当前位置:网站首页>String type and bitmap of redis
String type and bitmap of redis
2022-07-27 08:39:00 【lsd&xql】
redis Of string Type and bitmap
redis Operation principle
redis There are many clients connected , Standing on the redis From the perspective of the machine , It's just that there are a lot of socket The connection of , And it's in the kernel
above ,redis It's a process , Processes can call on the kernel epoll, To traverse to find which client sent data ( Here is a single process and single thread to process user data ).
redis Use
redis The default is 16 Databases 

Input :
Enter basic group 
keys * Query all key
FLUSHDB Clear away all key
For the above nx Your order is my current key If it is not set, set ooxx Set successfully , If the key There has been a value 了 ,
Then return to nil ( It is mainly used for acquiring distributed locks , Only one can succeed )
about xx command , Only when it exists can it be operated .
mset command ( Set up multiple key and value)
append Command and getrange command 
redis Forward and reverse indexing 
The front is from 0,1,2 At the beginning , The latter is from -1 Beginning to decline , So you can also write in the following way 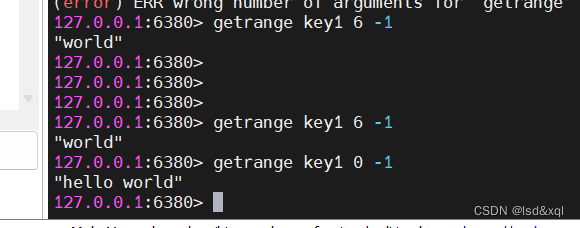
SETRANGE Set the string in the given range 
Get string length 
obtain key The corresponding value type ( Mainly to see set Command grouping is in string above )
Let's take a look at object command 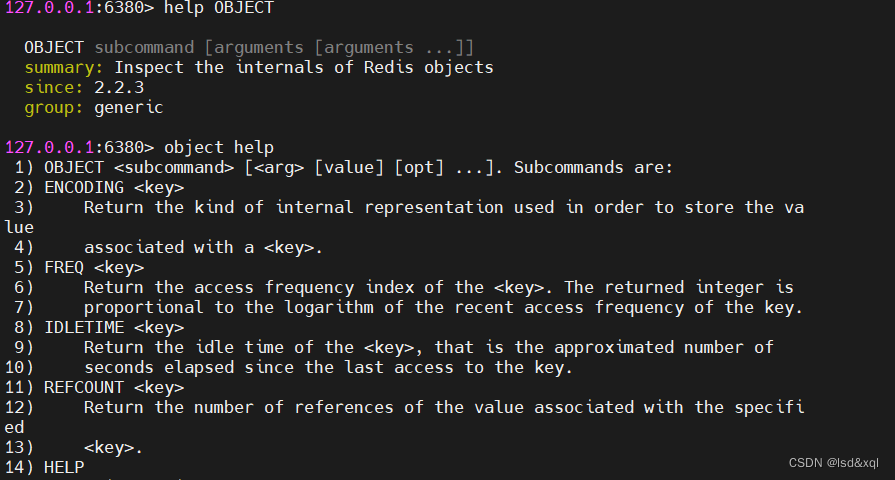
It can see value Code type of ( oriented redis string type , Besides string operation, there are also calculation operations 【 The operation of calculation is numerical 】)
incr and decr Relevant command 【 Can be used to rush to buy , seckill , give the thumbs-up , comments , Details page ( For example, Taobao details page , The backend will definitely initiate an asynchronous query on the number of purchases , check redis, Can avoid and issue , Transaction operation on Database ,
Completely by redis Memory operation replaces )】

