当前位置:网站首页>Redis sentinel cluster working principle and architecture deployment # yyds dry goods inventory #
Redis sentinel cluster working principle and architecture deployment # yyds dry goods inventory #
2022-07-02 20:23:00 【Jiangxiaolong's technology blog】
Redis Working principle and architecture deployment of sentry cluster
Table of Contents
- Redis Working principle and architecture deployment of sentry cluster
- 1.redis Sentinel mode principle
- 2. build redis The sentry cluster
- 2.1. Environmental preparation
- 2.2. Deploy on all machines redis
- 2.3. Three stations redis Deployment completed
- 2.4. To configure redis Master-slave
- 2.5. Deploy sentinel process sentinel
- 2.6. Start the sentry to observe the changes in the configuration file
- 2.7. Simulate the main library failure and verify whether the application is available
- 2.8. The main library hangs up the changes in the configuration files of other nodes
1.redis Sentinel mode principle
redis Lack of master-slave replication : When the main database goes down ,slave You can't become the main library by yourself , Write data , Every time, it needs to be manually configured to change from the library to the main library to write data , After the master database is repaired, it is also necessary to manually configure the import slave database host before configuring the master-slave replication
redis The advantages of sentinel mode : redis Sentinels are built on master-slave , There is a monitoring function , Monitor whether the main database is abnormal , When the main database is abnormal, it will automatically send a slave Change to main library , It eliminates human configuration
redis Sentinel mode principle : Sentinel mode is based on master-slave replication , Will be in every redis Open a... On the node sentinel monitor , Every sentinel Each process has its own port number and IP, all sentinel Share cluster information , All in the cluster sentinel Can communicate , When the main database goes down , On the main library sentinel It will send messages to other nodes in the cluster sentinel Send a message saying that the main library is down , Need to vote from the library master, At this time, on each node sentinel Compare yourself redis Configured ID Number , such as slave1 Of ID Large ,slave1 Will be elected master As main storehouse , When the failed primary database rejoins the cluster , On the main library sentinel Will be sent to other nodes sentinel Ask who is the main library , At this time slave1 Upper sentinel Will tell the on the main library sentinel say slave1 It's the main warehouse , Rejoining the main database of the cluster will find slave1 Synchronous data , If the rejoined master database wants to become the master database again , You only need to execute the authorization command to become the main library again .
Program configuration during master-slave replication redis When the address is written, the address of the main database is written , You need to manually modify the application every time the main library goes down
With sentinel mode , Configuration in program code is not redis Address , But the addresses of all sentinels configured , Form an address pool , Even if one of the sentinels in the cluster breaks down , There are two other sentinels , Every time you need to find redis When writing data , The program will first find the sentinel process , Information sharing between sentinels , Will immediately tell the program who is the main library , Then the program gets what the sentry told it redis Main database address , Will go to find the master inventory data , So even if the main library is broken , There is no need to modify the program code
The sentry's configuration file after starting the sentry service , Try not to modify , Because the Sentry will automatically add configuration
The recommended number of sentinel clusters is odd , such as 3/5/7
With sentinels , When the main library hangs up , The sentry elected a new Treasury , The configuration file will be automatically modified to the address of the latest main library
Sentinel election rules : The first judgment slave-priority Weight priority , Whoever is taller is elected master Main library , If all agree , Compare the of each node for so long id, Who's big, who's elected
Comparison between sentinel mode architecture and master-slave replication architecture 
2. build redis The sentry cluster
2.1. Environmental preparation
| IP | service |
|---|---|
| 192.168.81.210 | redis+sentinel+master |
| 192.168.81.220 | redis+sentinel+slave |
| 192.168.81.230 | redis+sentinel+slave |
Steps for configuring sentinel clusters :
1. At all nodes redis
2. Configure master-slave replication , One master and two slaves
3. Configure... On all nodes sentinel, start-up sentinel after , The configuration file will be automatically added
2.2. Deploy on all machines redis
192.168.81.210 To configure
192.168.81.220 To configure
because redis-1 A set has been deployed redis, We can copy it directly
192.168.81.230 To configure
because redis-1 A set has been deployed redis, We can copy it directly
2.3. Three stations redis Deployment completed
2.4. To configure redis Master-slave
On both sets slave Synchronize master database configuration on
2.5. Deploy sentinel process sentinel
Profile explanation
Three stations redis Servers should be configured as follows , The... In the configuration file has been bind Written as a system variable , In coordination cat Write to file , Therefore, you can directly execute the following commands
After configuration, remember to check the configuration file bind Whether a column belongs to the respective host ip Address 
2.6. Start the sentry to observe the changes in the configuration file
All three machines operate like this. Start the sentry
Observe the changes of configuration file before and after sentry startup
Before startup 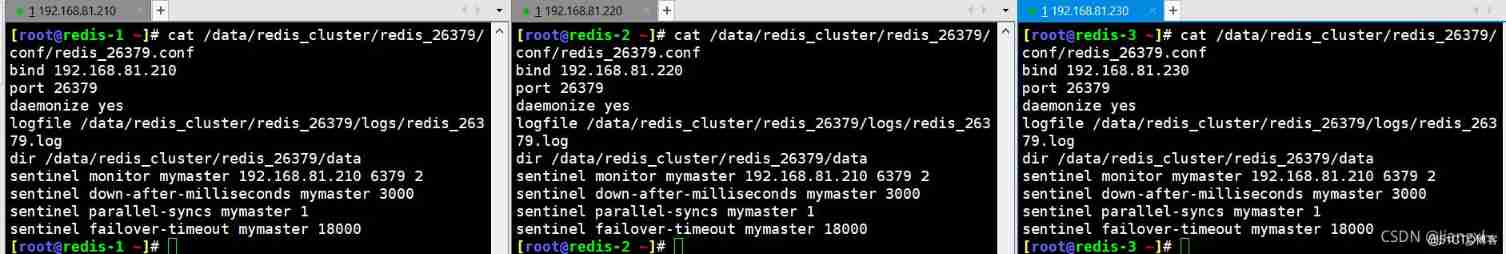
After starting

