当前位置:网站首页>[set theory] binary relation (example of binary relation operation | example of inverse operation | example of composite operation | example of limiting operation | example of image operation)
[set theory] binary relation (example of binary relation operation | example of inverse operation | example of composite operation | example of limiting operation | example of image operation)
2022-07-03 04:37:00 【Programmer community】
List of articles
- One 、 Examples of inverse operations
- Two 、 Examples of composite operations ( Reverse order synthesis )
- 3、 ... and 、 Examples of limiting operations
- Four 、 Like operation examples
One 、 Examples of inverse operations
A
=
{
a
,
b
,
c
,
d
}
A = \{ a, b, c, d \}
A={ a,b,c,d}
B
=
{
a
,
b
,
<
c
,
d
>
}
B = \{ a, b, <c, d> \}
B={ a,b,<c,d>}
C
=
{
<
a
,
b
>
,
<
c
,
d
>
}
C = \{ <a, b> , <c, d> \}
C={ <a,b>,<c,d>}
Find the inverse operation of the above set
The inverse operation can only aim at Ordered pair Conduct , If there is no order, right , There is no concept of relational operation ;
A
A
A There are no ordered pairs in the set , Therefore, there is no concept of relational operation , Inverse it , The result is an empty set ;
A
−
1
=
∅
A^{-1} = \varnothing
A−1=∅
B
B
B Collection Yes Ordered pair
<
c
,
d
>
<c, d>
<c,d> , The inverse operation is to find the inverse of all ordered pairs ;
B
−
1
=
{
<
d
,
c
>
}
B^{-1} = \{ <d, c> \}
B−1={ <d,c>}
C
C
C Collection Yes Ordered pair
<
a
,
b
>
,
<
c
,
d
>
<a,b> , <c, d>
<a,b>,<c,d> , The inverse operation is to find the inverse of all ordered pairs ;
C
−
1
=
{
<
b
,
a
>
,
<
d
,
c
>
}
C^{-1} = \{ <b,a> , <d, c> \}
C−1={ <b,a>,<d,c>}
Two 、 Examples of composite operations ( Reverse order synthesis )
B
=
{
a
,
b
,
<
c
,
d
>
}
B = \{ a, b , <c,d> \}
B={ a,b,<c,d>}
R
=
{
<
a
,
b
>
,
<
c
,
d
>
}
R = \{ <a,b> , <c,d> \}
R={ <a,b>,<c,d>}
G
=
{
<
b
,
e
>
,
<
d
,
c
>
}
G = \{ <b, e> , <d, c> \}
G={ <b,e>,<d,c>}
Find the result of the following synthesis operation , there synthesis refer to Reverse order synthesis
B
o
R
−
1
B o R^{-1}
BoR−1
R
−
1
=
{
<
b
,
a
>
,
<
d
,
c
>
}
R^{-1} = \{ <b,a> , <d,c> \}
R−1={ <b,a>,<d,c>}
B
o
R
−
1
=
{
<
c
,
d
>
}
o
{
<
b
,
a
>
,
<
d
,
c
>
}
=
{
<
d
,
d
>
}
B o R^{-1} = \{ <c, d> \} o \{ <b,a> , <d,c> \} = \{ <d, d> \}
BoR−1={ <c,d>}o{ <b,a>,<d,c>}={ <d,d>}
synthesis The default is Reverse order synthesis
G
o
B
G o B
GoB
G
o
B
=
{
<
b
,
e
>
,
<
d
,
c
>
}
o
{
<
c
,
d
>
}
=
{
<
c
,
c
>
}
G o B = \{<b,e>, <d, c>\} o \{ <c,d> \} = \{ <c,c> \}
GoB={ <b,e>,<d,c>}o{ <c,d>}={ <c,c>}
G
o
R
G o R
GoR
G
o
R
=
{
<
b
,
e
>
,
<
d
,
c
>
}
o
{
<
a
,
b
>
,
<
c
,
d
>
}
=
{
<
a
,
e
>
,
<
c
,
c
>
}
G o R =\{<b,e>, <d, c>\} o \{ <a,b> , <c,d> \} = \{ <a,e>, <c,c> \}
GoR={ <b,e>,<d,c>}o{ <a,b>,<c,d>}={ <a,e>,<c,c>}
R
o
G
R o G
RoG
R
o
G
=
{
<
a
,
b
>
,
<
c
,
d
>
}
o
{
<
b
,
e
>
,
<
d
,
c
>
}
=
{
<
d
,
d
>
}
R o G =\{ <a,b> , <c,d> \} o \{<b,e>, <d, c>\} = \{ <d,d> \}
RoG={ <a,b>,<c,d>}o{ <b,e>,<d,c>}={ <d,d>}
