当前位置:网站首页>Nuclei (2) Advanced - In-depth understanding of workflows, Matchers and Extractors
Nuclei (2) Advanced - In-depth understanding of workflows, Matchers and Extractors
2022-08-04 23:19:00 【Test Dev Kevin】
前面的文章中介绍了nuclei的基础使用方法,可以参考文章:
POCSimulated attack weapon——Nuclei入门(一)
Next, I will focus on explainingnuclei中的三个概念,Workflows、Mathcer和Extractors.These will help you write more complex and efficient detection scripts!
workflows
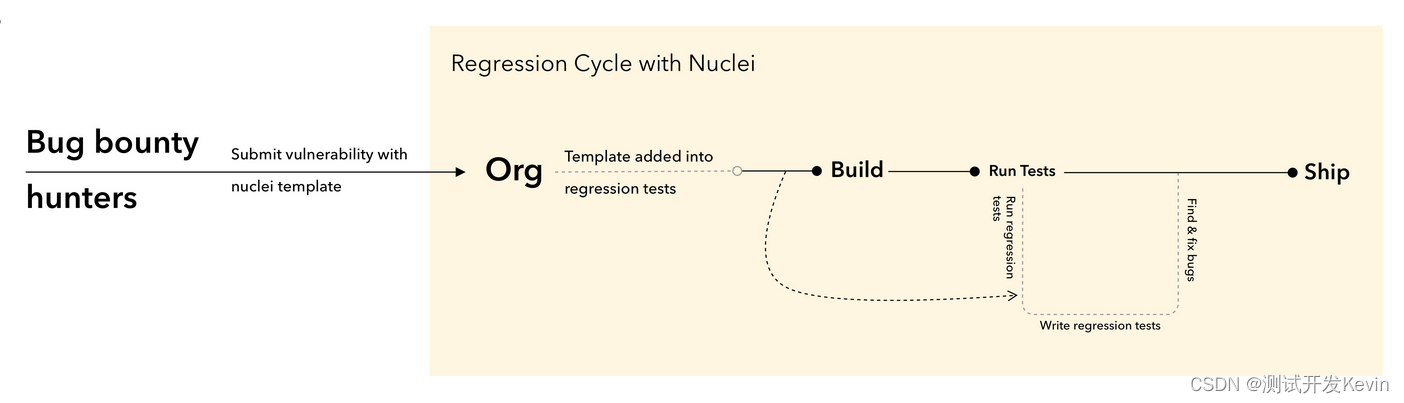
WorkflowsAllows users to customize the execution order of templates,这是使用nuclei最高效的方式,It is officially recommended that users use customWorkflowsThis reduces scan time,提升扫描效率!
- Basic Workflow
例如,定义workflow 扫描files目录下如下yaml
workflows:
- template: files/git-config.yaml
- template: files/svn-config.yaml
- template: files/env-file.yaml
- template: files/backup-files.yaml
- tags: xss,ssrf,cve,lfi- 条件工作流
首先确认springboot-detect.yaml是否正确执行,如果OK,则运行subtemplates下的template,实例如下:
id: springboot-workflow
info:
name: Springboot Security Checks
author: dwisiswant0
workflows:
- template: security-misconfiguration/springboot-detect.yaml
subtemplates:
- template: cves/CVE-2018-1271.yaml
- template: cves/CVE-2018-1271.yaml
- template: cves/CVE-2020-5410.yaml
- template: vulnerabilities/springboot-actuators-jolokia-xxe.yaml
- template: vulnerabilities/springboot-h2-db-rce.yaml运行workflows
nuclei -list http_urls.txt -w workflows/my-workflow.yaml
Matchers
Mathcer顾明思议,Just provide some rules,to compare and match the response results!There are six types in common use
mathcer,如下所示:
- status Integer Comparisons of Part
- size Content Length of Part
- word Part for a protocol
- regex Part for a protocol
- binary Part for a protocol
- dsl Part for a protocol
For example, you want to compare and match the response code,写法如下:
matchers:
# Match the status codes
- type: status
# Some status codes we want to match
status:
- 200When you want to do complex matching of response codes,可以使用dsl
matchers:
- type: dsl
dsl:
- "len(body)<1024 && status_code==200"
- "contains(toupper(body), md5(cookie))"The meaning of the previous example is that the length of the matching response body is less than1024 并且状态码是200
Judge capitalizedbody中是否包括cookie的md5sum
使用condition: and\or Multiple conditions can be matched,Default multiple conditions areand的关系
官方实例如下:
matchers:
# Match the body word
- type: word
# Some words we want to match
words:
- "[core]"
- "[config]"
# Both words must be found in the response body
condition: and
# We want to match request body (default)
part: body详情请参考 https://nuclei.projectdiscovery.io/templating-guide/operators/matchers/
Extractors
Extractors Also check the results,与matchers相比,It can display the content that satisfies the rules,Also he has different typesExtractors,如下所示:
1. regex - Extract data from response based on a Regular Expression.
2. kval - Extract key: value/key=value formatted data from Response Header/Cookie
3. json - Extract data from JSON based response in JQ like syntax.
4. xpath - Extract xpath based data from HTML Response
例如:
extractors:
- type: xpath # type of the extractor
attribute: href # attribute value to extract (optional)
xpath:
- "/html/body/div/p[2]/a" # xpath value for extraction5. dsl - Extract data from the response based on a DSL expressions.
详情请参考https://nuclei.projectdiscovery.io/templating-guide/operators/extractors/
由于使用nuclei时间尚浅,关于Extractors和Matchers,Personally, I don't think there's a big difference in usage!
Both are verifications of the results,与matchers相比,ExtractorsIt can display the content that satisfies the rules!If you need to write complex response validation,Then it takes time to researchdsl了.
如何从nuclei中受益
当使用了nuclei一段时间后,Personally I think it is actually usednucleiThe most valuable is the variety insidetemplate,We can look at eachtemplatescript to learn attack methods,And also according to the insidereference to view the details of the vulnerability,This is particularly helpful for the relevant accumulation of safety knowledge!As for the sending of the attack request,This is actually a lot easier,我们是否使用nuclei其实都无所谓的,举个简单的例子,关于CVE-2020-9484的 yaml脚本定义如下:
id: CVE-2020-9484
info:
name: Apache Tomcat Remote Command Execution
author: dwisiswant0
severity: high
description: |
When using Apache Tomcat versions 10.0.0-M1 to 10.0.0-M4, 9.0.0.M1 to 9.0.34, 8.5.0 to 8.5.54 and 7.0.0 to 7.0.103 if
a) an attacker is able to control the contents and name of a file on the server; and
b) the server is configured to use the PersistenceManager with a FileStore; and
c) the PersistenceManager is configured with sessionAttributeValueClassNameFilter="null" (the default unless a SecurityManager is used) or a sufficiently lax filter to allow the attacker provided object to be deserialized; and
d) the attacker knows the relative file path from the storage location used by FileStore to the file the attacker has control over; then, using a specifically crafted request, the attacker will be able to trigger remote code execution via deserialization of the file under their control.
Note that all of conditions a) to d) must be true for the attack to succeed.
reference:
- http://packetstormsecurity.com/files/157924/Apache-Tomcat-CVE-2020-9484-Proof-Of-Concept.html
- https://nvd.nist.gov/vuln/detail/CVE-2020-9484
- https://lists.apache.org/thread.html/r77eae567ed829da9012cadb29af17f2df8fa23bf66faf88229857bb1%40%3Cannounce.tomcat.apache.org%3E
- https://lists.apache.org/thread.html/[email protected]%3Cusers.tomcat.apache.org%3E
classification:
cvss-metrics: CVSS:3.1/AV:L/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:H
cvss-score: 7
cve-id: CVE-2020-9484
cwe-id: CWE-502
tags: cve,cve2020,apache,tomcat,rce
requests:
- method: GET
headers:
Cookie: "JSESSIONID=../../../../../usr/local/tomcat/groovy"
path:
- "{
{BaseURL}}/index.jsp"
matchers-condition: and
matchers:
- type: status
status:
- 500
- type: word
part: body
words:
- "Exception"
- "ObjectInputStream"
- "PersistentManagerBase"
condition: and这个脚本中,The easiest is probablyrequests:Part of the attack script code,我们用jmeter Or the way you write your own code can be easily simulated!而description:部分以及reference:Parts are what we need to focus on!It is also our deep understandingpocBest example of an attack!
边栏推荐
- MySQL的JSON 数据类型2
- node中package解析、npm 命令行npm详解,node中的common模块化,npm、nrm两种方式查看源和切换镜像
- 赶紧进来!!!教你C语言实现扫雷小游戏(文章最后有源码!!!)
- I was rejected by the leader for a salary increase, and my anger rose by 9.5K after switching jobs. This is my mental journey
- 话题 | 雾计算和边缘计算有什么区别?
- The Controller layer code is written like this, concise and elegant!
- [Cultivation of internal skills of string functions] strcpy + strcat + strcmp (1)
- 407. 接雨水 II
- 956. 最高的广告牌
- C语言实现扫雷 附带源代码
猜你喜欢
![[Mock Interview - 10 Years of Work] Are more projects an advantage?](/img/fa/2652629d1ff4653aca0d626ac89bf8.jpg)
[Mock Interview - 10 Years of Work] Are more projects an advantage?
使用OpenCV实现一个文档自动扫描仪
【手撕AHB-APB Bridge】~ AMBA总线 之 AHB
【七夕快乐篇】Nacos是如何实现服务注册功能的?