redis Binary security
redis When a process interacts with the outside world , Stream oriented we have byte streams , And character stream , that redis client
At the time of the visit , from socket What you get inside is the data of byte stream , As long as the client and server of both sides have the same
Codec mode , The data will not be destroyed .
Such as set k1 = 9999, perform strlen Output 4,redis The data stored in it is stored according to one character and one byte , direct
Write to the character stream , perform incr Then take out the byte stream and convert it into numerical value , It will be updated after being converted to numerical value key Of encoding
code , As long as it is added successfully, it will be updated to int 了 , If you add it next time, you can directly check this encoding Type , If you add
No int An error is reported for the type
The other is set k2 in , It is Zhan 3 Bytes of ( Software and redis Communications utf-8)
Let's set up another k3 Occupy 2 Bytes (gbk code )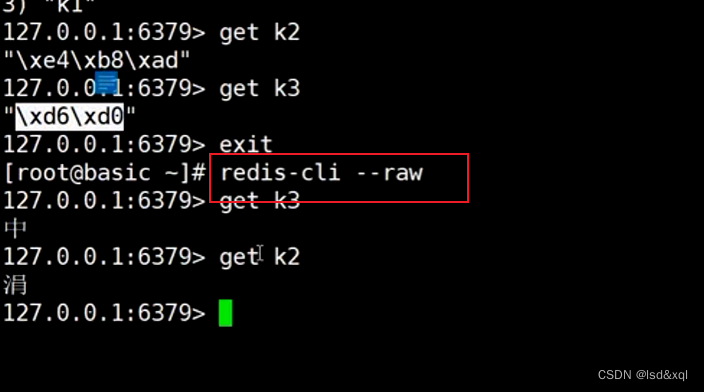
Then exit with redis-cli --raw To log in , Will trigger a format ( If you don't bring –raw Yes, I can only recognize ascii The code
, In case of excess, it shall be subject to 16 To show , If you add raw Will trigger the format of the code set )
key There are encoding Words , It is equivalent to an optimization , To judge whether my current operation is feasible
getset command
getset The command is to return the old value and set the new value ,( be relative to get and set If executed alone , Send two separate
The order passed ,IO Communication twice , This method only communicates once 【 Save resources 】)
mset Set up multiple key Multiple value
msetnx ( Set up multiple key Corresponding value Guaranteed atomicity ) In the picture below msetnx Set up k3 When it failed 
Bitmap (bitmap)
setbit Method , In the corresponding bit Set the value above the bit 
bitpos command :
Find the first byte First of all 1 Position of appearance 
Find the second byte to appear 1 The first position 
Statistics 1 There are several times in the byte range 
bitop Commands can be bitwise value And and or etc 
Scene question
1、 The company has a user system , Count the login days of users , And the window is random ( Push forward one week one day , And a week later , Count the number of days users log in )
One year is set to 400 God , have access to 50 Bytes save the user's login status throughout the year 
-2 and -1 For the last two bytes ( Inquire about 300 To the first day 400 God ) How many login times .【 Let users be key Login days are value】
Of course, if you think the number of users is particularly large, you can consider saving one for some users redis, Another part
Save another redis【 notes :1 Users 50 Bytes , that 20 Users save 1k Space ,20000 The more users need 1MB Space
2000000 Users need 100M Space 】
2、 JD.COM 618 Do activities and give gifts , How many gifts are in stock in the big warehouse ? Suppose there is 2E user
1、 Classify users ( Divided into zombie users Hot and cold users / Loyal users )
So we need to do active user statistics ,
What are active users :
for instance 1 Number -3 Number Continuous login De duplication of repeated login
redis How to do
First, in the 2022 year 1 month 1 Japan id by 1 The user of is logged in to bit Bit 1 Bit setting 1
stay 2022 year 1 month 2 Japan id by 1 and id by 7 Of users logged in at bit position 1 and bit position 7 Set up 1
summary
key Of type type , It is used to determine whether the access method has this type of operation , It can quickly return errors , Can avoid
abnormal .
encoding It can avoid the same type Type, but calculate according to different forms ,
also length attribute , If the data has not changed, you can directly return the length
边栏推荐
- 4277. Block reversal
- Background image related applications - full, adaptive
- sql_ Mode strict mode (ansi/traditional/strict_trans_tables)
- JWT authentication and login function implementation, exit login
- 693. 行程排序
- Functions and arrow functions
- Node installation and debugging
- Flutter 渲染机制——GPU线程渲染
- 1176 questions of Olympiad in informatics -- who ranked K in the exam
- 众昂矿业:新能源行业快速发展,氟化工产品势头强劲
猜你喜欢

Interviewer: what is scaffolding? Why do you need scaffolding? What are the commonly used scaffolds?
View 的滑动冲突

Create a project to realize login and registration, generate JWT, and send verification code

说透缓存一致性与内存屏障

First experience of tryme in opengauss

UVM入门实验1

One book 1201 Fibonacci sequence

海关总署:这类产品暂停进口

Vcenter7.0 installation of ibm3650m4 physical machine
Day4 --- flask blueprint and rest ful
随机推荐
Installation and use of beef XSS
借生态力量,openGauss突破性能瓶颈
Day6 --- Sqlalchemy advanced
Minio installation and use
【渗透测试工具分享】【dnslog服务器搭建指导】
好吃难吃饱七分为宜;好喝难喝醉三分为佳
4274. Suffix expression
MCDF顶层验证方案
[ciscn2019 southeast China division]web11 1
Initial summary of flask framework creation project
Oppo self-developed large-scale knowledge map and its application in digital intelligence engineering
Realization of backstage brand management function
It's better to be full than delicious; It's better to be drunk than drunk
如何卸载--奇安信安全终端管理系统
3428. 放苹果
【uni-app高级实战】手把手带你学习一个纯实战复杂项目的开发1/100
Explain cache consistency and memory barrier
JS basic knowledge - daily learning summary ①
[uni app advanced practice] take you hand-in-hand to learn the development of a purely practical complex project 1/100
VS Code中#include报错(新建的头文件)