当前位置:网站首页>SSO single sign on
SSO single sign on
2022-07-06 20:25:00 【Brother Youji】
1、SSO explain
SSO English full name Single Sign On, Single sign on .SSO In multiple application systems , Users only need to log in once to access all mutual trust application systems .SSO(Single Sign On)_ Baidu Encyclopedia
For example, visit the Netease account center ( Netease email account security center ) After login Visit the following sites are login status
- Netease live https://v.163.com
- Netease blog https://blog.163.com
- Netease Huatian https://love.163.com
- Netease koala https://www.kaola.com
- NetEase Lofter http://www.lofter.com
2、 Benefits of single sign on system
- User perspective : Users can log in once and use many times , No need to record multiple sets of user names and passwords , worry .
- System administrator Perspective : The administrator only needs to maintain a unified account center , convenient .
- New system development perspective : When developing a new system, you only need to directly connect to a unified account center , Simplify development process , To save time .
3、 Design objectives
This article is also mainly to explore how to design & Achieve one SSO System
Here are the core functions that need to be implemented :
- Single sign on
- Single sign out
- Support cross domain single sign on
- Support cross domain single sign out
Two 、SSO Design and implementation
1、 Core applications and dependencies
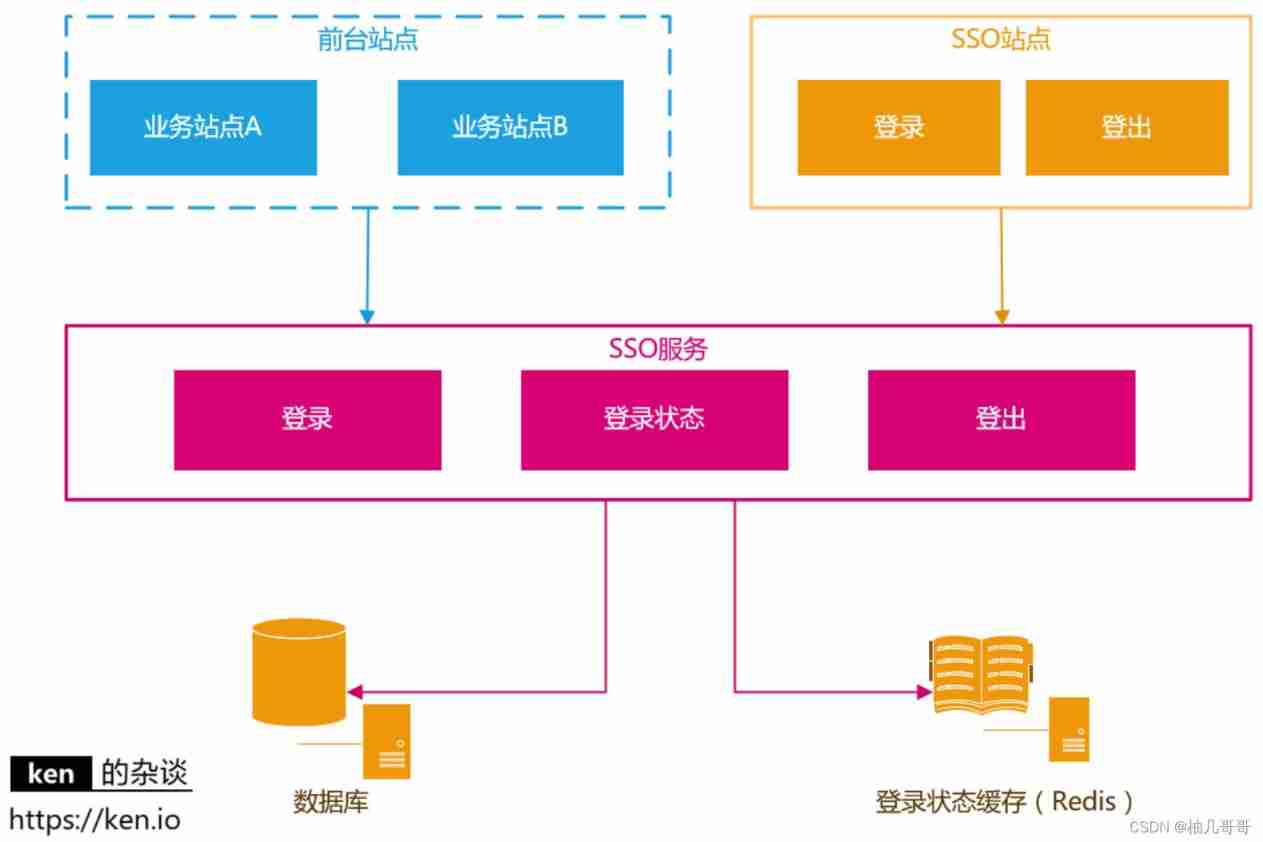
| application / modular / object | explain |
|---|---|
| Front desk site | The site you need to log in to |
| SSO Site - Sign in | Provide login page |
| SSO Site - Log out | Provides access to log off |
| SSO service - Sign in | Provide login service |
| SSO service - The login status | Provide login status verification / Login information query service |
| SSO service - Log out | Provides the user to log off the login service |
| database | Store user account information |
| cache | Store user login information , Usually use Redis |
2、 Storage and verification of user login status
common Web Framework for Session The implementation of is to generate a SessionId Store in browser Cookie in . And then Session Content is stored in server-side memory , This ken.io Before Session working principle It's also mentioned in . The whole idea is also used for reference . After the user logs in successfully , Generate AuthToken Give it to the client to save . If it's a browser , It's stored in Cookie in . If it's a cell phone App It's stored in App In the local cache . This paper is mainly based on Web Site SSO. When the user is browsing the page that needs to log in , The client will AuthToken Submit to SSO Service validation login status / Get user login information
For the storage of login information , The proposal USES Redis, Use Redis Cluster to store login information , It can guarantee high availability , It can be extended linearly . At the same time, we can also make SSO Services meet load balancing / Scalable requirements .
| object | explain |
|---|---|
| AuthToken | Use it directly UUID/GUID that will do , If there is validation AuthToken The need for legitimacy , Can be UserName+ Timestamp encryption generation , Verify the validity after decryption by the server |
| login information | Usually it's going to be UserId,UserName cached |
3、 The user login / Login verification
- Login sequence diagram

