当前位置:网站首页>[judgment question] [short answer question] [Database Principle]
[judgment question] [short answer question] [Database Principle]
2022-07-03 12:46:00 【Laughing cold faced ghost】
List of articles
One . Judgment questions
1. The main target of data security is legal users .
right key : wrong
2. Database recovery is the use of redundant data to rebuild the database .
right key : Yes
3. The definition of foreign key level cascading is to ensure the consistency of data between related tables .
right key : Yes
4. Columns that create unique indexes can have some duplicate values .
right key : wrong
5. The output of a stored procedure can be passed to a variable .
right key : Yes
6. Writing programs does not belong to the task of the logical structure design stage of the database .
right key : Yes
7. A rule must be defined once it is used .
right key : wrong
8. By default , The index created is a nonclustered index .
right key : Yes
9. Triggers can be called and executed in a program .
right key : wrong
10.Sa Account can create and delete database roles .
right key : Yes
11. Because you can insert... Through the view 、 Modify or delete data , So the view is also a real table .
right key : wrong
12.DELETE Statement just deletes the data in the table , The table itself still exists in the database .
right key : Yes
13. When each stored procedure executes, it returns an integer return code to the caller . If the value of the return code is not explicitly set , The return code is 0, Indicates that the stored procedure was successfully executed .
right key : Yes
14. The more indexes you build in the database, the better .
right key : wrong
15. stay SQL SERVER in , The trigger is executed during data insertion . Update or delete previously executed .
right key : wrong
16. wildcard “_” Represents a single character .
right key : Yes
17. Data redundancy is not allowed in the database .
right key : wrong
18. A table can create multiple foreign keys .
right key : Yes
19. stay SQL Server In the system , Data information and log information cannot be placed in the same operating system file .
right key : Yes
20. When using subqueries , Subqueries must be enclosed in parentheses , So as to distinguish external query and sub query .
right key : Yes
21. A stored procedure is a set of precompiled Transcat-SQL sentence .
right key : Yes
22. The view itself does not save data , Instead, save a query statement .
right key : Yes
23.SQL Server Allows users to customize data types .
right key : Yes
24. The only key is the primary key .
right key : wrong
25. Columns that set unique constraints can be null .
right key : Yes
26. Information and data are relative , Sometimes they can be converted to each other .
right key : Yes
27. The primary key field can be null .
right key : wrong
28.SQL Server Automatically for primary key Create an index on the constrained column .
right key : Yes
29.SQL Server The database of can be converted into Access database .
right key : Yes
30. When deleting a table , Triggers in the table are deleted at the same time .
right key : Yes
31. stay SQL Server Users in cannot create global variables .
right key : Yes
32. Only data files can be backed up during database backup .
right key : wrong
33. Triggers are triggered by events and executed .
right key : Yes
34. Trigger conflicts with constraint , The trigger will not execute .
right key : Yes
Two . Short answer
1. What is business ? What are the characteristics of transactions ?
A transaction is a unit of work executed in a database system , It is a user-defined sequence of operations .
The nature of transactions : 1) Atomicity 2) Uniformity 3) Isolation, 4) persistence
2. What is data integrity ? What are the types of data integrity ?
The integrity of the database refers to protecting the correctness of the data in the database 、 Effectiveness and compatibility , Prevent incorrect data from entering the database and causing invalid operations .
Data integrity is divided into the following 4 class :
(1) Domain integrity
(2) Entity integrity
(3) Referential integrity
(4) User defined integrity
3. What is database backup ? What are the types of backups ?
Database backup refers to the process that the system administrator periodically or irregularly copies part or all of the contents of the database to another location or another disk to save .
Backup is divided into 4 Kind of :
(1) Full database backup
(2) Differential database backup
(3) Transaction log backup
(4) File and filegroup backup
4. What is stored procedure ? What are the benefits of using stored procedures ?
Stored procedures are a series of pre edited 、 It can realize specific data operation function SQL Code set , It is associated with a specific database , Stored in SQL Server Server .
Benefits of using stored procedures :
(1) Enhance the reusability and sharing of code
(2) Reduce network data traffic
(3) Speed up the system
(4) Ensure system security
5. What is a view ? What are the advantages of using views ?
View is a SELECT The statement specifies , A statement storage definition used to retrieve some row or column data in a database table . essentially , View is actually a SQL Inquire about .
Advantages of using views :
(1) Query simplification
(2) Protect the security of data in the database
(3) Mask the complexity of the database
边栏推荐
- Is it safe to open an account for online stock speculation? Who can answer
- 雲計算未來 — 雲原生
- Is it OK to open an account for online stock speculation? Is the fund safe?
- 【数据库原理复习题】
- Apache Mina Development Manual
- 4. 无线体内纳米网:电磁传播模型和传感器部署要点
- [embedded] - Introduction to four memory areas
- 十條職場規則
- Node.js: express + MySQL的使用
- Wechat applet pages always report errors when sending values to the background. It turned out to be this pit!
猜你喜欢

