当前位置:网站首页>Buuctf, web:[geek challenge 2019] buyflag
Buuctf, web:[geek challenge 2019] buyflag
2022-07-03 22:08:00 【Part 02】
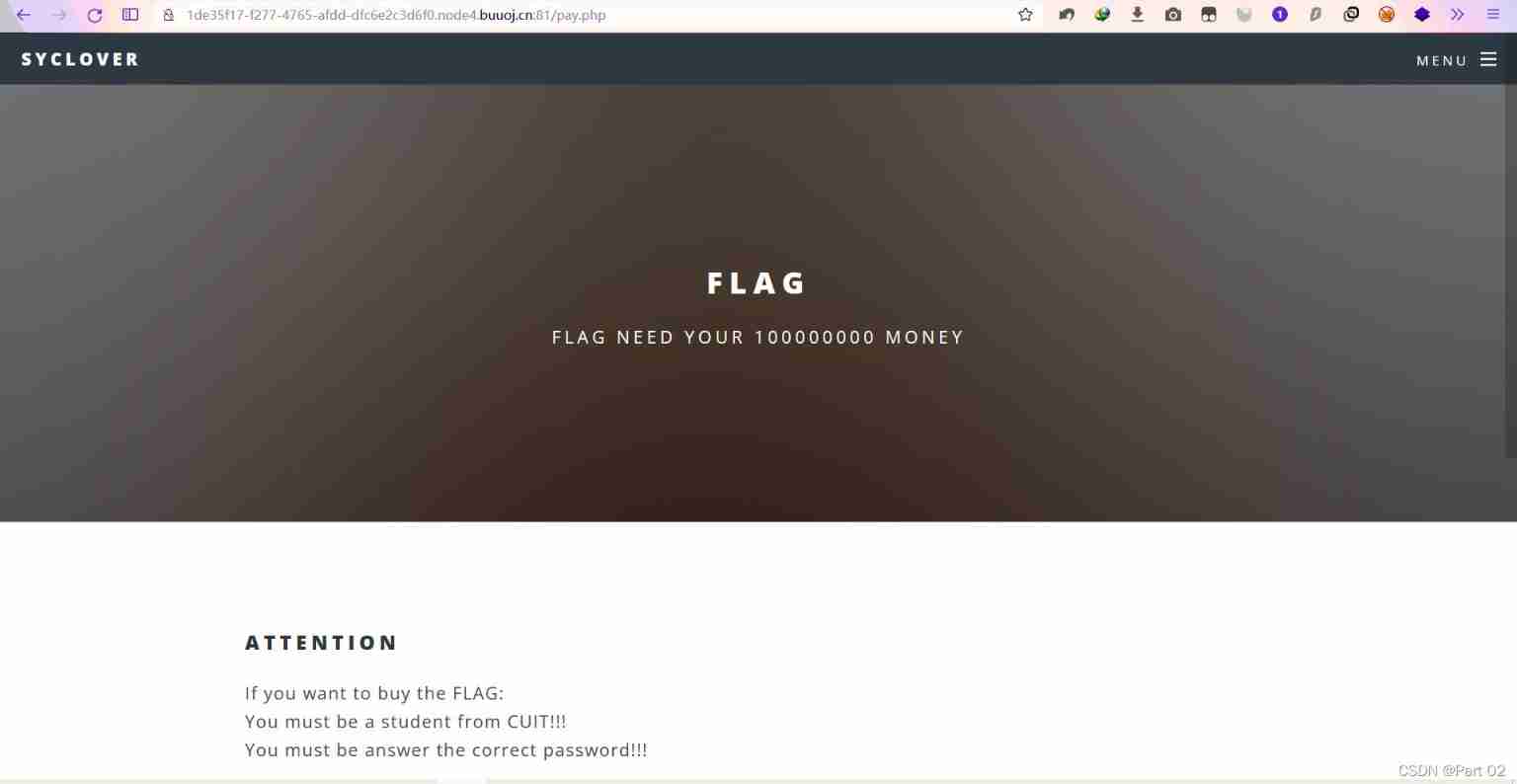
attention
If you want to buy the FLAG:
You must be a student from CUIT!!!
