当前位置:网站首页>Chapter 1 Introduction and use skills of interceptors
Chapter 1 Introduction and use skills of interceptors
2022-07-26 23:51:00 【Sleepy sheep】
1-1 Interceptor Getting started with interceptors


Demonstrate one by one
Create a project

take restful Copy the code from , Easy to demonstrate
open xml Increased reliance on

provided Only in the development and compilation will reference , When packaging for final use jar Will be excluded
Add interceptor package


Generate three methods



Why introduce the dependency just now ?
because

These three methods all point to native request and response object , If you do not introduce dependent programs, you will report compilation errors

return true It will be delivered to the later interceptor or controller ,false It will directly return to the client , The result determines whether to continue execution or end immediately and return the response back , This is very important for program control

After the target resource is processed successfully , But before the response text is generated , What to do
![]()

After the corresponding text of the target is generated , That's how it works
![]()

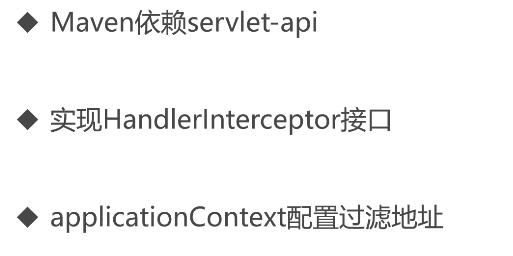
stay applicationContext Configure in to make springmvc To identify
Intercept all requests , Then the intercepted request is delivered to Myinterceptor And execute it in the sequence of the implementation methods inside
function

The response returns success , View console

This sentence is increasing
![]()
1-2 Interceptor Using skills

There will be many problems to be solved in actual use
start-up
But the controller prints out a lot of extra information

Every time you send localhost This url Its essence is through tomcat To call springmvc The parsing function of , To get the corresponding resources , These resources are in line with /** All rules will be blocked
![]()
The interceptor is not affected by this sentence

Exclude some static addresses
Run again 
At this time, only client.html Captured
There are too many static types , If you configure one by one like the above, it may be a long time , How to make us understand static resources and controller Applications are effectively differentiated ?
Unified management of static resources

By managing the static resource directory to uniformly exclude these
![]()
Reverse thinking is also possible, such as only restful Intercept all requests under
![]()
![]()
If more than one is needed uri Where to intercept , Additional writing
![]()
If a request is filtered by multiple interceptors at the same time , Which one is the first to execute ?
increase myinterceptor1

Configure the new interceptor

Two interceptors work uri It's the same , That's first ? What about execution later ?、

The order is reversed , Why? ?

return false What happens when an interrupt occurs ?


The request that should be executed and subsequent processing are all blocked , At the same time, the response is all produced in the current method
Pass in an array to test


What you get in the corresponding part of the request is the response text generated in the interceptor
1-3 Inteceptor and Filter The difference between


边栏推荐
- Part II - C language improvement_ 7. Structure
- 证券公司哪家佣金最低?网上开户安全吗
- Three effective strategies for the transformation of data supply chain to be coordinated and successful
- [shader realizes shine effect _shader effect Chapter 3]
- Pre research of data quality management tools Griffin vs deequ vs great expectations vs quality
- Upload files to the server
- np. transpose & np.expand_ dims
- In simple terms, cchart daily lesson - happy high school lesson 57 new starting point, the old tree and new bud of colorful interface library
- 第二部分—C语言提高篇_10. 函数指针和回调函数
- C language dynamic memory management
猜你喜欢

