当前位置:网站首页>[hcie TAC] question 5 - 1
[hcie TAC] question 5 - 1
2022-07-04 15:50:00 【Heterogenesis】
Misplaced restore :
#AR28
acl 2000
rule 5 deny source 10.5.1.32 0
int g 0/0/2
traffic-filter outbound acl 2000
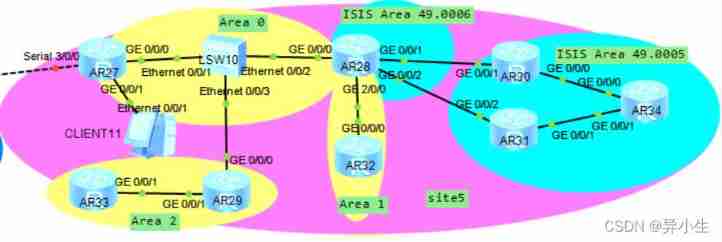
subject :AR32 Of loopback0 The interface address cannot be accessed ISIS Partial address of the area .
One 、 Fault root cause judgment
AR32loopbac 0 The interface address cannot be accessed AR31 All addresses and AR34 Of g 0/0/1 Address of the interface , The root cause is AR28 Of g 0./0/2 The outlet direction of the interface is filtered .
Two 、 Fault analysis
2.1、 The fault phenomenon reappears , stay AR32 On the implementation ping -a 10.5.1.32 x.x.x.x { among x.x.x.x by ISIS All addresses of the zone }, It is found that some addresses are inaccessible , The inaccessible addresses are as follows :
<AR32>ping -a 10.5.1.32 10.5.130.31
PING 10.5.130.31: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
--- 10.5.130.31 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
------------------------------------------------------------------------------
<AR32>ping -a 10.5.1.32 10.5.1.31
PING 10.5.1.31: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
--- 10.5.1.31 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
-----------------------------------------------------------------------------
<AR32>ping -a 10.5.1.32 10.5.14.31
PING 10.5.14.31: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
--- 10.5.14.31 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
------------------------------------------------------------------------------
<AR32>ping -a 10.5.1.32 10.5.14.34
PING 10.5.14.34: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
---- 10.5.14.34 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
……
Omit can ping My address
From the test results ,AR32 loopback0 The address that the interface cannot access is as follows :
a、AR31 Of loopback0 Interface ,ip The address is 10.5.1.34;
b、AR31 Of g0/0/1 Interface ,ip The address is 10.5.14.31;
c、AR31 Of g0/0/2 Interface ,ip The address is 10.5.130.31;
d、AR34 Of g0/0/1 Interface ,IP The address is 10.5.14.34;
Need to check AR32 Whether there is a corresponding route entry in the route table of .
2.2、 stay AR32 On the implementation display ip routing-table command , see AR32 The routing table for , The output is as follows :
<AR32>dis ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 21 Routes : 21
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.5.1.27/32 OSPF 10 2 D 10.5.239.28 GigabitEthernet0/0/0
10.5.1.28/32 OSPF 10 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.1.29/32 OSPF 10 2 D 10.5.239.28 GigabitEthernet0/0/0
10.5.1.30/32 O_ASE 150 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.1.31/32 O_ASE 150 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.1.32/32 Direct 0 0 D 127.0.0.1 LoopBack0
10.5.1.33/32 OSPF 10 3 D 10.5.239.28 GigabitEthernet0/0/0
10.5.1.34/32 O_ASE 150 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.14.0/24 O_ASE 150 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.34.0/24 O_ASE 150 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.40.0/24 OSPF 10 3 D 10.5.239.28 GigabitEthernet0/0/0
10.5.128.0/24 OSPF 10 2 D 10.5.239.28 GigabitEthernet0/0/0
10.5.129.0/24 O_ASE 150 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.130.0/24 O_ASE 150 1 D 10.5.239.28 GigabitEthernet0/0/0
10.5.239.0/24 Direct 0 0 D 10.5.239.32 GigabitEthernet0/0/0
10.5.239.32/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/0
10.5.239.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/0
From the output results ,AR32 In the routing table of ISIS All routes of the zone , explain AR28 Admiral ISIS The process is introduced into OSPF In progress . Then you need to check ISIS Whether there is in the routing table of the regional device OSPF Area routing , To judge AR28 Whether it will OSPF The process is introduced into ISIS In progress .
