当前位置:网站首页>Cryptography -- the mode of block cipher
Cryptography -- the mode of block cipher
2022-07-02 23:08:00 【yiixiou】
Block ciphers and stream ciphers
Cryptographic algorithms can be divided into block ciphers and stream ciphers .
- Group password : A class of cryptographic algorithms that can only process a piece of data of a specific length at a time . The number of bits of a packet is called the packet length .DES The packet length of is 64 The bit ,DES You can only encrypt at one time 64 The plaintext of bits , And generate 64 Ciphertext of bit . Treat in groups , There is no need to record the progress of encryption through internal state .
- Stream code : A class of cryptographic algorithms for continuous data processing . Generally speaking, with 1 The bit 、8 Bit or 32 Encryption and decryption in bits . Encrypt and decrypt a string of data streams , Need to maintain internal state . One time password belongs to stream password .
Block cipher mode
Due to the limited processing length of block cipher , So when processing long plaintext data , The block cipher algorithm needs to be iterated , The iterative method is called block cipher pattern . The main models are :
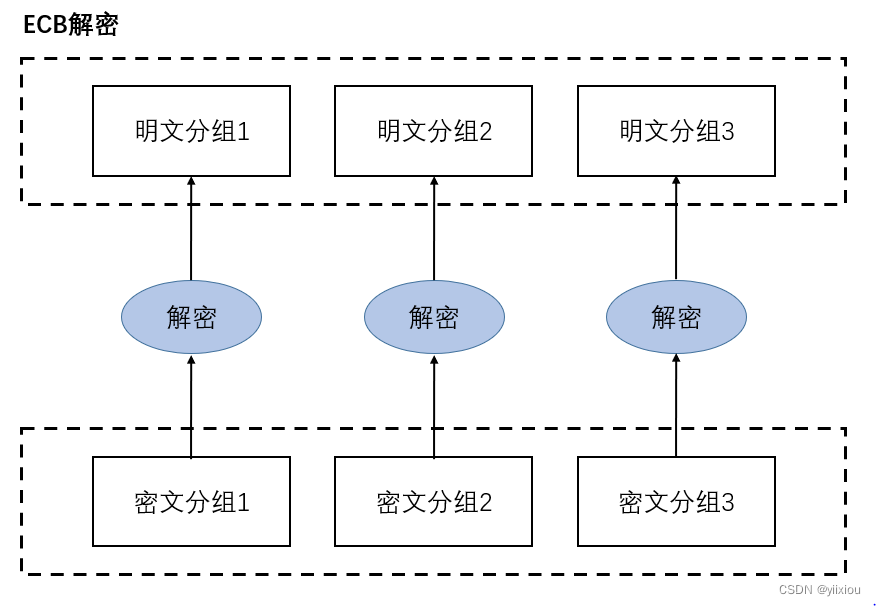
ECB Pattern : Electronic codebook mode .
ECB The result of encryption of plaintext group is directly regarded as ciphertext Group . Plaintext grouping and ciphertext grouping are one-to-one correspondence . shortcoming : Attackers can manipulate plaintext without breaking passwords ( Manipulate ciphertext order , Because plaintext grouping and ciphertext grouping correspond one by one ).
CBC Pattern : Password group link mode .
CBC The pattern first groups the plaintext with the previous ciphertext XOR operation , And then encryption . There is a difference between plaintext group and ciphertext group XOR And cryptographic algorithm .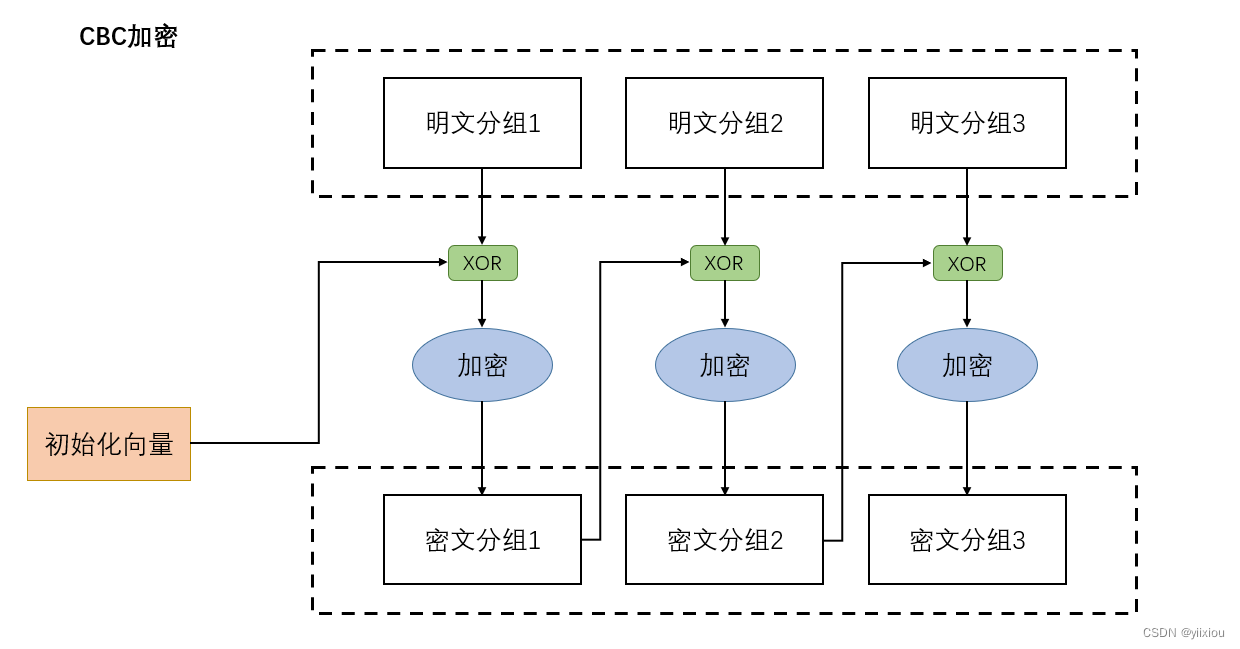

