当前位置:网站首页>Web - Information Collection
Web - Information Collection
2022-07-03 04:18:00 【Stars return to the wild】
List of articles
Information gathering
One 、 Domain name information
1. Whois Inquire about
whois It refers to the information left during domain name registration , For example, leave the administrator's name 、 Phone number 、 mailbox . After knowing the domain name of the target , The first thing we need to do is to get the domain name whois Information , Because the domain name registrant may be the website administrator Manager , You can try social work 、 tricks , Check whether other domain names are registered to expand the scope of attack .
1.1 Check the website
Love station Tool Network https://whois.aizhan.com
Home of stationmaster http://whois.chinaz.com
VirusTotal https://www.virustotal.com
Through these websites, you can query the relevant information of the domain name , Such as domain name service providers 、 Domain name owner , And their email 、 Telephone 、 Address etc. .
With secdriver.com For example :
Use love station tool network to query the website , Successfully inquired the Registrar of the website 、 Creation time 、 Update time 、 Domain name server and other information .
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-ZqhjFD49-1644732756755)(C:\Users\paranoia\AppData\Roaming\Typora\typora-user-images\image-20220211200533401.png)]](/img/b2/ffb06495f106b75449f920847fe176.jpg)
1.2 kali Tools
Use kali To query the website , The order is as follows :
whois domain name
example :whois secdriver.com
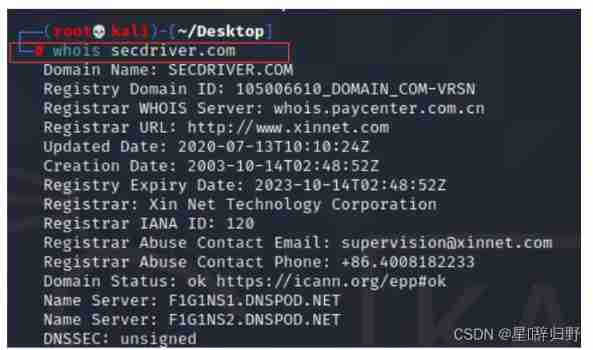
2. Record information inquiry
Website filing is in accordance with national laws and regulations , The owner of the website needs to apply to the relevant state departments for filing , This is a kind of website management of the Ministry of information industry of the people's Republic of China , In order to prevent the occurrence of illegal website business activities on the Internet . Mainly for domestic websites , If the website is set up in other countries , There is no need to file .
The following websites are commonly used :
ICP Record inquiry network :http://www.beianbeian.com
Check the inner eye :http://www.tianyancha.com
National Internet security management platform :http://www.beian.gov.cn/portal/recordQuery
Using the national Internet security management platform, the query results are as follows :
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-jmXQQ1x6-1644732756761)(C:\Users\paranoia\AppData\Roaming\Typora\typora-user-images\image-20220213111955508.png)]](/img/7f/44957a196f3761a8868008881cd962.jpg)
Two 、 Subdomain information
www.baidu.com
Root domain name com
The main domain name baidu.com
subdomain (baidu.com) www.baidu.com
Subdomain name is also called secondary domain name , It refers to the domain name under the top-level domain name . Suppose our target network is relatively large , It's obviously irrational to start directly from the main domain , Because for a goal of this size , Generally, its main domain is the key protection area , So it's better to enter a sub domain of the target first , Then find a way to detour close to the real goal .
