当前位置:网站首页>[computer level 3 information security] overview of information security assurance
[computer level 3 information security] overview of information security assurance
2022-07-28 05:13:00 【Happy star】
1、 The emergence and development of information technology , It has roughly experienced the following three stages : The first stage , The invention of telecommunication technology ( Telegraph and telephone 、 The radio 、 The TV ) The second stage , The development of computer technology ( Turing machine theory 、 Von Neumann architecture 、 The integrated circuit 、 Large scale integrated circuit computer ) The third stage , Use of the Internet (ARPAnet、TCP/IP agreement 、 The Internet )
2、 The negative impact of information technology :
Information flooding 、 Information pollution 、 Information crime
3、 Information security development stage :
Communication security phase
Contemporary information security originated from 20 century 40 Communication confidentiality in the s . During this period , People are mainly concerned about the security of information in the communication process , namely “ Confidentiality ”.
1949 Shannon published 《 Communication theory of secure system 》, First of all, the issue of information confidentiality is comprehensively discussed from the perspective of information theory .Computer security phase
20 century 60 Age and 70 years , The concept of computer security began to be gradually implemented .
1965 In, the United States first proposed computer security (COMPUSEC). At this time, computers are mainly used in the military ,1969 Year of Ware The report initially raised the problem of computer security and its evaluation .
20 century 70 The S is the founding era of computer security .
20 century 80 A landmark feature of the S is the standardization of computer security .Information security stage
20 century 90 After the age
Main concern “ early warning 、 Protect 、 testing 、 Respond to 、 recovery 、 counterattack ” The whole process
4、 Modern information security mainly includes :
( One ) Safety of operating system , Including strict and scientific management , Such as the organization and management of information network system 、 To supervise and inspect ; Establishment of rules and regulations 、 Implement and improve ; The sense of responsibility of managers 、 Foresight 、 Vigilance, etc ; law 、 Policy protection , Such as whether the user has legal rights , Whether the policy allows... Etc ; Physical control security , If the machine room is locked 、 Line safety 、 Suitable environment ; Hardware operation safety ; Operating system security , Such as whether the data file is protected ; disasters 、 Fault recovery ; Deadlock avoidance and release ; Prevent electromagnetic information leakage, etc .
( Two ) Security of system information , Including user password authentication ; User access control ; Data access rights 、 Mode control ; Audit trail ; Data encryption, etc .
5、 The basic attribute of information security :
integrity 、 Confidentiality 、 Usability 、 Controllability 、 Non repudiation ( Non repudiation )
6、 Information security technology
(1) Core basic security technology ( Mainly including cryptography );
(2) Security infrastructure technology ( Identification and certification technology 、 Authorization and access control technology );
(3) Infrastructure security technology ( Host system security technology 、 Network system security technology, etc );
(4) Apply security technology ( Network and system security attack technology 、 Network and system security protection and response technology 、 Safety audit and responsibility identification technology 、 Malicious code detection and Prevention Technology );
(5) Support safety technology ( Information security evaluation technology 、 Information security management technology )
7、P2DR Security model :
P2DR The model is the United States ISS The representative model of dynamic network security system proposed by the company , It consists of four main parts : Strategy (Policy)、 protective (Protection)、 testing (Detection) And response (Response).
8、 Information security technology framework IAFT
IATF The core idea of information security is Defense in depth strategy . Defense in depth strategy is to adopt a multi-level 、 In depth security measures to protect user information and information system security . In defense in depth strategy , personnel 、 Technology and operation There are three main core factors 
Defense in depth strategies prevent attacks that can break through a layer or a class of protection from destroying the entire information infrastructure .
IATF Four technical framework focus areas :
① Protect the local computing environment ;
② Boundary of the protected area ;
③ Protect network and infrastructure ;
④ Protection of supporting infrastructure ;
9、 The content of information security work
① Identify security requirements ;
② Design and implement safety plan ;
③ Information security evaluation ;
④ Information security monitoring and maintenance .

