当前位置:网站首页>Analysis of nearly 100 million dollars stolen and horizon cross chain bridge attacked
Analysis of nearly 100 million dollars stolen and horizon cross chain bridge attacked
2022-07-04 14:55:00 【Tokenview blockchain】
“
Tokenviewlabs
Horizon The cross chain bridge was stolen 1 Billion dollars
6 month 24 Japan ,Harmony The team tweeted ,Horizon Cross chain bridge attacked , The amount of loss is about 1 Billion dollars .6 month 26 Japan ,Harmony founder stephen tse Send a message to say , this Horizon Be attacked , Because the private key was leaked . The funds were stolen from the Ethereum side of the cross chain bridge . The attacker successfully accessed and decrypted some of these keys , Some of them are used to sign unauthorized transactions . at present Harmony Working with top blockchain tracking team and FBI cooperation , Investigate the theft .
Horizon By Layer1 Public chain Harmony Developed with Ethereum Cross chain bridge between assets . According to official information , Cross chain bridge is a technology that connects two blockchains by verifying cross chain transactions through two processes , It includes two processes: asset transfer and asset redemption :
Ethereum-to-Harmony The process of transferring assets : Assets locked in Ethereum At the same time, the assets of the same amount are Harmony It's cast on the wall .
Harmony-to-Ethereum Redemption process : stay Harmony The assets cast on are destroyed and the equivalent assets are unlocked on Ethereum .
in short ,Horizon Cross chain bridge allows assets to be in Ethereum-Harmony Free flow between two blockchains .
Horizon Theft process
This time Horizon The cross chain bridge attack lost a total of, including Ethereum 11 Kind of ERC20 Tokens and 13,100 ETH;BSC On 5,000 individual BNB and 640,000 individual BUSD, About 1 Billion dollars .
Hacker address :
https://eth.tokenview.com/cn/address/0x0d043128146654c7683fbf30ac98d7b2285ded00
Transit address
https://eth.tokenview.com/cn/address/0x9e91ae672e7f7330fc6b9bab9c259bd94cd08715
https://eth.tokenview.com/cn/address/0x58f4baccb411acef70a5f6dd174af7854fc48fa9
Private key disclosure address :
https://eth.tokenview.com/cn/address/0xf845a7ee8477ad1fb4446651e548901a2635a915
https://eth.tokenview.com/cn/address/0x812d8622c6f3c45959439e7ede3c580da06f8f25
Attacked contract MultiSigWallet:
https://eth.tokenview.com/cn/address/0x715cdda5e9ad30a0ced14940f9997ee611496de6
Tokenview Let me show you the whole attack process , Lost by the first trading vulnerability 13,100 ETH For example :
1 The attacker uses the address that divulges the private key 0x812...8f25 Called the contract 0x715...6de6 To verify .
2 The cross link bridge is protected by a group of verifier nodes , These nodes submit cross chain transaction confirmation through multi signature contracts , However, the contract only needs two verifiers to verify, which allows cross chain . The attacker is taking advantage of this , Finally successfully execute a transaction : take 13,100 ETH Transmit to the attacker's address 0x0d0...ed00. Since then, attackers have repeatedly used this attack to make profits .

Tokenview data
Asset tracking on the chain
On the Ethereum chain , The attacker transferred most of the tokens to two transit wallet addresses (0x9e9...8715 as well as 0x58f...8fa9), And exchange the token for ETH, And then ETH Return to the initial attack address (0x0d0...D00). The accumulated profit of this address is about 85,837 ETH.
According to the Tokenview Data analysis ,6 month 27 Japan Horizon The attacker has stolen 18,036 gold ETH There are three batches in total 18,033 gold ETH Transfer to Tornado Cash Mix money . The specific path is as follows :
6 month 27 Japan 15:10:11,Horizon The attacker's address is transferred out 18,036 gold ETH( about 2200 Thousands of dollars ) To your new address 0x1ec...6430.

Tokenview data
stay 15:11:06, The address will 6,012 gold ETH( about 738 Thousands of dollars ) into 0x43...47Ae, And with each 100 ETH Transfer to Tornado Cash.
stay 19:17:40, The address will be the second batch 6,012 gold ETH into 0x45...5970, Still with each stroke 100 ETH Transfer to Tornado Cash.
stay 23:48:52, The address will again 6,009 gold ETH into 0x8a...c3f4, Still with each stroke 100 ETH Transfer to Tornado Cash.
6 month 28 Japan 11:58:50, Cross chain bridge Horizon The attacker's address is transferred out again 18,036 gold ETH To your new address (0x809d...c5e4), Then the new address went to the address (0x89f...bd8b) into 6,012 gold ETH. So far Horizon The attacker's address balance is 49,79.67ETH.
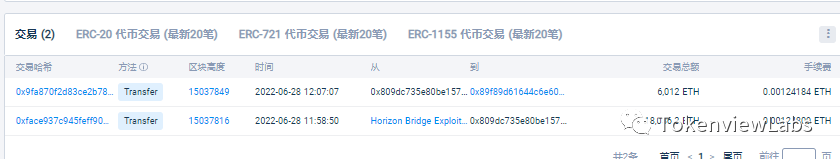
Tokenview data
ending
Horizon The attack on the cross chain bridge also triggered Harmony There is a heated discussion about how to ensure the safety of verifier nodes . In this attack , The attacker exploited the vulnerability of a small number of verifier nodes needed to pass the verification , Thus losing about 1 $billion in assets . Since the incident ,Harmony The Horizon The Ethereum side of the bridge moved to 4/5 Multisignature ( need 5 Among them 4 individual ). Currently, the attacker has started to pass Tornado Cash Transfer funds ,Harmony The team is also working with the blockchain tracking and analysis team and FBI, Track the whereabouts of funds .
