当前位置:网站首页>Talking about data security governance and privacy computing
Talking about data security governance and privacy computing
2022-08-05 02:49:00 【software testnet】
Intelligent digital era rich people's work and life,Will also face many security problems,For example, the data is not stored safely、Unauthorized access of data and privacy leak, etc.In recent years, more data leakage incidents have taken place in,如MongoDB 数据库被入侵、Facebook和SHEIN 数据库泄露等,The citizen privacy caused great harm.Data security governance has become a hot topic of the present people.Calculated on the premise of ensure the safety of user data privacy,It can effectively solve“数据孤岛”问题,Become an important technology to data security protection,Cause the extensive concern of the academic and industry.
相关法律法规
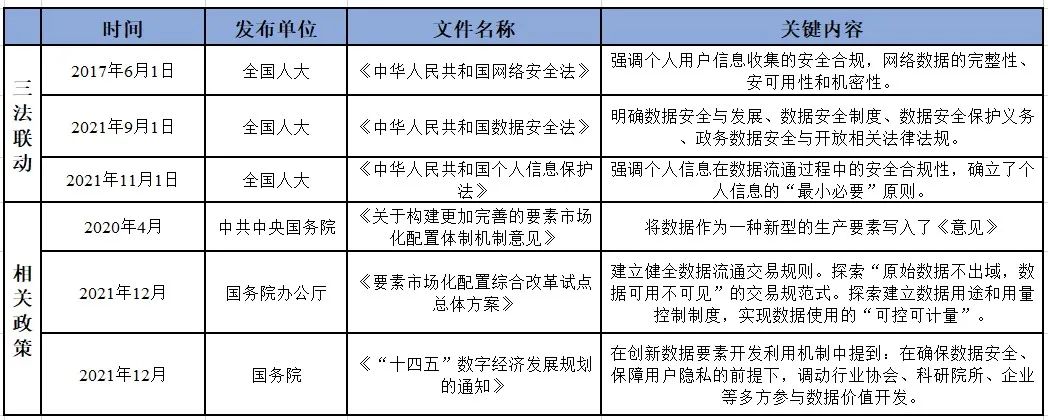
The domestic and foreign data frequent leak,A large number of enterprise's commercial interests、声誉受损.Data security laws and regulations successively promulgated,Supervision constantly update,Enterprises gradually realize the importance of data security governance with urgency.Global massive data safety and privacy protection laws and regulations formulation,如欧盟GDRP《通用数据保护条例》、加州CCPA《California's consumer privacy act》、加拿大PIPEDA《California's consumer privacy act》等.Our main laws and standards as set by the table1所示,In the release of the National People's Congress《数据安全法》、《网络安全法》和《个人信息保护法》The three linkage to,China ushered in the data security management and privacy protection compliance development stage.《数据安全法》Explicitly pointed out that the development of data security、数据安全制度、Data security and protection obligations and open government data security and relevant laws and regulations;《网络安全法》Mainly emphasize the personal user information collection safety compliance、网络数据的完整性、可用性和机密性;《个人信息保护法》Emphasis on personal information in the data flow in the process of security compliance,Establishes a personal information“最小必要”原则.The State Council also issued a number of solutions and advice,Clearly put forward the Suggestions to the flow of data security and planning.
《数据安全法》全文:http://www.npc.gov.cn/npc/c30834/202106/7c9af12f51334a73b56d7938f99a788a.shtml
《网络安全法》全文:http://www.sprd.gov.cn/newsShow.asp?dataID=635
《个人信息保护法》全文:http://www.npc.gov.cn/npc/c30834/202108/a8c4e3672c74491a80b53a172bb753fe.shtml
表1 The flow of data security compliance laws and regulations and the relevant policy
数据安全
Data security is the collection、传输和存储、处理、The safety of each phase and destroy sharing.Each stage is facing the risk of different,Such as acquisition phase data unreliable risks、Storage stage face data reveal that the risk of、Processing phase at risk of privacy data mining, etc,The main task of the data security risk lies in the recognition of these,And take appropriate preventive measures for security.At present enterprise mainly to various safety protection technology is applied to data China to ensure data security,Security company to integrate the various technologies together to form safety products,Such as encryption gateway and intelligent classification grading、脱敏系统,The client may direct the deployment of security products to solve the problem of safety protection.Although at present there are many security products,But still there is no unified security protection for the entire data solution,Main problems in risk management and privacy protection solution has not been fully discussed.Data security is still is often new problems,Safety protection strategy needs to constantly adjust to deal with the complex and changeable environment,How to put forward more security protection in the era of technological innovation model,Is still present and future big important topic in the field of data security.