3、 ... and 、 Examples of limiting operations
F
=
{
<
a
,
b
>
,
<
a
,
{
a
}
>
,
<
{
a
}
,
{
a
,
{
a
}
}
>
}
F = \{ <a,b> , <a, \{a\}> , <\{a\} , \{a, \{a\}\}> \}
F={ <a,b>,<a,{ a}>,<{ a},{ a,{ a}}>}
Reference resources : 【 Set theory 】 Binary relationship ( Domain of definition | range | Domain | Inverse operation | Reverse composition operation | Limit | image | Single root | Single value | The nature of composition operation ) 5、 ... and 、 Relationship constraints
1. seek
F
↾
{
a
}
F \upharpoonright \{a\}
F↾{ a}
F
F
F Ordered pairs in sets , The first element is
{
a
}
\{a\}
{ a} An ordered pair of elements in a set , The set of these ordered pairs is
F
F
F aggregate stay
{
a
}
\{a\}
{ a} Restrictions on sets ;
F
↾
{
a
}
=
{
<
a
,
b
>
,
<
a
,
{
a
}
>
}
F \upharpoonright \{a\} = \{ <a,b> , <a, \{a\}> \}
F↾{ a}={ <a,b>,<a,{ a}>}
2. seek
F
↾
{
{
a
}
}
F \upharpoonright \{\{a\}\}
F↾{ { a}}
F
F
F Ordered pairs in sets , The first element is
{
{
a
}
}
\{\{a\}\}
{ { a}} An ordered pair of elements in a set ,
{
{
a
}
}
\{\{a\}\}
{ { a}} The elements in the set are
{
a
}
\{a\}
{ a} , The set of these ordered pairs is
F
F
F aggregate stay
{
{
a
}
}
\{\{a\}\}
{ { a}} Restrictions on sets ;
F
↾
{
{
a
}
}
=
{
<
{
a
,
{
a
}
}
>
}
F \upharpoonright \{\{a\}\} = \{ <\{a, \{a\}\}> \}
F↾{ { a}}={ <{ a,{ a}}>}
3. seek
F
↾
{
a
,
{
a
}
}
F \upharpoonright \{a, \{a\}\}
F↾{ a,{ a}}
F
F
F Ordered pairs in sets , The first element is
{
a
,
{
a
}
}
\{a, \{a\}\}
{ a,{ a}} The elements in the collection That's right , The set of these ordered pairs is
F
F
F aggregate stay
{
a
,
{
a
}
}
\{a, \{a\}\}
{ a,{ a}} Restrictions on sets ;
F
↾
{
a
,
{
a
}
}
=
{
<
a
,
b
>
,
<
a
,
{
a
}
>
,
<
{
a
}
,
{
a
,
{
a
}
}
>
}
F \upharpoonright \{a, \{a\}\} = \{ <a,b> , <a, \{a\}> , <\{a\} , \{a, \{a\}\}> \}
F↾{ a,{ a}}={ <a,b>,<a,{ a}>,<{ a},{ a,{ a}}>}
4. seek
F
−
1
↾
{
{
a
}
}
F^{-1} \upharpoonright \{\{a\}\}
F−1↾{ { a}}
F
−
1
=
{
<
b
,
a
>
,
<
{
a
}
,
a
>
,
<
{
a
,
{
a
}
}
,
{
a
}
>
}
F^{-1} = \{ <b, a> , <\{a\}, a> , <\{a, \{a\}\}, \{a\} > \}
F−1={ <b,a>,<{ a},a>,<{ a,{ a}},{ a}>}
F
−
1
F^{-1}
F−1 Ordered pairs in sets , The first element is
{
{
a
}
}
\{\{a\}\}
{ { a}} The elements in the collection That's right , The set of these ordered pairs is
F
−
1
F^{-1}
F−1 aggregate stay
{
{
a
}
}
\{\{a\}\}
{ { a}} Restrictions on sets ;
F
−
1
↾
{
{
a
}
}
=
{
<
{
a
}
,
a
>
}
F^{-1} \upharpoonright \{\{a\}\} = \{ <\{a\}, a> \}
F−1↾{ { a}}={ <{ a},a>}
Four 、 Like operation examples
F
=
{
<
a
,
b
>
,
<
a
,
{
a
}
>
,
<
{
a
}
,
{
a
,
{
a
}
}
>
}
F = \{ <a, b> , <a, \{ a \}> , <\{ a \} , \{ a, \{a\} \}> \}
F={ <a,b>,<a,{ a}>,<{ a},{ a,{ a}}>}
Reference resources : 【 Set theory 】 Binary relationship ( Domain of definition | range | Domain | Inverse operation | Reverse composition operation | Limit | image | Single root | Single value | The nature of composition operation ) 6、 ... and 、 Image of relationship
F
F
F Assemble in
A
A
A Collective image , yes
F
F
F Assemble in
A
A
A Limited on the set range ;
1.
