当前位置:网站首页>[try to hack] active detection and concealment technology
[try to hack] active detection and concealment technology
2022-07-03 16:56:00 【Happy star】
https://www.bilibili.com/video/BV1bt4y1874s?p=79
Blog home page : Happy star The blog home page of
Series column :Try to Hack
Welcome to focus on the likes collection ️ Leaving a message.
Starting time :2022 year 7 month 3 Japan
The author's level is very limited , If an error is found , Please let me know , thank !
Active reconnaissance is based on OSNT Open source passive reconnaissance , Get more information about the goal , In order to find more places where there may be safety problems . But active reconnaissance will have a lot of interaction with the target , It is more likely to be detected by the target .
technology
1、 Camouflage tool signature
2、 Hide traffic from legitimate traffic
3、 Modify source and type
Adjust source IP Stack and tool identification settings
Common is to change User-Agent
Here we use msf To demonstrate msfconsoleuse auxiliary/fuzzers/http/http_form_field 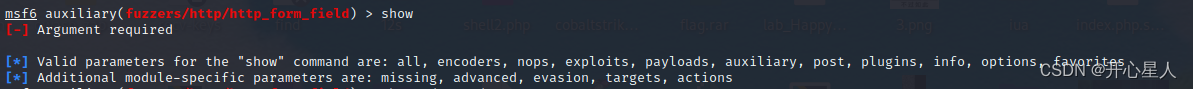
There is one advancedshow advanced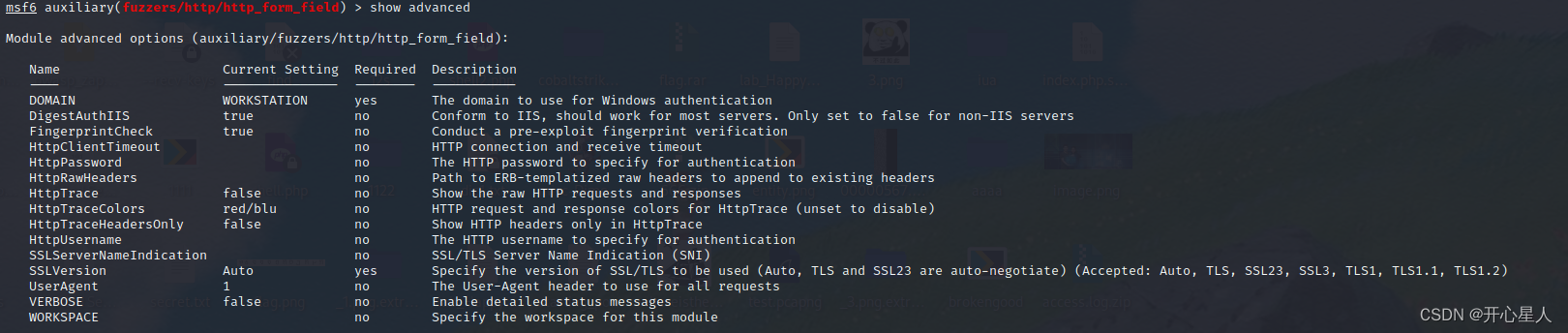
Yes useragentset useragent BaiduSpider // Search engine crawlers are generally not filtered set rhost 192.168.0.1 Set to route , Send... To route http Data packets run
wireshark Grab the bag and have a look
Filtering rules http&&ip.dst==192.168.0.1&&ip.src==192.168.0.106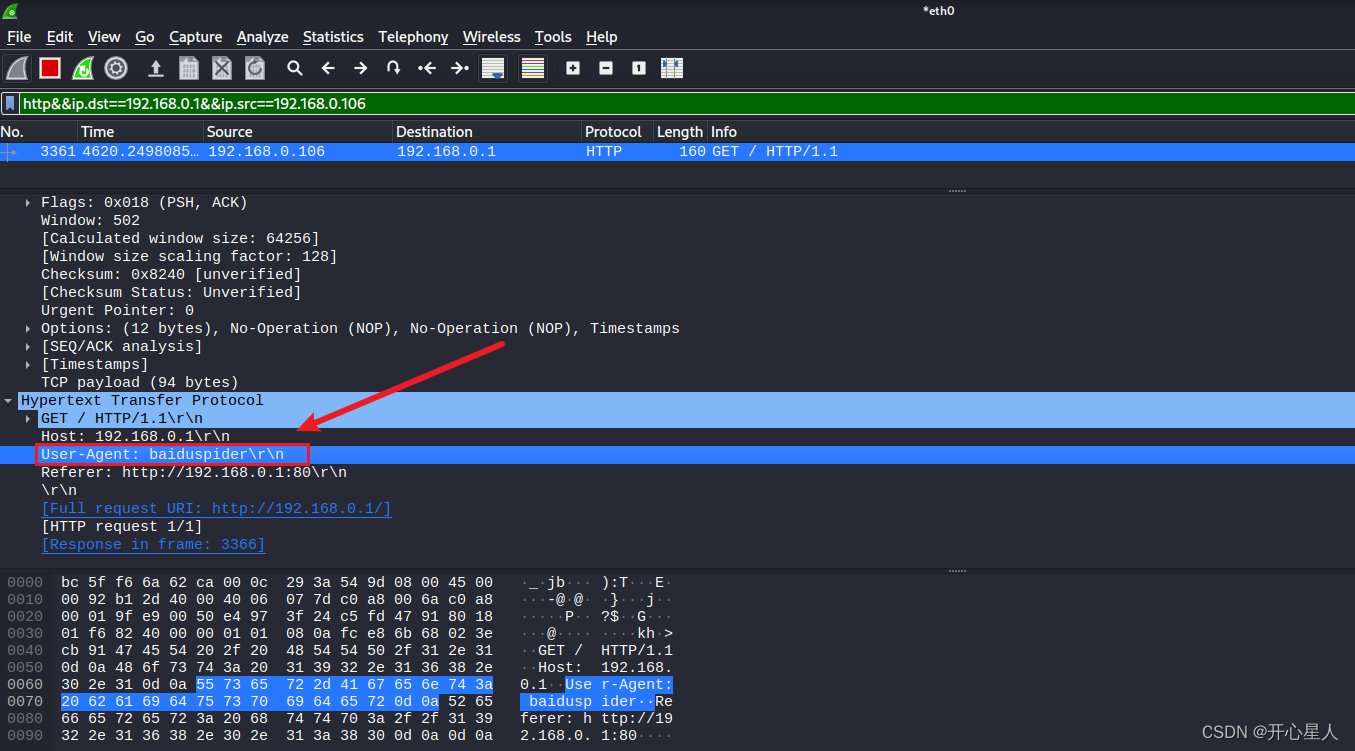