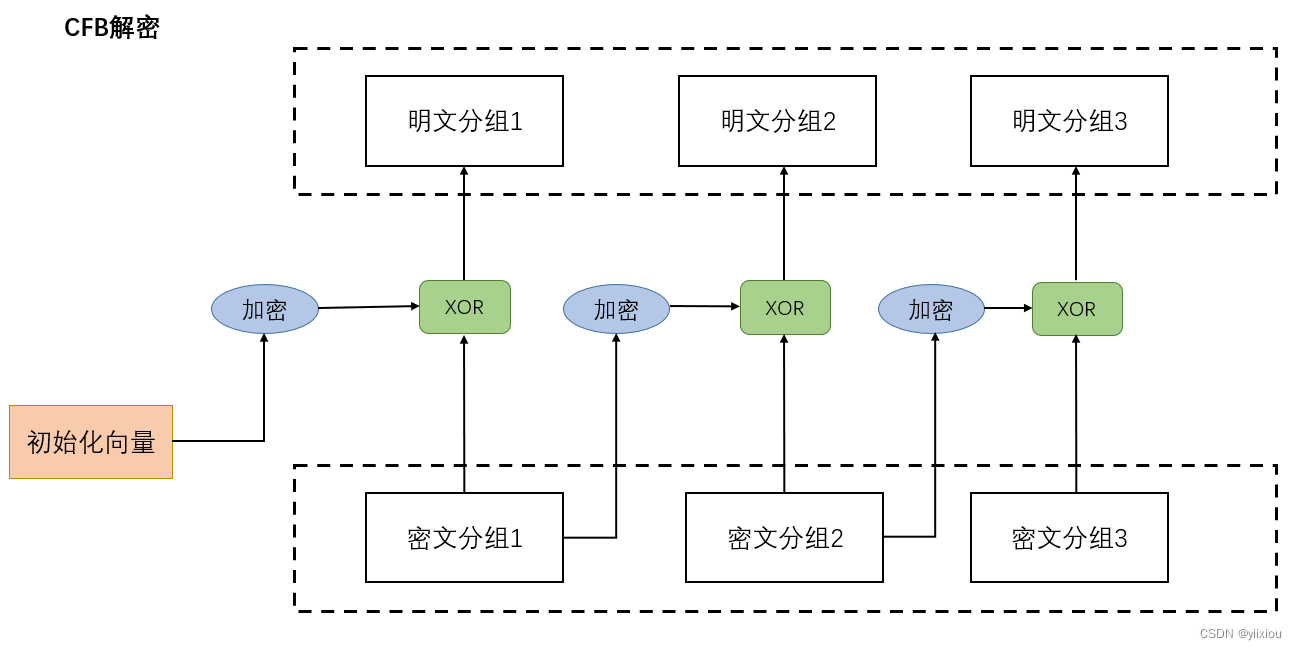
CFB Pattern : Ciphertext feedback mode .( The ciphertext group is fed back to the cryptographic algorithm )
CFB The mode will send the previous ciphertext packet back to the input of the cryptographic algorithm , Proceed again XOR operation . There is only XOR operation .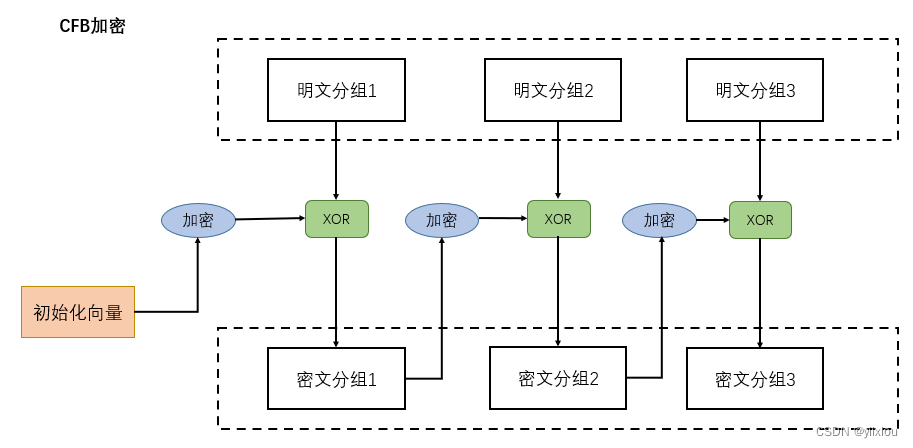