隐私计算
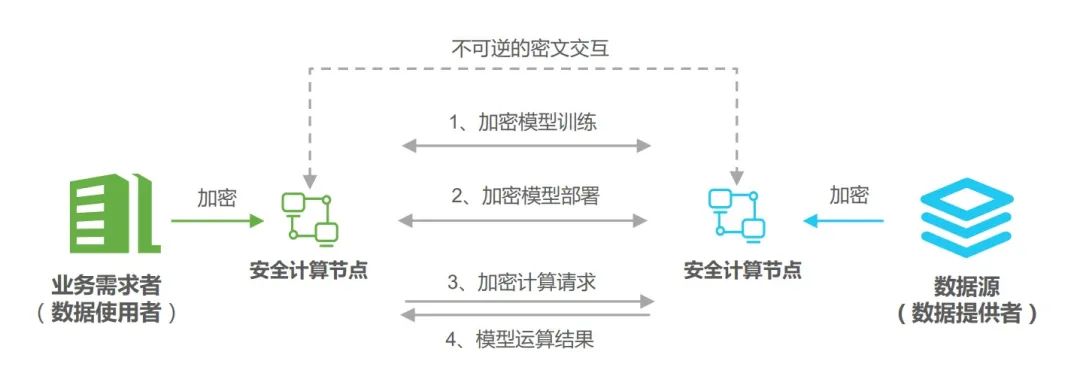
The rapid development of Internet technology,激发了数据要素流通的市场空间.Traditional data circulation mode can't meet the requirements of data security,Needs through innovative technology to realize the security of the data flow.Privacy calculation in guaranteeing data providers don't reveal that under the premise of the original data,对数据进行分析计算,数据以“Available invisible”的方式进行安全流通,能有效的解决“数据孤岛”问题,Become an important technology to data security protection.The various security and privacy calculation of computing technology can control the data usage and dosage of,Do the data“用途可控可计量”.在应用实践中,Privacy computation can also block chain technology to strengthen the“身份认证、访问控制、Calculation and regulatory”The trust mechanism of,As shown in figure shows the data were calculated based on privacy credible circulation.
图1 Based on the data privacy calculating credible circulation
Privacy calculate three kinds of technology implementation ideas:Based on cryptography、融合隐私保护技术的联合建模、可信执行环境.Based on cryptography:Mainly includes the multilateral security calculation,同态加密,差分隐私,A variety of cryptography technology such as zero knowledge proof .The current industry technology vendors usually multilateral security will be calculated as the main technical solution,Cryptography algorithms such as homomorphic encryption have been more applied in business practices,Or with the federal study、The trusted execution environment such as technical solution to carry out the integration application.融合隐私保护技术的联合建模:To take a federal study on technology and the integration of all kinds of privacy protection technology in the technical realization way,The federal study according to participate in the training data set for the client feature information is different,Divided into horizontal federal study、纵向联邦学习和联邦迁移学习.可信执行环境:Take to segregate and measure the privacy data computing environment,Encrypted data and algorithm input executable environment,Foreign only output the final calculated results,The original data and process data in situ, the destruction of,从而实现数据的“可用不可见”.
Privacy includes the following three key calculation scheme:多方安全计算(MPC)、可信联邦计算(TFL)和可信执行环境(TEE)
1 多方安全计算(MPC)
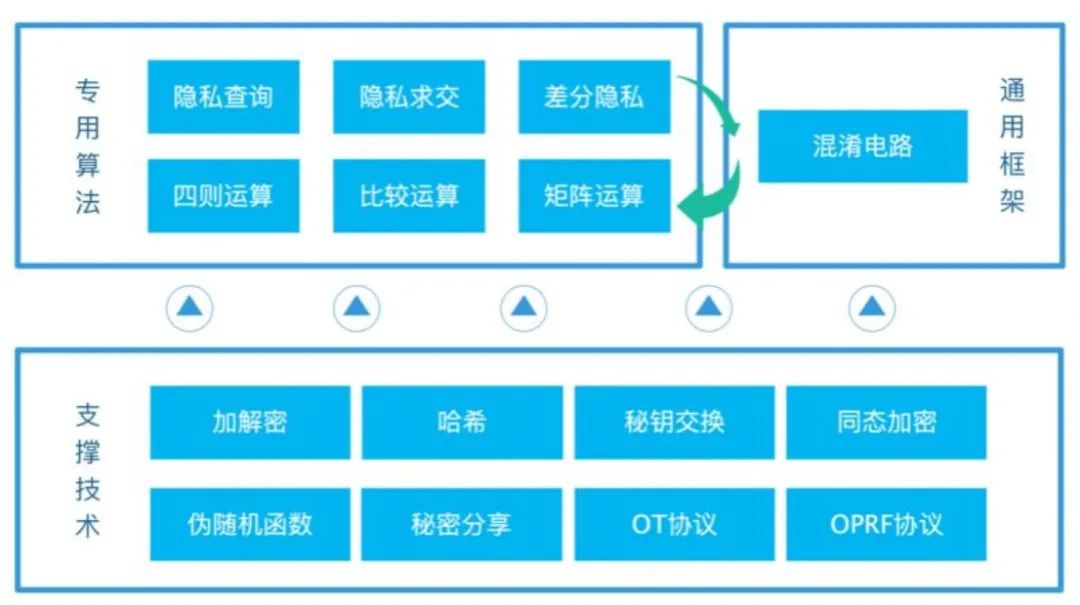
Multiparty secure computing to1986 Years passed by yao period wisdom academician Yao Shi millionaire questions.Two millionaire street encounter,They all want to flaunt wealth,See who is more rich,但是出于隐私,都不想让对方知道自己到底拥有多少财富,如何在不借助第三方的情况下,Let them know who was the more rich.姚氏“百万富翁问题”After the development of,Become a very active research field in modern cryptography,即多方安全计算.MPCCan support multiple players to collaborative computing and output calculated results,Make all parties in addition to the calculation results cannot obtain any other information,From the technical level to realize data available invisible,United mining data value,Broaden the use of data dimension.如图2所示,Multiparty secure computing technology consists of a series of technical,According to the level can be divided into special algorithm layer and supporting technology.