Modify packet parameters
Nmap Modify the original parameters nmap --spoof-mac 11:11:11:11:11:11 26 -sS -Pn -p80 192.168.0.1
It's really disguised mac Address , But why Destination yes 0.0.0.26, I don't know
Many other tools have similar functions to modify packet parameters
Such as masscan Of –adapter-mac、–adapter-ip
Use proxy anonymous Networks tor
When using Tor When the client , Your Internet Communication will be through Tor The network routing . Leaving Tor Before the network reaches its destination , The traffic will pass through several randomly selected relay stations ( Run by volunteers ). This will prevent Internet Service providers and people who monitor your local network view the websites you visit . It also prevents the website itself from knowing your actual location or IP Address - They will see the exit node IP Address and location . Even the relay station doesn't know who requested the traffic they passed . Tor All traffic in the network is encrypted .
apt install torservice tor start start-up torservice tor status see tor Whether to start 
Configure through installation proxychains4, Is to integrate any program and agent tools proxy Establishing a connection , The principle is similar to that of browser proxy .apt install proxychains4gedit /etc/proxychains4.conf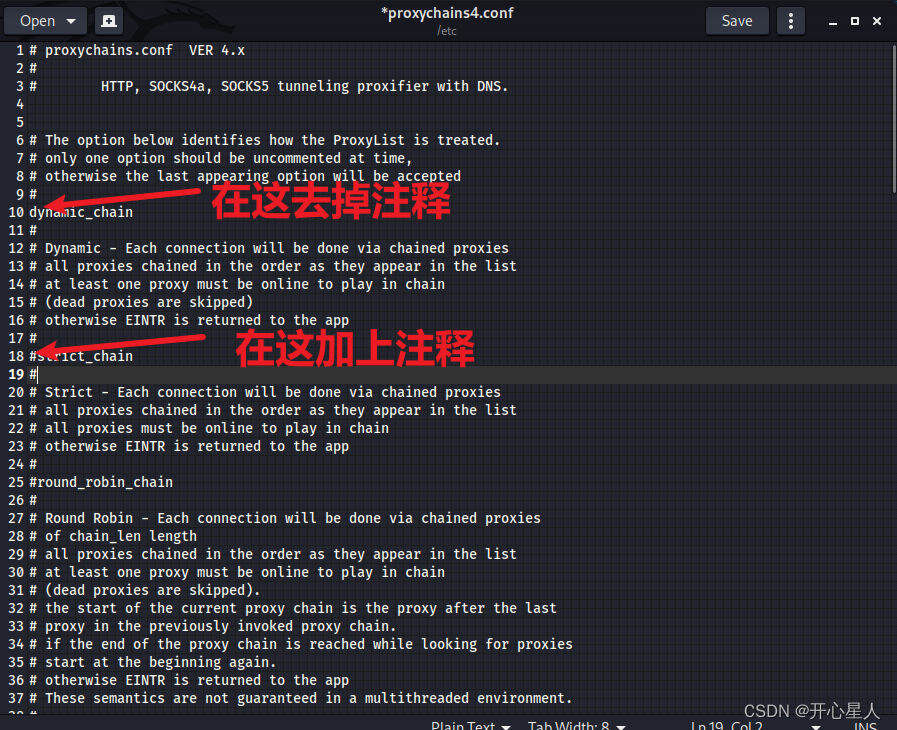

firefox www.whatismyip.com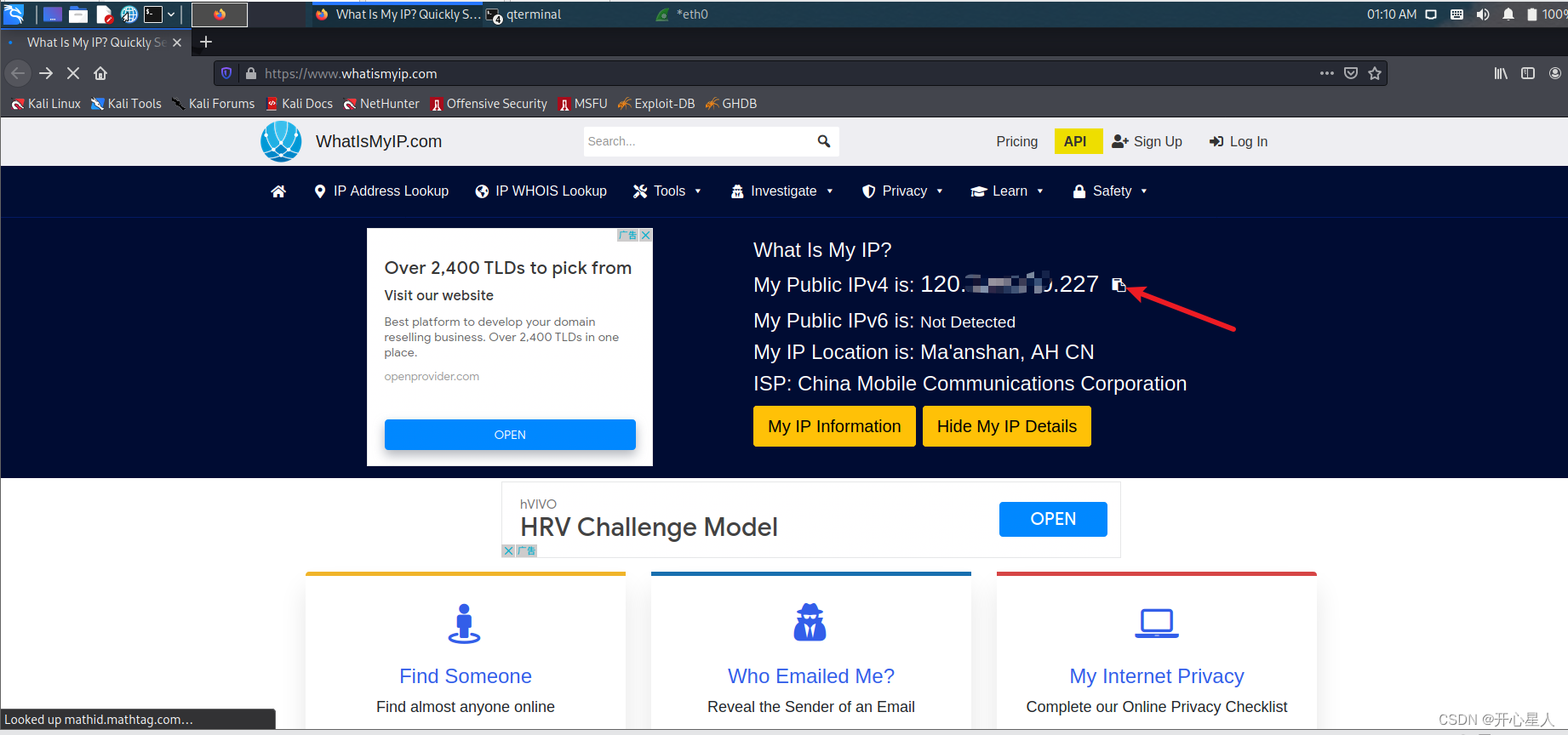