OFB Pattern : Output feedback mode .( The input of the cryptographic algorithm is the output of the previous cryptographic algorithm )
OFB The output of the pattern cipher algorithm will be fed back to the input of the cipher algorithm . Through the output of plaintext grouping and cryptographic algorithm XOR Generate cryptographic grouping .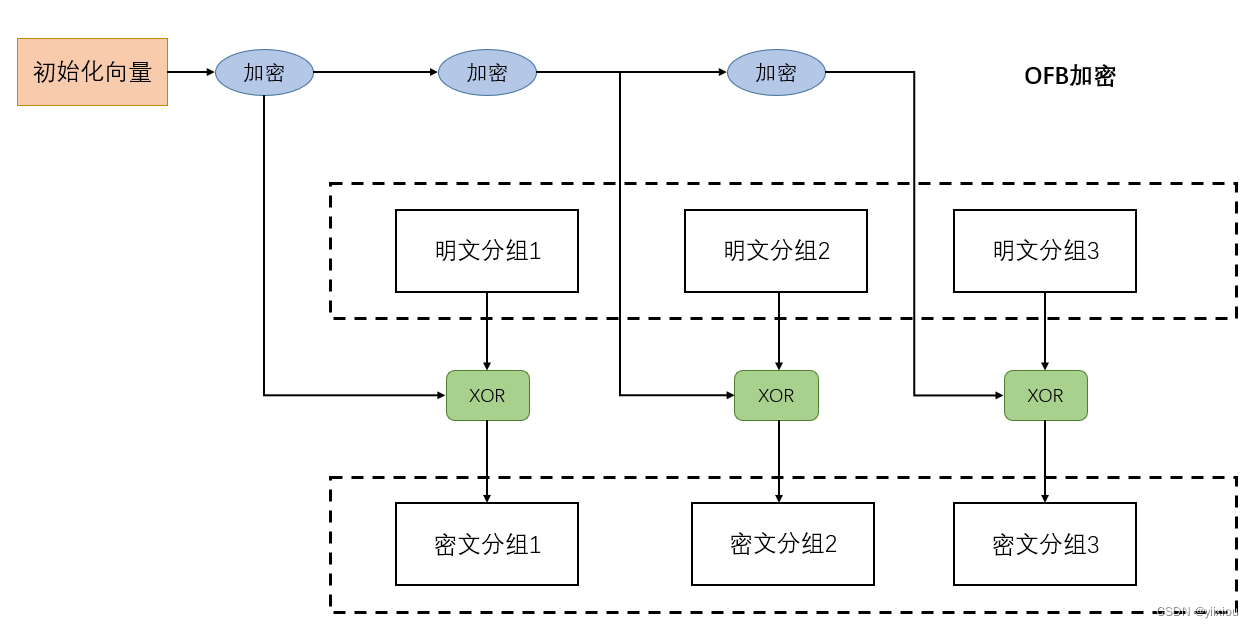

