当前位置:网站首页>How to prevent malicious crawling of information by one-to-one live broadcast source server
How to prevent malicious crawling of information by one-to-one live broadcast source server
2022-07-03 23:06:00 【Cloudleopard network technology】
In the process of running the one-to-one live broadcast source code , The generated data will be stored on the server , For any platform , Data security is the problem that needs to be solved most in data storage . Except for malicious access 、 Domain name hijacking and other data problems , Some crawlers will crawl website information maliciously , At this time, it is necessary to intercept , Prevent data leakage .
The one-to-one live broadcast source code can be configured on demand nignx The environment and Apache Environmental Science , Achieve interception , The specific operation steps are as follows :
One 、Nginx Environment :
1. create profile
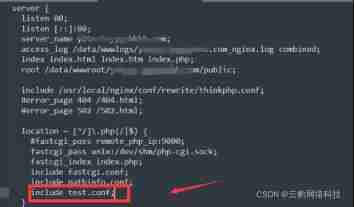
For example, enter nginx Install under directory conf Catalog , establish : test…conf
The contents are as follows :
# prohibit Scrapy Wait for the tool to grab if ($http_user_agent ~* (Scrapy|Curl|HttpClient)) {
return 403;
}
# Prohibit designation UA And UA Empty visit
if ($http_user_agent ~ "WinHttp|WebZIP|FetchURL|node-superagent|java/|
FeedDemon|Jullo|JikeSpider|Indy Library|Alexa Toolbar|AskTbFXTV|AhrefsBot|
CrawlDaddy|Java|Feedly|Apache-HttpAsyncClient|UniversalFeedParser|ApacheBench|
Microsoft URL Control|Swiftbot|ZmEu|oBot|jaunty|Python-urllib|
lightDeckReports Bot|YYSpider|DigExt|HttpClient|MJ12bot|heritrix|EasouSpider|Ezooms|BOT/0.1|
YandexBot|FlightDeckReports|Linguee Bot|^$" ) {
return 403;
}
2. Import the configuration file created above into the website configuration file
Include test.conf;
3. restart nginx Services take effect
systemctl restart nginx
Two 、apache Environment
1、 modify httpd.conf The configuration file
Add the following code , restart Apache take effect
Shell
DocumentRoot /home/wwwroot/xxx
SetEnvIfNoCase User–Agent “.*(FeedDemon|Indy Library|Alexa Toolbar|AskTbFXTV|AhrefsBot|CrawlDaddy|CoolpadWebkit|Java|Feedly|UniversalFeedParser|ApacheBench|Microsoft URL Control|Swiftbot|ZmEu|oBot|jaunty|Python-urllib|lightDeckReports Bot|YYSpider|DigExt|HttpClient|MJ12bot|heritrix|EasouSpider|Ezooms)” BADBOT
Orderallow,deny
Allow fromall
deny fromenv=BADBOT
3、 ... and 、 test
1、 Use curl -A Simulate grabbing , such as :
curl -I -A 'Spider' www.test888.cn
give the result as follows :
[[email protected]]# curl -I -A 'Spider' www.test888.cn
HTTP/1.1 403 Forbidden
Server: nginx/1.12.0
Date: Wed, 24 Apr 2021 11:35:21 GMT
Content-Type: text/html
Content-Length: 169
Connection: keep-alive
above , It is the one-to-one live source code that intercepts the content of information crawled by crawlers , Preventing malicious crawling is just one of the security strategies to ensure data security , To learn more about security policies , You can pay attention to the following content .
Statement : The above content is original by cloudleopard technology , Without the author's consent , Prohibited reproduced , Otherwise, relevant legal liability will be investigated .
边栏推荐
- Recursive least square adjustment
- User login function: simple but difficult
- How about opening an account at Hengtai securities? Is it safe?
- SDNU_ ACM_ ICPC_ 2022_ Winter_ Practice_ 4th [individual]
- Hcip day 14 notes
- Wisdom tooth technology announced that it had completed the round D financing of US $100million and had not obtained a valid patent yet
- 2 spark environment setup local
- 2022.02.14
- Unsafe and CAS principle
- Firefox set up proxy server
猜你喜欢

Gorilla/mux framework (RK boot): add tracing Middleware

The 2022 global software R & D technology conference was released, and world-class masters such as Turing prize winners attended

Leetcode: a single element in an ordered array

Schematic diagram of crystal oscillator clock and PCB Design Guide

In 2022, 6G development has indeed warmed up
Esp-idf turns off serial port log output.
Data consistency between redis and database

Pat grade A - 1164 good in C (20 points)
Hcip day 15 notes
Take you to master the formatter of visual studio code
随机推荐
Runtime. getRuntime(). totalMemory/maxMemory()
Exclusive download! Alibaba cloud native brings 10 + technical experts to bring "new possibilities of cloud native and cloud future"
Unity shader visualizer shader graph
Pandaoxi's video
2.14 summary
Leetcode: a single element in an ordered array
Pan Yueming helps Germany's Rochester Zodiac custom wristwatch
Hcip day 16 notes
IDENTITY
How can enterprises and developers take advantage of the explosion of cloud native landing?
Unique in China! Alibaba cloud container service enters the Forrester leader quadrant
Leetcode week 4: maximum sum of arrays (shape pressing DP bit operation)
To rotate 90 degrees clockwise and modify the video format
Hcip day 14 notes
Why should enterprises do more application activities?
Summary of fluent systemchrome
Day30-t540-2022-02-14-don't answer by yourself
The difference between SRAM and DRAM
BUUCTF,Misc:LSB
Shell script three swordsman awk