I saw it , This is the truth that no proxy is used ip, It's really my public network ip
proxychains firefox www.whatismyip.com Modify agent
边栏推荐
- MySQL single table field duplicate data takes the latest SQL statement
- 29:第三章:开发通行证服务:12:开发【获得用户账户信息,接口】;(使用VO类包装查到的数据,以符合接口对返回数据的要求)(在多处都会用到的逻辑,在Controller中可以把其抽成一个共用方法)
- 中南大学|通过探索理解: 发现具有深度强化学习的可解释特征
- ANOVA example
- Central South University | through exploration and understanding: find interpretable features with deep reinforcement learning
- Kotlin learning quick start (7) -- wonderful use of expansion
- 远程办公之如何推进跨部门项目协作 | 社区征文
- [combinatorial mathematics] counting model, common combinatorial numbers and combinatorial identities**
- Idea configuration plug-in
- NSQ source code installation and operation process
猜你喜欢

Idea configuration plug-in

What material is 13crmo4-5 equivalent to in China? 13crmo4-5 chemical composition 13crmo4-5 mechanical properties
The most complete postman interface test tutorial in the whole network, API interface test
UCORE overview
2022.02.14_ Daily question leetcode five hundred and forty
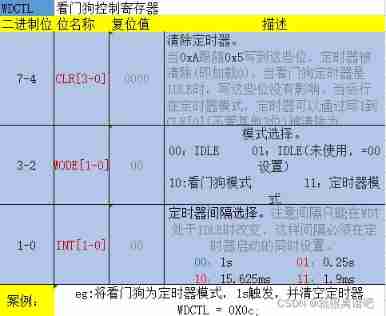
CC2530 common registers for watchdog

2022 love analysis · panoramic report of digital manufacturers of state-owned enterprises
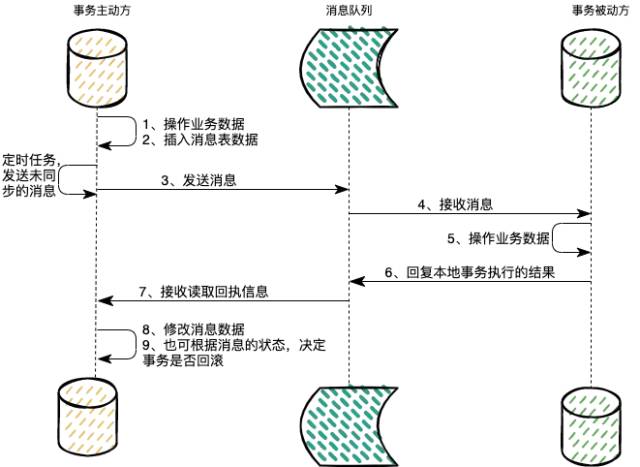
消息队列消息丢失和消息重复发送的处理策略

线程池:业务代码最常用也最容易犯错的组件
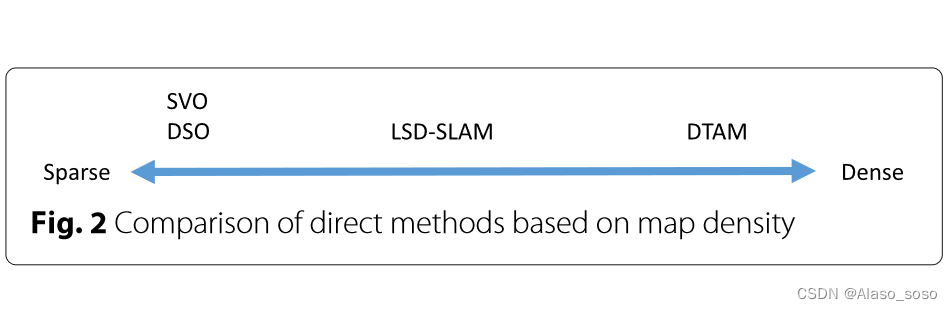
Visual SLAM algorithms: a survey from 2010 to 2016