1. ip Inquire about
ping secdriver.com
nslookup secdriver.com
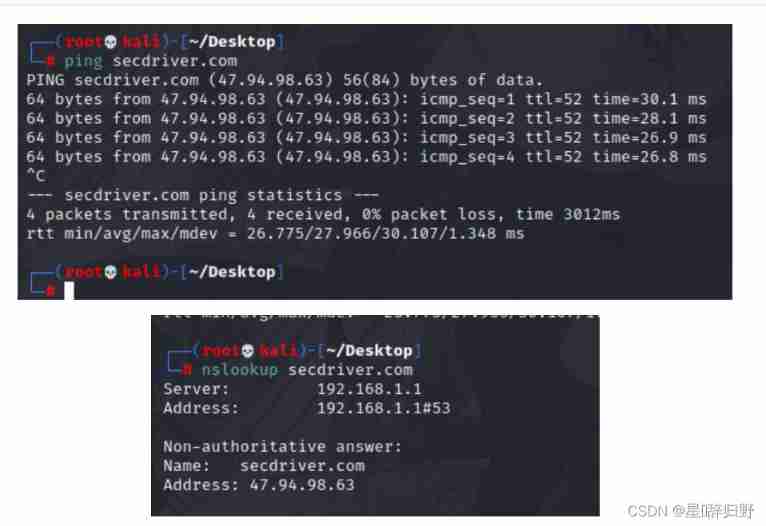
2. Website query
VirusTotal https://www.virustotal.com
fofa https://fofa.info/
Use VirusTotal Inquire about : Enter the website and click SEARCH-》 Click on RELATIONS View query results
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-EDl2eJ52-1644732756769)(C:\Users\paranoia\AppData\Roaming\Typora\typora-user-images\image-20220213114408959.png)]](/img/5b/23402d93eb80cc6a37bedd0ef6f377.jpg)
Use fofa Inquire about
sentence :domain="secdriver.com"
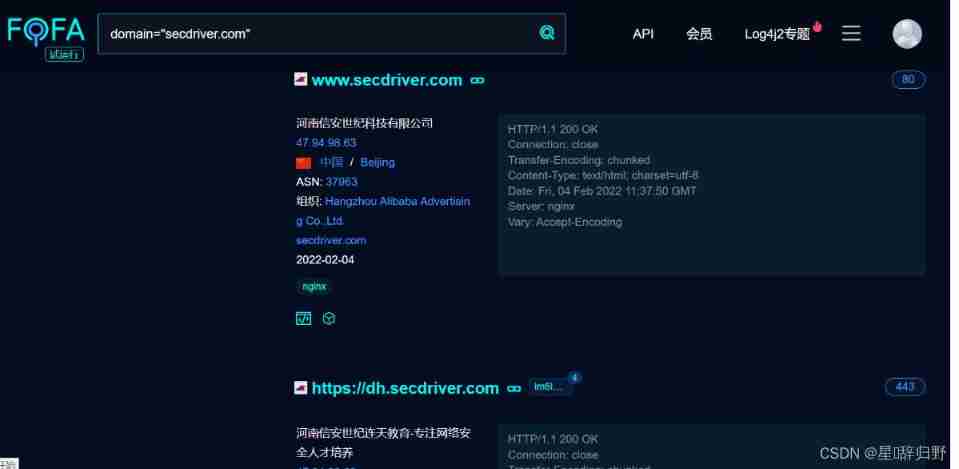
3. Tool scan
Use Layer Subdomain excavator
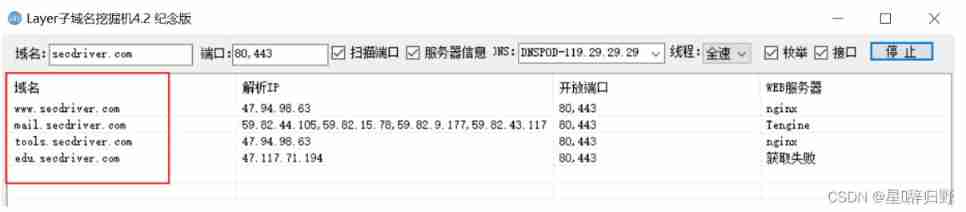
3、 ... and 、 Port information
1. Plug in detection
Installation of Firefox browser fofa pro view and shodan plug-in unit 
2. Tool scan
2.1 nmap
// Port information detection
nmap -sV 192.168.81.148 -p 3389,5985,6588,999,21,80 -A
// Scan common ports
nmap -sT 10.10.1.130 -p 80,89,8000,9090,1433,1521,3306,5432,445,135,443,873,5984,6379,7001,7002,9200,930
0,11211,27017,27018,50000,50070,50030,21,22,23,2601,3389
// scanning 127.0.0.1 front 3000 Ports
nmap -sT 127.0.0.1 -p 1-3000
// Before fast scanning 3000 Ports
nmap -sS 127.0.0.1 -p 1-3000

2.2 masscan
masscan 47.94.98.63 -p 1-3000 --rate=3000
2.3 Royal sword port scan
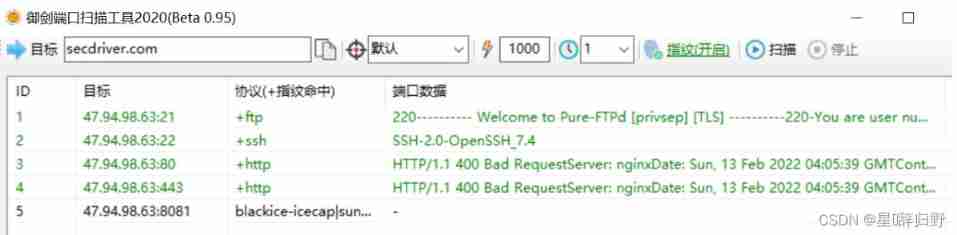
Four 、C Section and side station
1. Side station
It refers to other websites deployed on the server
Sidenote means to start with other websites on the same server , Raise the right , And then the server side is turned off , Naturally, the website was terminated
sidenote : Penetration scheme of different sites on the same server
2. C paragraph
C Paragraph refers to, for example 192.168.1.4,192 yes A paragraph ,168 yes B paragraph ,1 yes C paragraph ,4 yes D paragraph