2.3、 stay AR31 and AR34 On the implementation display ip routing-table command , see AR31 and AR34 The routing table for , The output is as follows :
<AR31>dis ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 23 Routes : 23
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.5.1.27/32 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
10.5.1.28/32 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
10.5.1.29/32 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
10.5.1.30/32 ISIS-L1 15 20 D 10.5.14.34 GigabitEthernet0/0/1
10.5.1.31/32 Direct 0 0 D 127.0.0.1 LoopBack0
10.5.1.32/32 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
10.5.1.33/32 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
10.5.1.34/32 ISIS-L1 15 10 D 10.5.14.34 GigabitEthernet0/0/1
10.5.14.0/24 Direct 0 0 D 10.5.14.31 GigabitEthernet0/0/1
10.5.14.31/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/1
10.5.14.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/1
10.5.34.0/24 ISIS-L1 15 20 D 10.5.14.34 GigabitEthernet0/0/1
10.5.40.0/24 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
10.5.128.0/24 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
10.5.129.0/24 ISIS-L1 15 30 D 10.5.14.34 GigabitEthernet0/0/1
10.5.130.0/24 Direct 0 0 D 10.5.130.31 GigabitEthernet0/0/2
10.5.130.31/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/2
10.5.130.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/2
10.5.239.0/24 ISIS-L2 15 74 D 10.5.130.28 GigabitEthernet0/0/2
=============================================================
<AR34>dis ip routing-table
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: Public
Destinations : 16 Routes : 17
Destination/Mask Proto Pre Cost Flags NextHop Interface
0.0.0.0/0 ISIS-L1 15 10 D 10.5.14.31 GigabitEthernet0/0/1
ISIS-L1 15 10 D 10.5.34.30 GigabitEthernet0/0/0
10.5.1.30/32 ISIS-L1 15 10 D 10.5.34.30 GigabitEthernet0/0/0
10.5.1.31/32 ISIS-L1 15 10 D 10.5.14.31 GigabitEthernet0/0/1
10.5.1.34/32 Direct 0 0 D 127.0.0.1 LoopBack0
10.5.14.0/24 Direct 0 0 D 10.5.14.34 GigabitEthernet0/0/1
10.5.14.34/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/1
10.5.14.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/1
10.5.34.0/24 Direct 0 0 D 10.5.34.34 GigabitEthernet0/0/0
10.5.34.34/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/0
10.5.34.255/32 Direct 0 0 D 127.0.0.1 GigabitEthernet0/0/0
10.5.129.0/24 ISIS-L1 15 20 D 10.5.34.30 GigabitEthernet0/0/0
10.5.130.0/24 ISIS-L1 15 20 D 10.5.14.31 GigabitEthernet0/0/1
From the output results ,AR31 In the routing table of OSPF All routes of the zone ,AR34 There are two default routes on. The next hop points to AR30 and AR31, explain AR28 Admiral OSPF The process is introduced into ISIS In progress , Both processes have all the routing information of the other region , It indicates that the whole network route can reach , There is no route filtering policy . The preliminary judgment may be AR28、AR31、AR32、AR34 There is a target on AR32loopback 0 Traffic filtering strategy of interface address . because AR28、AR31 There are login permission restrictions , So check out AR32、AR31、AR34 Whether there is a traffic filtering strategy that can lead to failure .
2.4、 stay AR31、AR32、AR34 On the implementation of separate display acl all、display traffic-filter applied-record、display traffic-policy applied-record command , Check to see if there is a target AR32loopback0 The flow filtering strategy of the interface .
……
Omit the output
From the output results ,AR31、AR32、AR34 No traffic filtering strategy that can lead to failure has been found , Judge AR28 There may be problems for AR32loopback0 The flow filtering strategy of the interface , But cause AR28 Login permission exists and cannot be checked directly , Only indirect tests can be carried out to verify the root cause of the fault .
