当前位置:网站首页>MSF SMB based information collection
MSF SMB based information collection
2022-06-11 09:15:00 【Always a teenager】
Today, let's continue to introduce the relevant knowledge of penetration testing , The main content of this paper is MSF be based on SMB Information collection .
disclaimer :
The content introduced in this article is only for learning and communication , It is strictly prohibited to use the technology in the text for illegal acts , Otherwise, you will bear all serious consequences !
Again : It is forbidden to perform penetration tests on unauthorized equipment !
One 、SMB summary
SMB by Server Message Block Abbreviation , Server message block , Also known as network file operating system .SMB It is an application layer network transmission protocol , Developed by Microsoft , The main function is to enable machines on the network to share computer files 、 Printer serial port and other resources .
today , We are based on SMB The protocol collects information about the target host , Use Kali Linux Host to one Windows 7 The host collects information .
Two 、 be based on SMB Protocol scan version number
First , Let's try based on SMB The version number of the protocol scan target host .
Get into MSF Interactive page , Carry out orders :
use auxiliary/scanner/smb/smb_version
After using this module , We set the... Of this module RHOSTS Parameters , The module can be executed , The execution results of the above process are as follows :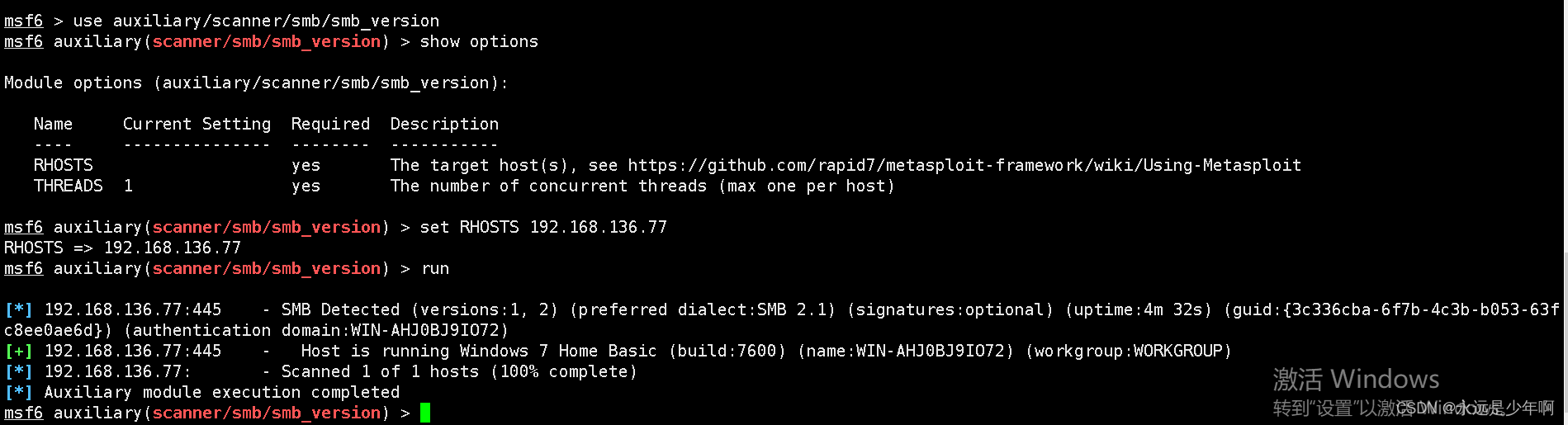
As can be seen from the above figure , This scanning method , Scan except SMB Version of protocol , And the version of the system .
3、 ... and 、 Scan shared files
Next , We try to scan the shared file information on the target host . We carry out orders :
use auxiliary/scanner/smb/smb_enumshares
After using this module , We need to set the target host RHOSTS、SMBUser( That is, the system user name )、SMBPass( System password ) Three parameters , As shown below :
after , We can then execute the module , The execution result of this module is as follows :
As can be seen from the above figure , Use this module , We scan multiple shared folders in addition to the target system .
Four 、 be based on SMB Enumerate user information
Last , We try to use SMB To scan the user profile of the target system . We carry out orders :
use auxiliary/scanner/smb/smb_lookupsid
After using this module , Still need to set up RHOSTS、SMBUser、SMBPass Three parameters , The setup process is exactly the same as before , As shown below :
After the above three parameters are set , We run the module , The results are shown below :
As can be seen from the above figure , Using this module , We scan multiple user information in addition to the system , Include user name 、ID wait .
Originality is not easy. , Reprint please explain the source :https://blog.csdn.net/weixin_40228200
边栏推荐
- 山东大学项目实训(四)—— 微信小程序扫描web端二维码实现web端登录
- Openstack explanation (24) -- registration of neutron service
- Type-C扩展坞自适应供电专利维权案例
- 2161. 根据给定数字划分数组
- ArcGIS 10.9.1 地质、气象体元数据处理及服务发布调用
- 1721. exchange nodes in the linked list
- MySQL startup error "bind on tcp/ip port: address already in use"
- Telecommuting best practices and Strategies
- 报错[DetectionNetwork(1)][warning]Network compiled for 6 shaves,maximum available 10,compiling for 5 s
- [image processing] spatial domain image enhancement
猜你喜欢