F
[
{
a
}
]
F[\{a\}]
F[{ a}]
F
F
F Assemble in
{
a
}
\{a\}
{ a} The image on the set , yes
F
F
F Assemble in
{
a
}
\{a\}
{ a} The value range of the restriction on the set ,
F
F
F Assemble in
{
a
}
\{a\}
{ a} The limit on the set is
{
<
a
,
b
>
,
<
a
,
{
a
}
>
}
\{ <a, b> , <a, \{ a \}> \}
{ <a,b>,<a,{ a}>} , Corresponding
F
F
F Assemble in
{
a
}
\{a\}
{ a} On the set, it looks like
{
b
,
{
a
}
}
\{ b, \{a\} \}
{ b,{ a}}
F
[
{
a
}
]
=
{
b
,
{
a
}
}
F[\{a\}] = \{ b, \{a\} \}
F[{ a}]={ b,{ a}}
2.
F
[
{
a
,
{
a
}
}
]
F[\{a, \{a\}\}]
F[{ a,{ a}}]
F
F
F Assemble in
{
a
,
{
a
}
}
\{a, \{a\}\}
{ a,{ a}} The image on the set , yes
F
F
F Assemble in
{
a
,
{
a
}
}
\{a, \{a\}\}
{ a,{ a}} The value range of the restriction on the set ,
F
F
F Assemble in
{
a
,
{
a
}
}
\{a, \{a\}\}
{ a,{ a}} The limit on the set is
{
<
a
,
b
>
,
<
a
,
{
a
}
>
,
<
{
a
}
,
{
a
,
{
a
}
}
>
}
\{ <a, b> , <a, \{ a \}> , <\{ a \} , \{ a, \{a\} \}> \}
{ <a,b>,<a,{ a}>,<{ a},{ a,{ a}}>} , Corresponding
F
F
F Assemble in
{
a
,
{
a
}
}
\{a, \{a\}\}
{ a,{ a}} On the set, it looks like
{
b
,
{
a
}
,
{
a
,
{
a
}
}
\{ b, \{a\} , \{ a, \{a\} \}
{ b,{ a},{ a,{ a}}
F
[
{
a
,
{
a
}
}
]
=
{
b
,
{
a
}
,
{
a
,
{
a
}
}
F[\{a, \{a\}\}] = \{ b, \{a\} , \{ a, \{a\} \}
F[{ a,{ a}}]={ b,{ a},{ a,{ a}}
3.
F
−
1
[
{
a
}
]
F^{-1}[\{a\}]
F−1[{ a}]
F
−
1
=
{
<
b
,
a
>
,
<
{
a
}
,
a
>
,
<
{
a
,
{
a
}
}
,
{
a
}
>
}
F^{-1} = \{ <b, a> , <\{a\}, a> , <\{a, \{a\}\}, \{a\} > \}
F−1={ <b,a>,<{ a},a>,<{ a,{ a}},{ a}>}
F
−
1
F^{-1}
F−1 Assemble in
{
a
}
\{a\}
{ a} The image on the set , yes
F
−
1
F^{-1}
F−1 Assemble in
{
a
}
\{a\}
{ a} The value range of the restriction on the set ,
F
−
1
F^{-1}
F−1 Assemble in
{
a
}
\{a\}
{ a} The limit on the set is
∅
\varnothing
∅ , Corresponding
F
−
1
F^{-1}
F−1 Assemble in
{
a
}
\{a\}
{ a} On the set, it looks like
∅
\varnothing
∅
F
−
1
[
{
a
}
]
=
∅
F^{-1}[\{a\}] = \varnothing
F−1[{ a}]=∅
4.