2.5、 stay AR32 On the implementation tracert -a 10.5.1.32 10.5.1.34 command , Indirect test AR28 Whether there is a traffic filtering policy on , The output is as follows :
<AR32>tracert -a 10.5.1.32 10.5.1.34
traceroute to 10.5.1.34(10.5.1.34), max hops: 30 ,packet length: 40,press CTRL_C to break
1 10.5.239.28 40 ms 20 ms 20 ms
2 * 10.5.129.30 80 ms *
3 10.5.34.34 60 ms * 40 ms
From the output results , stay AR32 In order to loopback 0 Go to the source address tracert AR34 Of loopback 0 Interface address , Data can only be passed through AR28 Of g 0/0/1 Interface forwarding out , And arrive smoothly AR34, But after AR28 Of g0/0/2 Packet loss occurs during interface , Further inspection is required .
2.6、 stay AR32 On the implementation tracert 10.5.1.34 command , Do not carry the source address directly tracert test , The output is as follows :
<AR32>tracert 10.5.1.34
traceroute to 10.5.1.34(10.5.1.34), max hops: 30 ,packet length: 40,press CTRL_C to break
1 10.5.239.28 20 ms 20 ms 10 ms
2 10.5.130.31 40 ms 10.5.129.30 20 ms 10.5.130.31 20 ms
3 10.5.34.34 30 ms 10.5.14.34 40 ms 10.5.34.34 30 ms
From the output results , Do not carry the source address , direct tracert AR34 Of loopback0 when , Packets can pass normally AR28 Of g0/0/1 Interface and g0/0/2 The interface arrives AR34, Description in AR28 There is a traffic filtering strategy , combination 2.5 and 2.6 It can be judged that AR28 Of g0/0/2 The interface is targeted at AR32 loopback0 The flow filtering strategy of the interface , But it is impossible to judge the direction of policy application , You need to check the traffic transmission path in the opposite direction to determine the direction of policy application .
2.7、 Determine the application direction of traffic filtering strategy
a、 stay AR34 On the implementation tracert -a 10.5.1.34 10.5.1.32, Determine the direction of policy application , The output is as follows :
<AR34>tracert -a 10.5.14.34 10.5.1.32
traceroute to 10.5.1.32(10.5.1.32), max hops: 30 ,packet length: 40,press CTRL_C to break
1 10.5.14.31 30 ms 20 ms 20 ms
2 10.5.130.28 30 ms 30 ms 10.5.129.28 30 ms
3 10.5.239.32 40 ms 20 ms 30 ms
From the output results ,AR34 In order to loopback0 The interface address is the source address , Packets can arrive smoothly AR32.
b、 stay AR31 With g0/0/1 Interface (10.5.14.31 、g0/0/2 Interface (10.5.130.31)、 loopback0 Interface (10.5.1.31) The address is the source address tracert AR31 Of loopback0 Address of the interface , The output is as follows :
<AR31>tracert -a 10.5.14.31 10.5.1.32
traceroute to 10.5.1.32(10.5.1.32), max hops: 30 ,packet length: 40,press CTRL_C to break
1 10.5.130.28 60 ms 10 ms 10 ms
2 10.5.239.32 30 ms 20 ms 20 ms
=====================================================
<AR31>tracert -a 10.5.130.31 10.5.1.32
traceroute to 10.5.1.32(10.5.1.32), max hops: 30 ,packet length: 40,press CTRL_C to break
1 10.5.130.28 20 ms 10 ms 10 ms
2 10.5.239.32 20 ms 20 ms 10 ms
======================================================
<AR31>tracert -a 10.5.1.31 10.5.1.32
traceroute to 10.5.1.32(10.5.1.32), max hops: 30 ,packet length: 40,press CTRL_C to break
1 10.5.130.28 30 ms 10 ms 20 ms
2 10.5.239.32 20 ms 20 ms 20 ms
From the output results , stay AR31 With g0/0/1 Interface 、 g 0/0/2 Interface 、 loopback0 The interface address is the source address tracert AR32 Of loopback0 Address of the interface , All packets can arrive smoothly AR32.
combination a、b hear , stay AR34 To AR32 There is no data flow direction for AR32loopback0 Traffic filtering strategy .
in summary :AR32 loopback0 cannot access AR31 All addresses of and AR34 Of g 0/0/1 The root cause of the interface address is in AR28 Of g0/0/2 There is a problem in the outgoing direction of the interface AR32loopback0 Traffic filtering strategy .