Tokenview Will continue to pay attention Horizon The latest developments of the cross chain bridge attack .
边栏推荐
- C language achievement management system for middle school students
- TechSmith Camtasia studio 2022.0.2 screen recording software
- [C language] Pointer written test questions
- Industrial Internet has greater development potential and more industry scenarios
- Ali was laid off employees, looking for a job n day, headhunters came bad news
- Leetcode 1200 minimum absolute difference [sort] the way of leetcode in heroding
- 03-存储系统
- openresty 重定向
- 金额计算用 BigDecimal 就万无一失了?看看这五个坑吧~~
- Node mongodb installation
猜你喜欢
![[C language] Pointer written test questions](/img/89/3d463cbbb321e45ba8342f0ddfef8f.png)
[C language] Pointer written test questions
Redis publish and subscribe
![LeetCode 1200 最小绝对差[排序] HERODING的LeetCode之路](/img/4a/6763e3fbdeaf9de673fbe8eaf96858.png)
LeetCode 1200 最小绝对差[排序] HERODING的LeetCode之路
如何配和弦
Detailed analysis of pytorch's automatic derivation mechanism, pytorch's core magic
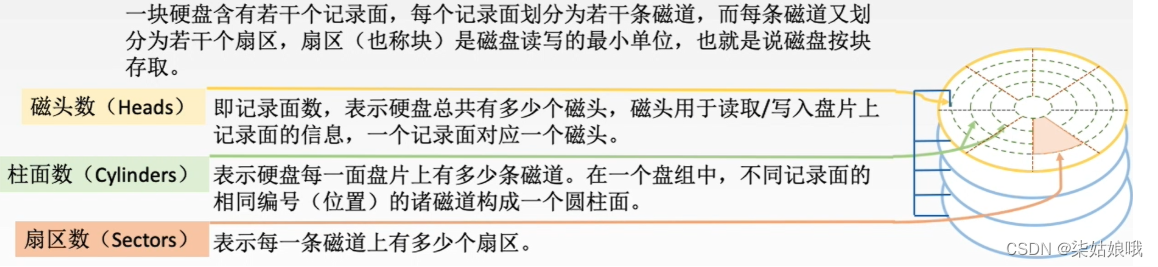
03-存储系统
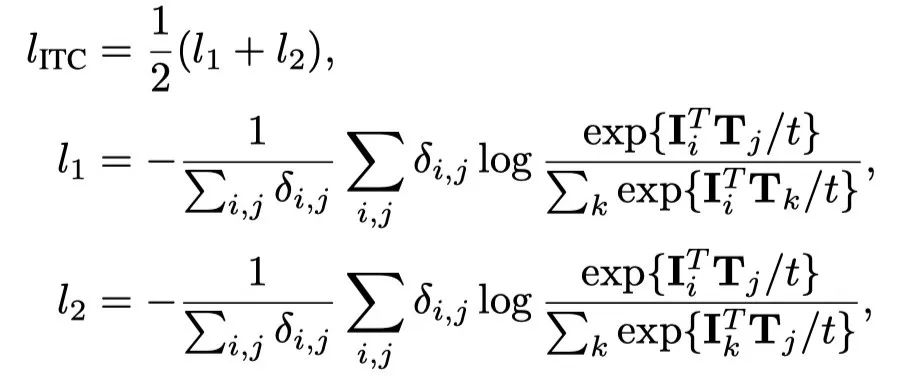
UFO:微软学者提出视觉语言表征学习的统一Transformer,在多个多模态任务上达到SOTA性能!...
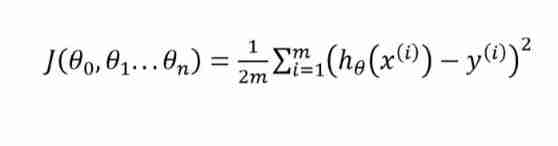
Five minutes per day machine learning: use gradient descent to complete the fitting of multi feature linear regression model
Guitar Pro 8win10最新版吉他学习 / 打谱 / 创作
Summary of common problems in development
随机推荐
[MySQL from introduction to proficiency] [advanced chapter] (IV) MySQL permission management and control
Detailed analysis of pytorch's automatic derivation mechanism, pytorch's core magic
openresty 重定向
LVGL 8.2 keyboard
如何配和弦
深度学习 网络正则化
TechSmith Camtasia studio 2022.0.2 screen recording software
Halo effect - who says that those with light on their heads are heroes
Red envelope activity design in e-commerce system
Comment configurer un accord
Leetcode 1200 minimum absolute difference [sort] the way of leetcode in heroding
Respect others' behavior
Ali was laid off employees, looking for a job n day, headhunters came bad news
Techsmith Camtasia Studio 2022.0.2屏幕录制软件
LVGL 8.2 Menu
03-存储系统
openresty 限流
Gin integrated Alipay payment
都在说DevOps,你真正了解它吗?
LVGL 8.2 Draw label with gradient color