Each sentinel host automatically adds one myid Configuration of , This is when the main database hangs up , The basis for the sentinel election , Judge whose myid Whoever is older will be elected as the main library
Each sentinel host also automatically adds sentinel known-sentinel This configuration , In this configuration, each sentinel will record the data of other nodes in the cluster id Number , In this way, information sharing can be realized , Even when the application asks the sentinel process who is the main library , At this time, because each sentinel process has information about other nodes , So you can tell the application who is the main library

2.7. Simulate the main library failure and verify whether the application is available
After the sentinel is deployed , Each node has cluster information sharing , When the main library hangs up , Sentinel process confirms that the main library is offline , The Sentinels according to their id Size elects a new main library , Take over the work of the main warehouse , Ensure that the application is not affected , When the main library is repaired , First synchronize the data of the current master database by raising the right , In making itself the main library

2.8. The main library hangs up the changes in the configuration files of other nodes
After the main library hangs up , The other two nodes elect master after , The configuration file will also be filled in as new master The address of

边栏推荐
- 什么叫在线开户?现在网上开户安全么?
- 八年测开经验,面试28K公司后,吐血整理出高频面试题和答案
- How to set priorities in C language? Elaborate on C language priorities
- Overview of browser caching mechanism
- esp32c3 crash分析
- 现在券商的优惠开户政策什么?实际上网上开户安全么?
- In depth understanding of modern web browsers (I)
- How to realize the function of detecting browser type in Web System
- What is online account opening? Is it safe to open an account online now?
- 笔记本安装TIA博途V17后出现蓝屏的解决办法
猜你喜欢
CS5268完美代替AG9321MCQ Typec多合一扩展坞方案
B端电商-订单逆向流程