3、 ... and 、 Fault handling
3.1、 The fault is AR28 Of g0/0/2 There is a problem in the outgoing direction of the interface AR32 loopback0 When the traffic filtering strategy of , Need to be in AR28 Execute the following command on :
display traffic-filter applied-record # Check whether there is traffic filtering
display traffic-policy applied-record # Check whether there is a traffic policy
system-view # Enter the system view
int g0/0/2 # Enter the interface view
undo traffic-filter outbound # Delete traffic filtering
undo traffic-policy outbound # Delete traffic policy
After the execution of the above order AR32 Execute the following command on to test whether the fault has been solved :
ping -a 10.5.1.32 10.5.1.31 # Test and AR31 Loopback connectivity
ping -a 10.5.1.32 10.5.14.31 # Test and AR31g0/0/1 Connectivity of interfaces
ping -a 10.5.1.32 10.5.130.31 # Test and AR31g0/0/2 Interface connectivity
ping -a 10.5.1.32 10.5.1.31 # Test and AR34loopback0 Connectivity of interfaces
3.2、 Other high possibilities —— stay AR28 There are advanced ACL Filter , Need to be AR28 Execute the following command on :
display acl all # View all ACL
system-view # Enter the system view
undo acl { senior ACL The serial number of } # Delete the ACL
After the execution of the above order AR32 Execute the following command on to test whether the fault has been solved :
ping -a 10.5.1.32 10.5.1.31 # Test and AR31 Loopback connectivity
ping -a 10.5.1.32 10.5.14.31 # Test and AR31g0/0/1 Connectivity of interfaces
ping -a 10.5.1.32 10.5.130.31 # Test and AR31g0/0/2 Interface connectivity
ping -a 10.5.1.32 10.5.1.31 # Test and AR34loopback0 Connectivity of interfaces
3.3、
quit # Exit to system view
save # Save configuration
If after executing the above command , The fault still exists , Please send a front-line engineer to the site to remove obstacles , Or provide complete equipment configuration , And call Huawei 400 Hotline , Ask Huawei experts for remote assistance .
边栏推荐
- 干货 | fMRI标准报告指南新鲜出炉啦,快来涨知识吧
- Rearrange array
- Implementation of web chat room
- Functional interface, method reference, list collection sorting gadget implemented by lambda
- In today's highly integrated chips, most of them are CMOS devices
- 大神详解开源 BUFF 增益攻略丨直播
- Unity预制件Prefab Day04
- %s格式符
- [flask] ORM one to many relationship
- Unity script API - component component
猜你喜欢
Unity脚本生命周期 Day02

夜天之书 #53 Apache 开源社群的“石头汤”
Huawei cloud database DDS products are deeply enabled
Unity脚本常用API Day03

What is the future of the booming intelligent Internet of things (aiot) in recent years?

I plan to teach myself some programming and want to work as a part-time programmer. I want to ask which programmer has a simple part-time platform list and doesn't investigate the degree of the receiv

【大连理工大学】考研初试复试资料分享

Dry goods | fMRI standard reporting guidelines are fresh, come and increase your knowledge
MySQL组合索引(多列索引)使用与优化案例详解

Nine CIO trends and priorities in 2022
随机推荐
Huawei cloud database DDS products are deeply enabled
Unity update process_ Principle of unity synergy
Redis sentinel mode realizes one master, two slave and three Sentinels
Analysis of nearly 100 million dollars stolen and horizon cross chain bridge attacked
I plan to teach myself some programming and want to work as a part-time programmer. I want to ask which programmer has a simple part-time platform list and doesn't investigate the degree of the receiv
在芯片高度集成的今天,绝大多数都是CMOS器件
AI has surpassed Dr. CS in question making?
How was MP3 born?
Salient map drawing based on OpenCV
LeetCode 1184. Distance between bus stops -- vector clockwise and counterclockwise
Shell programming basics
Unity预制件Prefab Day04
怎么判断外盘期货平台正规,资金安全?
LeetCode 35. Search the insertion position - vector traversal (O (logn) and O (n) - binary search)
文本挖掘工具的介绍[通俗易懂]
Interpretation of the champion scheme of CVPR 2020 night target detection challenge
LeetCode 1184. 公交站间的距离 ---vector顺逆时针
Weekly recruitment | senior DBA annual salary 49+, the more opportunities, the closer success!
夜天之书 #53 Apache 开源社群的“石头汤”
Solve the error of JSON module in PHP compilation and installation under CentOS 6.3