边栏推荐
- 【ARXIV2204】Vision Transformers for Single Image Dehazing
- Professor dongjunyu made a report on the academic activities of "Tongxin sticks to the study of war and epidemic"
- The most detailed installation of windows10 virtual machine, install virtual machine by hand, and solve the problem that the Hyper-V option cannot be found in the home version window
- How does Alibaba use DDD to split microservices?
- Interpreting the source code of cfrunloopref
- Anaconda common instructions
- 【CVPR2022】On the Integration of Self-Attention and Convolution
- Pipe /createpipe
- Offline loading of wkwebview and problems encountered
- 【内功心法】——函数栈帧的创建和销毁(C实现)
猜你喜欢

Simulink automatically generates STM32 code details

数据库日期类型全部为0
Array or object, date operation

Testcafe's positioning, operation of page elements, and verification of execution results
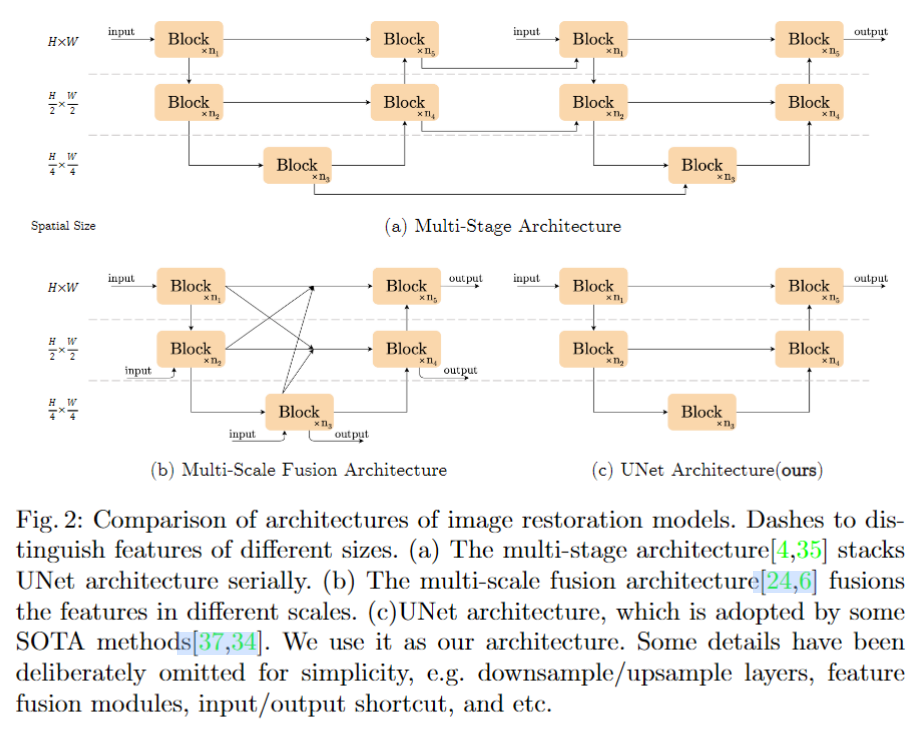
【ARXIV2204】Simple Baselines for Image Restoration

After easycvr is connected to the national standard equipment, how to solve the problem that the equipment video cannot be played completely?

【CPU占用高】software_reporter_tool.exe

11.< tag-动态规划和子序列, 子数组>lt.115. 不同的子序列 + lt. 583. 两个字符串的删除操作 dbc

驾驭EVM和XCM的强大功能,SubWallet如何赋能波卡和Moonbeam

Reading notes of SMT practical guide 1
随机推荐
【ARXIV2204】Vision Transformers for Single Image Dehazing
Applet import project
RT based_ Distributed wireless temperature monitoring system of thread (I)
jsonp 单点登录 权限检验
在ruoyi生成的对应数据库的代码 之后我该怎么做才能做出下边图片的样子
Implementation of simple upload function in PHP development
[learning record] data enhancement 1
After easycvr is connected to the national standard equipment, how to solve the problem that the equipment video cannot be played completely?
What is the reason why the easycvr national standard protocol access equipment is online but the channel is not online?
Using RAC to realize the sending logic of verification code
C language classic 100 question exercise (1~21)
MySQL 默认隔离级别是RR,为什么阿里等大厂会改成RC?
Why is MD5 irreversible, but it may also be decrypted by MD5 free decryption website
驾驭EVM和XCM的强大功能,SubWallet如何赋能波卡和Moonbeam
阿里怎么用DDD来拆分微服务?
How to analyze fans' interests?
【CVPR2022】Multi-Scale High-Resolution Vision Transformer for Semantic Segmentation
When initializing with pyqt5, super() and_ init _ () problems faced by the coordinated use of functions, as well as the corresponding learning and solutions
Transformer -- Analysis and application of attention model
这种动态规划你见过吗——状态机动态规划之股票问题(中)