图2 多方安全计算(MPC)技术框架
专用算法:Solve the specific problem constructed by the specialMPC协议,由于是针对性构造并进行优化,Special algorithm efficiency than based on mixed circuit(GC ,Garbled Circuit)The general framework of much higher,Contains the arithmetic、比较运算、矩阵运算、隐私集合求交集、Privacy data query and difference of privacy, etc.
Support technology layer:提供构建MPCThe basic technology to realize,Contains common encryption to decrypt、hash函数、密钥交换、同态加密(HE,Homomorphic Encryption)、Pseudo-random function, etc,还包含MPCThe basic tool:秘密分享(SS,Secret Sharing)、不经意传输协议(OT,Oblivious Transfer)、Casual as the random function(OPRF,Oblivious Pseudorandom Function)等.
2 可信联邦学习(TFL)
联邦学习(FL)由Google于2016年提出,Aims to build a federal learning model based on distributed data sets,In the original data without outbound,Collaborative learning machine learning task mode,Rule out using model parameters/The potential risk of gradient to reconstruct the original data.Any multilateral joint machine learning model,Inevitably the federal study the machine learning paradigm,基于FLCould calculate the quantitative analysis of privacy the pros and cons of various technical protection scheme,To guide the privacy computing algorithm design.Reasonable use including multilateral security calculation(MPC)、可信执行环境(TEE)、同态加密(HE)和差分隐私(DP)Technology integration is,Combined with the distributed machine learning and artificial intelligence algorithm,找到联合建模可信、Feasible and controllable solution,实践中FLThe integration of various kinds of privacy protection technology,这就是“可信联邦学习”的核心概念,Continuously improve the ability of the federal study,协同解决“数据孤岛”和“数据隐私计算”的问题.
3 可信执行环境(TEE)
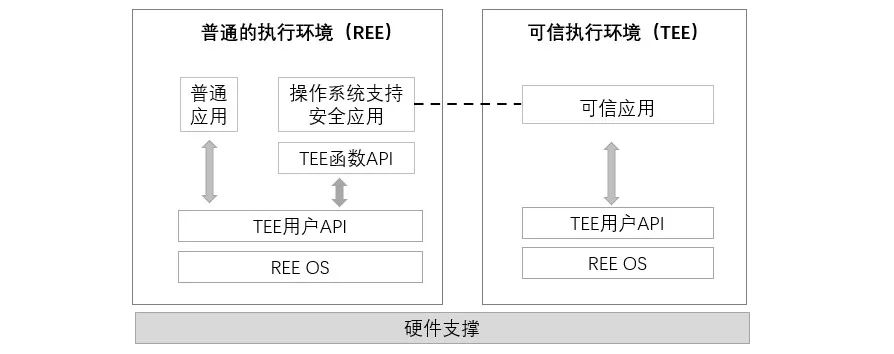
TEE通过可信、Resistance to tamper with the hardware and software to build a credible security environment,在硬件中为敏感数据单独分配一块隔离的内存,All sensitive data in the memory to calculate,并且除了经过授权的接口外,Other parts of the hardware can not access the information isolation in memory.如图3所示,Shows the average execution environment and the comparison of the trusted execution environment,The data in a trusted environment by credible program for processing,In order to protect the program code or data from the operating system、Other applications to steal or tamper with the.