KT148A语音芯片ic的开发常见问题以及描述

Cs5268 perfectly replaces ag9321mcq typec multi in one docking station solution
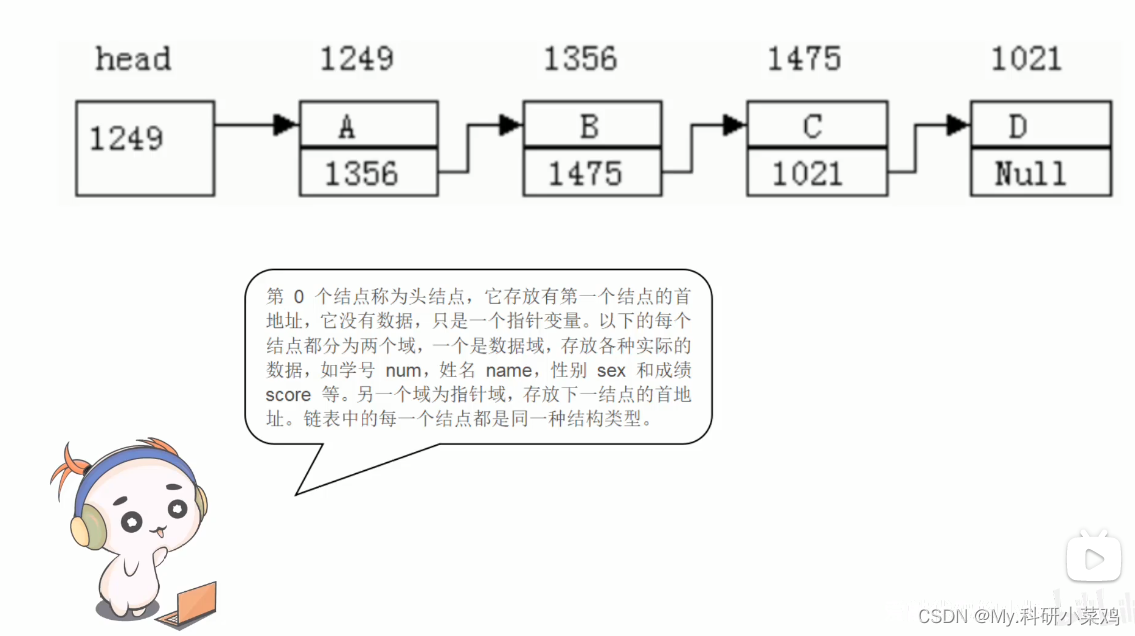
C language linked list -- to be added

KT148A语音芯片ic的软件参考代码C语言,一线串口

After eight years of test experience and interview with 28K company, hematemesis sorted out high-frequency interview questions and answers
![[internship] solve the problem of too long request parameters](/img/42/413cf867f0cb34eeaf999f654bf02f.png)
[internship] solve the problem of too long request parameters
SBT tutorial

Py's interpret: a detailed introduction to interpret, installation, and case application
随机推荐
Automatically generate VGg image annotation file
After writing 100000 lines of code, I sent a long article roast rust
功能、作用、效能、功用、效用、功效
Workplace four quadrant rule: time management four quadrant and workplace communication four quadrant "suggestions collection"
RPD出品:Superpower Squad 保姆级攻略
Share several map bed websites for everyone to share pictures
Common problems and description of kt148a voice chip IC development
[source code analysis] model parallel distributed training Megatron (5) -- pipestream flush
Outsourcing for three years, abandoned
at编译环境搭建-win
外包干了三年,废了...
AcWing 181. Turnaround game solution (search ida* search)
Database schema notes - how to choose the right database in development + who invented relational database?
How to open an account online? Is it safe to open a mobile account?
C language linked list -- to be added
What are the preferential account opening policies of securities companies now? Is it actually safe to open an account online?
[Chongqing Guangdong education] reference materials for labor education of college students in Nanjing University
Is it safe to open an account for online stock speculation? I'm a novice, please guide me
Burp install license key not recognized
【Kubernetes系列】kubeadm reset初始化前后空间、内存使用情况对比