ncnn神經網絡計算框架在香柳丁派OrangePi 3 LTS開發板中的使用介紹

Node.js: express + MySQL的使用

initial、inherit、unset、revert和all的区别

Low code platform international multilingual (I18N) technical solution

T430 toss and install OS majave 10.14

Solve the problem of VI opening files with ^m at the end
Social community forum app ultra-high appearance UI interface

如何在微信小程序中获取用户位置?
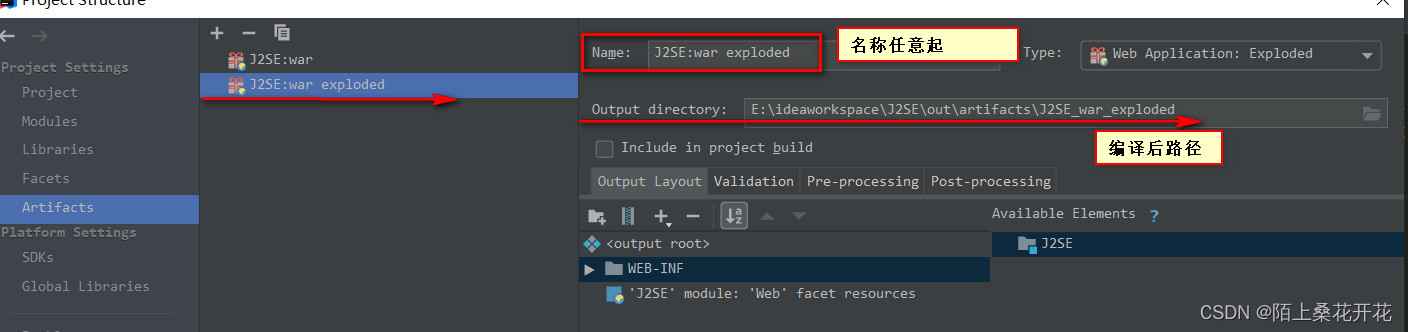
Idea packages the web project into a war package and deploys it to the server to run
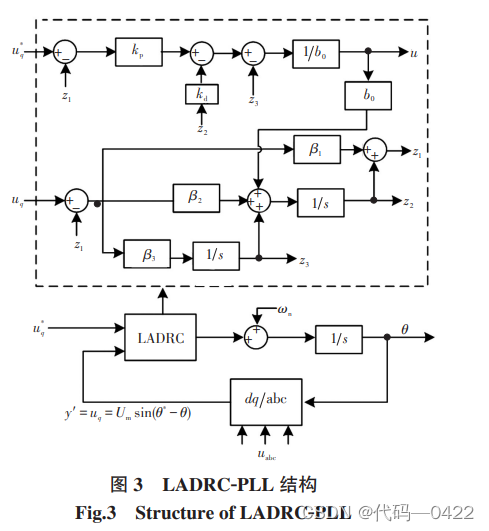
自抗扰控制器七-二阶 LADRC-PLL 结构设计
随机推荐
Record your vulnhub breakthrough record
Swift5.7 extend some to generic parameters
Xctf mobile--app2 problem solving
Swift5.7 扩展 some 到泛型参数
2020-11_ Technical experience set
Enable SASL authentication for memcached
initial、inherit、unset、revert和all的区别
01_ Using the concurrent tool class library, is thread safety safe
Swift bit operation exercise
Adult adult adult
Oh my Zsh + TMUX installation
Adult adult adult
JVM内存模型
Tianyi ty1208-z brush machine detailed tutorial (free to remove)
The difference between lambda and anonymous inner class
【习题六】【数据库原理】
Adult adult adult
Dix règles de travail
最新版抽奖盲盒运营版
Nodejs+Express+MySQL实现登陆功能(含验证码)