes :

previous_entry_length: Record the length of the previous node in the compressed list

according to previous_entry_length, The program can operate by pointer , Calculate the starting address of the previous node according to the starting address of the current node , So as to realize traversal from the end of the table to the header .
encoding:
Record node's content The type and length of data saved by attributes


content:
Responsible for saving the value of the node , The node value can be an array of bytes or an integer , The type and length of the value are determined by the encoding Attribute decision .
Chain update :
Add or remove nodes , If the length is greater than 254 byte , It may lead to previous_entry_length Size needs to be from 1 Bytes changed to 5 byte , This may cause subsequent nodes previous_entry_length Everything has changed , under these circumstances , Continuous space expansion operations are required .
explain :
(1) The worst time complexity of space allocation O(N), The worst time complexity of chain update O(N Fang )
(2) The situation is rare and as long as the number of nodes is small , No impact on performance .
边栏推荐
- 成功改变splunk 默认URL root path
- LeetCode 968. 监控二叉树
- The motivation of AES Advanced Encryption Protocol
- MySQL reset password, forget password, reset root password, reset MySQL password
- [Solved] Splunk: Cannot get username when all users are selected“
- Qt QScrollArea
- Solving ordinary differential equations with MATLAB
- 密码技术---密钥和SSL/TLS
- Motivation du Protocole de chiffrement avancé AES
- Call vs2015 with MATLAB to compile vs Project
猜你喜欢

【喜欢的诗词】好了歌
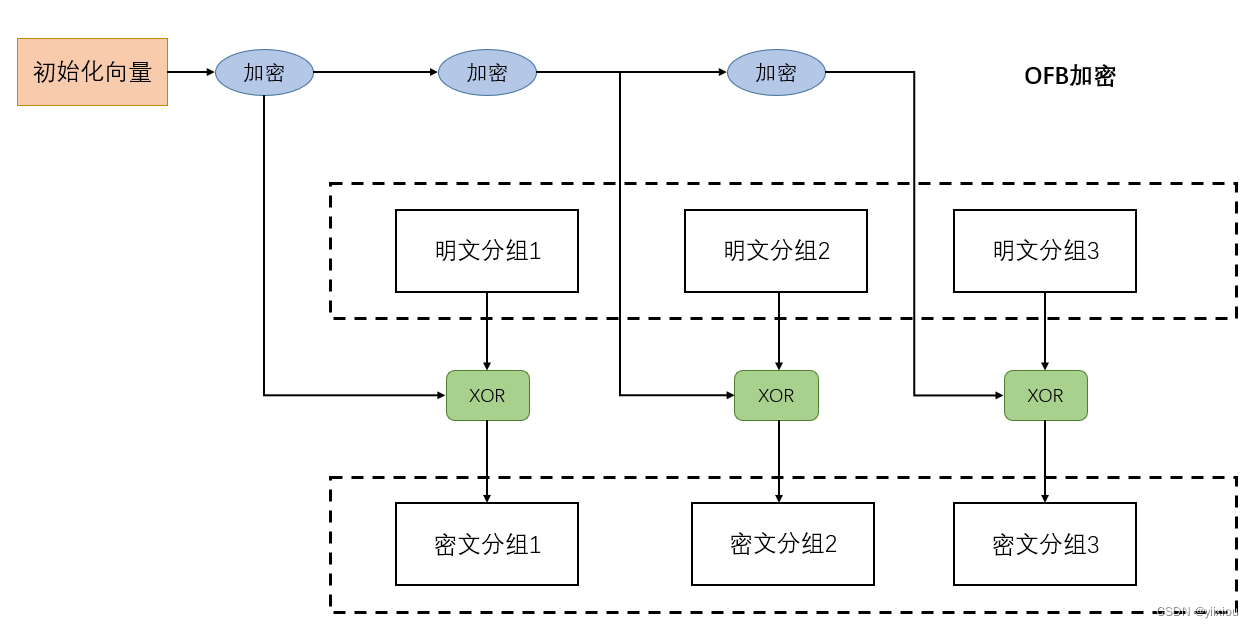
密码技术---分组密码的模式
PotPlayer设置最小化的快捷键

Typical case of data annotation: how does jinglianwen technology help enterprises build data solutions

AES高级加密协议的动机阐述
![[NPUCTF2020]ezlogin xPATH注入](/img/6e/dac4dfa0970829775084bada740542.png)
[NPUCTF2020]ezlogin xPATH注入
設置單擊右鍵可以選擇用VS Code打開文件

The first batch of Tencent cloud completed the first cloud native security maturity assessment in China

Redis 过期策略+conf 记录

Methods to solve the tampering of Chrome browser and edeg browser homepage
随机推荐
详解Promise使用
[Solved] Splunk: Cannot get username when all users are selected“
门牌制作 C语言
golang中new与make的区别
Methods to solve the tampering of Chrome browser and edeg browser homepage
LC173. 二叉搜索树迭代器
Jericho's thimble reaction when directly touching the prototype is abnormal [chapter]
Boot actuator - Prometheus use
PMP project integration management
Antd component upload uploads xlsx files and reads the contents of the files
Brief introduction of emotional dialogue recognition and generation
程序员版本的八荣八耻~
1px pixel compatibility of mobile terminal, 1px border
Potplayer set minimized shortcut keys
Go language sqlx library operation SQLite3 database addition, deletion, modification and query
AES高級加密協議的動機闡述
Configuration clic droit pour choisir d'ouvrir le fichier avec vs Code
Jerry's built-in short press and long press, no matter how long it is, it is a short press [chapter]
中国信通院、清华大学、腾讯安全,云原生安全产学研用强强联合!
潘多拉 IOT 开发板学习(HAL 库)—— 实验4 串口通讯实验(学习笔记)