You must be answer the correct password!!!Only Cuit's students can buy the FLAG
Three tips , buy , use money=100000000, It's a CUIT Of the students , Correct password
Source code

~~~post money and password~~~
if (isset($_POST['password']))
{
$password = $_POST['password'];
if (is_numeric($password))
{
echo "password can't be number</br>";
}
elseif ($password == 404)
{
echo "Password Right!</br>";
}
}Weak comparison
password=404a
This is the code
Grab the bag post Still no response , The second tip is useless , Students can only correspond to cookie Of user

Change it to 1
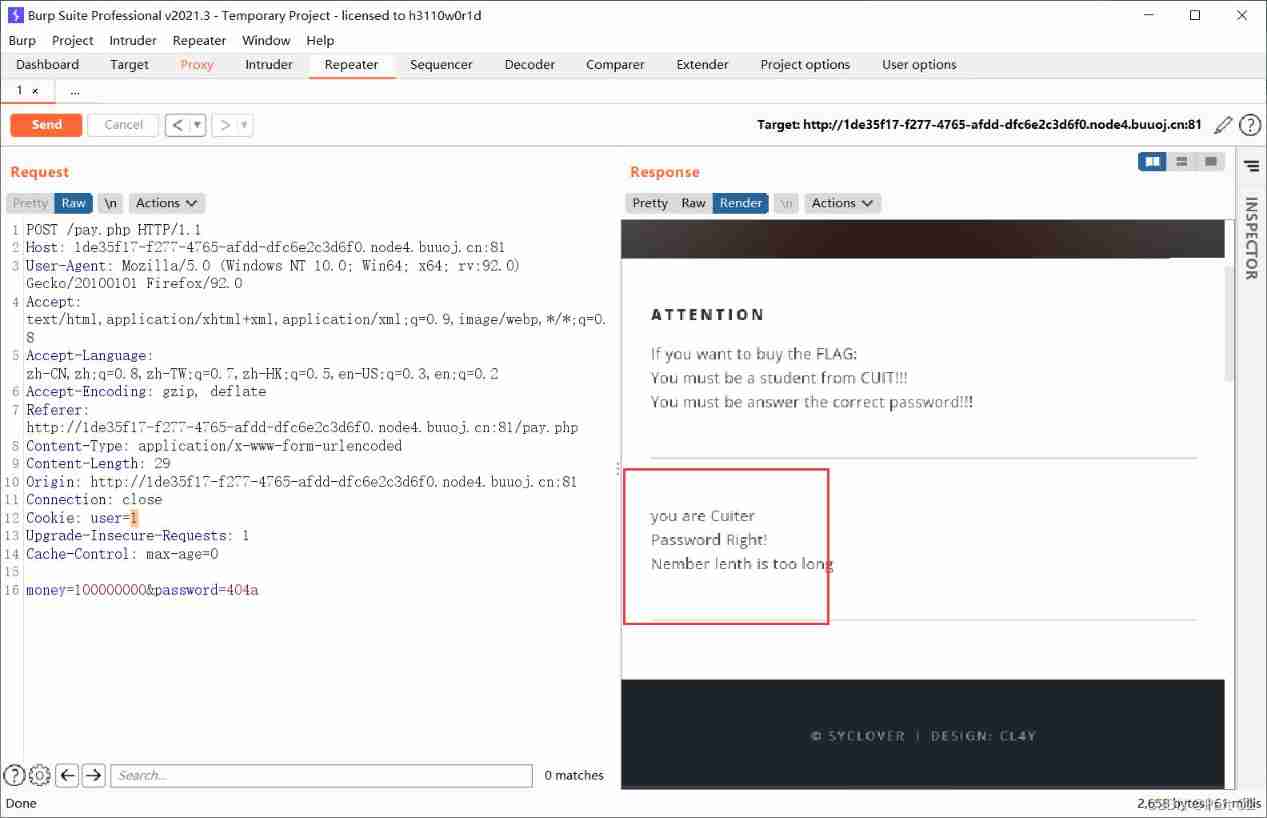
Three conditions meet two ,money The parameter is too long
Use scientific counting method to get flag, Operation not available
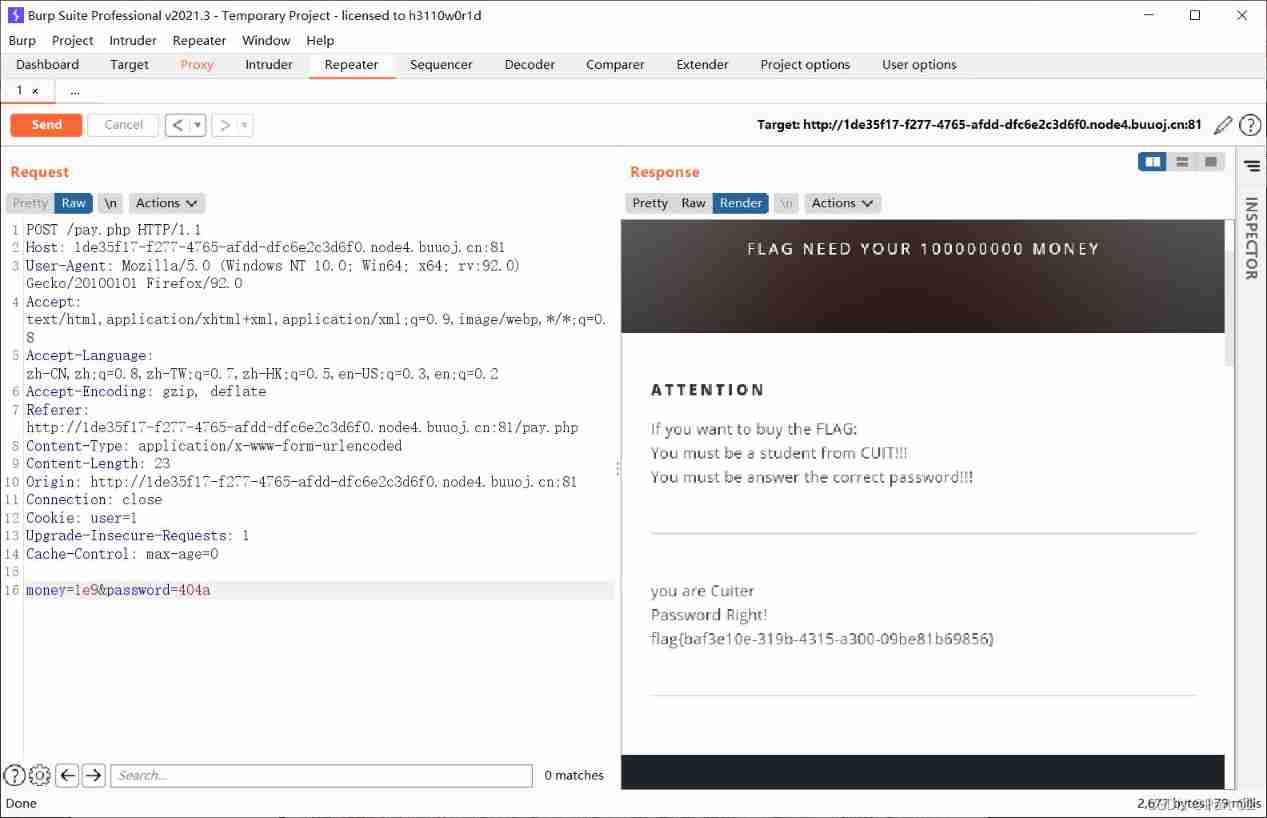
flag{baf3e10e-319b-4315-a300-09be81b69856}
边栏推荐
- treevalue——Master Nested Data Like Tensor
- Solve the problem that openocd fails to burn STM32 and cannot connect through SWD
- Tkinter Huarong Road 4x4 tutorial III
- Global and Chinese market of wireless hard disk 2022-2028: Research Report on technology, participants, trends, market size and share
- 2022 safety officer-a certificate registration examination and summary of safety officer-a certificate examination
- Blue Bridge Cup Guoxin Changtian single chip microcomputer -- led lamp module (V)
- Some 5000+ likes, the development notes of a director of cosmic factory, leaked
- Blue Bridge Cup Guoxin Changtian single chip microcomputer -- software environment (II)
- How to store null value on the disk of yyds dry inventory?