C Segment sniffer is about taking the same C Server under segment , That is to say D paragraph 1-255 A server in
C paragraph : Penetration scheme of different servers in the same network segment
3. Check the website online
Same as IP Website query ,C Segment query , On-line C paragraph , Side tools :https://www.webscan.cc/
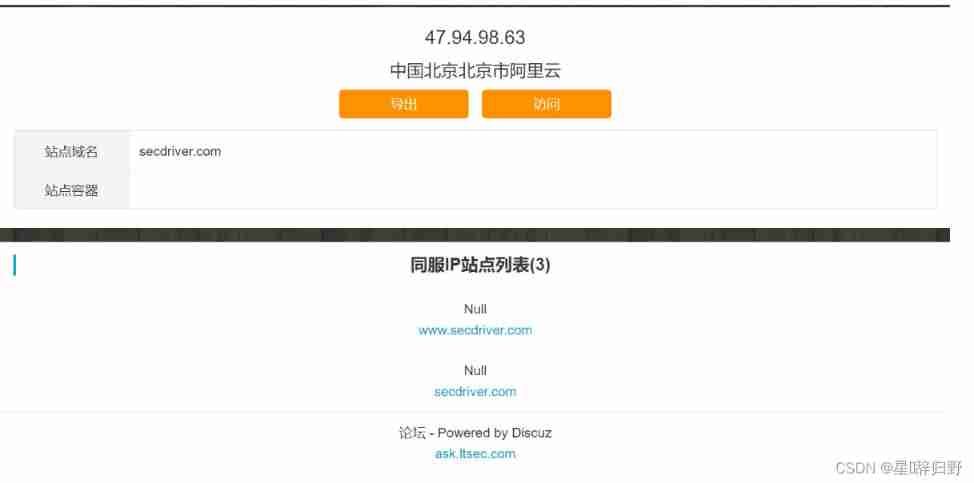
You can also use the Yujian port scanning tool to scan C paragraph
5、 ... and 、 catalog information
Sensitive files can be scanned through directory scanning , Background file , Database files and information disclosure files .
dirsearch Common parameters :
Common parameters :
-u Specify web site
-e Parameter specifies the site type php, jsp, asp, aspx, do, action, cgi, pl, html, htm, js, json,
tar.gz, bak
-w Specify dictionary scan
-t Specified thread
-random-agents Use random UA
python dirsearch -u http:// The target site -e* ( Website type )
robots agreement
robots.txt
robots.txt It's an agreement , Not an order .robots.txt It is the first file that the search engine should view when visiting the website .robots.txt Files tell the crawler what files can be viewed on the server .
6、 ... and 、 fingerprint identification
stay web In the process of infiltration ,Web Fingerprint identification is an important step in information collection , Through some open source tools 、 Platform or manual inspection CMS The system is public CMS Program or secondary development is crucial , Can accurately obtain CMS type 、Web Service component type and version information can help security engineers quickly and effectively verify known vulnerabilities . During the penetration test of the target , Target cms Is very important information , With a goal cms, You can use related bug To test , Conduct code audit, etc .
