******## 1. Experimental content ******
(1)Web front end HTML
It can be installed normally 、 Start stop Apache. understand HTML, Understand the form , understand GET And POST Method , Write a HTML.
(2)Web front end javascipt
understand JavaScript Basic functions of , understand DOM.
stay (1) On the basis of , To write JavaScript Verify user name 、 The rules of the code . After the user clicks the login button, it will echo “ welcome + The user name you entered ”
Attempt injection attack : Use echo user name injection HTML And JavaScript.
(3)Web Back end :MySQL Basics : normal setup 、 start-up MySQL, Building database 、 Create user 、 Change Password 、 Build table
******(4)Web Back end : To write PHP Webpage , Connect to database , User authentication ******
******(5) The simplest SQL Inject ,XSS Attack test ******
(6) install Webgoat Or similar platform , And finish SQL Inject 、XSS、CSRF attack .
## 2. Experimental process
(1)Web front end HTML
Use instruction service apache2 start start-up apache service 
Type in the browser kali Of ip According to the normal 
stay /var/www/html Under the table of contents , Create a new one with a form html file 20192407login.html
Open in browser and display normally 
(2)Web front end javascipt
Create a with a form HTML
After the user clicks the login button, it will echo “ welcome + The user name you entered 
(3)Web Back end :MySQL Basics : normal setup 、 start-up MySQL, Building database 、 Create user 、 Change Password 、 Build table
Turn on mysql And login 
Building database 
view the database 
Create a table logininfo, Insert “xjy” and “20192407” And view the contents of the database 

Change Password 

Create user 
New users can log in normally 
(4)Web Back end : To write PHP Webpage , Connect to database , User authentication
Write front-end and back-end code :

Enter the web page and run successfully 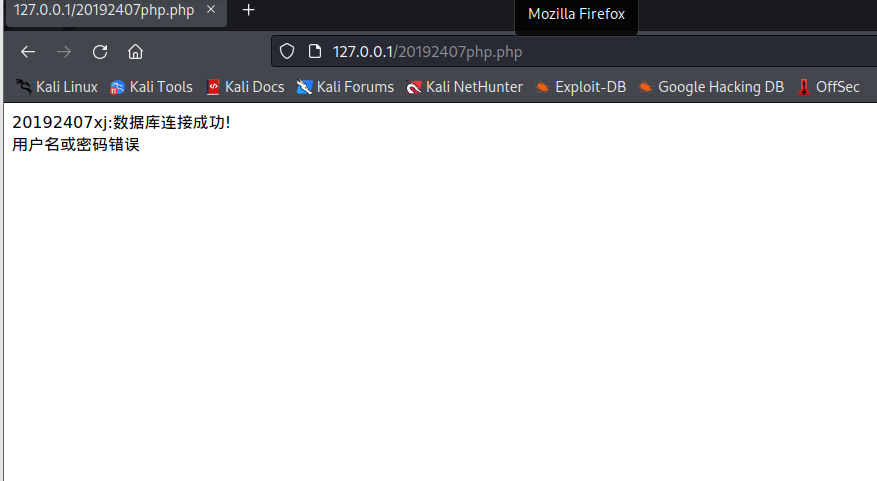

attach : database 
******(5) The simplest SQL Inject ,XSS Attack test ******
sql Inject :
XSS Attack test : Input 
(6) install Webgoat Or similar platform , And finish SQL Inject 、XSS、CSRF attack .
download Webgoat And use java -jar webgoat-server-8.2.2.jar Instruction loading 

Sign in webgoat
sql Inject : Get the contents of the table 
xss attack 
CSRF attack
adopt csrf To submit requests across sites , Then fill in the response flag.

take GET The head of the request referer Fields to be removed , stay burpsite Submit it inside , And then you get flag,
******## 3. Problems and solutions ******
- problem 1: The database could not be started properly :
** problem 1 Solution : Query the execution code on the Internet :flush privileges that will do .**
4. Learn to understand 、 Thinking etc.
The difficulty of this experiment is moderate, but the content is cumbersome ,kali And the database are also in use. Fortunately, they can be solved . This experiment makes me understand the HTML, Back end PHP, Database and SQL Injection attack 、XSS attack 、CSRF Attack has a deeper understanding . I also have a further understanding of online attack methods .




![[enter textbook latex record]](/img/f0/5ca60f0894d4ae544e7399d18a3a42.png)