According to the picture above , After the user logs in AuthToken Save in Cookie in . domain=test.com The browser will domain Set to .test.com, This way to access all of *.test.com Of web Site , Will be AuthToken Take it to the server side . And then through SSO service , Complete the verification of user status / Access to user login information
- Access to login information / Login status verification

4、 The user to log out
What users have to do when they log out is simple :
- Server clear cache (Redis) Login status in
- The client clears the stored AuthToken
- Log out of the sequence diagram

5、 Cross domain login 、 Log out
As mentioned earlier , The core idea is client storage AuthToken, Server side through Redis Store login information . Since the client is going to AuthToken Stored in Cookie Medium . So the problem to be solved across domains , It's how to solve Cookie Cross domain read-write problem of .
Cookie It's not cross domain , Like me
The core idea of cross domain solution is :
- After the login is completed, through callback , take AuthToken Pass to a site other than the primary domain name , The site itself will AuthToken Stored in the current domain Cookie in .
- After the logout is completed, it can be called back , Call the logout page of a non primary domain name site , Complete set Cookie Medium AuthToken Expired operations .
- Cross domain login ( The primary domain name is already logged in )

Cross domain login ( The primary domain name is not logged in )
Cross domain logout 
3、 ... and 、 remarks
- About the plan
This design is more to provide implementation ideas . If it involves APP User login, etc , During a visit to SSO The service , Add to APP The signature verification of . Of course , If there is a wireless gateway , Verifying the signature is not a problem .
- About sequence diagrams
The sequence diagram doesn't contain all the scenarios ,ken.io Just the core / Main scene , In addition, for some information that does not affect the understanding of ideas, you can save .
边栏推荐
- 【云原生与5G】微服务加持5G核心网
- 22-07-05 七牛云存储图片、用户头像上传
- Why do novices often fail to answer questions in the programming community, and even get ridiculed?
- [network planning] Chapter 3 data link layer (3) channel division medium access control
- Tencent architects first, 2022 Android interview written examination summary
- 使用ssh连接被拒
- 爬虫(14) - Scrapy-Redis分布式爬虫(1) | 详解
- 【Yann LeCun点赞B站UP主使用Minecraft制作的红石神经网络】
- Redisson bug analysis
- 【DSP】【第二篇】了解C6678和创建工程
猜你喜欢
Pytest (3) - Test naming rules
Rhcsa Road
Tencent byte and other big companies interview real questions summary, Netease architects in-depth explanation of Android Development