Pytorch分布式训练/多卡/多GPU训练DDP的torch.distributed.launch和torchrun

堪称奔驰“理财产品”,空间媲美宝马X5,采用了非常运动的外观

【3D建模制作技巧分享】ZBrush如何设置笔刷快捷键

直接插入排序

【3D建模制作技巧分享】zbrush贴图映射小技巧

NebulaGraph v3.2.0 Release Note,对查询最短路径的性能等多处优化
随机推荐
Laravel 实现redis分布式锁
一点点读懂regulator(二)
自从新来了个字节20K出来的,就见识到了什么是天花板
功耗控制之DVFS介绍
[QNX Hypervisor 2.2用户手册]10.5 vdev ioapic
kernel问题定位手段总结
Service Mesh落地路径
Service Mesh landing path
仪表板展示 | DataEase看中国:数据呈现中国资本市场
使用代理对象执行实现类目标方法异常
吐槽 | 参加IT培训的正确姿势
407. 接雨水 II
Go 语言快速入门指南:什么是 TSL 安全传输层
@Import注解的作用以及如何使用
【游戏建模模型制作全流程】使用ZBrush制作骷髅王
【游戏建模模型制作全流程】在ZBrush中雕刻恶魔城男性角色模型
Shell编程之循环语句与函数的使用
Pytorch分布式训练/多卡/多GPU训练DDP的torch.distributed.launch和torchrun
赶紧进来!!!教你C语言实现扫雷小游戏(文章最后有源码!!!)
【3D建模制作技巧分享】如何使用ZBrush导出效果图