- Yyds dry inventory hcie security Day12: concept of supplementary package filtering and security policy
猜你喜欢
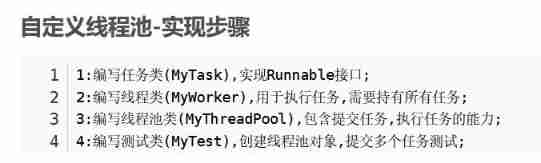
Pooling idea: string constant pool, thread pool, database connection pool

Redis single thread and multi thread

Compréhension de la technologie gslb (Global Server load balance)
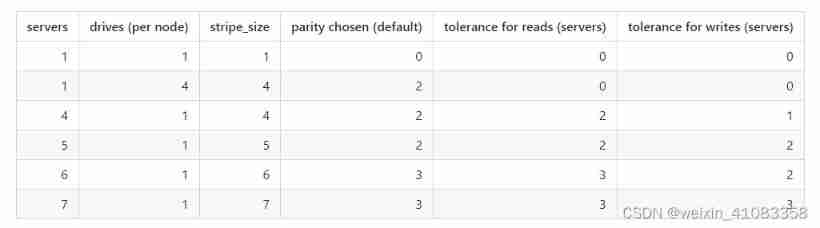
Minio deployment

gslb(global server load balance)技术的一点理解
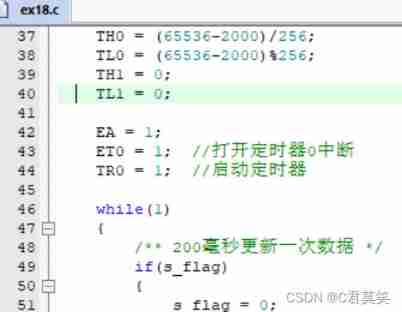
Code in keil5 -- use the code formatting tool astyle (plug-in)
![Intimacy communication -- [repair relationship] - use communication to heal injuries](/img/c2/f10405e3caf570dc6bd124d65b2e93.jpg)
Intimacy communication -- [repair relationship] - use communication to heal injuries
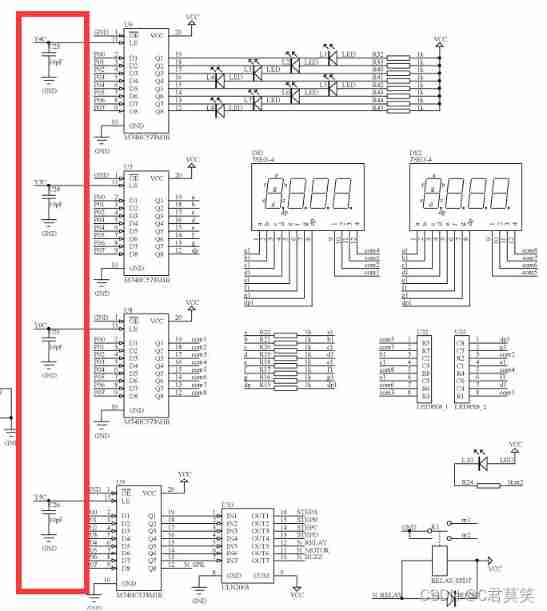
Bluebridge cup Guoxin Changtian single chip microcomputer -- detailed explanation of schematic diagram (IV)
![[dynamic planning] counting garlic customers: the log of garlic King (the longest increasing public subsequence)](/img/29/543dce2f24130d22c1824385fbfa8f.jpg)
[dynamic planning] counting garlic customers: the log of garlic King (the longest increasing public subsequence)
treevalue——Master Nested Data Like Tensor
随机推荐
China HDI market production and marketing demand and investment forecast analysis report Ⓢ 2022 ~ 2028
How does sentinel, a traffic management artifact, make it easy for business parties to access?
Data consistency between redis and database
Tidb's initial experience of ticdc6.0
Oil monkey plug-in
十大券商开户注册安全靠谱吗?有没有风险的?
On my first day at work, this API timeout optimization put me down!
使用dnSpy对无源码EXE或DLL进行反编译并且修改
How to install sentinel console
DR-NAS26-Qualcomm-Atheros-AR9582-2T-2R-MIMO-802.11-N-5GHz-high-power-Mini-PCIe-Wi-Fi-Module
What is the content of the securities practice examination?
Summary of basic knowledge of exception handling
Base ring tree Cartesian tree
Global and Chinese market of wall mounted kiosks 2022-2028: Research Report on technology, participants, trends, market size and share
Control loop of program (while loop)
Leetcode problem solving - 230 The k-th smallest element in the binary search tree
Imitation Netease cloud music applet
Development mode and Prospect of China's IT training industry strategic planning trend report Ⓣ 2022 ~ 2028
DOM light switch case
MySQL - idea connects to MySQL