2022 refrigeration and air conditioning equipment installation and repair examination contents and new version of refrigeration and air conditioning equipment installation and repair examination quest
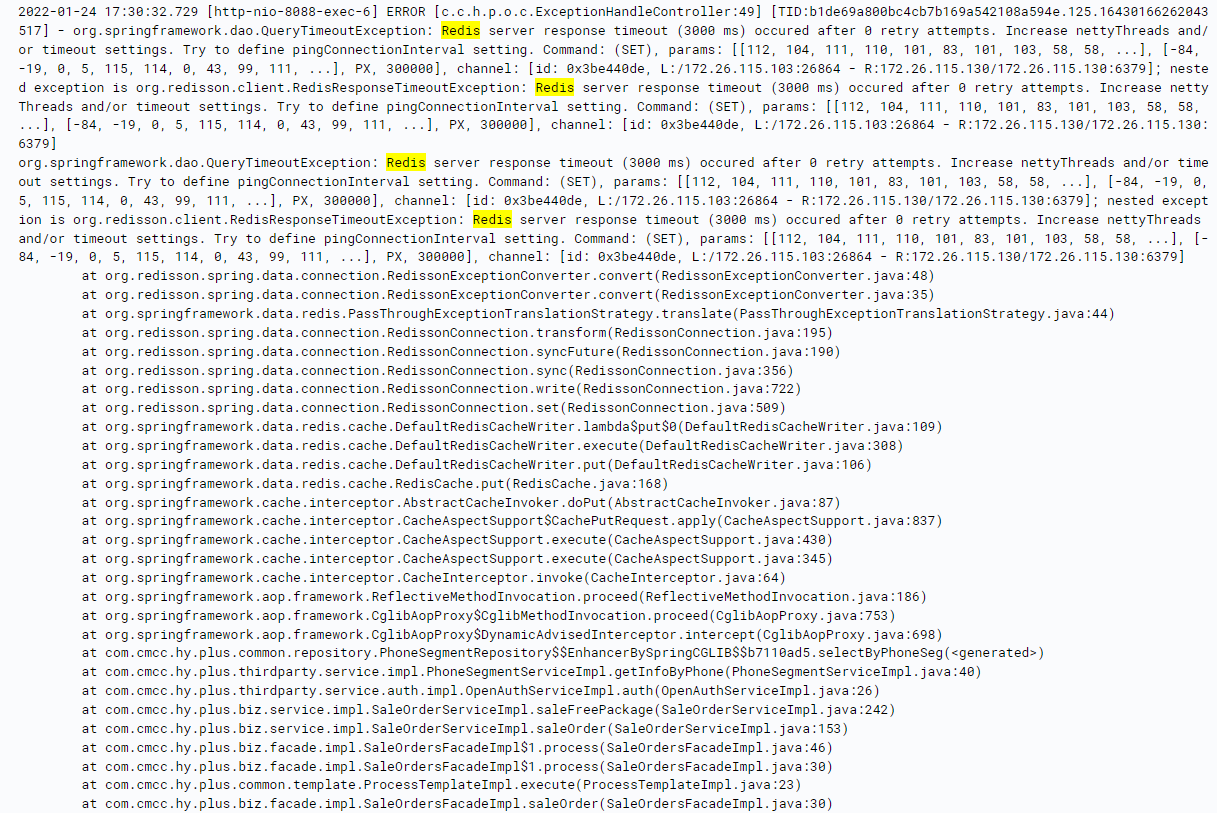
Redisson bug analysis
Maximum likelihood estimation and cross entropy loss
看过很多教程,却依然写不好一个程序,怎么破?
持续测试(CT)实战经验分享
Utilisation de l'écran OLED
系统与应用监控的思路和方法
随机推荐
永磁同步电机转子位置估算专题 —— 基波模型类位置估算概要
Pytest (3) - Test naming rules
BUUCTF---Reverse---easyre
Quel genre de programmation les enfants apprennent - ils?
Event center parameter transfer, peer component value transfer method, brother component value transfer
Discussion on beegfs high availability mode
Poj1149 pigs [maximum flow]
[weekly pit] output triangle
Gui Gui programming (XIII) - event handling
JVM_常见【面试题】
Trends of "software" in robotics Engineering
I've seen many tutorials, but I still can't write a program well. How can I break it?
Tencent T2 Daniel explained in person and doubled his job hopping salary
使用ssh连接被拒
OLED屏幕的使用
[weekly pit] positive integer factorization prime factor + [solution] calculate the sum of prime numbers within 100
Groovy basic syntax collation
5. 無線體內納米網:十大“可行嗎?”問題
PowerPivot - DAX (first time)
Speech recognition (ASR) paper selection: talcs: an open source Mandarin English code switching corps and a speech