当前位置:网站首页>Is CICC securities reliable? Is it legal? Is it safe to open a stock account?
Is CICC securities reliable? Is it legal? Is it safe to open a stock account?
2022-06-24 16:43:00 【Koufu Q & A】
Take the answer 1:
1、 Get the online account opening link for account opening
2、 Have your ID card and bank card ready .
3、 Enter ID card name and mobile phone number , And obtain the verification code and fill in .
4、 Upload the front and back of ID card photos .
5、 The system will recognize our ID card information , We need to check and improve our identity information .
6、 Set the transaction password and bind the bank card .
7、 Next, go to risk assessment and questionnaire , Check the answers according to the questions in the risk assessment .
8、 Video authentication and review , After the audit, our account opening procedures will be completed .
9、 Backstage audit , If there is no problem, wait for SMS notification , After receiving the notice, you can trade .
If you have any questions, please contact , Our company gives a free low commission account 、 High value benefits such as monthly gold shares , Listed companies serve you wholeheartedly , Click on the top right corner , Welcome to contact !
边栏推荐
- Embedded Software Engineer written interview guide arm system and architecture
- MySQL進階系列:鎖-InnoDB中鎖的情况
- @There is a free copyright protection service for enterprises in Dawan District
- Popular explanation [redirection] and its practice
- The RTSP video structured intelligent analysis platform easynvr stops calling the PTZ interface through the onvif protocol to troubleshoot the pending status
- Percona Toolkit series - Pt deadlock logger
- Teach you to write a classic dodge game
- A memory leak caused by timeout scheduling of context and goroutine implementation
- Video structured intelligent analysis platform easycvr video recording plan function optimization / regularly delete expired videos
- How to collect and define project requirements in the early stage of EDI project implementation?
猜你喜欢
Advanced programmers must know and master. This article explains in detail the principle of MySQL master-slave synchronization

Daily algorithm & interview questions, 28 days of special training in large factories - the 15th day (string)

Ps\ai and other design software pondering notes

A survey of training on graphs: taxonomy, methods, and Applications
MySQL進階系列:鎖-InnoDB中鎖的情况

C. K-th not divisible by n (Mathematics + thinking) codeforces round 640 (Div. 4)

Cognition and difference of service number, subscription number, applet and enterprise number (enterprise wechat)
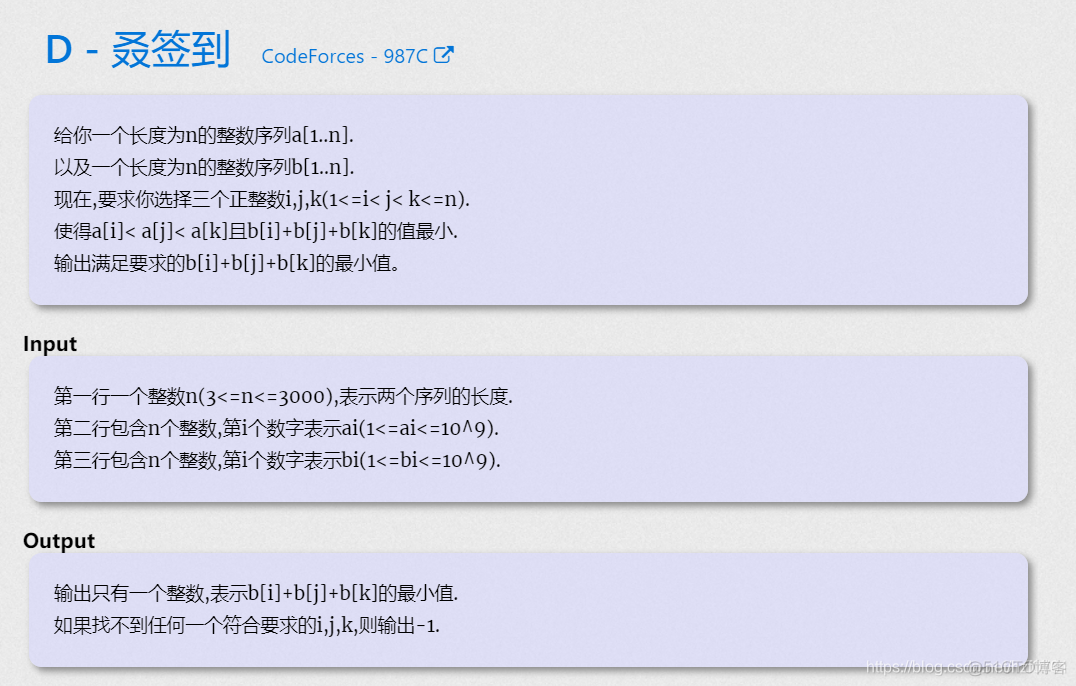
C. Three displays codeforces round 485 (Div. 2)
![[leetcode108] convert an ordered array into a binary search tree (medium order traversal)](/img/e1/0fac59a531040d74fd7531e2840eb5.jpg)
[leetcode108] convert an ordered array into a binary search tree (medium order traversal)
MySQL Advanced Series: locks - locks in InnoDB
随机推荐
A survey on dynamic neural networks for natural language processing, University of California
Enterprise service growth path (7): what key factors will affect SaaS' sales performance?
What is thermal data detection?
Recent progress of ffmpeg go
Comparison of jmeter/k6/locust pressure measuring tools (not completed yet)
Goby+awvs realize attack surface detection
Handling of communication failure between kuberbetes pod
Clickhouse high performance column storage core principle
[idea] dynamic planning (DP)
Find out the invisible assets -- use hosts collision to break through the boundary
Kubernetes 1.20.5 setting up Sentinel
MySQL date timestamp conversion
Scuffle on China's low code development platform -- make it clear that low code
Kubernetes characteristic research: sidecar containers
Kubernetes popular series: getting started with container Foundation
中金证券靠谱吗?是否合法?开股票账户安全吗?
50 growers | closed door meeting of marketing circle of friends ス gathering Magic City thinking collision to help enterprise marketing growth
proxy pattern
Script design for automatic login and command return
【prometheus】1. Monitoring overview