CTR Pattern : counter mode .
CTR Mode is a stream cipher that generates a key stream by encrypting the counter accumulated step by step . The final ciphertext packet is a bit sequence obtained by encrypting the counter , Group with plaintext XOR obtain .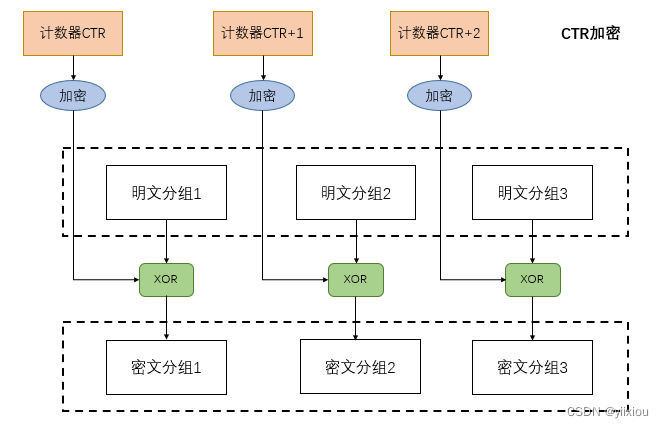

边栏推荐
- Detailed explanation and application of merging and sorting
- Strictly abide by the construction period and ensure the quality, this AI data annotation company has done it!
- 【喜欢的诗词】好了歌
- ping域名报错unknown host,nslookup/systemd-resolve可以正常解析,ping公网地址通怎么解决?
- WebRTC音视频采集和播放示例及MediaStream媒体流解析
- 2016. 增量元素之间的最大差值
- 剑指 Offer II 099. 最小路径之和-双百代码
- 归并排序详解及应用
- MySQL reset password, forget password, reset root password, reset MySQL password
- Static file display problem
猜你喜欢

数据标注典型案例,景联文科技如何助力企业搭建数据方案
Uniapp wechat login returns user name and Avatar

AES高級加密協議的動機闡述

QT qpprogressbar details

Mask R-CNN
Value sequence < detailed explanation of daily question >

Typical case of data annotation: how does jinglianwen technology help enterprises build data solutions

Innovation strength is recognized again! Tencent security MSS was the pioneer of cloud native security guard in 2022

Qt QScrollArea

Addition, deletion, modification and query of handwritten ORM (object relationship mapping)
随机推荐
Jerry's fast touch does not respond [chapter]
Share 10 JS closure interview questions (diagrams), come in and see how many you can answer correctly
STM32之ADC
密码技术---密钥和SSL/TLS
最小生成树 Minimum Spanning Tree
分布式监控系统zabbix
LeetCode 968. 监控二叉树
严守工期,确保质量,这家AI数据标注公司做到了!
[Luogu p1541] tortoise chess [DP]
psnr,ssim,rmse三个指标的定量分析
設置單擊右鍵可以選擇用VS Code打開文件
Qt QSplitter拆分器
Start from the bottom structure to learn the customization and testing of FPGA --- Xilinx ROM IP
Sword finger offer II 099 Sum of minimum paths - double hundred code
海思 VI接入视频流程
Chow-Liu Tree
AES高级加密协议的动机阐述
`Usage of ${}`
数据标注典型案例,景联文科技如何助力企业搭建数据方案
Jerry's charge unplugged, unable to touch the boot [chapter]