随机推荐
Processing strategy of message queue message loss and repeated message sending
Zebras are recognized as dogs, and Stanford found the reason why AI made mistakes
【剑指 Offer】58 - I. 翻转单词顺序
Hong Kong Polytechnic University | data efficient reinforcement learning and adaptive optimal perimeter control of network traffic dynamics
Svn usage specification
How to allow remote connection to MySQL server on Linux system?
Interpretation of several important concepts of satellite antenna
What material is 13crmo4-5 equivalent to in China? 13crmo4-5 chemical composition 13crmo4-5 mechanical properties
为抵制 7-Zip,列出 “三宗罪” ?网友:“第3个才是重点吧?”
什么是质押池,如何进行质押呢?
Execute script unrecognized \r
ANOVA example
To resist 7-Zip, list "three sins"? Netizen: "is the third key?"
[combinatorial mathematics] counting model, common combinatorial numbers and combinatorial identities**
Network security web penetration technology
Analysis of variance summary
[combinatorics] recursive equation (outline of recursive equation content | definition of recursive equation | example description of recursive equation | Fibonacci Series)
Prepare for the golden three silver four, 100+ software test interview questions (function / interface / Automation) interview questions. win victory the moment one raises one 's standard
What is the material of sa302grc? American standard container plate sa302grc chemical composition
一台服务器最大并发 tcp 连接数多少?65535?