F
−
1
[
{
{
a
}
}
]
F^{-1}[\{ \{a\} \}]
F−1[{ { a}}]
F
−
1
=
{
<
b
,
a
>
,
<
{
a
}
,
a
>
,
<
{
a
,
{
a
}
}
,
{
a
}
>
}
F^{-1} = \{ <b, a> , <\{a\}, a> , <\{a, \{a\}\}, \{a\} > \}
F−1={ <b,a>,<{ a},a>,<{ a,{ a}},{ a}>}
F
−
1
F^{-1}
F−1 Assemble in
{
{
a
}
}
\{ \{a\} \}
{ { a}} The image on the set , yes
F
−
1
F^{-1}
F−1 Assemble in
{
{
a
}
}
\{ \{a\} \}
{ { a}} The value range of the restriction on the set ,
F
−
1
F^{-1}
F−1 Assemble in
{
{
a
}
}
\{ \{a\} \}
{ { a}} The limit on the set is
<
{
a
}
,
a
>
<\{a\}, a>
<{ a},a> , Corresponding
F
−
1
F^{-1}
F−1 Assemble in
{
{
a
}
}
\{ \{a\} \}
{ { a}} On the set, it looks like
{
a
}
\{a\}
{ a}
F
−
1
[
{
{
a
}
}
]
=
{
a
}
F^{-1}[\{ \{a\} \}] = \{a\}
F−1[{ { a}}]={ a}
边栏推荐
- Joint set search: merge intervals and ask whether two numbers are in the same set
- 2022 registration of G2 utility boiler stoker examination and G2 utility boiler stoker reexamination examination
- 4 years of experience to interview test development, 10 minutes to end, ask too
- 逆袭大学生的职业规划
- Number of uniform strings of leetcode simple problem
- 怎么用Kotlin去提高生产力:Kotlin Tips
- 因子选股-打分模型
- 2022 tea master (intermediate) examination questions and tea master (intermediate) examination skills
- Arthas watch grabs a field / attribute of the input parameter
- [set theory] binary relation (example of binary relation on a | binary relation on a)
猜你喜欢

Php+mysql registration landing page development complete code

The usage of micro service project swagger aggregation document shows all micro service addresses in the form of swagger grouping
X-ray normal based contour rendering

Preliminary cognition of C language pointer

Leetcode simple question: check whether the string is an array prefix
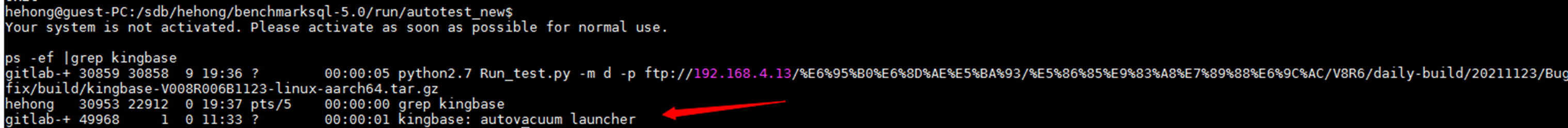
When using the benchmarksql tool to test the concurrency of kingbasees, there are sub threads that are not closed in time after the main process is killed successfully

JVM原理简介
![[fxcg] market analysis today](/img/ac/294368e3496a5b808b38833053ee81.jpg)
[fxcg] market analysis today
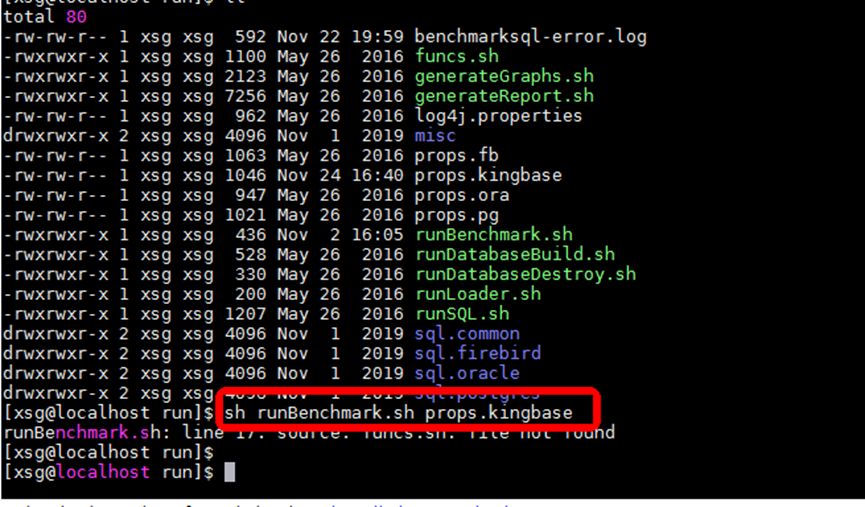
FuncS sh file not found when using the benchmarksql tool to test kingbases
Web - Information Collection
随机推荐
Hj35 serpentine matrix
Crazy scientist
Writing skills of multi plate rotation strategy -- strategy writing learning materials
Smart contract security audit company selection analysis and audit report resources download - domestic article
[literature reading] sparse in deep learning: practicing and growth for effective information and training in NN
2022 registration of G2 utility boiler stoker examination and G2 utility boiler stoker reexamination examination
SSM based campus part-time platform for College Students
有道云笔记
FFMpeg example
Pyqt control part (II)
Reptile exercise 02
Know that Chuangyu cloud monitoring - scanv Max update: Ecology OA unauthorized server request forgery and other two vulnerabilities can be detected
The least operation of leetcode simple problem makes the array increment
The simple problem of leetcode: dismantling bombs
STM32 reverse entry
[dynamic programming] subsequence problem
Basic use of continuous integration server Jenkins
GFS distributed file system (it's nice to meet it alone)
[PCL self study: filtering] introduction and use of various filters in PCL (continuously updated)
2022 t elevator repair simulation examination question bank and t elevator repair simulation examination question bank