MySQL random paging to get non duplicate data
第二部分—C语言提高篇_8. 文件操作
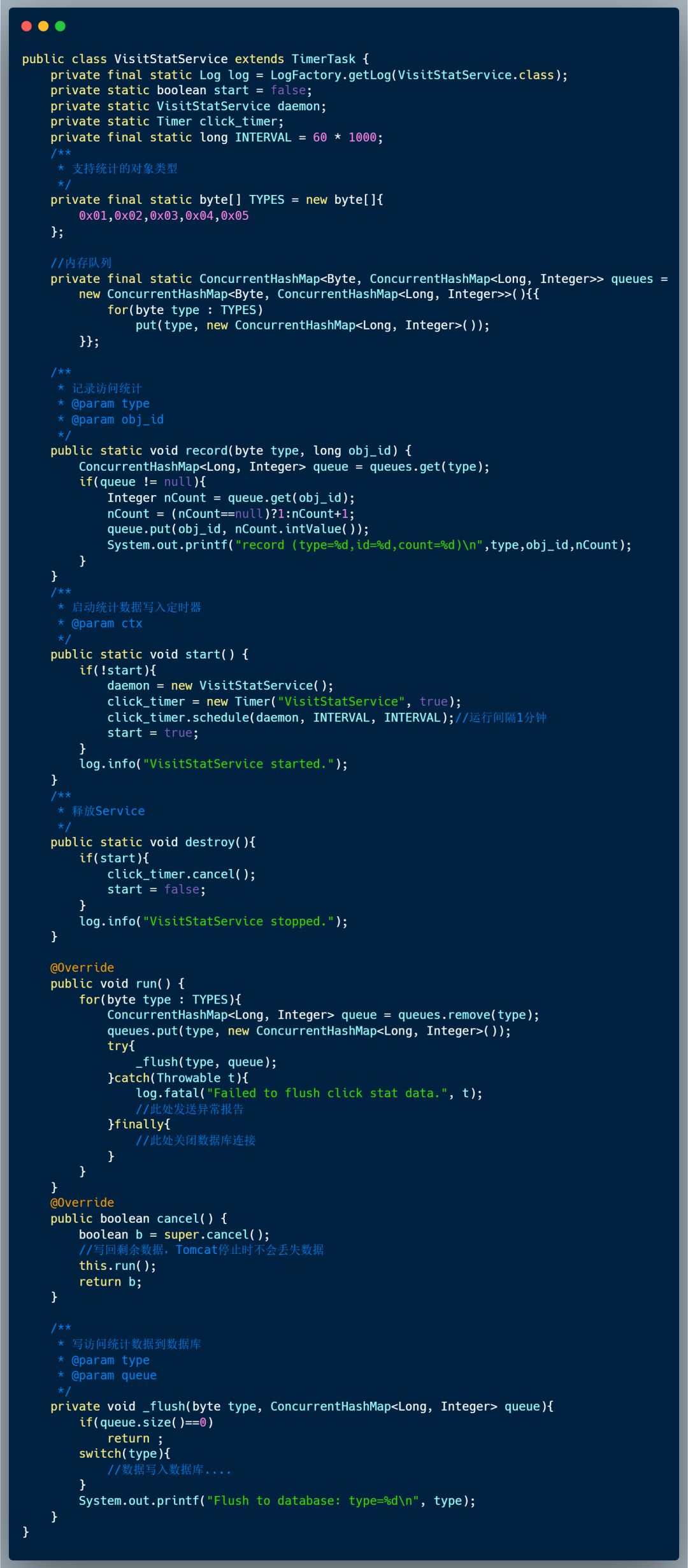
An online accident, I suddenly realized the essence of asynchrony

18. Opening and saving file dialog box usage notes

push to origin/master was rejected 错误解决方法

New features of ES6

2. Realize the map of navigation bar and battle page

Number that cannot be bought
Silicon Valley class lesson 6 - Tencent cloud on demand management module (I)

Customer case | student education relies on observation cloud to create a new ecosystem of observable Smart Education
随机推荐
Tensorflow2.0 深度学习运行代码简单教程
C语言数组
Which securities company has the lowest commission? Is online account opening safe
ES6新特性
会议OA之我的会议
2022.7.26-----leetcode.1206
Kingbasees SQL language reference manual of Jincang database (3.1.1.3. currency type)
[Luogu] p2709 little B's inquiry
How to use data pipeline to realize test modernization
Section 6: introduction to cmake grammar
Dynamic SQL
Pytorch学习记录(二):张量
Security team: Recently, there is an rce vulnerability in the COREMAIL email client of windows, which may lead to the disclosure of the private key of the wallet
Sign up now | frontier technology exploration: how to make spark stronger and more flexible
力扣152题:乘积最大子数组
第二部分—C语言提高篇_7. 结构体
Pyqt5 how to set pushbutton click event to obtain file address
[2016] [paper notes] differential frequency tunable THz technology——
第二部分—C语言提高篇_5. 位运算
Three person management of system design