当前位置:网站首页>量子三体问题: Landau Fall
量子三体问题: Landau Fall
2022-07-02 10:10:00 【weixin_42849849】
边栏推荐
- Essential for operation and maintenance - Elk log analysis system
- numpy数组计算
- JS reverse row query data decryption
- de4000h存储安装配置
- How to get the operating system running PHP- How to get the OS on which PHP is running?
- [opencv learning] [moving object detection]
- Security RememberMe原理分析
- Unity SKFramework框架(十八)、RoamCameraController 漫游视角相机控制脚本
- Japan bet on national luck: Web3.0, anyway, is not the first time to fail!
- 【云原生数据库】遇到慢SQL该怎么办(上)?
猜你喜欢

Fully autonomous and controllable 3D cloud CAD: crowncad's convenient command search can quickly locate the specific location of the required command.

Unity SKFramework框架(二十)、VFX Lab 特效库

三翼鸟两周年:羽翼渐丰,腾飞指日可待
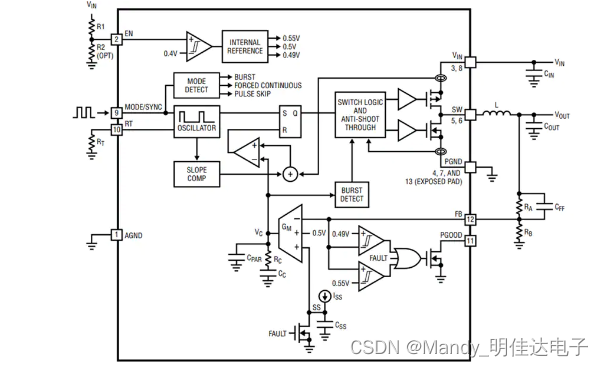
Ltc3307ahv meets EMI standard, step-down converter qca7005-al33 phy
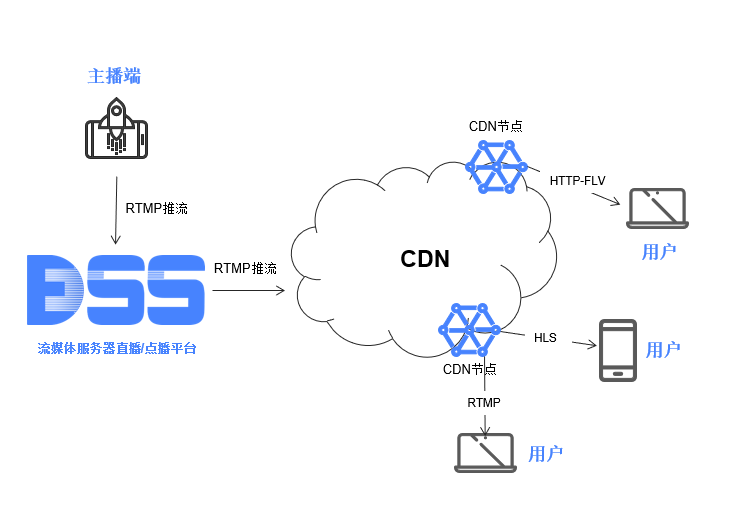
操作教程:EasyDSS如何将MP4点播文件转化成RTSP视频流?
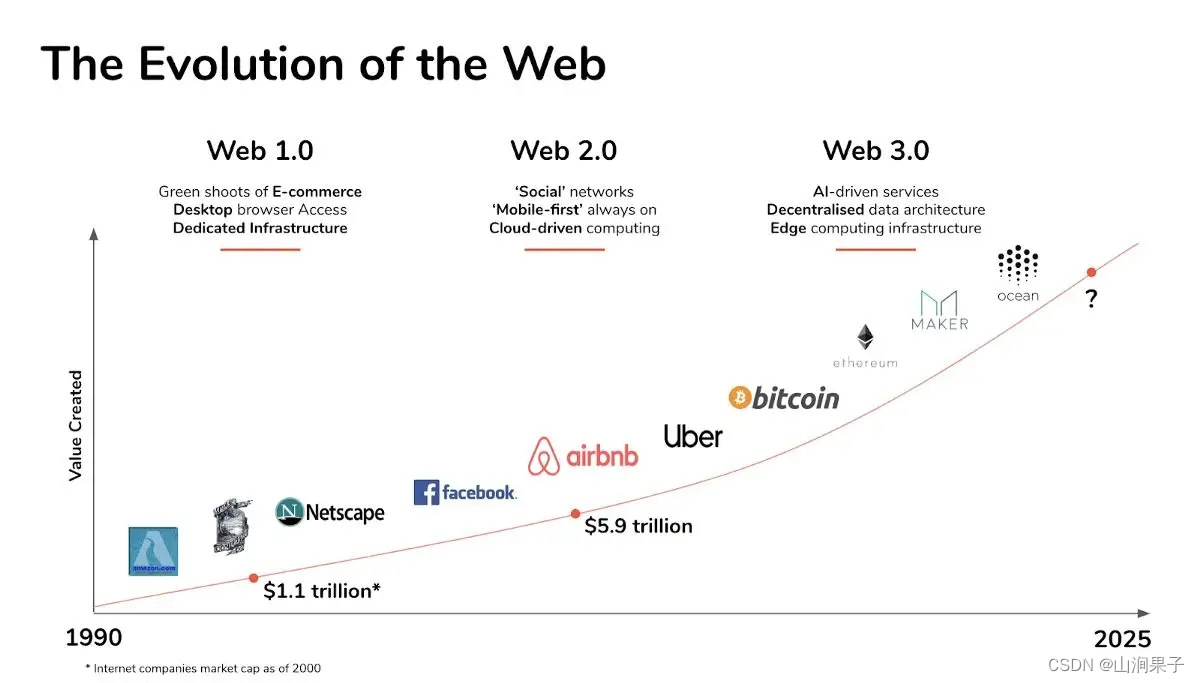
Japan bet on national luck: Web3.0, anyway, is not the first time to fail!