1. Recognition mode
Website specific files
Such as /templets/default/style/dedecms.css—dedecms
Website unique files md5
Such as favicon.ico, But the file can be modified to make it inaccurate .
Website file naming rules
Return the keyword of the header Such as header=“rememberMe=deleteMe”
Web keywords
Such as /data/sessions/index.html——dedecms/data/admin/ver.txt
Url features
Meta features
Script features
robots.txt
Website path characteristics
Website static resources
Crawler website directory information
2. The object of fingerprint recognition
CMS Information : Like a big man CMS、 DedeCms 、 The empire CMS、phpcms、ecshop etc. ;
The front-end technology : such as HTML5、jquery、bootstrap、pure、ace etc. ;
Web The server : such as Apache、lighttpd, Nginx, IIS etc. ;
application server : such as Tomcat、Jboss、weblogic、websphere etc. ;
development language : such as PHP、Java、Ruby、Python、C# etc. ;
Operating system information : such as linux、win2008、win7、kali、centos etc. ;
CDN Information : Whether to use CDN, Such as cloudflare、360cdn、365cyd、yunjiasu etc. ;
WAF Information : Whether to use waf, Such as Topsec、safedog、Yundun etc. ;
IP And domain name information :IP And domain name registration information 、 Service provider information, etc ;
Port information : Some software or platforms also detect common ports open to the server .
3. Identification tools
Tools :whatweb
whatweb domain name // Single domain name identification
whatweb -i target.txt --log-brief=result.txt
Online identification :
http://pentest.gdpcisa.org/whatcms
Plug in class :Wapplyzer
4. CDN distinguish
CDN It's a content distribution network .CDN It is an intelligent virtual network based on the existing network , Rely on edge servers deployed everywhere .
Load balancing content distribution through the central platform , Scheduling and other functional modules , Let users get the content they need nearby , Reduce network congestion , Improve user access response speed and hit rate .
CDN The basic principle is to widely use various cache servers , Distribute these cache servers to areas or networks where users' access is relatively concentrated .
When users visit the website , Use the global load technology to make users' access Point to the nearest working cache server , The cache server responds directly to user requests .
distinguish CDN:
nslookup
Multifocal ping Website :https://ping.chinaz.com/
https://tools.ipip.net/ping.phpOnline identification :https://www.cdnplanet.com/tools/cdnfinder
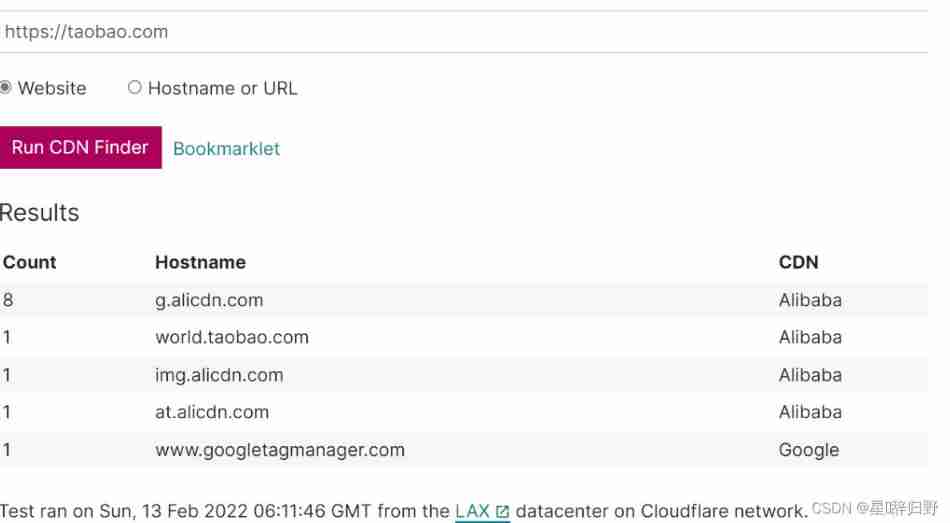
边栏推荐
- Mila, University of Ottawa | molecular geometry pre training with Se (3) invariant denoising distance matching
- Introduction to eth
- The longest subarray length with a positive product of 1567 recorded by leecode
- [set theory] inclusion exclusion principle (including examples of exclusion principle)
- 【刷题篇】接雨水(一维)
- Deep dive kotlin synergy (20): build flow
- P35-P41 fourth_ context
- How do you use lodash linking function- How do you chain functions using lodash?
