当前位置:网站首页>Build your own website (23)
Build your own website (23)
2022-07-03 16:50:00 【probezy】
In the last article , We downloaded the security certificate of the website from Alibaba cloud , But this certificate wants to take effect , It also needs to be configured accordingly , To configure it, you need to use VS code Yes cpolar Make necessary modifications to the configuration file of . Now? , Let's introduce , How to cpolar To configure , Make the webpage security file we downloaded take effect .
First , You need to unzip the downloaded website security file to a specific folder , Make Internet visitors visit , You can check the security certificate of our website . Generally speaking , The security certificate files of the website will be placed in “certs” In the folder , So our first step is to establish “certs” Folder . Need to pay attention to , To avoid file call errors , We'd better “certs” Folders are built on simple paths . ad locum , We will certs Put the folder in D Under the plate .
In this way , There are all relevant folders of our website , It contains the compressed files and folders of the domain name we purchased , Security certificate and key . And then we'll be at “certs” Under the folder , establish “site1” Folder , And paste two website security files into it ,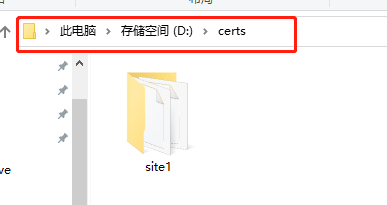
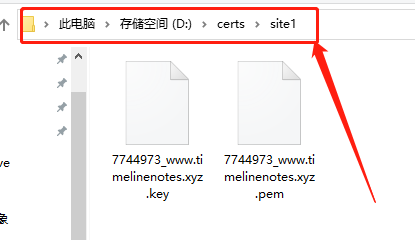
After placing the website security file , We need to remember the path of these security files , Then open the VS code, Yes cpolar To modify the configuration file of , Give Way cpolar Know the location of these two security files , So that it can be called when necessary .
ad locum , We need to find the tunnel name to configure the security file ( In this case is timelinenotes Tunnel ), And in the position indicated by the arrow , Insert the storage path and file name of the two security files .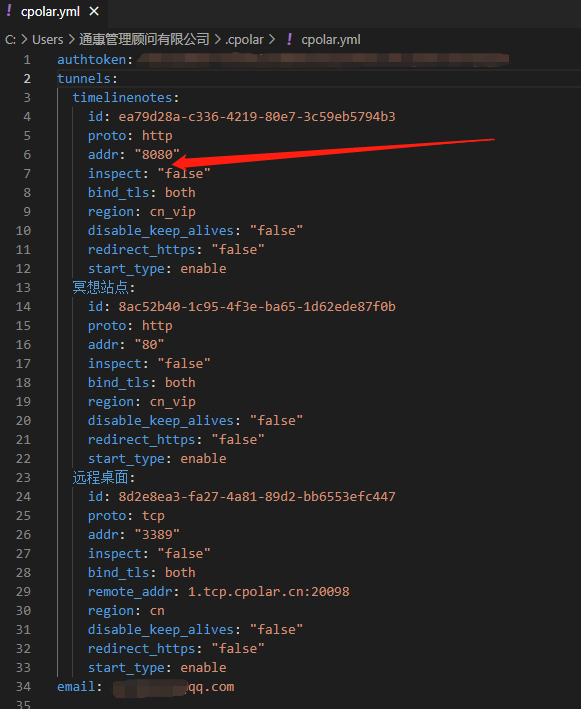
Because our website security files are stored in D disc certs In folder site1 Under the folder , Therefore, the parameters to be entered are :
crt:D:\certs\site1\ 7744973_www.timelinenotes.xyz.pem
key:D:\certs\site1\ 7744973_www.timelinenotes.xyz.key
These two parameters are different for each user ( The difference lies in the location where the security files are stored , And the number of the safety document itself is different ), Therefore, you need to input according to the actual situation . After input , That's what it looks like :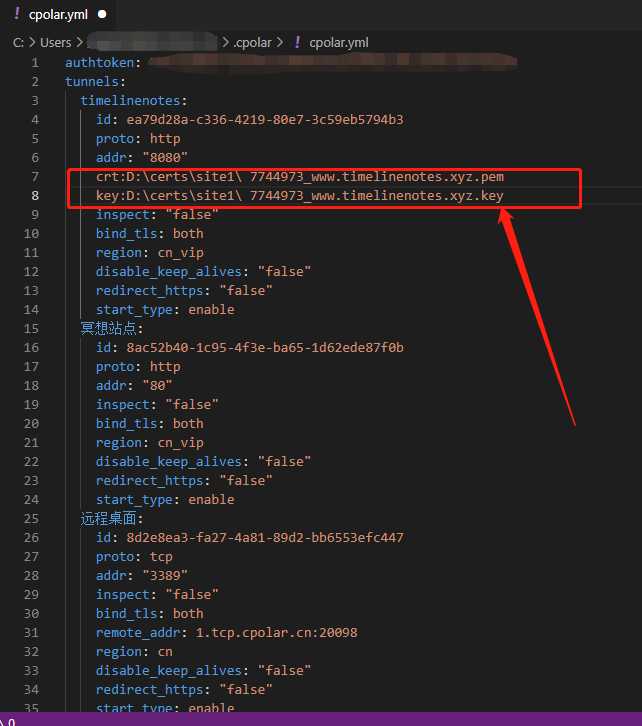
After this step of configuration , We have to restart cpolar, You can pass https The prefix name of , Visit our website . meanwhile , Before the website domain name “” Will also light up , It marks that our website is a safe website .
thus , We go through cpolar, The work of publishing the local website to the public network is completed . Put the web page on your local computer , It can save renting network servers ( In the past, websites had to rent servers to build ) A lot of expenses , It is very suitable for individuals and small businesses . however cpolar The role of is not limited to building websites , It can also be tested on Web pages 、 Telecommuting 、 Intranet data release 、 Build small servers and other aspects to show their skills . If you are right about cpolar Have any questions , Welcome to contact us , We will certainly provide you with assistance within our ability . Of course, you are welcome vip Customer join cpolar Official group , Explore together cpolar The infinite potential of .
边栏推荐
- Fast Ethernet and Gigabit Ethernet: what's the difference?
- The word backspace key cannot delete the selected text, so you can only press Delete
- What is the pledge pool and how to pledge?
- To resist 7-Zip, list "three sins"? Netizen: "is the third key?"
- CC2530 common registers for crystal oscillator settings
- [combinatorics] polynomial theorem (polynomial theorem | polynomial theorem proof | polynomial theorem inference 1 item number is the number of non negative integer solutions | polynomial theorem infe
- Processing strategy of message queue message loss and repeated message sending
- Aike AI frontier promotion (7.3)
- PHP CI (CodeIgniter) log level setting
- Extraction of the same pointcut
猜你喜欢
UCORE overview