MSF基于SMB的信息收集

Machine learning notes - convolutional neural network memo list

实现边充边OTG的PD芯片GA670-10

ArcGIS 10.9.1 geological and meteorological volume metadata processing and service publishing and calling

Opencv oak-d-w wide angle camera test

Typescript -- preliminary study of variable declaration

openstack详解(二十一)——Neutron组件安装与配置

Redis source code analysis hash object (z\u hash)

Openstack explanation (21) -- installation and configuration of neutron components
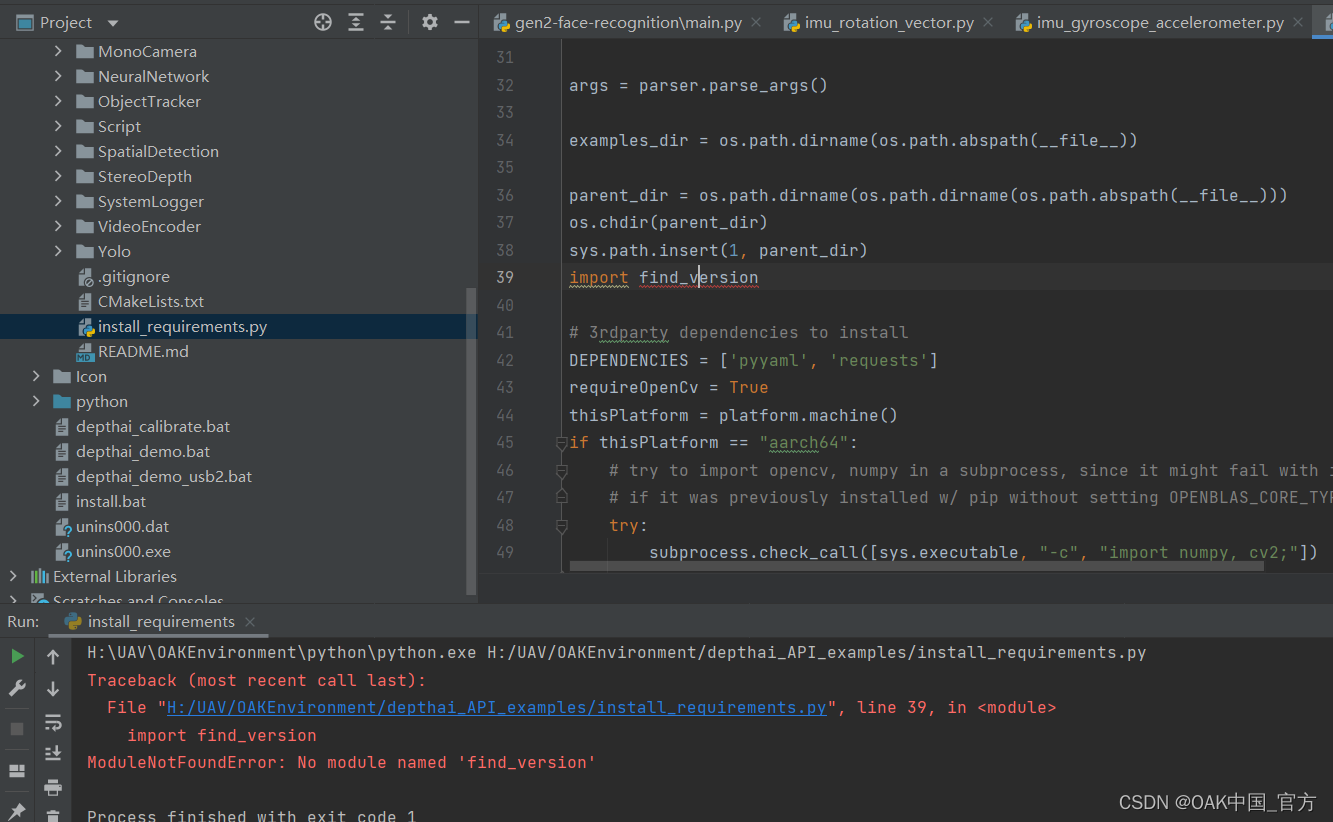
报错ModularNotFoundError: No module named ‘find_version’
随机推荐
Machine learning notes - convolutional neural network memo list
Opencv CEO teaches you to use oak (V): anti deception face recognition system based on oak-d and depthai
Strength and appearance Coexist -- an exclusive interview with Liu Yu, a member of Apache pulsar PMC
Device = depthai Device(““, False) TypeError: _init_(): incompatible constructor arguments.
服装ERP:企业如何进行施行规划?
面试题 02.02. 返回倒数第 k 个节点
实现边充边OTG的PD芯片GA670-10
ArcGIS 10.9.1 geological and meteorological volume metadata processing and service publishing and calling
PCBA方案定制,开发腕式血压计方案
Fabric. JS dynamically set font size
[237. delete nodes in the linked list]
报错RuntimeError: BlobReader error: The version of imported blob doesn‘t match graph_transformer
机器学习笔记 - Kaggle大师Janio Martinez Bachmann的故事
206. reverse linked list
What problems can ERP system help enterprises deal with?
[C language - data storage] how is data stored in memory?
1493. 删掉一个元素以后全为 1 的最长子数组
ArcGIS 10.9.1 地质、气象体元数据处理及服务发布调用
openstack详解(二十一)——Neutron组件安装与配置
ERP体系能帮忙企业处理哪些难题?