- Idea shortcut keys
- Interface in TS
猜你喜欢

300+ documents! This article explains the latest progress of multimodal learning based on transformer
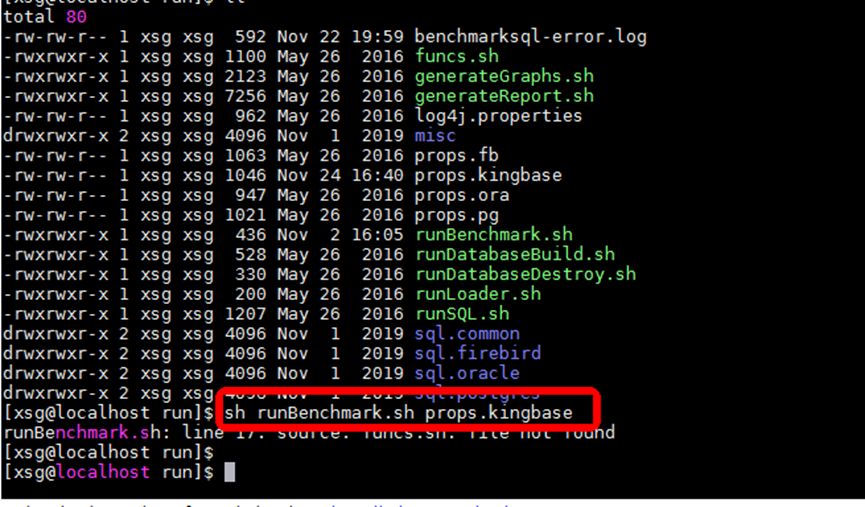
使用BENCHMARKSQL工具对KingbaseES执行测试时报错funcs sh file not found
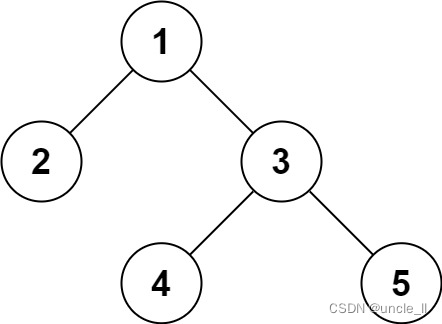
leetcode:297. Serialization and deserialization of binary tree
Solve BP Chinese garbled code
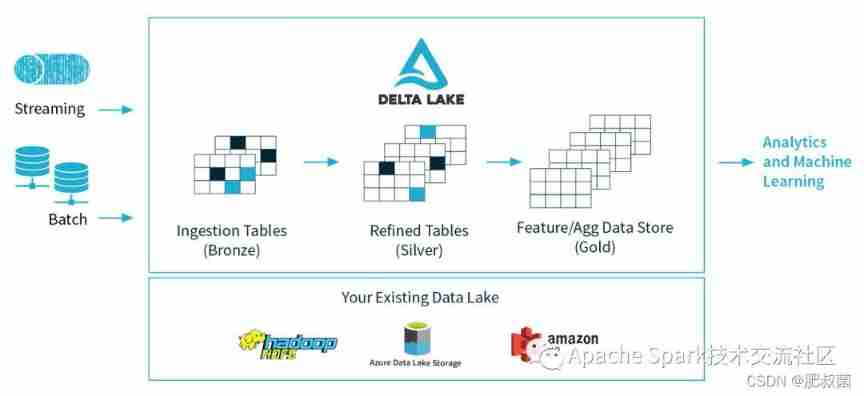
Data Lake three swordsmen -- comparative analysis of delta, Hudi and iceberg
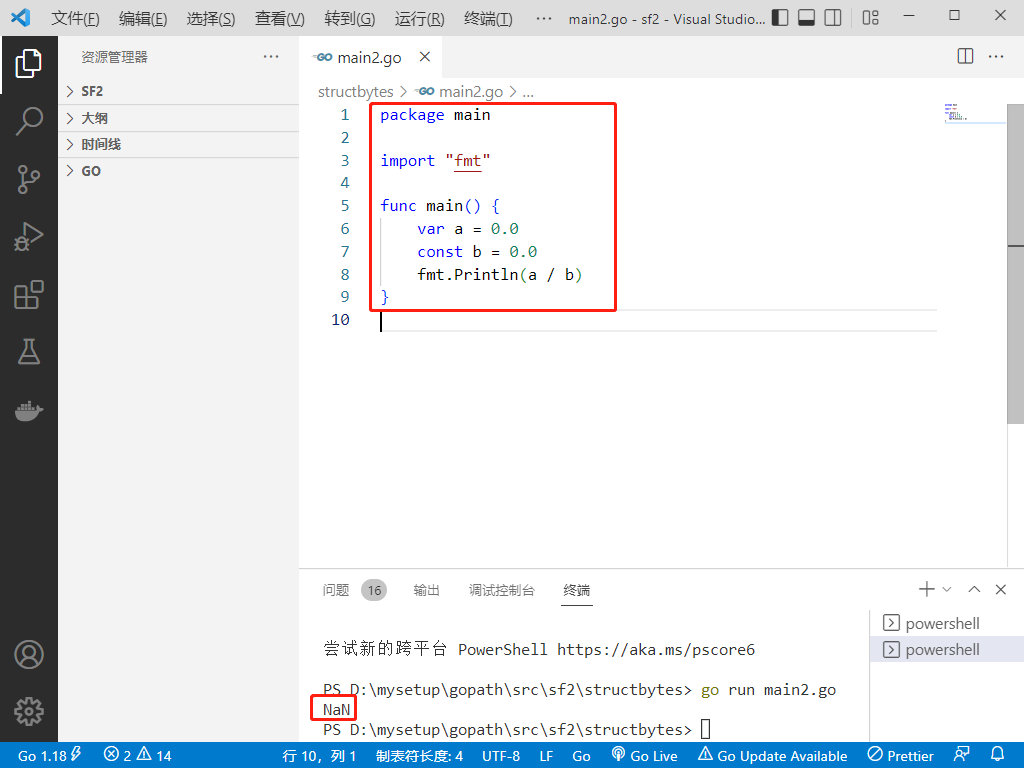
2022-07-02: what is the output of the following go language code? A: Compilation error; B:Panic; C:NaN。 package main import “fmt“ func main() { var a =
![[文献阅读] Sparsity in Deep Learning: Pruning and growth for efficient inference and training in NN](/img/7e/50fa6f65b5a4f0bb60909f57daff56.png)
[文献阅读] Sparsity in Deep Learning: Pruning and growth for efficient inference and training in NN

CVPR 2022 | Dalian Institute of technology proposes a self calibration lighting framework for low light level image enhancement of real scenes
The latest activation free version of Omni toolbox

Is it better to speculate in the short term or the medium and long term? Comparative analysis of differences
随机推荐
跨境电商多商户系统怎么选
Nodejs Foundation: shallow chat URL and querystring module
300+ documents! This article explains the latest progress of multimodal learning based on transformer
The time has come for the domestic PC system to complete the closed loop and replace the American software and hardware system
leetcode:297. Serialization and deserialization of binary tree
JS native common knowledge
Nat. Comm. | 使用Tensor-cell2cell对细胞通讯进行环境感知去卷积
What's wrong with SD card data damage? How to recover SD card data damage
JS实现图片懒加载
【刷题篇】接雨水(一维)
Sklearn data preprocessing
js实现在可视区内,文字图片动画效果
MySQL create table
[NLP]—sparse neural network最新工作简述
使用BENCHMARKSQL工具对KingbaseES执行测试时报错funcs sh file not found
一名外包仔的2022年中总结
[nlp] - brief introduction to the latest work of spark neural network
Deep dive kotlin synergy (20): build flow
Busycal latest Chinese version
Data Lake three swordsmen -- comparative analysis of delta, Hudi and iceberg