SAP MM 因物料有负库存导致MMPV开账期失败问题之对策

Analog to digital converter (ADC) ade7913ariz is specially designed for three-phase energy metering applications
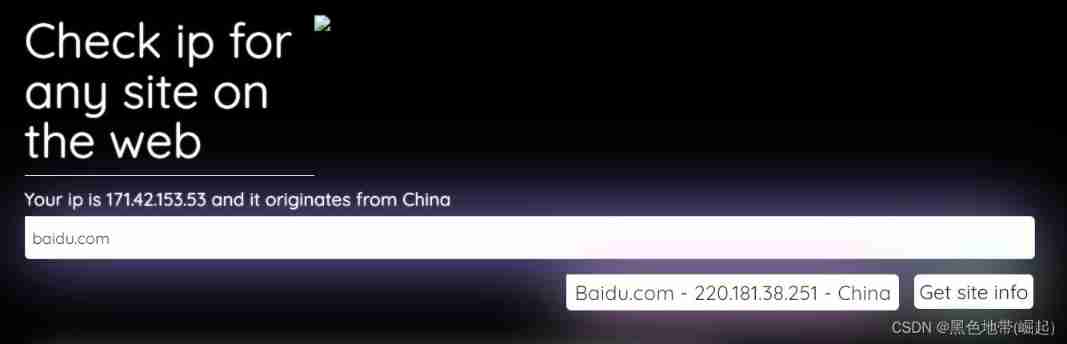
(7) Web security | penetration testing | how does network security determine whether CND exists, and how to bypass CND to find the real IP
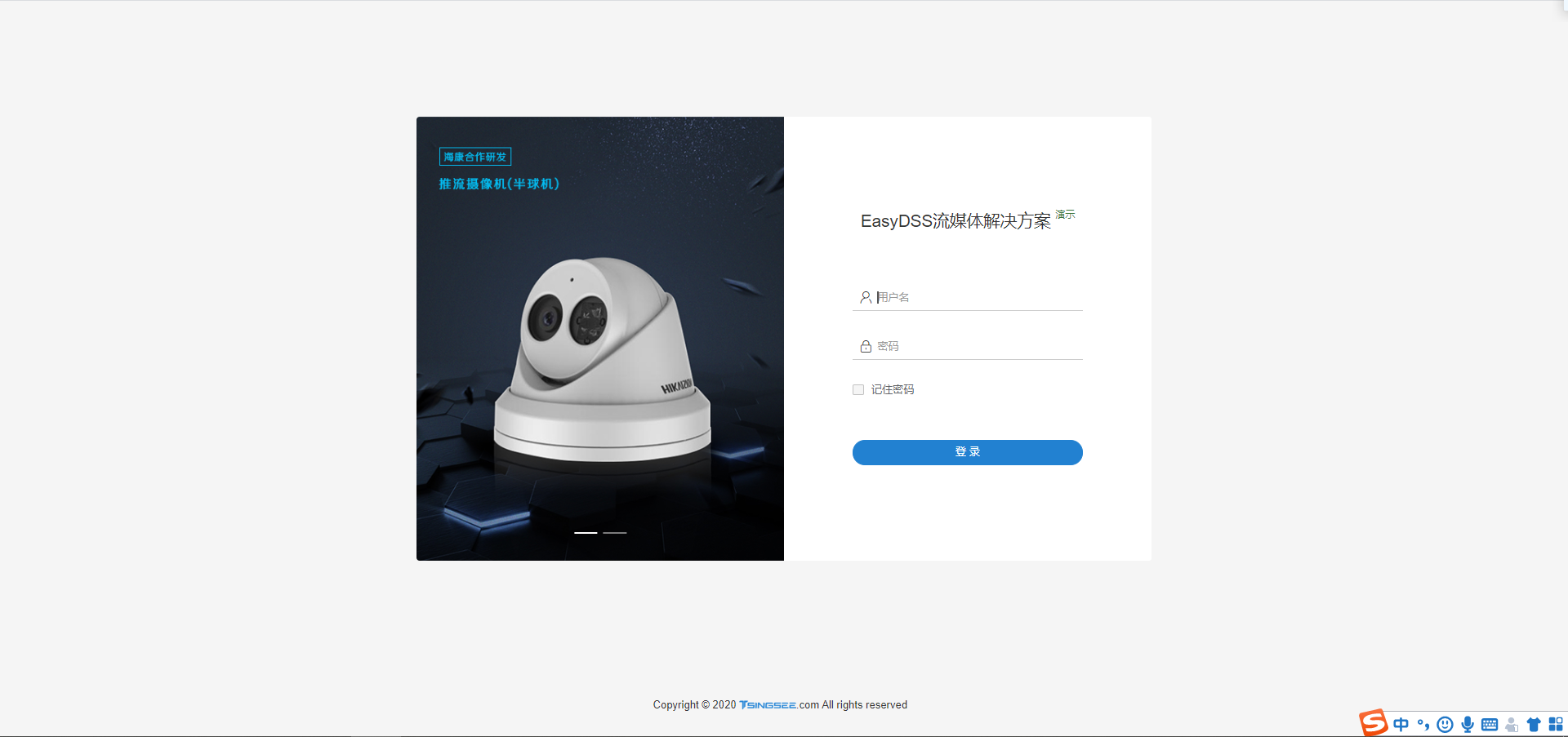
How to modify the error of easydss on demand service sharing time?
随机推荐
[error record] cannot open "XXX" because Apple cannot check whether it contains malware
Essential for operation and maintenance - Elk log analysis system
运维必备——ELK日志分析系统
为什么switch 的default后面要跟break?
Explanation of 34 common terms on the Internet
Jerry's weather code table [chapter]
Tencent three sides: in the process of writing files, the process crashes, and will the file data be lost?
de4000h存储安装配置
能自动更新的万能周报模板,有手就会用!
SSL证书的分类有哪些?如何选择合适的SSL证书?
JS逆向之巨量创意signature签名
Everyone wants to eat a broken buffet. It's almost cold
Unity SKFramework框架(十四)、Extension 扩展函数
Ali on three sides, it's really difficult to successfully get the offer rated P7
屠榜多目标跟踪!BoT-SORT:稳健的关联多行人跟踪
D如何检查null
三面阿里,有惊无险成功拿到offer定级P7,只能说是真的难
[opencv learning] [moving object detection]
The UVM Primer——Chapter2: A Conventional Testbench for the TinyALU
The redis development document released by Alibaba covers all redis operations