图3 Normal execution environment and comparison of the trusted execution environment
Ordinary application to the underlyingAPICan realize to the realization of the upper business.For the safety of the operating system supports applications,Hardware will break the trusted execution domain,通过TEE函数APIThe underlying userAPI,Complete the trusted computing.
总 结
This to drops the punishment of the company as a typical case,Embodies the country to strengthen network security、数据安全、The importance of personal information protection and protection,Important data processing for relevant enterprises should fully combed the related business、Establish and improve data security system,Compliance operations according to law.In data face“隐私泄露”和“数据孤岛“大背景下,Based on the analysis of the relevant privacy leak and in《网络安全法》《数据安全法》《个人信息保护法》Three laws of privacy protection in China driven by the development of technology.In this paper, how to effectively ensure the data security and privacy of,Introduce readers to the related concepts of data security and privacy protection,Calculation can effectively ensure the security of data privacy,At the same time solve the problem of data island,As an important technology to data security protection,This paper focus on the computing of privacy idea and relevant technical solution,包括多方安全计算、Trusted federal study and trusted execution environment,Provide a reference for the future of privacy protection.
参考文献
[1] Xiao, Z., & Xiao, Y. (2012). Security and privacy in cloud computing. IEEE communications surveys & tutorials, 15(2), 843-859.
[2] Wang, T., Mei, Y., Jia, W., Zheng, X., Wang, G., & Xie, M. (2020). Edge-based differential privacy computing for sensor–cloud systems. Journal of Parallel and Distributed computing, 136, 75-85.
[3] F. Deng-Guo, Z. Min, L. Hao, Big Data Security and Privacy Protection, Chinese Journal of
Computers, 37 (2014), 246–258.
[4] Goldreich, O. (1998). Secure multi-party computation. Manuscript. Preliminary version, 78, 110.
[5] Mo, F., Haddadi, H., Katevas, K., Marin, E., Perino, D., & Kourtellis, N. (2021, June). PPFL: privacy-preserving federated learning with trusted execution environments. In Proceedings of the 19th Annual International Conference on Mobile Systems, Applications, and Services (pp. 94-108).
[6] Fan Tingyu & Yuan Ke. (2021). Current Status and Trends of Big Data Security Research (2010- 2019)-Visual Analysis Based on CiteSpace. Software Guide (05), 243-248.
[7] Sabt, M., Achemlal, M., & Bouabdallah, A. (2015, August). Trusted execution environment: what it is, and what it is not. In 2015 IEEE Trustcom/BigDataSE/ISPA (Vol. 1, pp. 57-64). IEEE.
[8] https://www.iresearch.com.cn/Detail/report?id=3958&isfree=0
[9] https://zhuanlan.zhihu.com/p/384759946
边栏推荐
- 优炫数据库的单节点如何转集群
- Error: Not a signal or slot declaration
- C student management system Find student nodes based on student ID
- Note that Weifang generally needs to pay attention to issuing invoices
- Matlab map with color representation module value size arrow
- Ant Sword Advanced Module Development
- The 22-07-31 weeks summary
- Regular expression to match a certain string in the middle
- How to sort multiple fields and multiple values in sql statement
- 【Daily Training】1403. Minimum Subsequence in Non-Increasing Order
猜你喜欢
QT language file production

Everyone in China said data, you need to focus on core characteristic is what?

How Jin Cang database correctness verification platform installation file
Beidou no. 3 short message terminal high slope in open-pit mine monitoring programme
C language implements a simple number guessing game
Cloud Native (32) | Introduction to Platform Storage System in Kubernetes
Go 微服务开发框架 DMicro 的设计思路
基于左序遍历的数据存储实践
Ant Sword Advanced Module Development
word column notes
随机推荐
02 [Development Server Resource Module]
The problem of lack of dynamic library "libtinfo.so.5" in ksql application under UOS system
mysql树状结构查询问题
Open Source License Description LGPL
正则表达式,匹配中间的某一段字符串
语法基础(变量、输入输出、表达式与顺序语句)
[机缘参悟-60]:《兵者,诡道也》-2-孙子兵法解读
Introduction to SDC
leetcode 15
shell语句修改txt文件或者sh文件
云原生(三十二) | Kubernetes篇之平台存储系统介绍
627. 变更性别
2022-08-04: Input: deduplicated array arr, the numbers in it only contain 0~9.limit, a number.Return: The maximum number that can be spelled out with arr if the requirement is smaller than limit.from
The Tanabata copywriting you want has been sorted out for you!
链表的简单描述及代码的简单实现
Multithreading (2)
HDU 1114: Piggy-Bank ← The Complete Knapsack Problem
QT:神奇QVarient
Tencent Cloud [Hiflow] New Era Automation Tool
采用redis缓存的linux主从同步服务器图片硬盘满了移到新目录要修改哪些指向