Thread pool executes scheduled tasks

Basis of target detection (IOU)

CC2530 common registers for port initialization
CC2530 common registers for serial communication

Network security web penetration technology
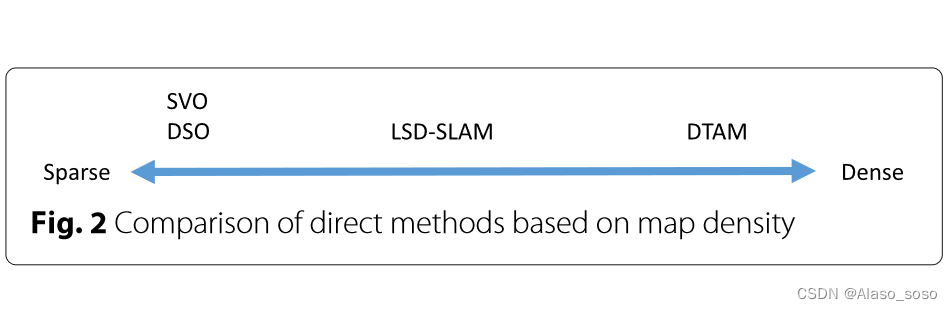
Visual SLAM algorithms: a survey from 2010 to 2016
![[combinatorics] non descending path problem (number of non descending paths with constraints)](/img/89/bd1a2ddd9632ab5d4b4bee9336be51.jpg)
[combinatorics] non descending path problem (number of non descending paths with constraints)
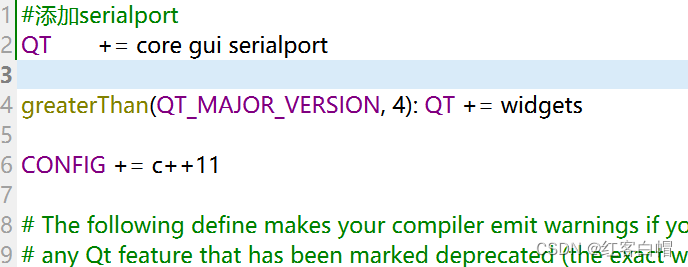
QT串口ui设计和解决显示中文乱码
![[combinatorics] polynomial theorem (polynomial theorem | polynomial theorem proof | polynomial theorem inference 1 item number is the number of non negative integer solutions | polynomial theorem infe](/img/9d/6118b699c0d90810638f9b08d4f80a.jpg)
[combinatorics] polynomial theorem (polynomial theorem | polynomial theorem proof | polynomial theorem inference 1 item number is the number of non negative integer solutions | polynomial theorem infe
随机推荐
Mysql 单表字段重复数据取最新一条sql语句
Mysql database DDL and DML
香港理工大学|数据高效的强化学习和网络流量动态的自适应最优周界控制
2022 love analysis · panoramic report of digital manufacturers of state-owned enterprises
CC2530 common registers for watchdog
PHP secondary domain name session sharing scheme
爱可可AI前沿推介(7.3)
[combinatorics] polynomial theorem (polynomial theorem | polynomial theorem proof | polynomial theorem inference 1 item number is the number of non negative integer solutions | polynomial theorem infe
ucore概述
【剑指 Offer】58 - I. 翻转单词顺序
[combinatorics] recursive equation (outline of recursive equation content | definition of recursive equation | example description of recursive equation | Fibonacci Series)
Summary of three methods of PHP looping through arrays list (), each (), and while
Daily code 300 lines learning notes day 10
Client does not support authentication protocol requested by server; consider upgrading MySQL client
What material is sa537cl1? Sa537cl1 corresponds to the national standard material
A survey of state of the art on visual slam
Le zèbre a été identifié comme un chien, et la cause de l'erreur d'AI a été trouvée par Stanford
8 tips for effective performance evaluation
[combinatorics] recursive equation (example 1 of recursive equation | list recursive equation)
Deep understanding of grouping sets statements in SQL